

WatchGuard Firewalls: Cyclops Blink Botnet (English Version)
source link: https://blog.boll.ch/watchguard-firewalls-cyclops-blink-botnet/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

WatchGuard Firewalls: Cyclops Blink Botnet (English Version)
According to current information, a limited number (~1%) of WatchGuard firewalls have been infected by a state-sponsored botnet called Cyclops Blink. Although there is currently no evidence of data exfiltration, it is possible that data from the firewalls has been compromised.
Blog article in German can be found here: https://blog.boll.ch/watchguard-firewalls-cyclops-blink-botnet-befall/
Official statement
https://detection.watchguard.com/
Blog with additional information
https://www.watchguard.com/wgrd-news/blog/important-detection-and-remediation-actions-cyclops-blink-state-sponsored-botnet
Cyclops Blink FAQ
https://techsearch.watchguard.com/
1. Is my firewall affected?
WatchGuard provides several ways to find an infestation of the botnet software on the firewalls:
Cyclops Blink Web Detector (online)
On the website https://detection.watchguard.com/Detector you can upload a support.tgz of the firewall and check for botnet infestation.
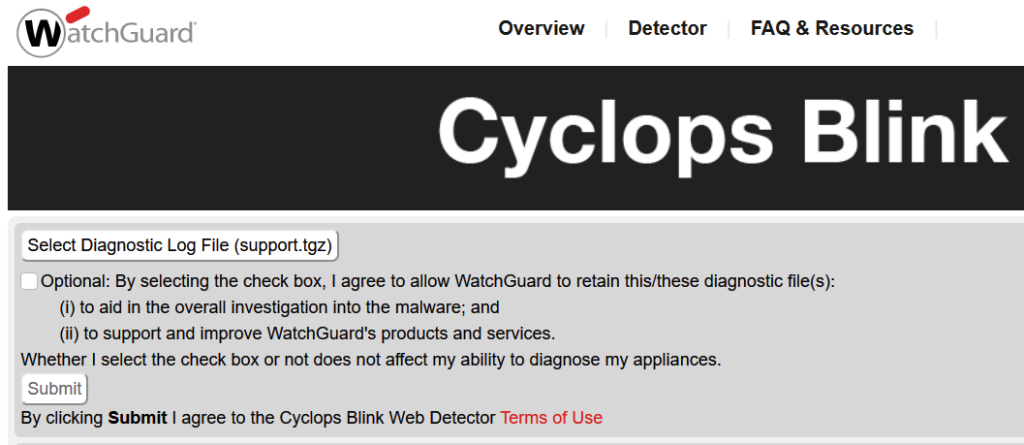
WatchGuard System Manager Cyclops Blink Detector
In the latest WSM version 12.7.2 update 2 (downloadable now) there is a Cyclops Blink Detector:
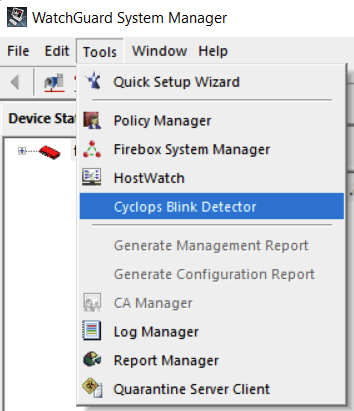
Download WSM Version 12.7.2 Update 2
https://cdn.watchguard.com/SoftwareCenter/Files/WSM/12_7_2_U2/wsm_12_7_2_U2.exe
WatchGuard Cloud Cyclops Blink Detector
Firewalls added to the WatchGuard Cloud also have a Cyclops Blink Detector:
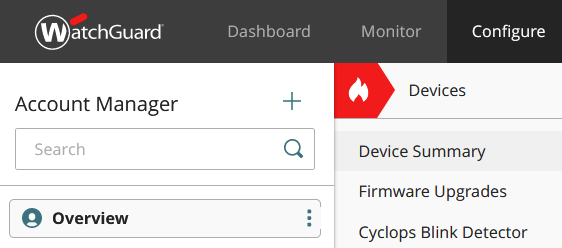
2a. My firewall is not affected
Even if your firewall is not affected, you should implement the following advice as soon as possible:
Install the latest firmware
Here you can find the latest firmware:
https://software.watchguard.com/SoftwareHome
Close the management ports from the Internet
WatchGuard assumes that the malware could be installed through the management ports.
https://techsearch.watchguard.com/KB?type=Article&SFDCID=kA10H000000XeAtSAK&lang=en_US
Changing administrator password
Administrator passwords should be changed regularly.
2b. My firewall is affected
Depending on the type of management, it may be necessary to completely reset and rebuild the firewall, as the malware may take root in the configuration and software:
Locally managed Firebox via WSM or Fireware WebUI
Cyclops Blink: Remediate a Locally-Managed Firebox
WatchGuard Cloud managed Fireboxes
Cyclops Blink: Remediate a Cloud-Managed Firebox
Firebox Cloud
Cyclops Blink: Remediate Firebox Cloud
FireboxV / XTMv
Cyclops Blink: Remediate FireboxV and XTMv
Fireboxes managed by the management server
Cyclops Blink: Remediate a Firebox Managed by WSM Management Server
625 total views, 2 views today
Leave a Reply Cancel reply
Comment *
Name *
Email *
Website
Save my name, email, and website in this browser for the next time I comment.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK