

Varonis for Windows and NAS
source link: https://www.varonis.com/products/windows-and-nas-security
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

Varonis for Windows and NAS
Automatically discover sensitive data, right-size permissions, and detect abnormal behavior.
Trusted by 7,000+ companies worldwide







Our vast library of data classification policies finds sensitive data hidden in your Windows file shares and NAS devices. Varonis goes beyond regular expressions with proximity matching, negative keywords, and algorithmic verification to generate high-fidelity results.
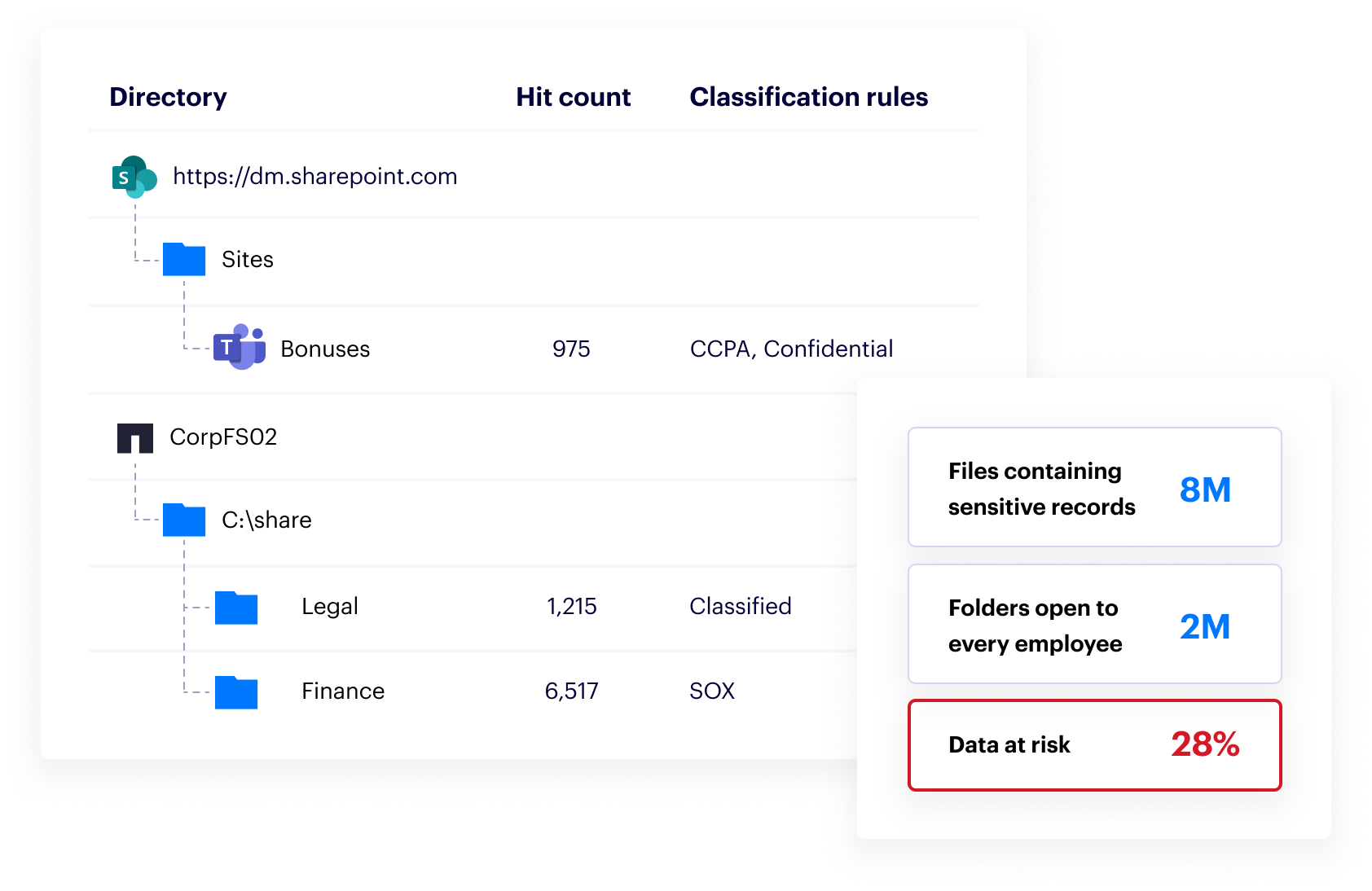

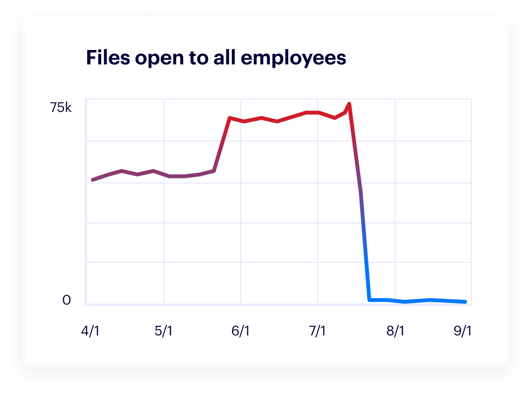
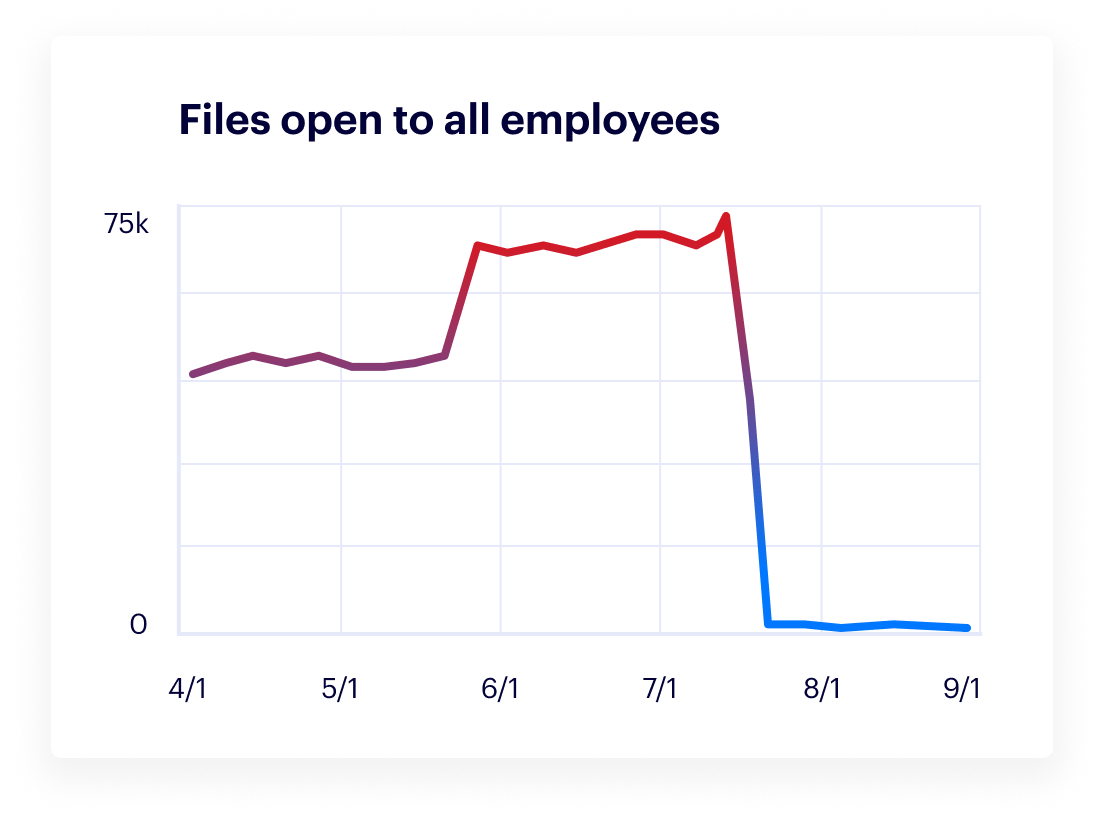
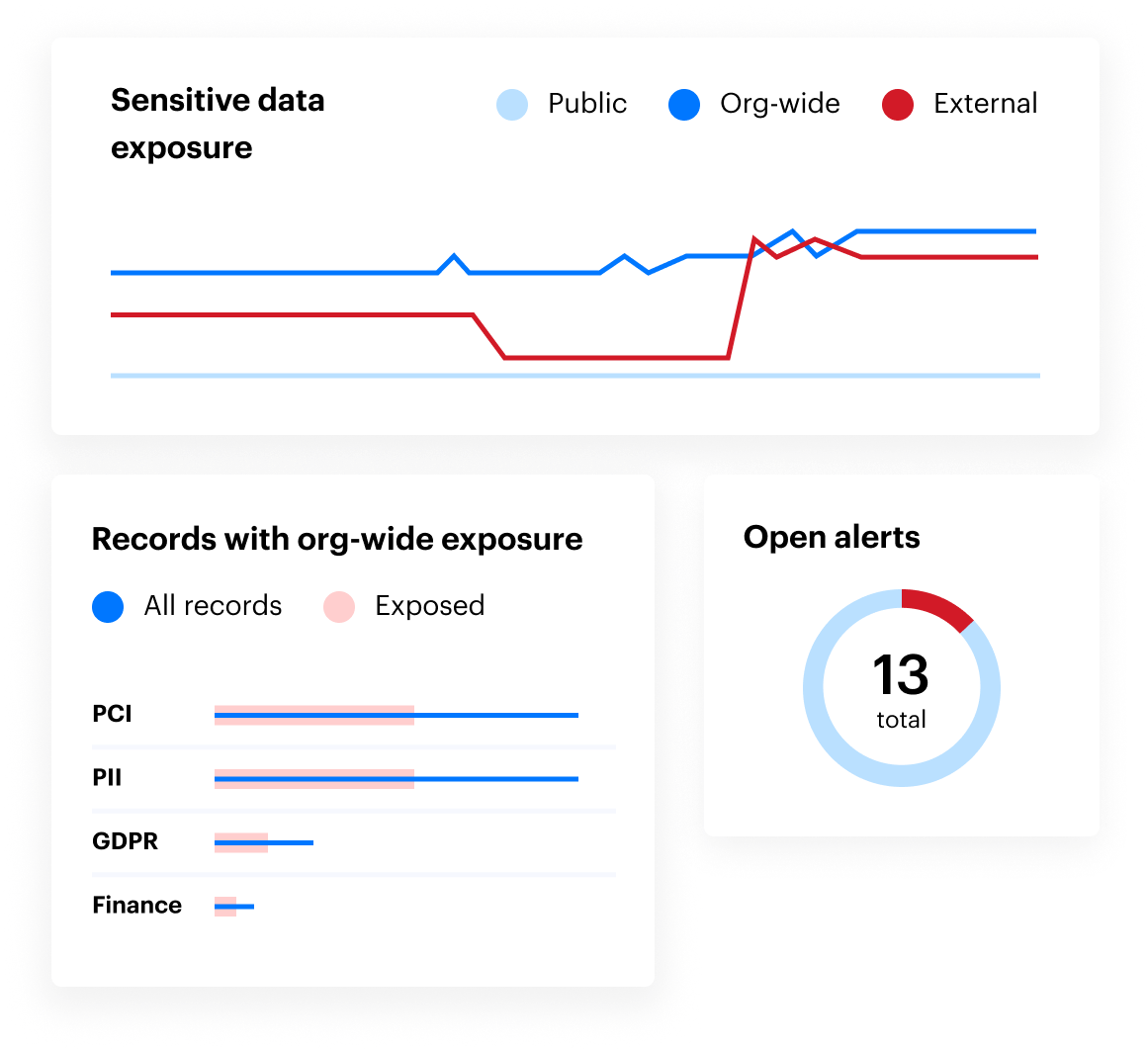
Varonis shows you where sensitive data lives, if it’s exposed, and how it’s being used. Get a real-time view of your data security posture and drill into any user or group to see exactly what data they can access across your entire environment.

Varonis monitors SMB/CIFS shares without requiring native auditing. We capture all the critical events you need — such as read, move, modify, and delete — accelerating cross-platform security investigations for cloud and on-prem environments.
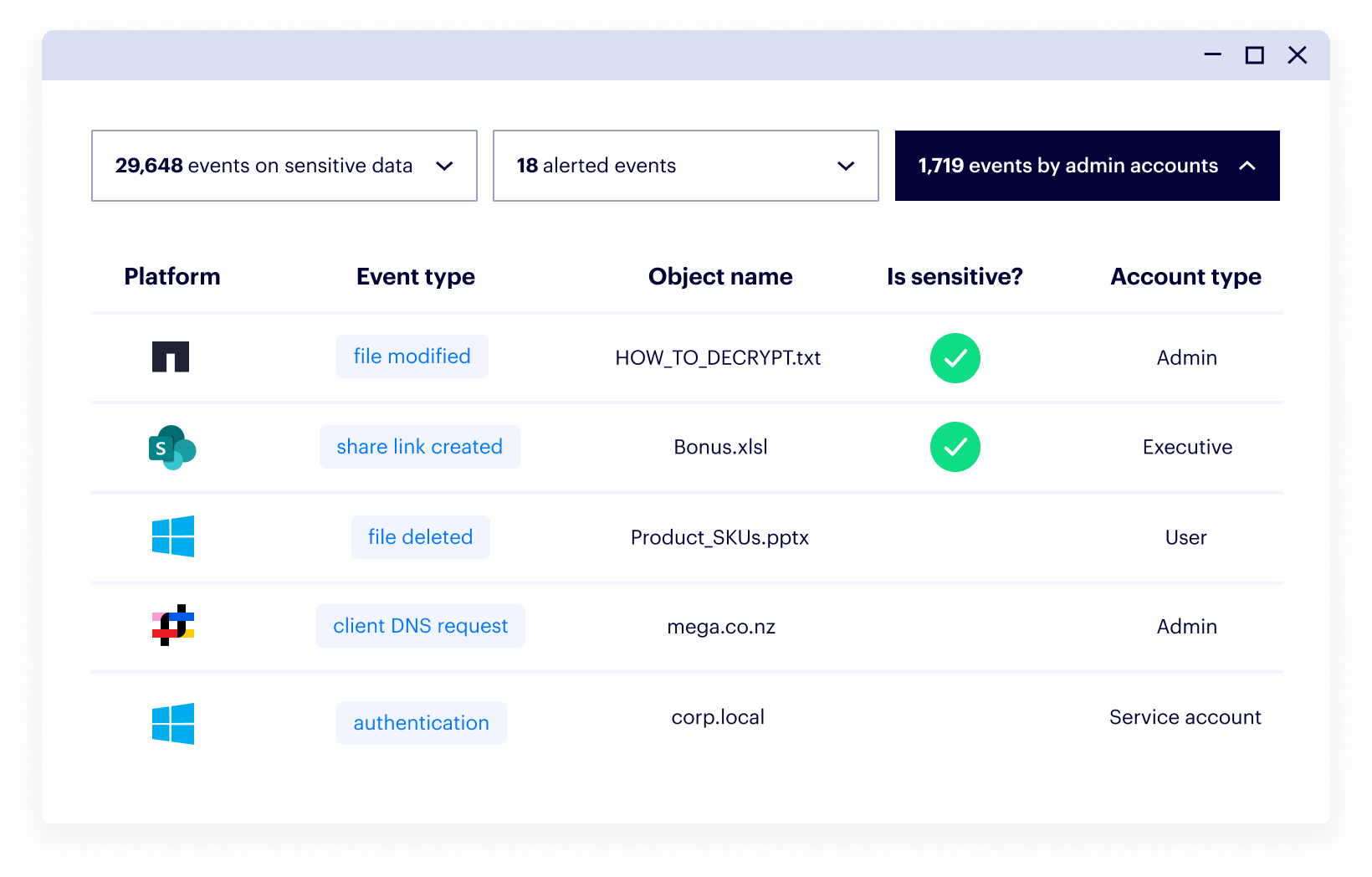

Varonis’ behavioral-based threat models detect abnormal data activity in real time — stopping threats to data before they become breaches. Our UEBA augments NAS backup capabilities for comprehensive ransomware protection.


Get started with our world-famous Data Risk Assessment.
- Critical findings report
- 1x1 with a data security expert
- Full access to the entire Varonis Data Security Platform
- Get started in 15 minutes
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK

