SHA256 and other hashing functions in SAS
source link: https://blogs.sas.com/content/sasdummy/2014/01/18/sha256-function-sas94/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

SHA256 and other hashing functions in SAS
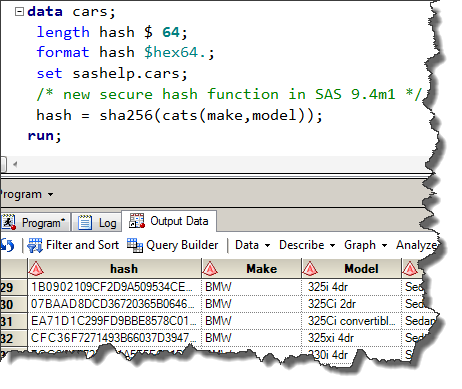
26For several releases, SAS has supported a cryptographic hash function called MD5, or "message digest". In SAS 9.4 Maintenance 1, the new SHA256 function can serve the same purpose with a better implementation.
UPDATE: Since first writing this in 2014, SAS has added a richer set of hashing functions/methods. They include MD5, SHA1, SHA256, SHA384, SHA512, CRC32 and HMAC methods. See "Hashing functions and hash-based message functions in SAS" in the documentation.
The job of a hash function is to take some input (of any type and of any size) and distill it to a fixed-length series of bytes that we believe should be unique to that input. As a practical example, systems use this to check the integrity of file downloads. You can verify that the published hash matches the actual hash after downloading.
Sometimes a hash is used to track changes in records within a database. You first calculate a hash value for each data record based on all of the fields. Periodically, you recheck those calculations. If a hash value changes for a data record, you know that some part of that record has changed since the last time you looked.
Here's another common use: storing passwords in a database. Because you can't (theoretically) reverse the hash process, you can use a hash function to verify that a supplied password is the same as a value you've stored, without having to store the original clear-text version of the password. It's not the same as encryption, because there is no decryption method that would compromise the original supplied password value.
MD5 has known vulnerabilities, especially with regard to uniqueness. A malicious person can use a relatively low-powered computer to compute an input that produces an identical hash to one you've stored, thus compromising the algorithm's usefulness.
Enter the SHA256 algorithm. It's the same idea as MD5, but without the known vulnerabilities. Here's a program example:
data _null_;
format hash $hex64.;
hash = sha256("SHA256 is part of SAS 9.4m1!");
put hash;
run; |
Output (formatted as hexadecimal so as to be easier on the eyes than 256 ones-and-zeros):
876CF270E81BA3E6219F9518AD9CBE303D8EEC734D4B5966F8D4FD9E89449C6C
As the name implies, it produces a value that is 256 bits (32 bytes) in size, as compared to 128 bits from MD5. Here's a useful article that compares the effectiveness of hash algorithms.
If you've been wanting to hash your data in SAS, but you've been poo-pooing the MD5 function -- well, now is your chance!
Recommend
-
 87
87
For the Minio object storage server, SHA256 hash calculations are an important part of the processing pipeline for payloads. As users issue PUT commands and upload objects, the integrity of the…
-
 26
26
Join GitHub today GitHub is home to over 50 million developers working together to host and review code, manage projects, and build software together.
-
 11
11
How many bytes (= ASCII characters) of Ruby code does it take to generate a SHA 256 hash sum of STDIN?
-
 4
4
实例来源网络,语言版本可能略有差异,请验证后使用。 Javascript HMAC SHA256 <script src="http://crypto-js.googlecode.com/svn/tags/3.0.2/build/rollups/hmac-sha256.js"></script>...
-
 4
4
Learn the Blockchain Basics - Part 3 : Hashing FunctionsJuly 16th 2021 new story7
-
 4
4
V2EX › 程序员 试问 sha256 后能否公开数据😂 d5 · 7 小时 43 分钟前 · 1040 次点击
-
 2
2
Message block - 512 Bits10000000 00000000 00000000 00000000►00000000 00000000 00000000 00000000►00000000 00000000 00000000 00000000►00000000 00000000 00000000 00000000►00000000...
-
 2
2
The SHA-256 Project This project was originally assigned in NYU Tandon's CS-GY 6903 Applied Cryptography course, Fall 2021. Here's the original course repo...
-
 6
6
代码实现sha-256加密算法 sha-256.go package tools import ( "crypto/sha256" "encoding/hex" ) //SHA256生成哈希值 func GetSHA256HashCode(stringMessage string) string { message :=...
-
 12
12
Latest AMD chipset driver brings additional AM5 support, SHA256, and USB4 debugging...
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK