

Lessons learned: Configuring JWT authentication in OpenSearch (v2.0.0)
source link: https://blog.davidvassallo.me/2022/07/15/lessons-learned-adding-jwt-authentication-to-opensearch-v2-0-0/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

Lessons learned: Configuring JWT authentication in OpenSearch (v2.0.0)
Opensearch has support for using JWT authentication:
https://opensearch.org/docs/latest/security-plugin/configuration/configuration/#json-web-token
This is a really nifty feature when integrating with 3rd party solutions to provide SSO. For various reasons, my main focus was on getting JWT URL parameters to work, i.e. being able to pass the JWT to opensearch and dashboards via the URL. Here are some important lessons I learnt after taking up way more time than it should have:
Some of the documentation is lagging behind
- The correct configuration in your opensearch/config/opensearch-security/config.yml file is:
jwt_auth_domain:http_enabled: truetransport_enabled: trueorder: 0http_authenticator:type: jwt[...] |
Note the “_enabled” lines… which are not mentioned in the current documentation (though hopefully this will be addressed: https://github.com/opensearch-project/documentation-website/pull/805)
- Even though JWT URL parameter authentication works when querying opensearch directly, it fails when used to access opensearch dashboards.
Ensure the following lines are present in the opensearch dashboards config file opensearch_dashboards.yml
opensearch_security.auth.type: "jwt"opensearch_security.jwt.url_param: your_param_name_here |
Make sure your JWT tokens contain the right claims
- Ensure that the JWT token contains the correct “iat” (issued at), “nbf” (not before) and “exp” (expiry) claims, all of which are validated automatically by opensearch
Make sure you get your permissions right
- When using JWT URL Parameter containing the default admin role “all_access” against opensearch (for example:
curl http://localhost:9200?jwtToken=aabbccdd), the request fails with:
{"error":{"root_cause":[{"type":"security_exception","reason":"no permissions for [cluster:monitor/main] and User [name=admin, backend_roles=[all_access], requestedTenant=null]"}],"type":"security_exception","reason":"no permissions for [cluster:monitor/main] and User [name=admin, backend_roles=[all_access], requestedTenant=null]"},"status":403} |
Solution: Ensure that the role “all_access” is mapped directly to the internal user, not a “backend role”. To do this, navigate to Security > Roles > all_access and switch tab to “Mapped Users”. Click on “Manage mapping” and add “admin” to the “users” section:
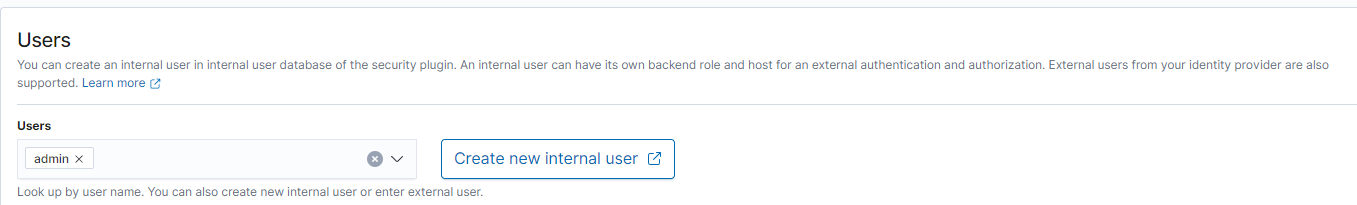
The end result should show:
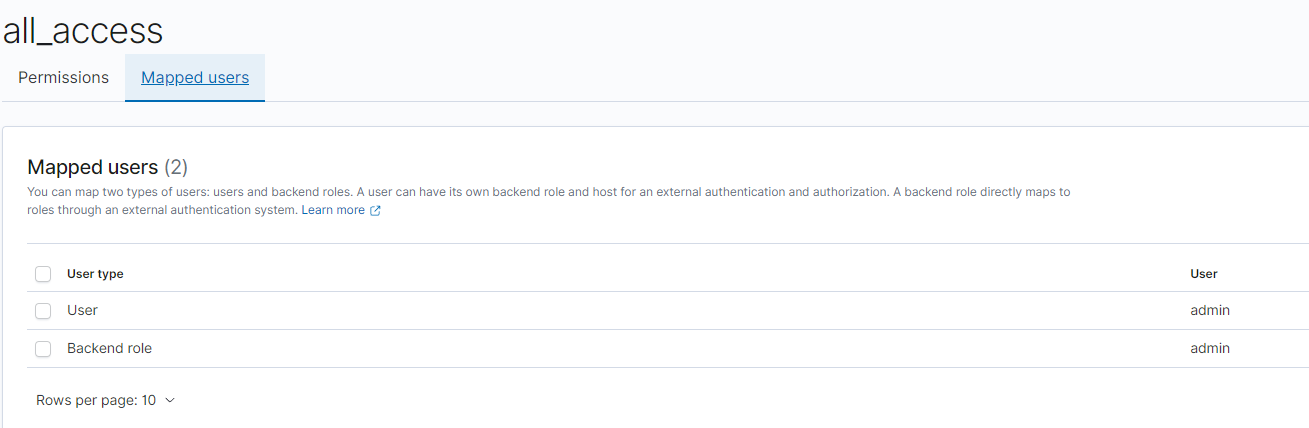
(note the “User type” set to “User” in the first row above)
Note: the above has also been submitted via pull requests to the official opensearch docs:
Related
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK
