

MyloBot 2022 – Evasive botnet that just sends extortion emails?
source link: https://minerva-labs.com/blog/mylobot-2022-so-many-evasive-techniques-just-to-send-extortion-emails/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

MyloBot 2022 – Evasive botnet that just sends extortion emails?
MyloBot was first detected in 2018 and was one of the most evasive Botnets at the time. According to various reports, it incorporated different techniques such as:
- Anti VM techniques
- Anti-sandbox techniques
- Anti-debugging techniques
- Wrapping internal parts with an encrypted resource file
- Code injection
- Process hollowing – a technique in which an attacker creates a new process in a suspended state, and later replaces that process’s code with the the malicious one in order to remain undetected.
- Reflective EXE – executing EXE files directly from memory, without having them on disk.
- Delaying mechanism of 14 days before accessing its command-and-control servers.
We recently found a 2022 version of MyloBot and decided to check whether and how this sophisticated botnet has evolved and were quite surprised, as it would appear that not much has changed since 2018. Several Anti – Debugging and Anti – VM techniques have disappeared and more injection techniques are now being implemented but, ultimately, the second stage payload downloaded from the C&C server is used to send Extortion emails. But let’s dig into the analysis and talk about the most interesting techniques used in our sample.
First Stage of the Attack
The first tricky Anti-Debugging technique used by the author is setting up an unhandled exception filter using “SetUnhandledExceptionFilter”. Usually, when an exception occurs and no exception handler is registered, the kernel32!UnhandledExceptionFilter() function is called. Using “SetUnHandledExceptionFilter” makes it possible to register a custom unhandled exception filter. But if the program is being debugged, the custom filter will not be called, and the exception will be passed to the debugger. This means that the threat actor can register its real payload in a custom exception filter and hide it from analyst eyes.
Another significant technique used in the first stage of the attack is a call to the “CreateTimerQueueTimer” WINAPI function. According to the documentation, this function “Creates a timer-queue timer. This timer expires at the specified due time, then after every specified period. When the timer expires, the callback function is called.” Which is exactly what is happening in our sample.
In the callback function the author triggers the UnhandledExceptionFilter by dividing by zero, which triggers the custom unhandled exception filter to be called.
Later, after ensuring that it is not being debugged, MyloBot looks for the ‘MMZ’ resource, which is an encrypted executable. If the resource is found, it loads it into the memory and decodes it:
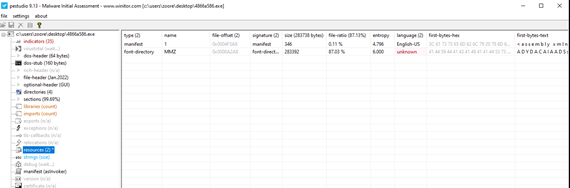
Figure 1 – First stage resources
The decoded executable is injected into a newly running in-suspended-state process. This process is an instance of the original executable whose memory was unmapped and replaced with the decoded resource file, a technique called Process Hollowing.
Second Stage of the Attack – decoded resource
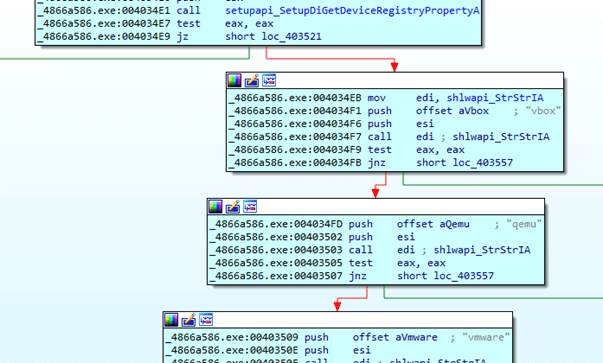
With the resuming thread of the second stage hollowed process it performs an Anti-VM check using SetupDiGetClassDevs, SetupDiEnumDeviceInfo and SetupDiGetDeviceRegistryProperty to query the friendly name of all devices present on the current system and checks for the the strings VMWARE, VBOX, VIRTUAL HD and QEMU within the name:
Next, it checks for persistent software/other persistent malware running on the endpoint by querying subkeys of:
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run
- HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
If any subkey is found and that subkey name does not relate to “Microsoft”, the malware queries its value, checks if the value contains the ‘.exe’ extension, checks if the file exists and if it is currently running. If it is running, it terminates it. This is most likely in order to terminate other malware or utilities running on the endpoint.
The second stage executable then creates a new folder under C:\ProgramData . It looks for svchost.exe under a system directory and executes it in suspended state. Using an APC injection technique, it injects itself into the spawned svchost.exe process.
Third Stage of the Attack – svchost.exe
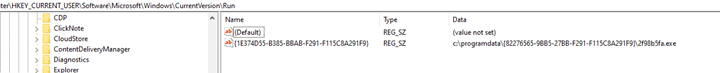
This stage is responsible for creating persistency. First, it writes the first stage executable to the created folder, after that, it creates a registry key under HKCU\Software\Microsoft\Windows\CurrentVersion\Run with the path to the written file as a value:
Next, it executes the written file. It checks running processes and looks for a 64bit process. When it finds it, it injects a 90-byte function into the process and a path to the written file. In this stage the injection is performed using the CreateRemoteThread technique. After some delay, the injected 64bit process function will execute the path that was written. If no 64bit processes were found, the process runs notepad.exe and injects into that.
Fourth Stage of the Attack
The file used in this stage is a copy of the first stage file. However, this time its purpose is to contact a C&C server, download the next stage executable (and an update.txt file in some cases) and execute it.
Fifth Stage of the Attack
When a file is downloaded and executed on the victim’s endpoint, we see again the previously reviewed evasion patterns. It uses a “SetUnHandledExceptionFilter” as the Anti-Debugger, “CreateTimerQueueTimer” for a callback function execution, division by zero to trigger “UnhandledExceptionFilter” and encrypted resource loading and decrypting. One thing that is different in this stage is the resource itself, as we can see it is not the same as the previous:
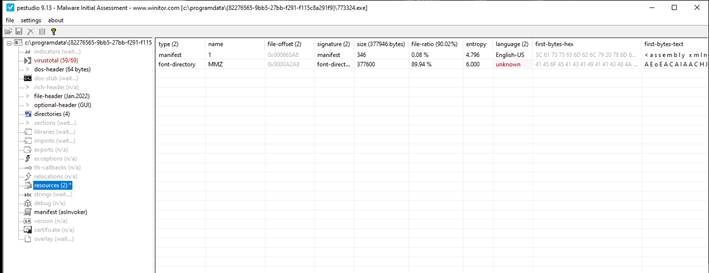
Figure 5 – Downloaded payload resources
It uses the previously mentioned Process Hollowing technique to inject the decoded code into a new process and executes it.
The Hollowed process first checks if a file named “update.txt” exists. If it does, it reads the file into the process memory. Then, it runs a 64bit cleanmgr.exe process and injects the whole payload into it using a CreateRemoteThread technique. If the cleanmgr.exe file does not exist, it uses a svchost.exe file instead:
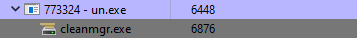
Sixth Stage of the Attack – downloaded payload
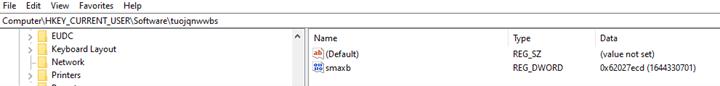
Running as cleanmgr.exe, a malicious payload first uses an additional Timing Anti-Debugging technique. When a process is traced in a debugger, there is a huge delay between instructions and execution. The “native” delay between some parts of code can be measured and compared with the actual delay using several approaches. Our sample creates a new HKCU\Software\tuojqnwwbs registry key, calls RtlTimeToSecondsSince1970 which is used for “Converting the specified 64-bit system time to the number of seconds since the beginning of January 1, 1970” and saves the value in the created registry key:
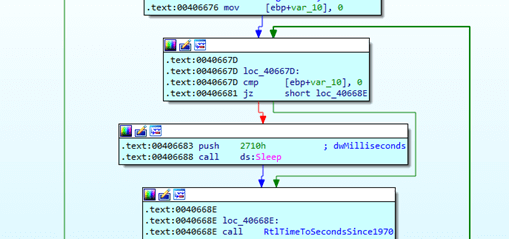
It calls RtlTimeToSecondsSince1970 again later and checks a time delta:
Next, a “\Sessions\2\BaseNamedObjects\Santiv18” mutex is created. If the “update.txt” file is not found, the malware uses the victim’s endpoint to send Extortion emails:
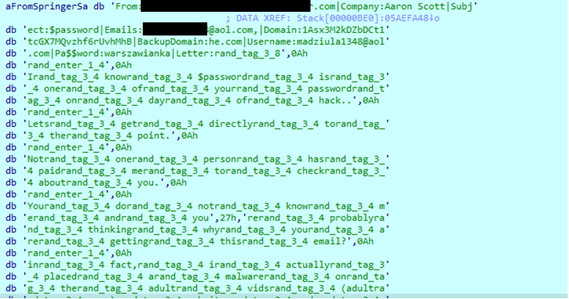
The email content is:
I know michigan is one of your password on day of hack..
Lets get directly to the point.
Not one person has paid me to check about you.
You do not know me and you’re probably thinking why you are getting this email?
in fact, i actually placed a malware on the adult vids (adult porn) website and you know what, you visited this site to experience fun (you know what i mean).
When you were viewing videos, your browser started out operating as a RDP having a key logger which provided me with accessibility to your display and web cam.
immediately after that, my malware obtained every one of your contacts from your Messenger, FB, as well as email account.
after that i created a double-screen video. 1st part shows the video you were viewing (you have a nice taste omg), and 2nd part displays the recording of your cam, and its you.
Best solution would be to pay me $2732.
We are going to refer to it as a donation. in this situation, i most certainly will without delay remove your video.
My BTC address : 14JuDQdSEQtFq7SkFHGJackAxneY9ixAUM
[case SeNSiTiVe, copy & paste it]
You could go on your life like this never happened and you will not ever hear back again from me.
You’ll make the payment via Bitcoin (if you do not know this, search ‘how to buy bitcoin’ in Google).
if you are planning on going to the law, surely, this e-mail can not be traced back to me, because it’s hacked too.
I have taken care of my actions. i am not looking to ask you for a lot, i simply want to be paid.
if i do not receive the bitcoin;, I definitely will send out your video recording to all of your contacts including friends and family, co-workers, and so on.
Nevertheless, if i do get paid, i will destroy the recording immediately.
If you need proof, reply with Yeah then i will send out your video recording to your 8 friends.
it’s a nonnegotiable offer and thus please don’t waste mine time & yours by replying to this message.
Even though this seems to be the final payload, we observed that it still has the ability to download an additional file to the endpoint:
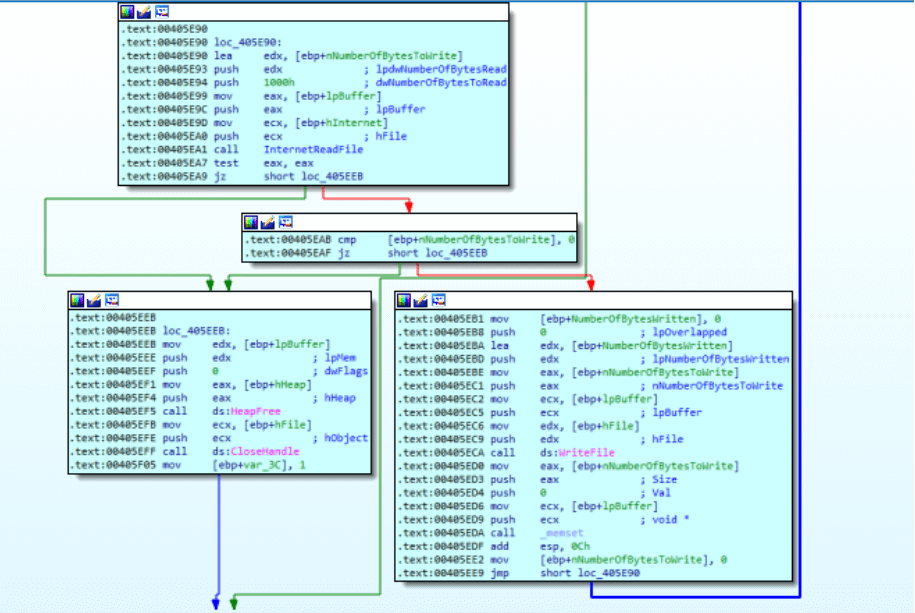
This might indicate that the threat actor left a door open for itself and might yet decide to pass additional files.
We also noticed that the payload has the ability to create a scheduled task which might be used for adding persistency for the next stage (if it is performed).
This threat actor went through a lot of trouble to drop the malware and keep it undetected, only to use it as an extortion mail sender. Botnets are dangerous exactly because of this unknown upcoming threat. It could just as easily drop and execute ransomware, spyware, worms, or other threats on all infected endpoints.
We observed a large amount of similar samples at VT.
This is an interesting example of an attack that might not appear to be “harmful” or very common, but it holds 2 major risks for an organization:
- The organization domain might find itself block by other organizations which could in turn severely harm its
- The attacker has gained a significant foothold on the network domain and has made harmless actions. But, after a while, the attacker may change the payload and impose more malicious actions, like in the examples above.
How Minerva Labs prevents these types of attacks
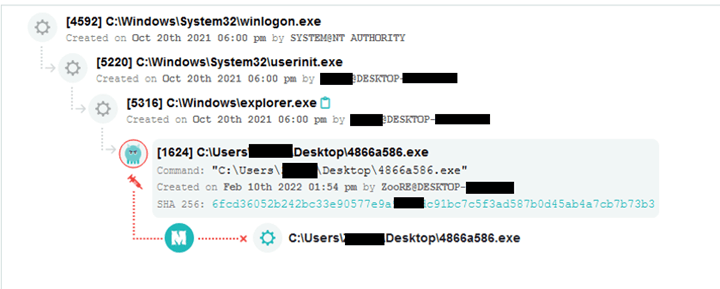
Minerva Labs Memory Injection Prevention module prevents this attack and protects the endpoint from becoming a bot. It is part of Minerva’s ransomware protection:
IOC’s
First stage executable – 4866a586.exe 6fcd36052b242bc33e90577e9a9cf5dc91bc7c5f3ad587b0d45ab4a7cb7b73b3
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK