How automation in CSPM can improve cloud security
source link: https://www.csoonline.com/article/3687745/how-automation-in-cspm-can-improve-cloud-security.html
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

How automation in CSPM can improve cloud security
Automation capabilities in cloud security posture management platforms can speed the process of monitoring and remediating security and compliance risks.
By Enoch Anbu Arasu Ponnuswamy
CSO | Feb 16, 2023 2:00 am PST

Golden Dayz/Shutterstock
With the rapid growth and increasing complexity of cloud environments, organizations are increasingly at risk from various security threats. Cloud security posture management (CSPM) is a process that helps organizations continuously monitor, identify, and remediate security risks in the cloud. The use of automation in CSPM is crucial to ensuring the security and compliance of an organization's cloud infrastructure.
A key component of CSPM is the automation of its core tasks: continuous monitoring, remediation of issues, compliance management, and alerts and notifications. The integration of robotic process automation (RPA) in CSPM helps to reduce the need to perform repetitive and mundane tasks, making it a powerful tool for organizations to secure and streamline their cloud environment, support the overall security posture, and manage security risks more efficiently.
Why CSPM is vital to cloud security
Cloud environments are becoming more complex with the deployment of resources such as Docker containers, endpoint APIs, Kubernetes nodes, and other serverless functions. It can be difficult for organizations to maintain control and gain visibility into their underlying infrastructure. This is particularly challenging when it comes to configuring and managing access permissions for each resource.
CSPM is an essential tool for addressing these challenges and fortifying your cloud security posture. It is typically adopted by businesses that prioritize a cloud-first strategy and want to leverage the benefits of cloud technology while minimizing risk by following best practices.
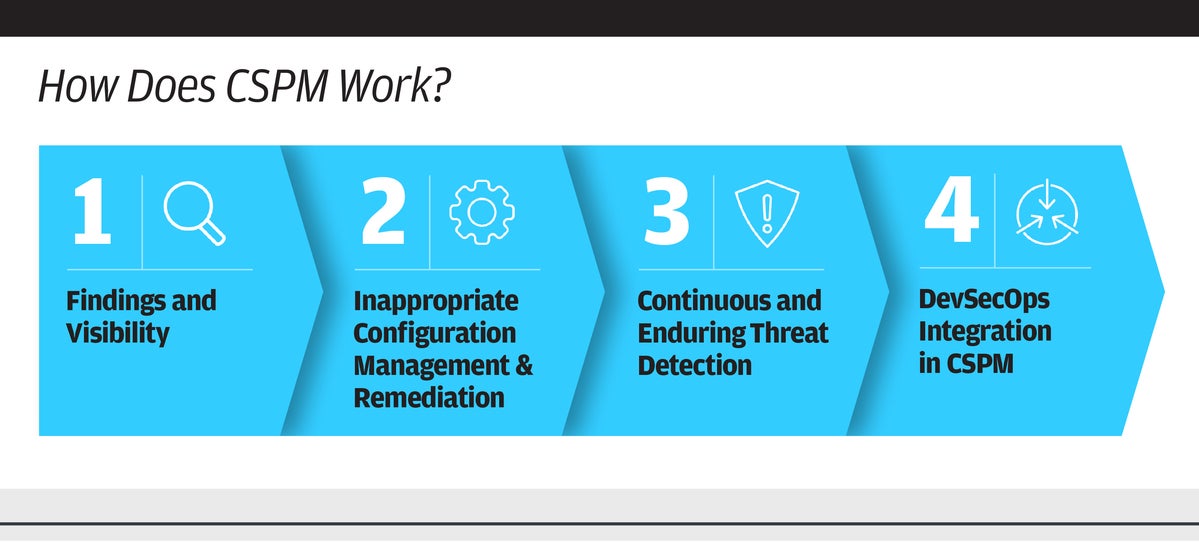
With its built-in automation capabilities, CSPM assists and streamlines DevSecOps efforts by constantly monitoring the cloud infrastructure, with a key benefit being the ability to quickly detect and address misconfigurations, allowing organizations to be proactive in maintaining compliance, as shown below.
How does CSPM work?
CSPM starts with the collection of data from various sources such as cloud providers, security tools, and other systems. The data is then analyzed to identify any potential security risks. This can include identifying misconfigured resources, detecting potential threats, and identifying any other issues that may pose a risk to the organization's cloud environment.
Foundry
Once potential risks are identified, CSPM provides the ability to take corrective actions. This can include automated remediation of issues, such as applying security patches or configuring resources to meet security standards. It also provides alerts and notifications to the relevant personnel within the organization to take necessary action.
Another important benefit of CSPM is its assistance in maintaining regulatory compliance. Many organizations operate in industries subject to regulations such as HIPAA, PCI DSS, or GDPR. CSPM helps to ensure that the organization's cloud environment is compliant with these regulations by continuously monitoring for misconfigurations or vulnerabilities that may put an organization at risk of non-compliance and taking the necessary steps to fix them.
CSPM also provides organizations with centralized visibility across cloud environments. This includes gaining an overview of all the resources and configurations, providing a single source of truth for the cloud resources, and eliminating blind spots in security.
How enterprises benefit from cloud security automation
Automation in CSPM is designed to continuously monitor and identify potential vulnerabilities and misconfigurations in an organization's cloud environment and then take the necessary steps to remediate them. Here are a few key capabilities of automation in CSPM that organizations can leverage to improve their cloud security posture:
- Continuous monitoring: Automation in CSPM enables continuous monitoring of the cloud environment. This includes collecting data from sources cloud providers and security tools and analyzing it to identify potential vulnerabilities and misconfigurations. Automated monitoring helps organizations to detect and respond to potential threats promptly.
- Automatic remediation: CSPM automation allows organizations to take corrective actions automatically when potential vulnerabilities or misconfigurations are identified. This can include applying security patches, configuring resources to meet security standards, or even shutting down resources that are deemed to be at risk.
- Compliance management: CSPM helps organizations to stay compliant with regulations such as HIPAA, PCI DSS, and GDPR by continuously monitoring for misconfigurations or vulnerabilities that may put an organization at risk of non-compliance and taking the necessary steps to fix them.
- Centralized visibility: Automation in CSPM enables organizations to gain centralized visibility across cloud environments. This includes gaining an overview of all resources and configurations, providing a single source of truth for cloud resources, and eliminating blind spots in security.
- Alerts and notifications: Automation in CSPM provides alerts and notifications to the relevant personnel within an organization when potential vulnerabilities or misconfigurations are detected. This allows organizations to take the necessary steps to remediate any issues as quickly as possible.
- Robotic process automation: RPA helps automate repetitive and mundane tasks in CSPM. It allows for a quick response to security alerts, updates to security policies, or compliance checks.
Automation is a crucial component of CSPM, and organizations can leverage its capabilities to improve their cloud security posture. Continuous monitoring, automatic remediation, compliance management, centralized visibility, alerts and notifications, and RPA make CSPM a powerful tool for keeping an organization's cloud infrastructure secure and compliant and supporting the overall security posture of an organization.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK