
6

RouterOS 抓包并用Wireshark分析
source link: https://www.taterli.com/9297/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

RouterOS 抓包并用Wireshark分析 – TaterLi 个人博客
RouterOS 抓包并用Wireshark分析
RouterOS 抓包并用Wireshark分析
RouterOS本身集成抓包功能,但是路由器上储存有限,而且不好分析,比较好的方法就是抓包,转发至tcpdump,然后做成pcap,再分析.
在服务器运行tcpdump.
tcpdump -i ens3 'udp port 37008' -w capture.pcap在Tools->Packet Sniffer设置过滤器,以及设置接收服务器,勾线只发送过滤流量.
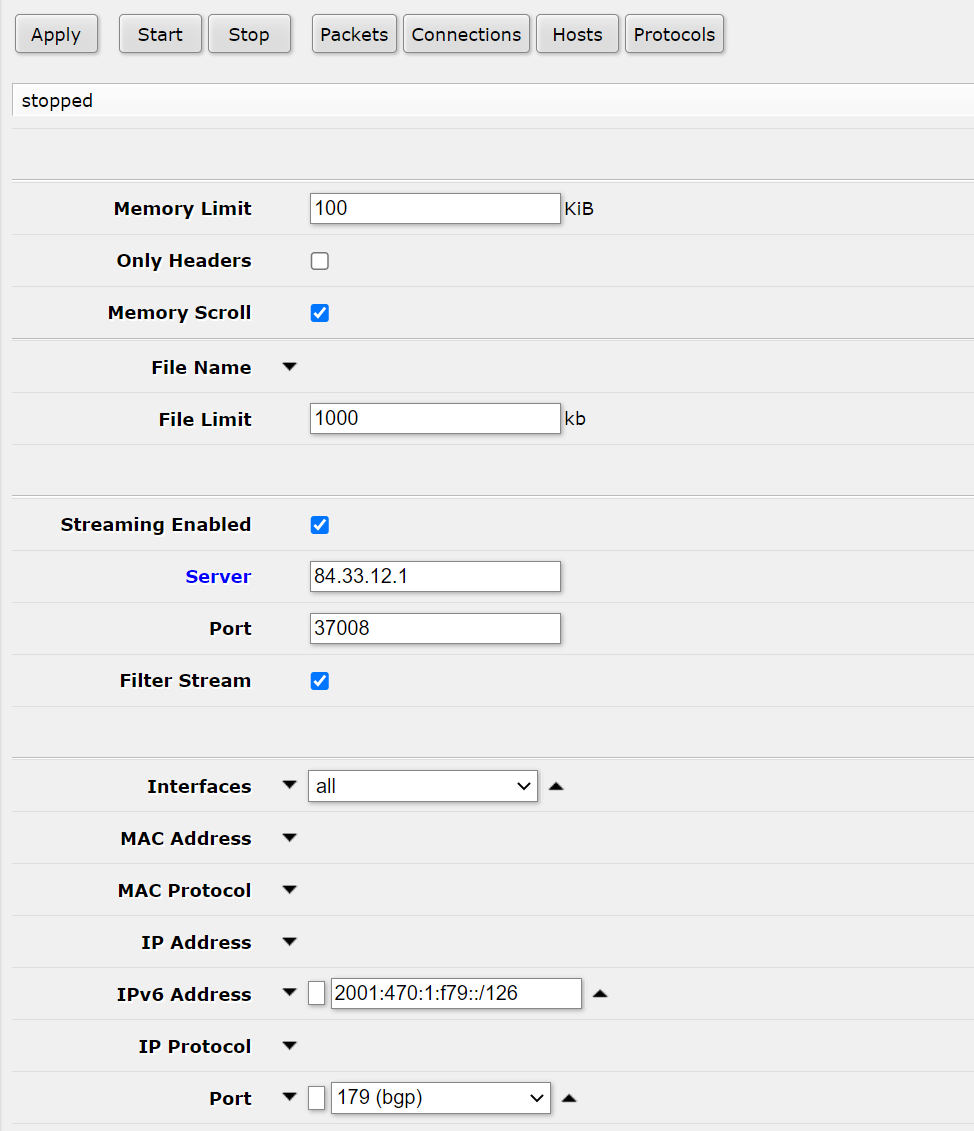
然后看到抓到结果,第一层是UDP,从公网发来的,后面是重包装的.
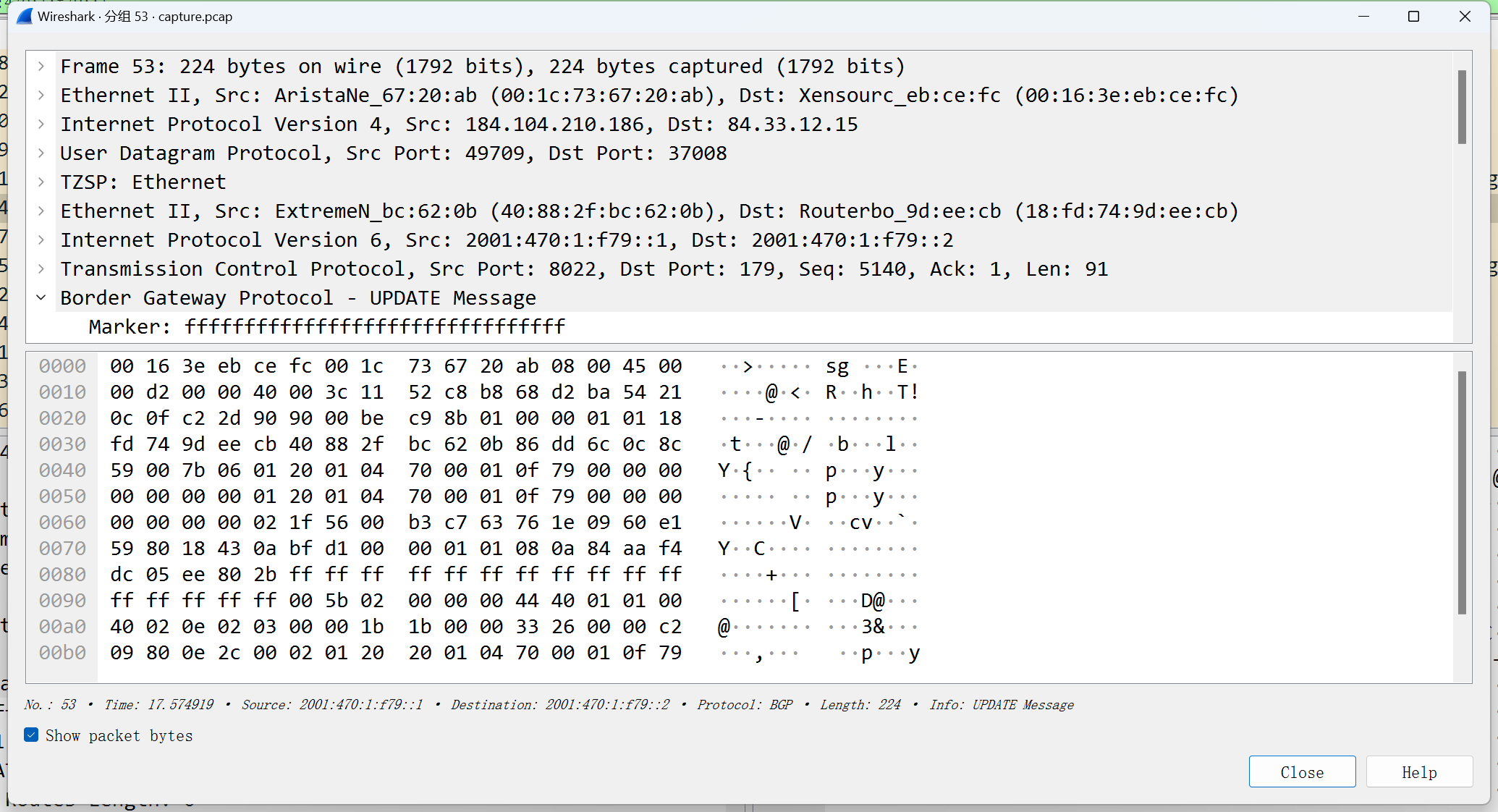
其实就是简单的重包装数据.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK