

Exploring GitHub Advanced Security for Azure DevOps
source link: https://www.visualstudiogeeks.com/devops/github/exploring-github-advanced-security-for-ado
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

It has been a few months since GitHub Advanced Security (GHAS) has been made generally available for Azure DevOps. During this time, I’ve engaged with numerous customers eager to implement GHAS within their Azure subscriptions. In this post, I wanted to show you a quick way to set up GHAS within Azure DevOps and explore the features available.

Enabling Advanced Security in Azure DevOps
This is easy, however, you need to be a member of the Project Collection Administrator group. You can verify that from Organization Settings -> Permissions and then the Members tab. You should see your name.
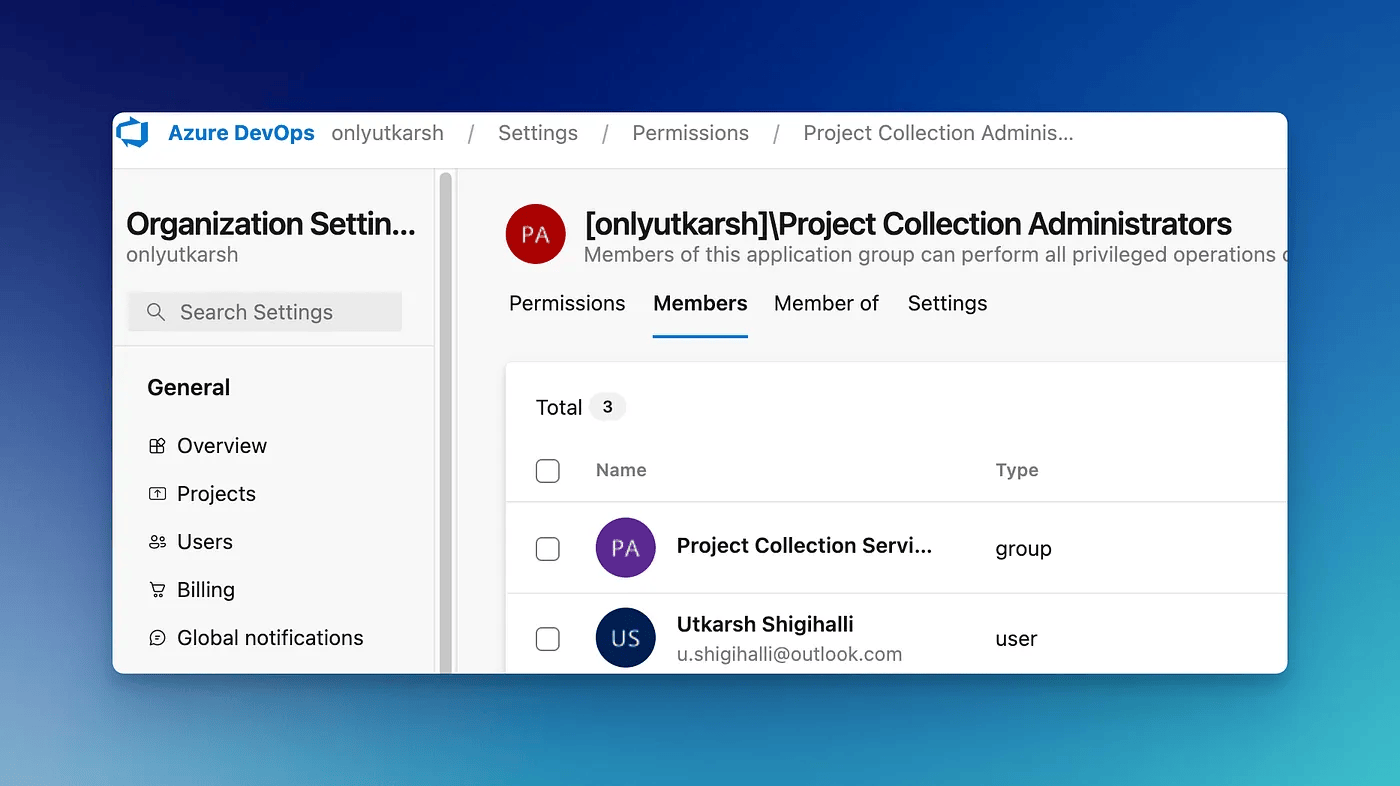
Once you have verified you are a Project Collection Administrator, you are ready to enable GHAS.
You can enable GHAS either individually per repo or across the organisation for all the repositories.
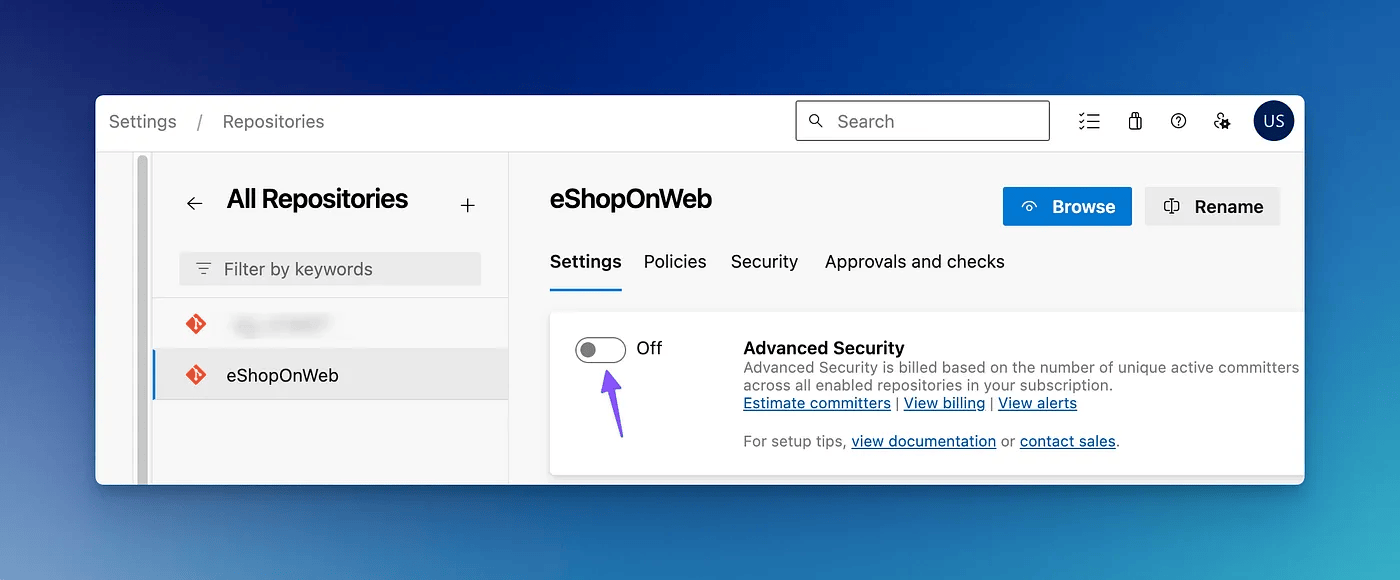
If you want to enable it for all the repositories in your organization, you will need to go to organization settings and then the Repositories section and enable it there.
For this post, I am enabling it only for a single repository. Once you click the Advanced Security flag (1), you will be prompted to show the number of committers you will be billed against (more on billing below). This repository has only me committing to it, so it has correctly identified 1 active committer (2).
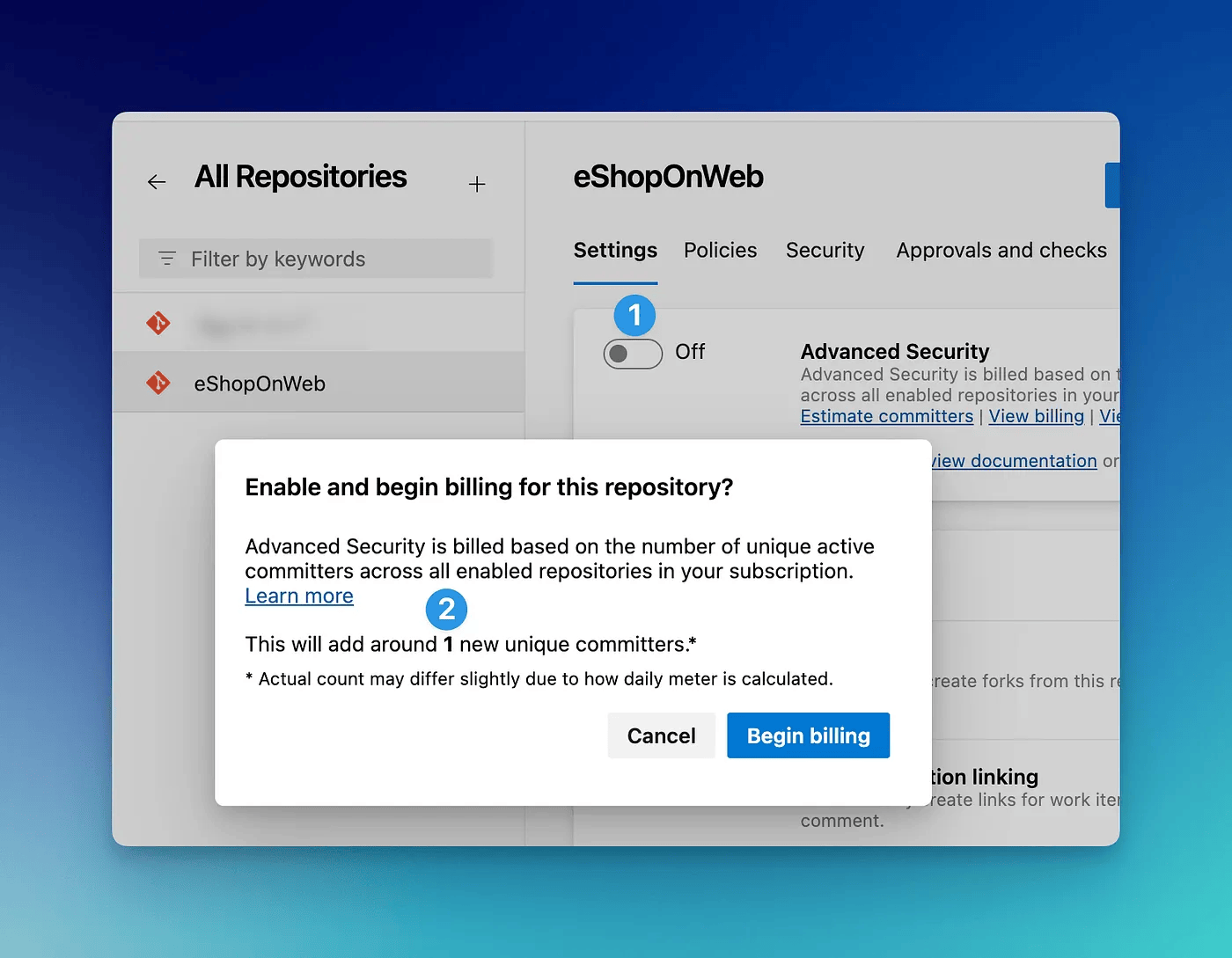
Once you click Begin billing GHAS should be enabled.
If your ADO instance does not have a linked and active subscription, you might get the below error.
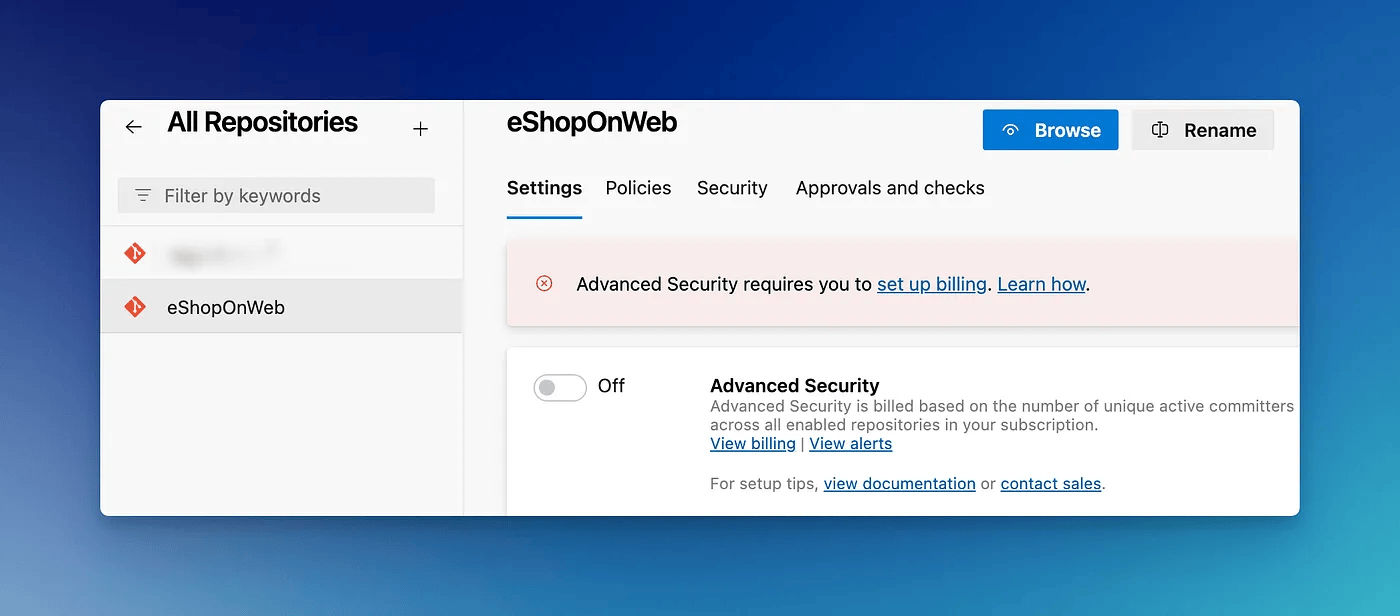
You will need to select an active Azure subscription under the Billing tab under organization settings in ADO.
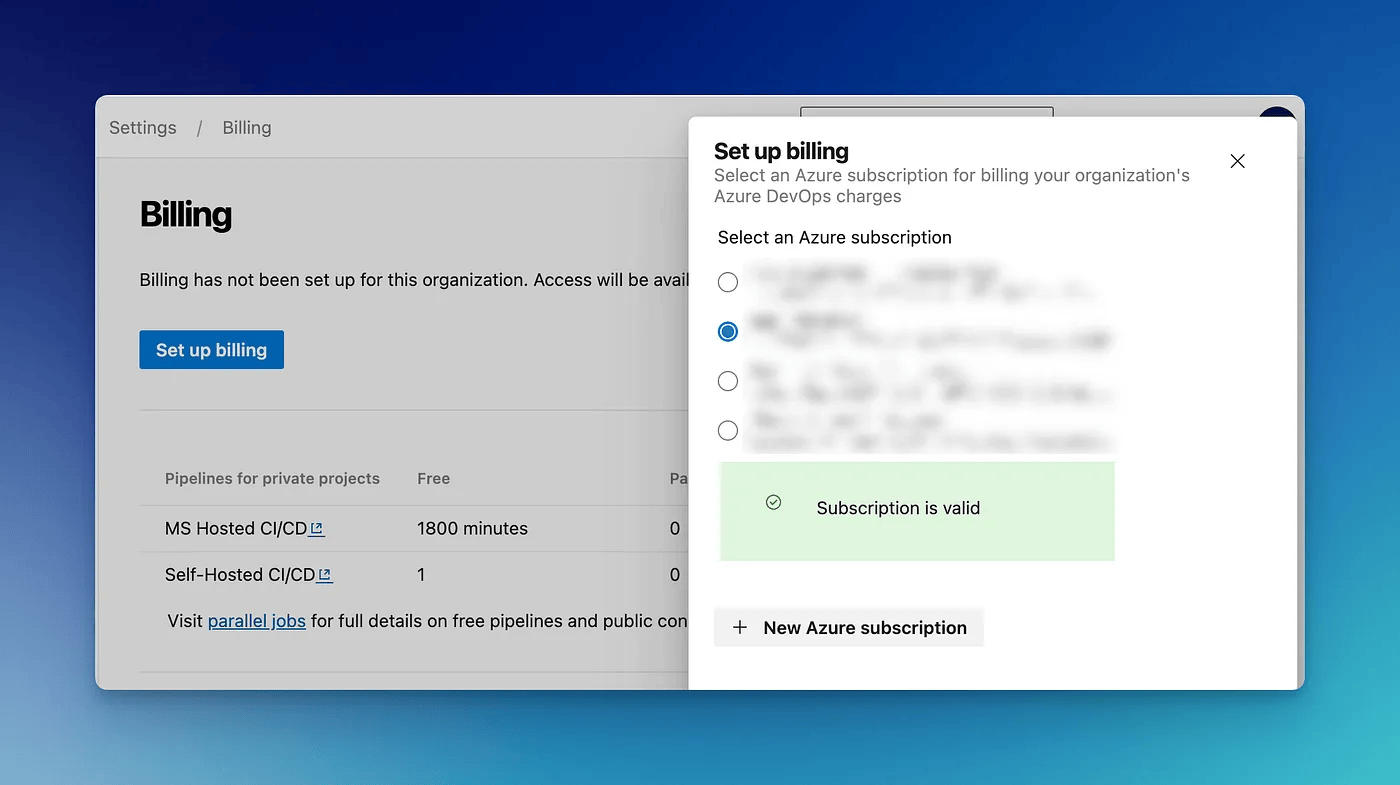
Once you select a valid subscription, you will be able to enable GHAS for the repositories.
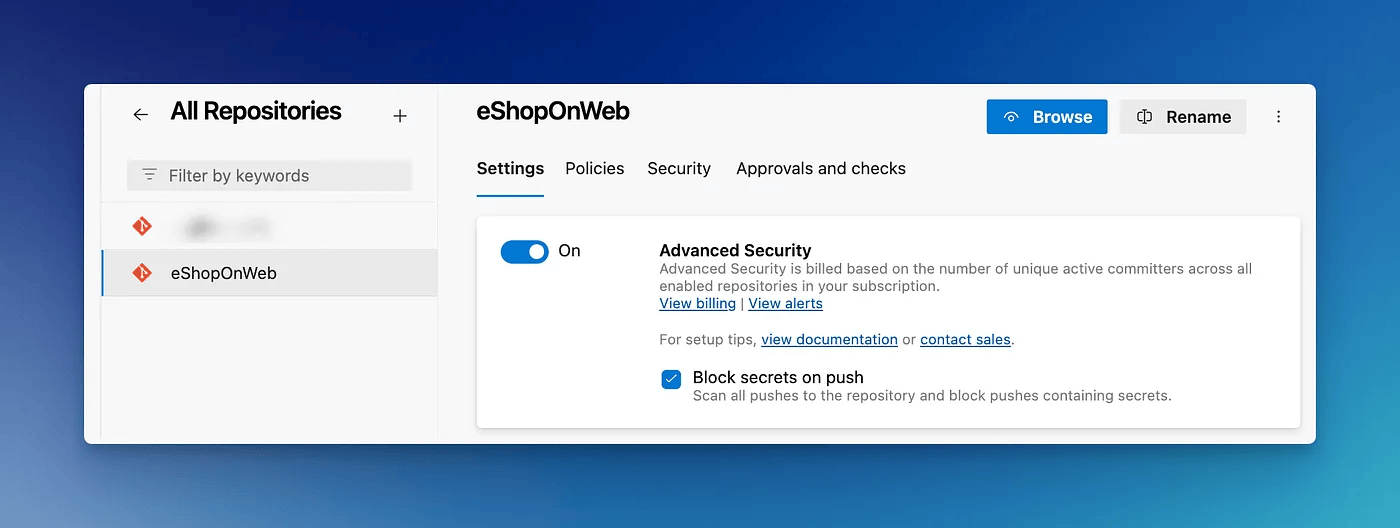
Exploring GHAS features
Block secrets on push
Once you enable GHAS, by default Block secrets on push feature is enabled too. With this setting enabled, ADO will automatically check any incoming pushes for embedded secrets and reject them automatically. Not only works on CLI, but it works on the web interface too.
For a simple test, below I am trying to commit a file with the GitHub API key, and it was rejected.
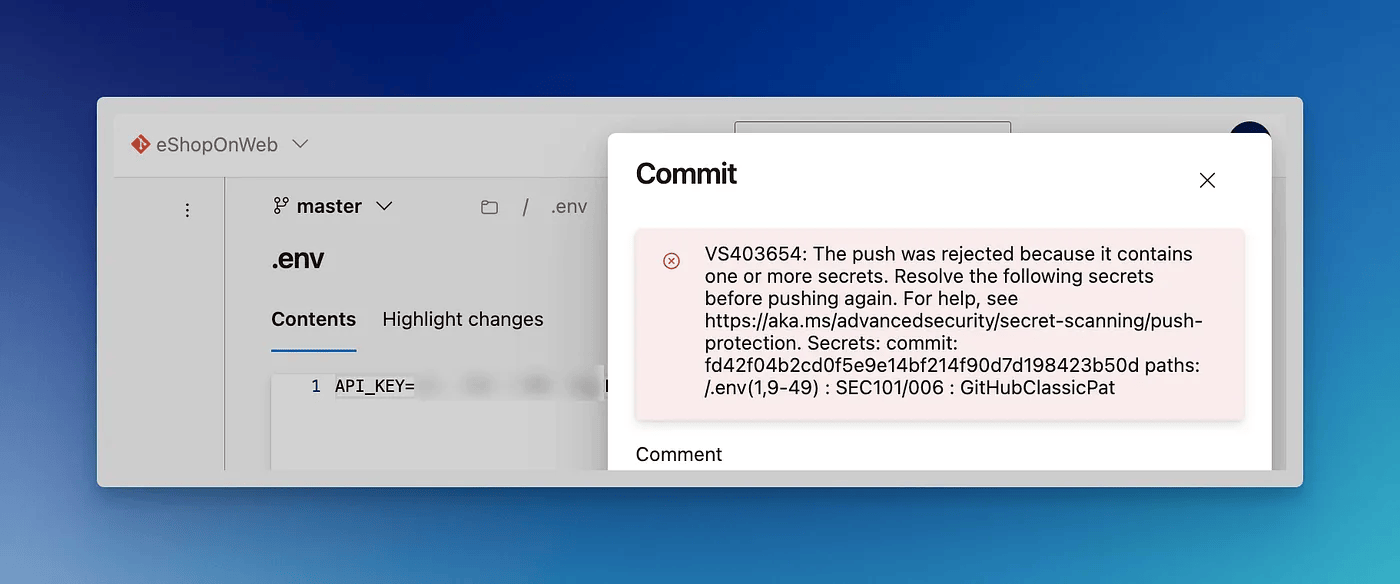
Note that at the time of writing this GHAS supports secrets push protection only for certain service providers. Although secrets from the majority of service providers are supported, I was surprised to see GitLab personal access token is not supported yet.
Although not recommended, there is a way to push a secret that has been blocked. To push, you need to have skip-secret-scanning:true in your commit message.
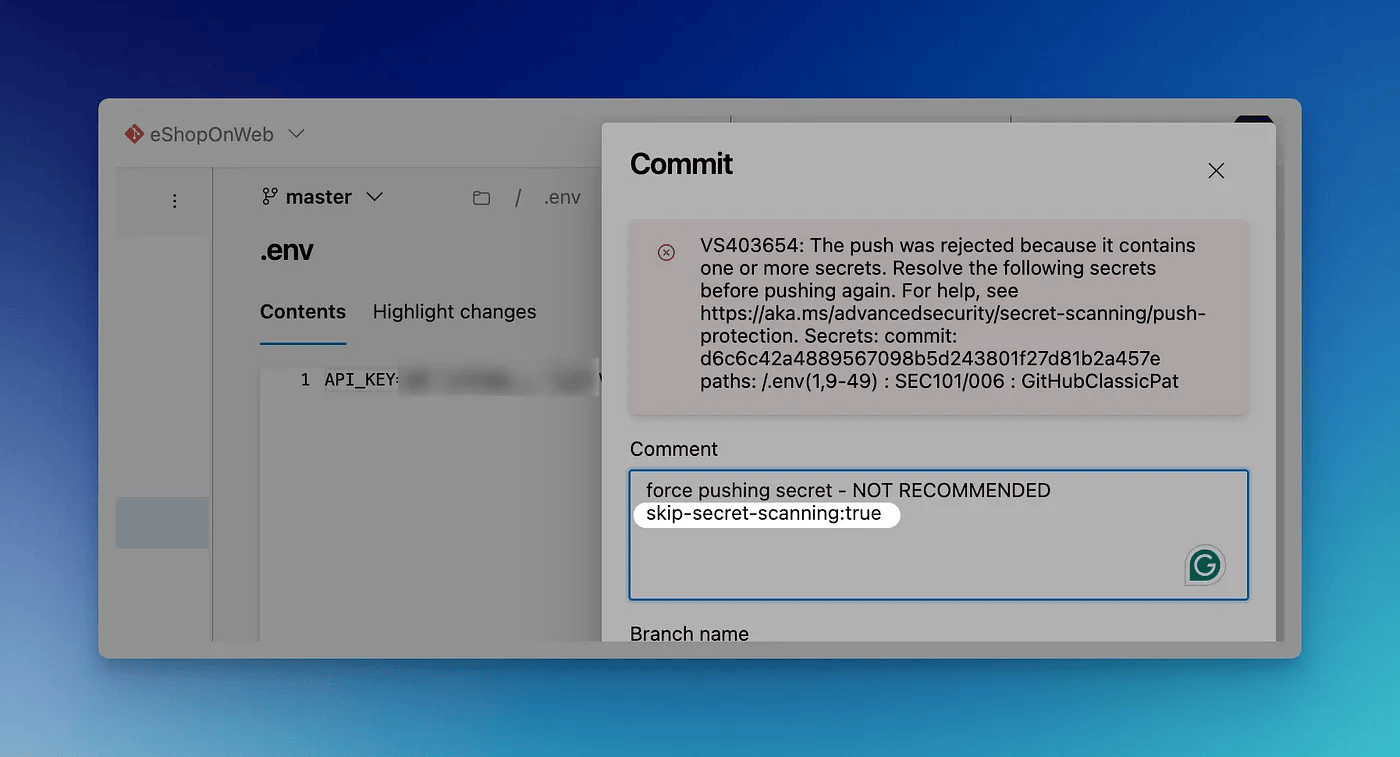
This will allow the secret to be committed, however, it will be caught in the Secret scanning alert (more on that below).
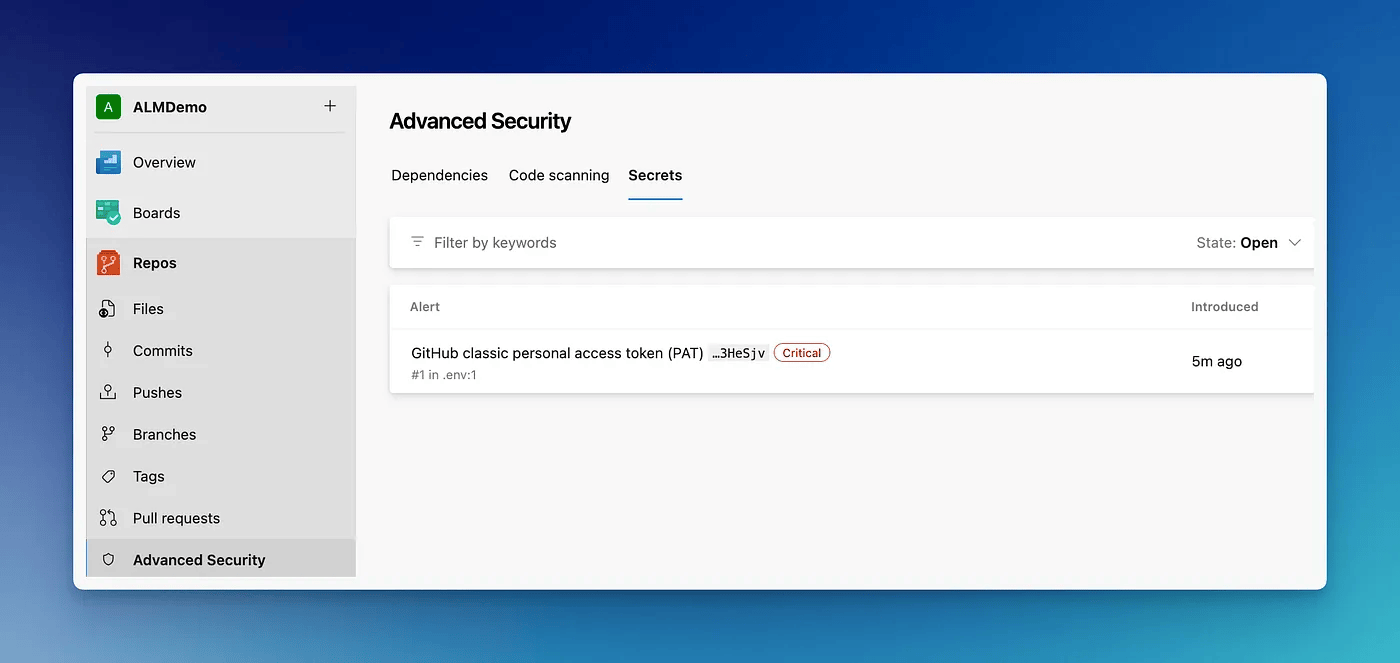
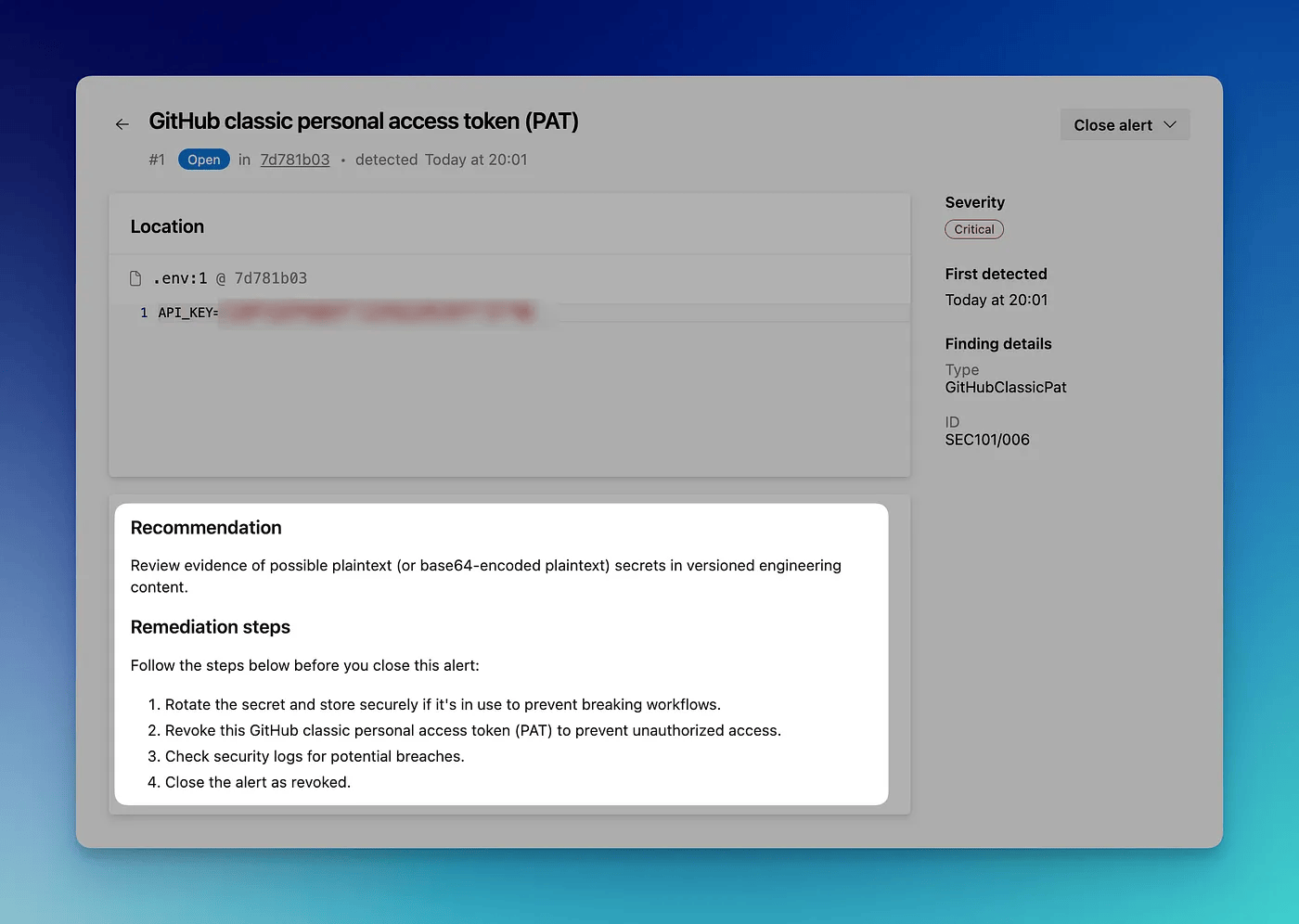
The great thing about GHAS is that clicking on the alert will give you remediation steps too.
Dependency Scanning and Code Scanning
Dependency and Code scanning are additional features of GHAS. Dependency scanning will scan any vulnerabilities in your repo from your open-source dependencies. Code scanning will scan your source code (from supported languages) for vulnerabilities.
Both these tasks are enabled through pipeline tasks. On any GHAS-enabled repo, you will be able to run the pipeline with these tasks and get the status of the repo.
You can create a pipeline and add the tasks for dependency and code scanning.
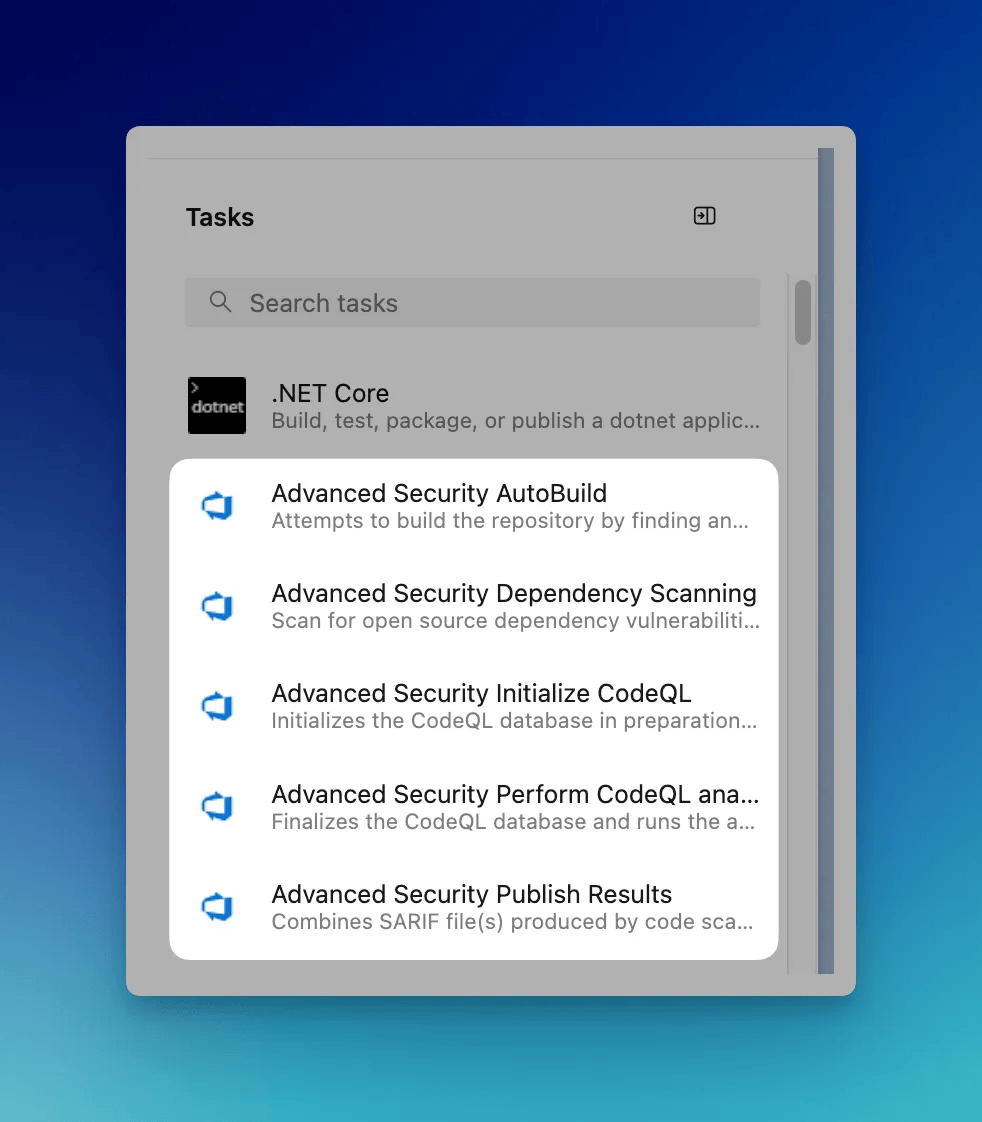
However, this post has already gotten super long than I intended it to be, I will probably do another post and explore both of those functionalities in detail.
Pricing
GHAS for Azure DevOps is a paid product and is available only for Azure DevOps Services. For Azure DevOps Service linked to an Azure Subscription, this will automatically be visible in your billing for subscription. At the time of writing this, it costs 49$ per active committer per month.
That is it for this post. Thank you for reading. 🎉

Utkarsh Shigihalli
Utkarsh is passionate about software development and has experience in the areas of Azure, Azure DevOps, C# and TypeScript. Over the years he has worked as an architect, independent consultant and manager in many countries including India, United States, Netherlands and United Kingdom. He is a Microsoft MVP and has developed numerous extensions for Visual Studio, Visual Studio Code and Azure DevOps.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK
