

Cloud Providers and Anti-CSRF Tokens - DZone
source link: https://dzone.com/articles/safeguarding-web-applications-with-cloud-service-p
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

Safeguarding Web Applications With Cloud Service Providers: Anti-CSRF Tokenization Best Practices
Cloud service providers bolster security with Anti-CSRF tokenization and IDS, strengthening web app defenses against evolving threats such as CSRF attacks.
Cloud services have transformed organizational approaches to security, presenting a range of tools and features to strengthen defenses against evolving threats. This study examines the multifaceted involvement of cloud service providers in enhancing security through Anti-CSRF tokenization and the establishment of effective Intrusion Detection Systems (IDS). Subsequently, it investigates how top cloud service providers specifically aid organizations in implementing and refining Anti-CSRF tokenization strategies to counter Cross-Site Request Forgery (CSRF) attacks, thereby reinforcing web application security.
The study delves into the essential role played by cloud managed service providers in designing, deploying, and managing IDS solutions, illustrating how their expertise and resources contribute to robust threat detection and response capabilities. Begin by assessing your current software development processes and identifying areas where CSRF vulnerabilities exist. Evaluate your existing security measures. Establish clear objectives and targets for integrating Anti-CSRF tokenization and enhancing the software development life cycle (SDLC). Incorporate Anti-CSRF tokenization protocols into the initial phases of the software development lifecycle.
The principle of anti-CSRF tokens, alternatively referred to as synchronizer token patterns or CSRF tokens, involves providing the user's browser with a unique piece of information (token) that must be included in subsequent requests. This token, which is difficult for third parties to guess, is required for the application to process HTTP requests effectively. By verifying the token before processing requests, the system ensures that only the authenticated user can initiate actions within their session.
As an illustration, consider a scenario without CSRF protection: Suppose you operate a web application hosted on www.nowebattacksplease.com. When a user wishes to publish a message on their profile within the application, they fill out a form and click the Submit button.

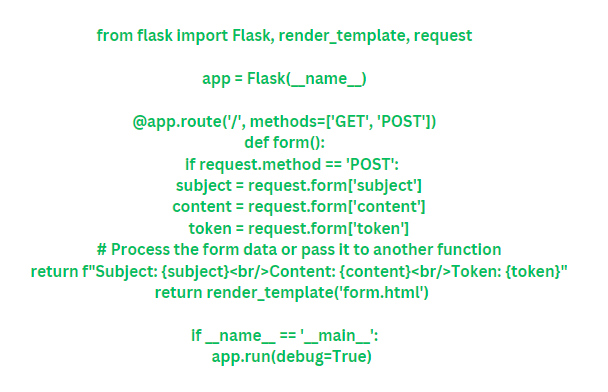
The backend code appears as follows (Python code):
We'll also need to create a template file named form.html in the templates directory with the following content:
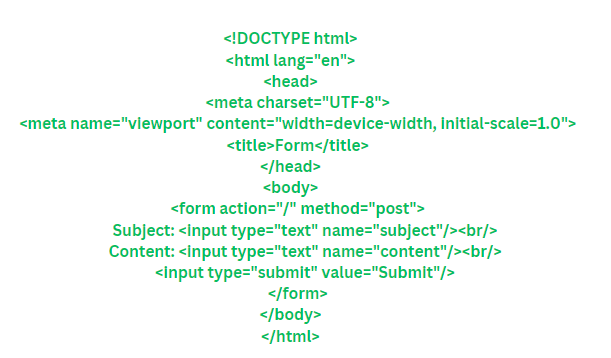
This Python code creates a basic web application using Flask. When you access the root URL (/), it renders the form.html template, which contains the HTML form. When the form is submitted, the data is sent to the server as a POST request, and the server retrieves the form data using the request form in the form() function. Finally, it processes the form data and returns a response.
If the user is authenticated and the attacker is familiar with the request structure, they could potentially exploit a CSRF attack to post an advertisement on the user's profile.
On a vulnerable webpage, this could lead to CSRF if the server mistakenly recognizes the counterfeit request as originating from an authorized user. However, suppose your website employs a basic token-based CSRF prevention method, where the server assigns the token within a session cookie immediately after the user logs in. Subsequently, all form submissions include a concealed field holding the token. Assuming correct token validation, this effectively eradicates the CSRF vulnerability.
You'll also need to create a template file named form.html in the templates directory with the following content:
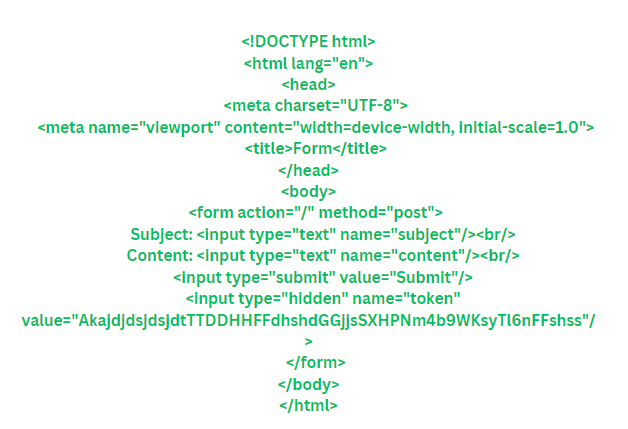
The server must exclusively authorize POST requests originating from the same user, containing precisely the specified token value. By implementing this safeguard, any malicious attempts to conduct CSRF attacks from an unauthorized source are thwarted. Without knowledge of the valid user's current token stored in the cookie, an attacker cannot fabricate HTTP requests successfully. Since the server denies any requests without this token, all unauthorized attack attempts are rendered ineffective.
Cloud services can scale resources up or down based on demand, which can help in handling sudden spikes in traffic or attacks. For example, Cloud MSPs can scale IDS systems up or down based on the evolving needs of your organization. This scalability can prevent resource exhaustion attacks and ensure that security measures remain effective even during peak times. Cloud providers typically offer redundancy and disaster recovery capabilities across multiple geographic regions. This redundancy ensures that data and services remain available even in the event of a localized failure or a malicious attack. They can continuously update their platforms to patch vulnerabilities and improve security. This helps in keeping infrastructure and applications protected against emerging threats.
Services enable granular control over user access to resources, allowing organizations to implement the principle of least privilege. This means that users only have access to the resources necessary for their roles, reducing the risk of unauthorized access and data breaches. Cloud MSPs typically have access to advanced IDS tools and technologies that may be cost-prohibitive for individual organizations to acquire and maintain. These tools often include sophisticated threat intelligence feeds, machine learning algorithms, and anomaly detection capabilities to enhance the effectiveness of the IDS system.
Overall, a cloud infrastructure company can play a crucial role in enhancing the effectiveness of Anti-CSRF tokenization mechanisms by providing scalable infrastructure, built-in security features, managed services, global availability, compliance assistance, integration with development tools, and continuous monitoring and updates.
In summary, cloud services offer a dependable and secure environment for hosting applications and storing data, allowing organizations to concentrate on their primary business objectives. By tapping into the knowledge and infrastructure of cloud services providers, security can be bolstered. Nevertheless, it remains crucial for organizations to augment these inherent security features with supplementary measures and best practices. This holistic approach is essential to safeguard against emerging threats effectively.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK