

iTWire - Imperva red team discovered a vulnerability in TikTok that can reveal u...
source link: https://itwire.com/business-it-news/security/imperva-red-team-discovered-a-vulnerability-in-tiktok-that-can-reveal-user-activity-and-information.html
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

Thursday, 04 May 2023 08:16
Imperva red team discovered a vulnerability in TikTok that can reveal user activity and information Featured
By David HeathIThe Imperva Red Team recently discovered a vulnerability in TikTok that could allow attackers to monitor users' activity on both mobile and desktop devices.
The vulnerability, which has now been fixed, was caused by a window message event handler that did not properly validate the message origin, providing attackers access to sensitive user information.
The PostMessage API (also known as the HTML5 Web Messaging API) is a communication mechanism that enables secure cross-origin communication between different windows or iframes within a web application. The API (Application Programming Interface) allows scripts from separate origins to exchange messages, overcoming the restrictions imposed by the Same-Origin Policy, which typically limits data sharing between different sources on the web.
The API consists of a method, window.postMessage(), and an event message. The postMessage() method is used to send a message from the source window to the target window or iframe, while the message event is triggered on the receiving end when a new message is received.
According to the Imperva report, “the first step in discovering the vulnerability was to identify all the message event handlers in TikTok's web application. This involved a comprehensive analysis of the source code in locating instances where the PostMessage API was being used.
“Once all the message event handlers were identified, we proceeded to carefully read and understand the code for each handler. This allowed us to determine the purpose of each handler and evaluate the security implications of processing untrusted messages.”
During the code analysis, the team came across a script in TikTok's web application that appeared to be involved in user tracking. Specifically, the script contained a message event handler responsible for processing incoming messages of type "simulator:verify." It seemed that this handler was used for a client-side caching system.
Upon closer inspection, it was noticed that this message event handler did not properly validate the origin of incoming messages, making it susceptible to exploitation by malicious actors. Additionally, the handler was found to send back sensitive user information in response to these messages, further exacerbating the risk.
The following is an excerpt from the vulnerable source code responsible for processing incoming messages and sending information back to the sender.
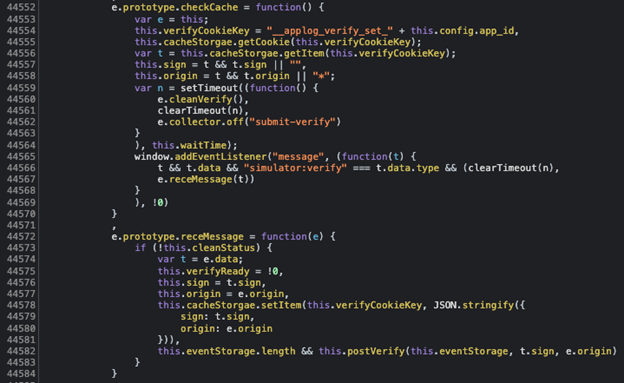
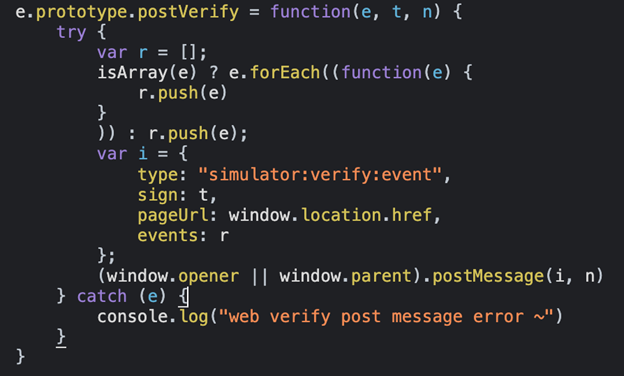
As demonstrated in the code snippet above, the receiveMessage function fails to verify the origin of the incoming message. The function also invokes the postVerify method, which sends back sensitive information, including the current TikTok URL and a list of events corresponding to various actions that can be performed on the platform. This information is sent to either the window.opener or window.parent, which could potentially be any website.
During the investigation, it was also discovered that by redirecting the user to the /profile endpoint on TikTok, the platform automatically redirects the user to their profile page. This action inadvertently leaks the user's TikTok username, compromising their privacy.
By exploiting this vulnerability, attackers could send malicious messages to the TikTok web application through the PostMessage API, bypassing the security measures. The message event handler would then process the malicious message as if coming from a trusted source, granting the attacker access to sensitive user information.
Exploiting this vulnerability could allow attackers to gain access to various types of TikTok users' information, including:
- User's device: Information about the user's device, such as device type, operating system, and browser details, could be accessed by the attacker.
- Videos viewed: Attackers could monitor which videos the user viewed on the platform, potentially revealing the user's interests and preferences.
- Duration of views: In addition to the videos viewed, attackers could also gather information about the duration of views, providing further insight into user behavior and engagement.
- User's account information: Personal information associated with the user's TikTok account, such as username, videos, and other account details, could be exposed to the attacker.
- Search queries: Another piece of information that could be leaked through this vulnerability is the user's search queries. By accessing the TikTok URL, attackers could view the search terms the user has entered, revealing their interests and potentially sensitive information.
This information can be used for malicious purposes such as targeted phishing attacks, identity theft, or blackmail.
The Imperva Red Team notified TikTok of the vulnerability, which was promptly fixed and Imperva would like to thank TikTok for their quick response and cooperation.
This disclosure serves as a reminder of the importance of proper message origin validation and the potential risks of allowing communication between domains without appropriate security measures.
Imperva created a video to explain the vulnerability. It’s available here.
Read 522 times
Please join our community here and become a VIP.
Subscribe to ITWIRE UPDATE Newsletter here
JOIN our iTWireTV our YouTube Community here
BACK TO LATEST NEWS here
GARTNER MARKET GUIDE FOR NDR 2022
You probably know that we are big believers in Network Detection and Response (NDR).Did you realise that Gartner also recommends that security teams prioritise NDR solutions to enhance their detection and response?
Picking the right NDR for your team and process can sometimes be the biggest challenge.
If you want to try out a Network Detection and Response tool, why not start with the best?
Vectra Network Detection and Response is the industry's most advanced AI-driven attack defence for identifying and stopping malicious tactics in your network without noise or the need for decryption.
Download the 2022 Gartner Market Guide for Network Detection and Response (NDR) for recommendations on how Network Detection and Response solutions can expand deeper into existing on-premises networks, and new cloud environments.
PROMOTE YOUR WEBINAR ON ITWIRE
It's all about Webinars.Marketing budgets are now focused on Webinars combined with Lead Generation.
If you wish to promote a Webinar we recommend at least a 3 to 4 week campaign prior to your event.
The iTWire campaign will include extensive adverts on our News Site itwire.com and prominent Newsletter promotion https://itwire.com/itwire-update.html and Promotional News & Editorial. Plus a video interview of the key speaker on iTWire TV https://www.youtube.com/c/iTWireTV/videos which will be used in Promotional Posts on the iTWire Home Page.
Now we are coming out of Lockdown iTWire will be focussed to assisting with your webinars and campaigns and assistance via part payments and extended terms, a Webinar Business Booster Pack and other supportive programs. We can also create your adverts and written content plus coordinate your video interview.
We look forward to discussing your campaign goals with you. Please click the button below.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK
