

Multi-repository enablement: effortlessly scale code scanning across your reposi...
source link: https://github.blog/2023-04-17-multi-repository-enablement-effortlessly-scale-code-scanning-across-your-repositories/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

Multi-repository enablement: effortlessly scale code scanning across your repositories
We’ve gotten great feedback on default setup, a simple way to set up code scanning on your repository. Now, you have the ability to use default setup across your organization's repositories, in just one click.
In January, we launched default setup, a new way to enable code scanning. Default setup has been a game changer, allowing you to enable code scanning on your repository in just a few clicks, without using a .yaml workflow file. We’ve gotten great feedback from the security community, and the numbers speak for themselves. Almost half of all new code scanning implementations now utilize default setup to enable code scanning and 96% of users who try default setup continue to use the feature today.
In the last month, we’ve expanded our default setup feature to offer you greater flexibility and ease of enablement. These enhancements include the ability to scale code scanning across specific groups of repositories or even your entire organization, additional query pack configurations, and the ability to use an API to leverage default setup.
First, let’s take a deeper look at the highly requested feature, multi-repository enablement, for code scanning default setup.
Multi-repository enablement
Multi-repository enablement allows you to easily enable many security features, including default setup for code scanning, directly from the security coverage page in security overview. This feature offers greater flexibility and granularity than the “Enable all” functionality, which enables a security feature for all repositories in your organization. With multi-repository enablement, you can now effortlessly filter for repositories on the security coverage page by attributes, such as team or repository topic, and enable code scanning default setup for only those repositories with just a few clicks.
Additionally, you have the option to exclude repositories where you don’t want code scanning default setup, or other security features, enabled by using the negation symbol (“-“) when filtering. This is particularly useful for excluding repositories such as test or documentation repositories. These options allow you to scale code scanning effortlessly, ensure that the feature is only enabled on the repositories that matter most, and gain greater visibility into your application security surface.
To get started using multi-repository enablement, go to the security coverage page in security overview.
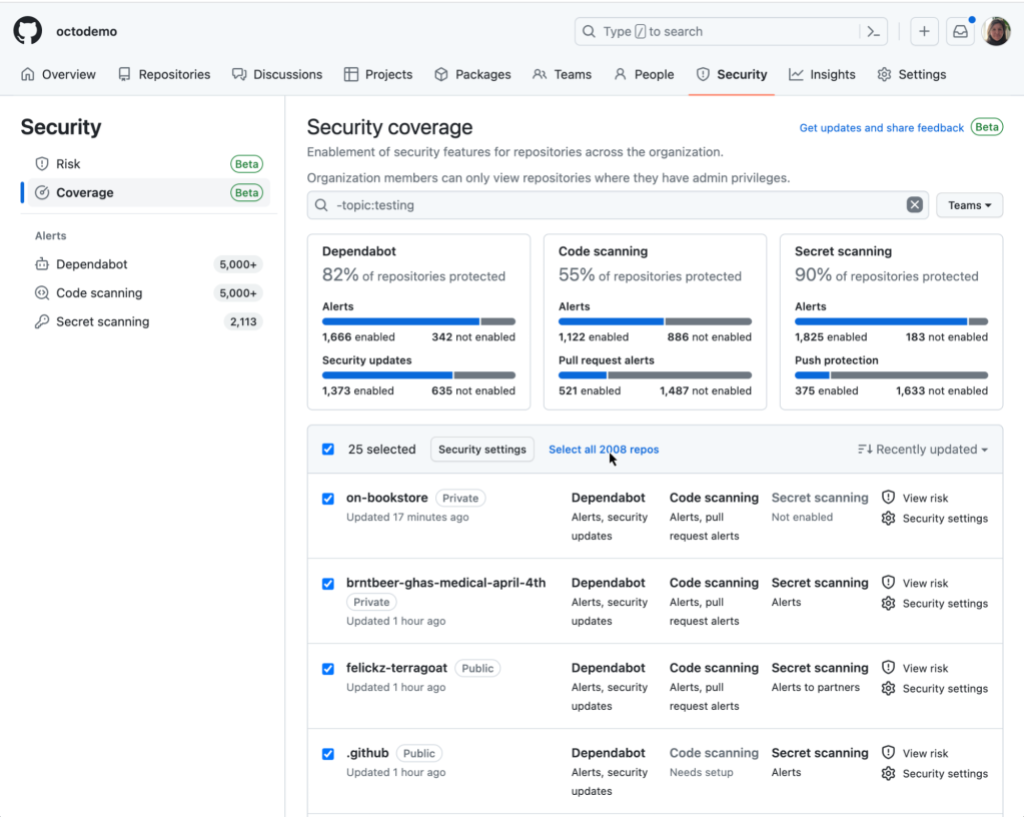
There, you’ll be able to select multiple repositories by checking the checkbox next to each repository. To select all repositories on the page, click the checkbox in the header row, and then click the “Select all repos” hyperlink to select more than 25 repositories.
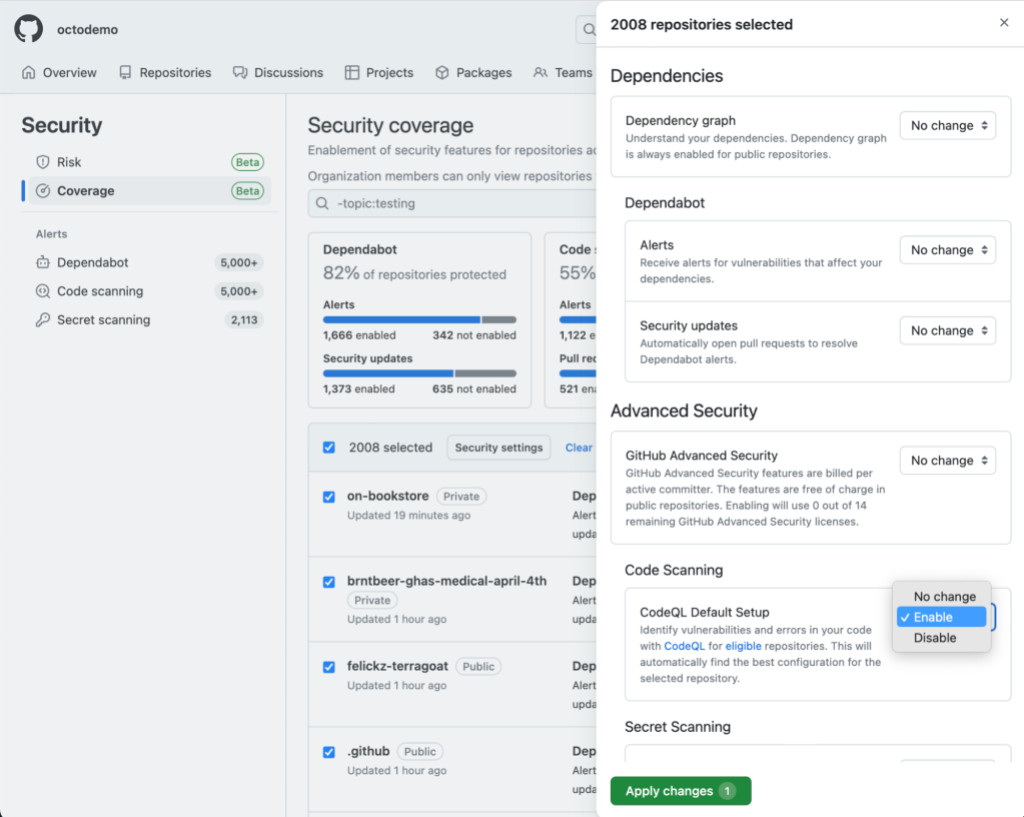
Next, click the “Security settings” button in the header row to choose which security features to enable/disable by selecting the relevant drop-downs in the enablement panel. The settings will apply to all eligible repositories that you selected in the previous step. Note: for those security feature drop-downs that say “No change,” the feature’s enablement status will not be modified. If the security feature was previously enabled for some repositories and not others, the enablement state will remain this way after submitting your changes. Finally, click “Apply changes” to submit your changes.
Enable all for code scanning
Along with the new multi-repository enablement feature, we also offer a one-click option to enable code scanning default setup for all eligible repositories in your organization. To use this option, navigate to the “Code security and analysis” section on the “Settings” tab of your organization. There, you’ll see an option to “Enable all” for code scanning default setup, in the same way we have for other GitHub Advanced Security products.
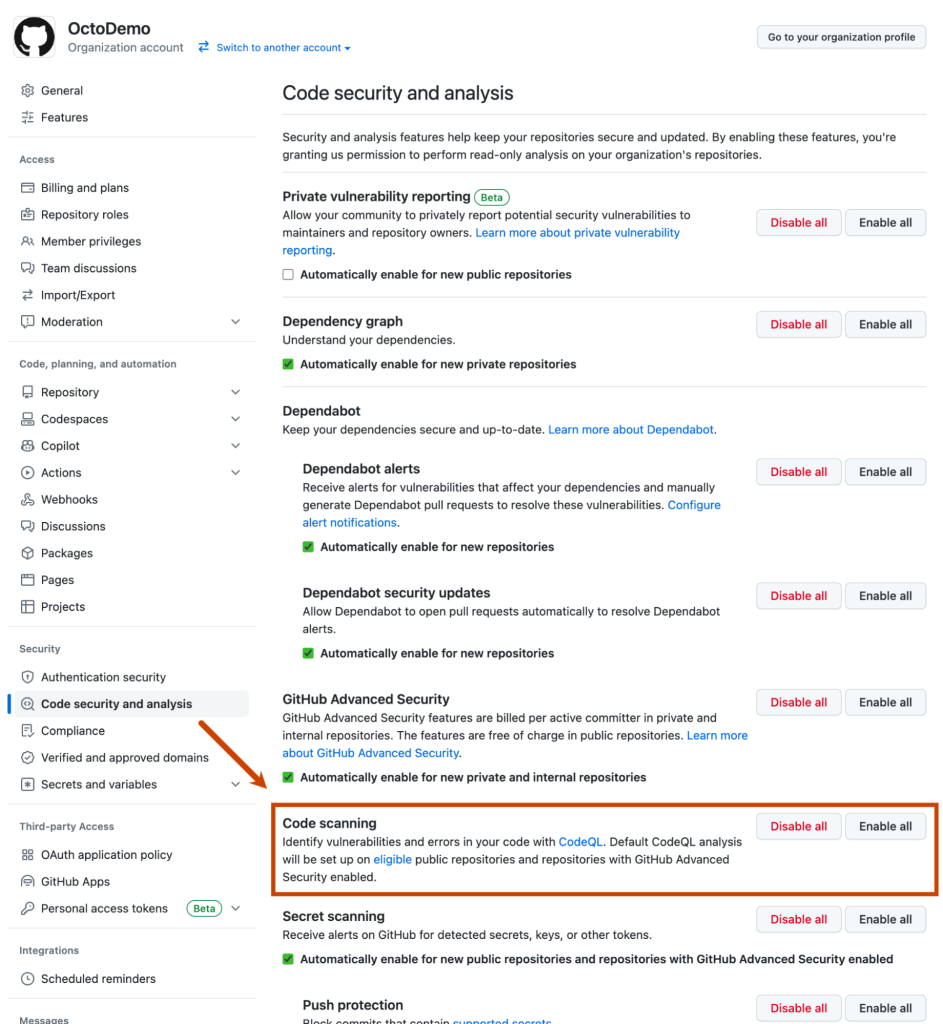
Clicking “Enable all” will automatically set up code scanning’s default setup on all eligible repositories in the organization. As a reminder, default setup automatically uses the most up-to-date starter workflow to find the best configuration for each repository. For information on how to see which repositories are enabled, please see our documentation.
Default setup improvements
We’ve also been working to enhance the default setup experience at the repository level. We have recently added the ability to use the extended query suites for analysis. This query suite can be selected during setup or changed at any time by viewing and editing your CodeQL configuration.
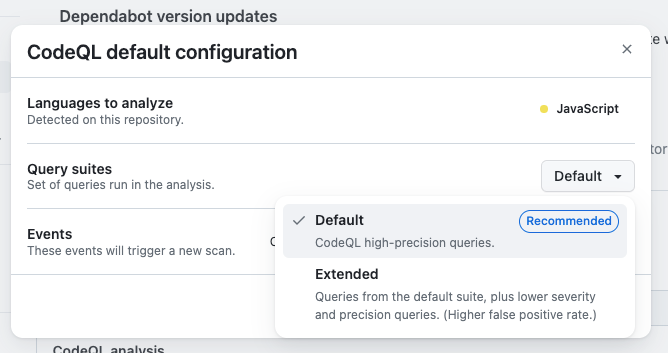
Our extended suite includes the same high precision queries as our default suite, but also includes lower severity and experimental queries. This is useful if you’d like to see a wider range of alerts.
We’ve also shipped an API for repositories to programmatically enable code scanning’s default setup. This can be used to onboard a repository to code scanning, specify which query suite the configuration should use, view the current configuration, and offboard the repository from default setup.
These improvements are meant to give you more flexibility in how you can leverage default setup to meet your specific use case. We have a number of other exciting enhancements on our roadmap for default setup, including support for additional languages and additional customization options, so watch this space for future announcements.
Learn more about GitHub security solutions
GitHub is committed to helping build safer and more secure software without compromising on the developer experience. To learn more or enable GitHub’s security features in repositories, check out the getting started guide.
The GitHub Insider Newsletter
Get the best of GitHub. Once a month. Directly to your inbox.
SubscribeMore on code scanning

Multi-repository variant analysis: a powerful new way to perform security research across GitHub
Multi-repository variant analysis lets you scale security research across thousands of repositories, giving you a powerful tool to find and respond to newly discovered vulnerabilities.
Application security orchestration with GitHub Advanced Security
Learn how teams can leverage the power of GitHub Advanced Security’s code scanning and GitHub Actions to integrate the right security testing tools at the right time.
3 ways to meet compliance needs without slowing down agility
Learn how to enable developer productivity and collaboration while staying secure and compliant. Stay compliant without slowing down your business. From security to CI/CD, automate every step of your software workflow—so your developers can stay focused on what matters most: building.
More on CodeQL

CodeQL zero to hero part 1: the fundamentals of static analysis for vulnerability research
Learn more about static analysis and how to use it for security research! In this blog post series, we will take a closer look at static analysis concepts, present GitHub’s static analysis tool CodeQL, and teach you how to leverage static analysis for security research by writing custom CodeQL queries.
Improvements to CodeQL’s data flow library for C++
These changes will improve the experience for custom query authors and enable better precision in some of our standard queries. Learn how to enable them for your custom queries.
Multi-repository variant analysis: a powerful new way to perform security research across GitHub
Multi-repository variant analysis lets you scale security research across thousands of repositories, giving you a powerful tool to find and respond to newly discovered vulnerabilities.
Recommend
-
 45
45
README.md Zephyr ?️ Effortlessly sync UserDefaults over iCloud
-
 23
23
README.md Docute Effortlessly documentation done right. Features No build process, website is generated on the fly. A sim...
-
 22
22
README.md Rendora
-
 24
24
README.md
-
 11
11
Multi-Cloud Networking: Overcoming Challenges for Data Across Clouds March 29, 2021 Ben Stiles
-
 4
4
VMworld ...
-
 7
7
Codespaces for multi-repository and monorepo scenariosWe’re releasing exciting improvements that will streamline your Codespaces experience when working with multi-repository projects and monorepo...
-
 3
3
Multi-repository Support Released! Jessie Houghton
-
 6
6
Managing Data Actions / Multi Actions in File Repository Here is the new and most awaited feature in SAP Analytics Cloud – Data Actions part has been released and with no doubt it’s really useful on Security part of S...
-
 5
5
Effortlessly plan meetings across time zonesSort by: Hi there Product Hunters! 🚀 In these times of globally distributed teams, it’s common to find yourself working with people in several different time zones. Whe...
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK