

Mantis – The Most Powerful Botnet Behind 3000 DDoS Attacks On Cloudflare Users
source link: https://www.theinsaneapp.com/2022/07/mantis-the-most-powerful-botnet-behind-cloudflare-attack.html
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
Mantis – The Most Powerful Botnet Behind 3000 DDoS Attacks On Cloudflare Users
A spate of attacks targeting nearly 1,000 Cloudflare customers was linked to the botnet that caused the largest HTTPS distributed attack (DDoS) in June 2022.

Calling the powerful botnet Mantis, the web performance and security company attributed it to more than 3,000 HTTP DDoS attacks against its users.
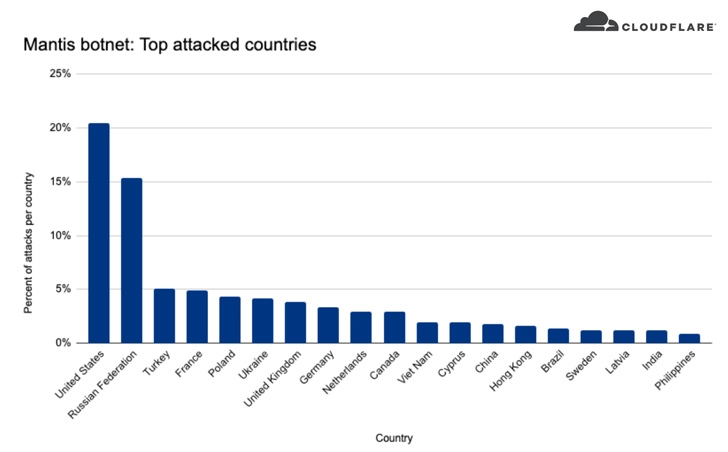
Internet, telecom, media, and gaming are the most targeted industry verticals. More than 20% of attacks were directed at U.S.-based businesses. Russia, Turkey, and France, followed closely by the U.K. and Germany.
The company claimed it had mitigated a DDoS attack against an unnamed customer website using its Free plan. It reached 26 million requests per second (RPS), and each node generated approximately 5,200 RPS.
The tsunami of junk traffic was short-lived and generated more than 212 million HTTPS requests. It came from more than 1,500 networks across 121 countries. India, Brazil, Russia, and the U.S. topped it all.
Cloudflare’s Omer Yachimik stated that although the Mantis botnet has a small number of bots (around 5,000), they can create a large force responsible for the largest HTTP DDoS attacks ever observed.
Mantis is unique for many reasons. First, it can carry out HTTPS DDoS attacks. These attacks are costly due to the computational resource required to secure TLS encrypted connections.
Second, unlike traditional botnets, which rely on IoT devices like routers and DVRs, Mantis leverages stolen virtual machines and powerful servers to provide additional resources.
Volumetric attacks generate more traffic than the target system can process. This causes the victim to exhaust its resources. While adversaries used UDP to launch amplifying attacks in the past, there has been an evolution to TCP reflected vectors that use middleboxes.
In May 2022, Microsoft disclosed that it had prevented 175,000 UDP-reflected amplification attacks directed at its Azure infrastructure over the past year. It also noticed a TCP-reflected amplification attack against an Azure resource in Asia, which reached 30 million packets/second (PPS) and lasted for 15 minutes.
The Azure Networking Team stated that “Reflected amplifying attacks” are here to stay and present a serious threat to the internet community. They continue to develop and exploit new vulnerabilities within protocols and software implementations to bypass traditional countermeasures.
Popular Stories You Shouldn’t Miss:
Let's fix the way you consume content. Stay up-to-date, ahead of the curve, and get smarter every day. Don't wait, Download the app today! Reinvent the way you feed your curiosity!
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK