Zack Whittaker (@[email protected]) - Mastodon
source link: https://mastodon.social/@zackwhittaker
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.


Zack Whittaker@[email protected]
NEW: Belorussian hackers have targeted foreign diplomats in the country since Feb. 2022, at the start of the invasion of Ukraine.
Group targets them by intercepting traffic at the telecom provider level, suggesting government collaboration, per ESET.
Once ESET researchers spotted the hackers in 2022, they have been able to trace back their activities all the way back to 2014.
https://techcrunch.com/2023/08/10/belarus-hackers-target-foreign-diplomats/
The CSRB has released its second ever report on cyber safety, a study of a loosely affiliated hacker group that compromised dozens of well-defended companies with low-complexity attacks. https://www.cisa.gov/resources-tools/resources/review-attacks-associated-lapsus-and-related-threat-groups-report
New, by @carlypage: NCC Group confirms it is laying off more employees, months after cutting 7% of its workforce.
NEW: Researchers set up a network of honeypot computers and watched more than 100 hours of hackers taking them over and using them.
The research gives insight into various types of hackers, their goals and levels of sophistication.
More from @GossiTheDog on the U.K. voter register hack:
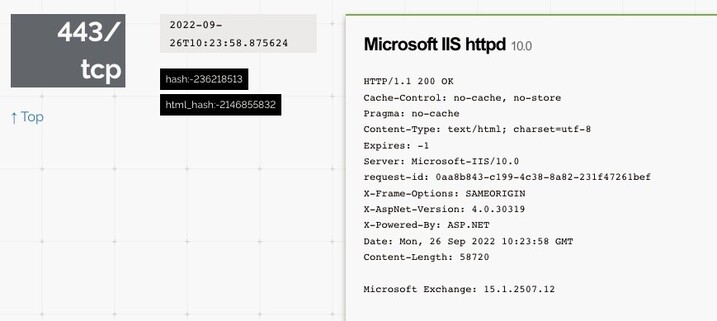
At the time of the cyberattack, the Electoral Commission was running an on-premise Exchange Server vulnerable to ProxyNotShell, a then-unpatched zero-day vulnerability. If exploited, ProxyNotShell can be used to gain "complete compromise" of a victim's network.
#ProxyNotShell in Exchange Server fingered in UK Electoral Commission hack.
TechCrunch found Electoral Commission were using on prem Exchange.
I had a look via @shodan history feature - their Exchange Server, with OWA enabled, was online until later in 2022 (when the incident began) - and didn't have ProxyNotShell patches installed, as Microsoft hadn't released them.
The mitigations MS released were bypassable, as seen in the Rackspace Hosted Exchange hack.
https://techcrunch.com/2023/08/09/parsing-uk-electoral-commission-cyberattack/
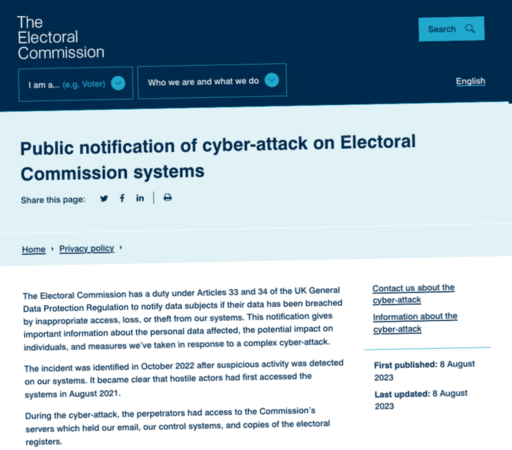
New: A massive cyberattack targeting the U.K. voter register is one of the U.K.’s largest ever hacks, with more than 40 million voters affected.
TechCrunch has marked up the Electoral Commission's cyberattack notice to dissect what was said about the hack, and what was left out.
More: https://techcrunch.com/2023/08/09/parsing-uk-electoral-commission-cyberattack/
Yesterday I published a lengthy story for WIRED about the mystery around radiation spikes that occurred at Chernobyl during Russia's invasion of Ukraine. I've just posted a new edition of my Zero Day publication with additional information, analysis and images.
https://zetter.substack.com/p/radiation-spikes-at-chernobyl-a-mystery
Questions we've asked the U.K. Electoral Commission about the breach of ~40 million voter records:
• Why was there a year-long delay in publicly disclosing the breach from the known point of intrusion?
• Does the EC have the technical ability, such as logs, to determine what, if any, data was exfiltrated from its systems?
• The hackers accessed the EC's email system. Was this an on-premise server or hosted by a third-party? Was this the point of compromise?
More: https://techcrunch.com/2023/08/08/electoral-commission-hack-40-million-uk-voters/
The Electoral Commission has confirmed that as many as 40 million UK voters may be impacted after it fell victim to a "complex cyberattack". The attack was discovered in October (!), but the watchdog says hackers first accessed its systems in August 2021 https://techcrunch.com/2023/08/08/electoral-commission-hack-40-million-uk-voters/
Exclusive: After Russian troops seized control of the Chernobyl nuclear power plant last year, radiation sensors in the region started recording alarming spikes. The official Ukrainian explanation was that the spikes were caused by Russian military vehicles stirring up radioactive dust in the area. But that explanation has been disputed. Now the mystery deepens. Security researcher Ruben Santamarta has discovered suspicious patterns in the sensor data that suggest the data was possibly manipulated to fabricate the radiation spikes. Experts agree with him that it seems the most likely explanation. The question is if the data was manipulated, who did it and why?
Ruben will be presenting his findings on Thursday at the BlackHat security conference and will release a 100-page paper showing his research.
But you can read my detailed story about the findings and mystery surrounding the spikes here:
https://www.wired.com/story/chernobyl-radiation-spike-mystery/
one of the best genres of cyber news story is when someone sees an arXiv preprint paper about an incredible side channel attack via the acoustics of farts
A new, packed ~this week in security~ just went out, with:
• Cloud host assisted APT hackers
• FBI investigating multi-state hospital ransomware attack
• US warns of 'critical compromise' to Air Force comms
• Senate votes to allow weed users to get security clearance
• CISA says 2022's most exploited bug is...
• And a brand new cyber cat.
Sign up/RSS: https://this.weekinsecurity.com
Read online: https://mailchi.mp/zackwhittaker/this-week-in-security-august-6-2023-edition
New, by me: LetMeSpy, a spyware maker based in Poland, said it will shut down and cease operations after a hacker broke in and wiped out its servers.
Radeal CEO Rafal Lidwin, who develops the spyware, did not respond to a request for comment.
More: https://techcrunch.com/2023/08/05/letmespy-spyware-shuts-down-wiped-server/
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK