Researchers discover brute-force attack that can bypass Android phone fingerprin...
source link: https://www.techspot.com/news/98788-researchers-discover-brute-force-attack-can-bypass-android.html
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

Researchers discover brute-force attack that can bypass Android phone fingerprint locks
It doesn't work on iOS devices
By Rob Thubron Today 6:15 AM 7 comments
In brief: We tend to believe that if our Android phones are lost or stolen, a fingerprint lock will ensure that the sensitive data they hold stays safe. But Chinese researchers have found a way to break through this protection by using a brute-force attack.
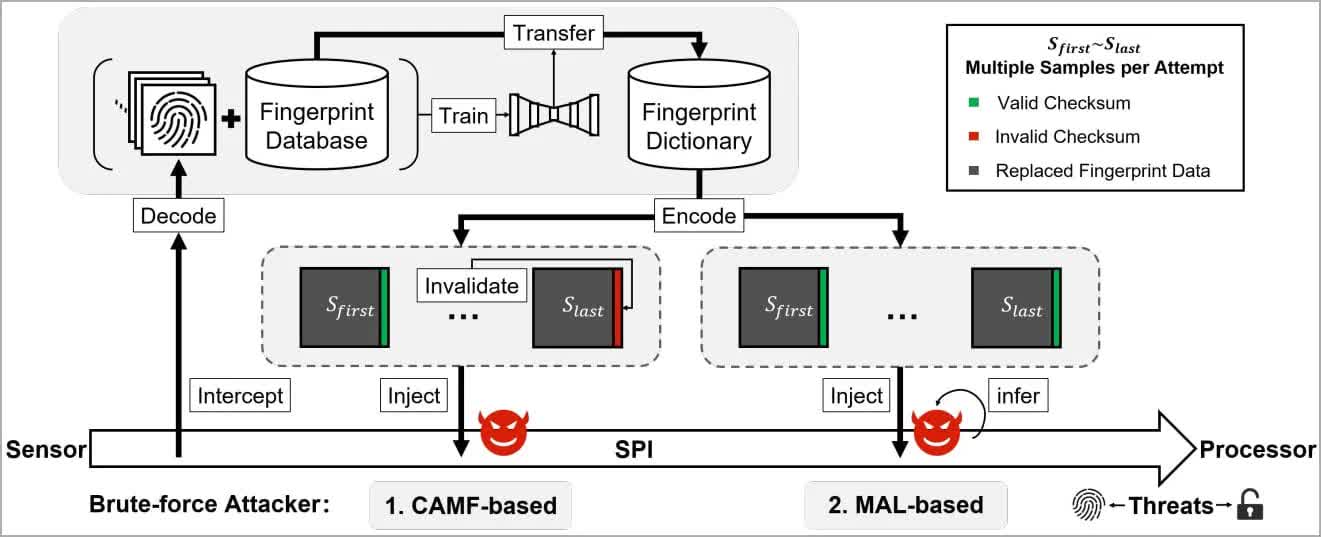
Researchers from Tencent Labs and Zhejiang University found that they could bypass a fingerprint lock on Android smartphones by using a brute-force attack, which is when a large number of attempts are made to discover a password, code, or some other form of security protection.
To protect against brute-force attacks, Android phones usually have safeguards such as limiting the number of attempts a user can make, as well as liveness detection. But the researchers bypassed these by using two zero-day vulnerabilities dubbed Cancel-After-Match-Fail (CAMF) and Match-After-Lock (MAL).
As per Bleeping Computer, it was also discovered that biometric data on the fingerprint sensors' Serial Peripheral Interface (SPI) lacked comprehensive protection, thereby allowing a man-in-the-middle (MITM) attack to steal the fingerprints.
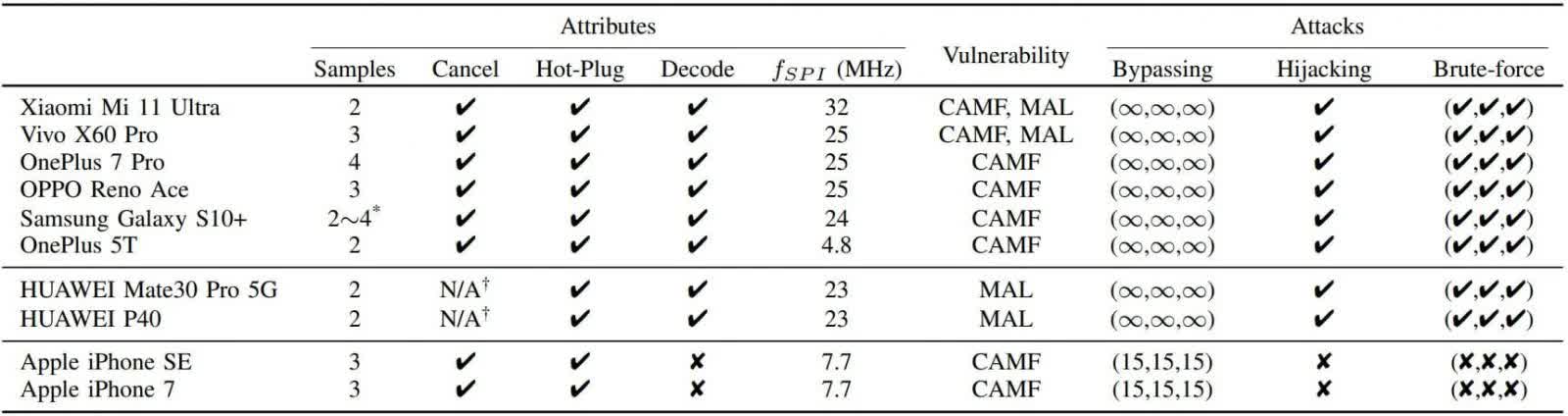
The researchers tested the brute-force attack, called BrutePrint, on ten popular smartphone models. They were able to perform an unlimited number of fingerprint login attempts on the Android and HarmonyOS (Huawei) phones. iOS devices fared much better, allowing just ten additional attempts on the iPhone SE and iPhone 7, bringing the total to 15, which isn't enough for a brute-force attack.
All Android devices were vulnerable to the SPI MITM attack, but it was ineffective against iPhones
According to analysis, BrutePrint could break into a device that has only one fingerprint set up in between 2.9 and 13.9 hours. Those with more than one fingerprint are easier as the attacker has a higher chance of finding a match, so the time for success drop to between 0.66 hours and 2.78 hours.
The good news is that this isn't the easiest attack to pull off. Not only would someone need physical access to a target phone and a some time, but they'd also require access to a fingerprint database from either biometric data leaks or academic datasets. Some hardware is also required, though it only costs around $15. However, the technique could find use with law enforcement and state-sponsored actors.
Masthead credit: Daniel Romero
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK