Using Trusted Certificates with IBM Endpoint Manager for Mobile Devices
source link: https://darrylmiles.blog/2013/07/02/using-trusted-certificates-with-ibm-endpoint-manager-for-mobile-devices/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

Using Trusted Certificates with IBM Endpoint Manager for Mobile Devices
IBM Endpoint Manager for Mobile Devices requires a certificate to manage iOS devices – through Apple’s Push Notification Service (APNS). This APNS certificate allows the Management Extender to establish a secure, trusted channel of communication with the iOS devices. This setup is straightforward and is detailed here. Our MDM evaluators guide provides step by step instructions with screen captures. Contact me if you don’t have a copy.
If you’ve installed IEM to manage some devices, you’ll note that for iOS devices you have to install a self signed certificate first. You can remove the requirement for this by installing a well known or trusted certificate from Verisign, Godaddy, Gotrust etc.
The steps to install IEM with a trusted certificate below. I want to acknowledge the great article by Orb Data which provided me some great info, and explained certificates in PEM format.
- Complete Step 1: Deploy the Management Extender Fixlet and Step 2: Obtain certificate to manage Apple iOS devices to install the Management Extender. Save the final APNS certificate as push.cer and place it in a directory on your IEM server, say D:\ManagementExtender\APNS\push.cer. Now this has the certificate covered for IEM communicating with Apple’s APNS service.
- Now for the certificate for device to IEM server communication, we need to create a certificate request that a certificate authority can process. I was using Godaddy to define a certificate for the domain name mdm.darrylmiles.me. On a Mac I used OpenSSL I would run this command:openssl req -new -newkey rsa:2048 -nodes -keyout yourdomain.key -out yourdomain.csr
For my domain name, I entered: openssl req -new -newkey rsa:2048 -nodes -keyout darrylmiles.me.key -out darrylmiles.me.csr
I was able to the use the command illustrated on Godaddy’s web site here.
The result of this command is two files:
- Now on your certificate authority web site, take the text from within your CSR file (in my case darrylmiles.me.csr) and copy this into appropriate request page:
- Once the certificate request was accepted, I downloaded it as shown:
- The ZIP file contained two files gd_bundle.crt and mdm.darrylmiles.me.crt. Both files contained the certificate information in PEM format, ie.—–BEGIN CERTIFICATE—–
Lots of letters/numbers here…
—–END CERTIFICATE—–I renamed the files as follows:
gd_bundle.crt to gd_bundle.crt
mdm.darrylmiles.me.crt to mdm.darrylmiles.me.cer - I copied the darrylmiles.me.key, mdm.darrylmiles.me.crt and mdm.darrylmiles.me.cer to the IEM server to a directory called D:\ManagementExtender\Cert\
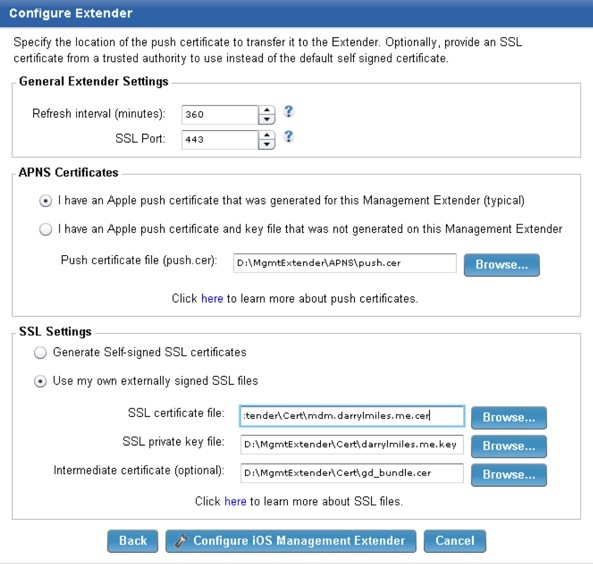
- I then configured the management extender using these settings:
- That’s it. Once the management extender is configured it’s now ready to accept device enrolments. Here are some screen captures of an iOS device being enrolled:
That’s it. IEM is now setup with a trusted certificate. If you have any queries, feel free to contact me or post a question to our developerWorks forum.
Darryl
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK