

Tech.co Explains - VoIP Phone Security Risks 2022
source link: https://tech.co/business-phone-systems/voip-security
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

VoIP Security – 2022 Guide
Is VoIP secure? Not always. But it can be made secure. Learn more about VoIP security and stop your calls being intercepted.

Voice over Internet Protocol (VoIP) is quickly becoming the new norm for business telephone systems. It's faster, clearer, and more comprehensive for companies of all sizes to conduct business over the phone. But is it secure?
Given the increasing presence of cybercrime around the world, the importance of security has never been more significant. Scam calls, phishing attacks, malware, and plenty of other online security threats are losing businesses money at an alarming rate, largely due to vulnerable loopholes that could easily be closed with a more security alternative.
Simply put, your business' telephone system doesn't have to be a source of stress from a security standpoint. Understanding the importance of VoIP security and taking steps to get set up with a secure VoIP provider is the best way to ensure you're safe, and we're going to walk you through the nitty gritty details.
How secure is VoIP?
VoIP phone systems offer a lot of benefits. From affordability to improved functionality and flexibility, a business can run much smoother and more efficiently with a VoIP system over a traditional phone system, which is largely why they've become so popular. Unfortunately, even with these added benefits, the problem of security is a notable downfall for the technology.
Basically, a VoIP system is a phone setup that connects calls via the internet, rather than a traditional phone line. This leaves them at least somewhat vulnerable to hacks, as all internet-connected devices are. Subsequently, it's less about the security of your VoIP system and more about the security of your internet network.
Following the best practices that we mention below, you can secure your VoIP system from ever being hacked. Even basic measures like exclusively using encrypted WiFi networks can decrease your chances of getting hacked substantially.
Suffice it to say, yes, landline phones are a bit more secure than VoIP systems, but if you follow the steps we talk about below and avoid any common pitfalls of online security, you'll have nothing to worry about.

VoIP Security Threats
The best way to ensure your VoIP system stays secure is to know what might be out there. Unfortunately, a VoIP vulnerability leaves you wide open to a whole array of threats that could lead to everything from a simple nuisance to a full blow security.
Fortunately, knowledge is power, and we've collected some of the more credible VoIP security threats to help you understand exactly how to protect yourself in real time. Here are a few of the most notable VoIP security threats and consequences:
- Malware – As with any system that is connected to the internet, VoIP systems are susceptible to malware attacks, as well as other viruses that could slow down or compromise your system.
- VoIP phishing – Also known as Vishing, this attack is designed to target specific phone users, duping them into believing that the call is from a reputable source through Caller ID and convincing them to provide valuable personal and company information that could lead to a security breach.
- Denial of Service (DoS) – This attack is specifically made to disrupt phone service. It overloads the system, depriving it of important resources, which eventually leads to poor call quality, uptime, and latency.
- Eavesdropping – If your VoIP system is set up on an unencrypted WiFi network, you could have nefarious actors listening in on conversations with ease. This could lead to a serious security breach, particularly if you are talking about sensitive information with team members.
- Robocalls – Certainly more of a nuisance than a serious threat, but voicemail allows for pretty much anyone to leave a message, including robocalls and other spammers that are trying to get you to respond to an annoying and futile request.
There are other security threats with VoIP, but if you can make sure to cover your bases on these five, you should have a secure enough system to manage your every day calls. And while you might not realize it, securing your VoIP system is extremely important.
The Importance of VoIP Security
Now, you might be thinking to yourself, how important is VoIP security really? Even if you've never fallen victim yourself, the reality is that the threat of security breaches via a phone system is pretty serious.
In fact, 62% of businesses in 2018 experienced social engineering hacks, a type of phone scam that masquerades as a genuine call to get valuable information about a given company. Twitter was targeted in a similar attack in 2020, which saw 45 of its most prominent accounts — including Barack Obama, Kim Kardashian, and Bill Gates — promoting a cryptocurrency scam that amassed hundreds of thousands of dollars.
Simply put, the importance of VoIP security cannot be understated. On a more specific note, because VoIP technology relies on the internet to make calls, it's inherently vulnerable to certain attacks. Given that more than 25% of WiFi networks around the world are without any form on encryption, a VoIP provider that is lax on security could cause some serious problems for your business.
Oh yeah, and it gets worse. While 25% of WiFi networks around the world are without encryption, the US is not on the better side of that average. If you're running a business in the US, the odds are much higher (34%-44%) that the network your using unencrypted, which means you really need to make sure that you choose a trusted VoIP provider that follows best practices.
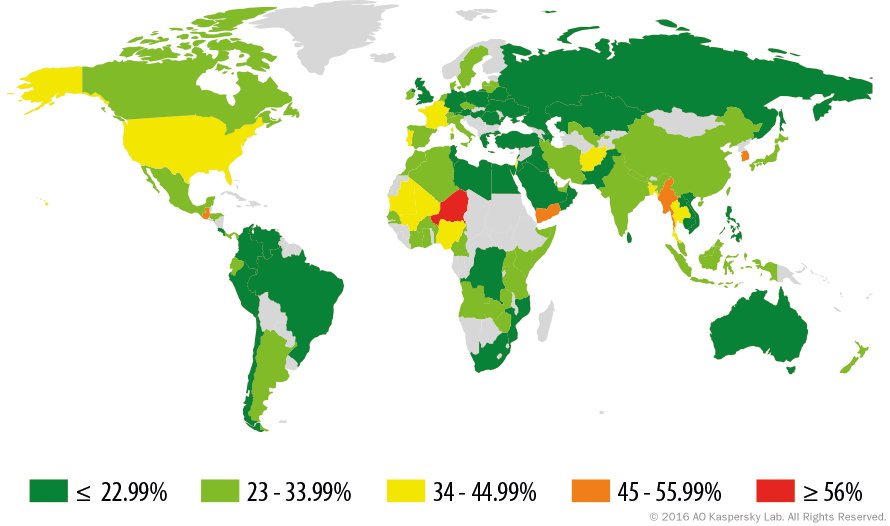
World map showing the percentage of unencrypted WiFi networks by country
Use a strong password
Many VoIP phones require a password to be used, offering a simple, default password during setup. To ensure your device remains secure, you need to be sure to change that default password to a strong alternative that you won't forget and that won't be able to guess. Password best practices dictate that it should be at least 10 characters long.
If you want to take it to the next level, you might want to add some other password security measures, like expiration dates for new passwords and two-factor authentication. These extra measures may seem tedious, but the reality is that they greatly increase security, and make it nearly impossible for hackers to gain access if employed consistently and correctly.

Update your system regularly
It may seem like a hassle, but when it comes to online security, updating your software on a consistent basis is an invaluable tool in protecting your devices. This is especially true for VoIP phone systems, as providers consistently experience attempted breaches that can only be closed with swift and effective software updates.
This means that you need to actually pay attention to this pesky notifications that want you to update your phone system (yes, even if it requires a restart right in the middle of a business workday). It might even behoove you to assign this task to a security person in the company, so you can be sure all the devices at your business are regularly updated, as one un-updated device could ruin it for the bunch.
Monitor your call logs
Another surefire way to make sure your VoIP system is secure is to actually keep an eye on it. Most VPN providers will allow you to take a look at call logs, giving you a clear breakdown of who is calling where and how often, allowing you to monitor for any suspicious behavior that could lead to a security breach.
So what are you keeping an eye out for? Anything that looks inconsistent with your business practices could be a security threat. Strange numbers, odd hours, and anything that seems out of the ordinary will be a dead giveaway that there is some kind of vulnerability in your system, allowing you to quickly discover the problem and, more important, fix it as soon as possible.
Require remote employees to use a VPN
In an era when remote work is becoming more and more popular, the importance of security cannot be understated. Employees working from home can open up a whole array of security vulnerabilities, particularly if you have them logging into the company phone system from a smartphone or connected phone system at their home.
To avoid any security pitfalls, make sure your team is required to use a VPN for all at home usage. This will protect their internet activity from external sources, including phone calls on a VoIP system, so there is no risk of an unsecured WiFi network creating problems for your business.
Check out our in-depth business VPN guide for more info

Educate your team
As a business owner or security manager, understanding all these VoIP security best practices is obviously important, but not nearly as important as relaying them to your team. In fact, all the knowledge in the world won't help you unless you pass it on, which is why educating your team about security best practices, for VoIP or otherwise, is an integral aspect of running a successful, breach-free company.
From strict requirement for devices to active learning opportunities in the office, security needs to be made a priority for everyone if you want to have any hope of keeping your phone system secure. Because again, a single weak link the chain can open the door for your entire team to get hacked.
Encryption
To avoid getting too complicated, encryption is essentially the process of making internet data more secure. In the same way an unencrypted WiFi network can compromise your security, providers that don't offer call encryption will leave you open to a wide range of potential breaches, which just won't do.
More specifically, you want to make sure your VoIP provider is offering Transport Layer Security (TLS) and Secure Real-time Transport Protocol (SRTP), the two most common and necessary protocols for VoIP technology.
Support
All technology has a hiccup here and there, and VoIP phone systems are no different. You're always going to want to be sure that you have an expert backing you up in these situations, which means that understanding your support options from provider to provider is vital.
From sporadic hours and live chat to 24/7 phone support, providers truly run the gamut as far as what you can expect from a customer service standpoint. Make sure the provider you opt for is ready and available to field your support request, as it could be the difference between secure data and a security breach.

Compliance Accreditation
Because concerns about data security are so prevalent in the world today, there are plenty of regulations out there designed to keep people safe. Unfortunately, not all providers follow these regulations, shirking their responsibility to be compliant with specific measures. Be sure to check which accreditations your provider has before signing off. Some important ones include:
- HIPAA Compliance – This specific relates to health care providers securing patient data in a way that fully and completely protects anything from being stolen.
- PCI Compliance – This accreditation insists that, if your business accepts credit card payment, you must comply with much strict rules about how secure your system is.
- SOC 2 Compliance -This is a more vague compliance, which ensures that consumer data is protected to a certain extent. It's considered the minimum standard for businesses dealing with consumer data.
As you can imagine, the more compliant with these and other measures, the better your provider will be with security, which makes it a decidedly important aspect to watch out for when making a decision.
Getting Started with a Secure VoIP Phone System
Now, if all this talk about security breaches hasn't scared you off, getting started with a VoIP phone system shouldn't be too hard at all. Tech.co has done extensive research to identify the best VoIP phone providers, and you can compare prices for your business with just the click of a button. Simply take advantage of our handy comparison tool, to receive tailored, accurate pricing for your business, without breaking a sweat.
Frequently Asked Questions
Tech.co is reader-supported. Using Tech.co's comparison form, you can receive quotes from various suppliers, tailored to the needs of your business. If you enter into a contract with a provider, we may receive a payment for the introduction. Equally, if you make a purchase through the links on our site, we may earn a commission. This helps Tech.co provide free advice and reviews and carries no additional cost to you. Most importantly, it doesn’t affect our editorial independence. Click to return to top of page
Jack is the Deputy Editor for Tech.co. He has been writing about a broad variety of technology subjects for over a decade, both in print and online, including laptops and tablets, gaming, and tech scams. As well as years of experience reviewing the latest tech devices, Jack has also conducted investigative research into a number of tech-related issues, including privacy and fraud.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK