

About Apple threat notifications and protecting against state-sponsored attacks
source link: https://support.apple.com/en-us/HT212960
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

About Apple threat notifications and protecting against state-sponsored attacks
Apple threat notifications are designed to inform and assist users who may have been targeted by state-sponsored attackers.
Apple threat notifications are designed to inform and assist users who may have been targeted by state-sponsored attackers. These users are individually targeted because of who they are or what they do. Unlike traditional cybercriminals, state-sponsored attackers apply exceptional resources to target a very small number of specific individuals and their devices, which makes these attacks much harder to detect and prevent. State-sponsored attacks are highly complex, cost millions of dollars to develop, and often have a short shelf life. The vast majority of users will never be targeted by such attacks.
If Apple discovers activity consistent with a state-sponsored attack, we notify the targeted users in two ways:
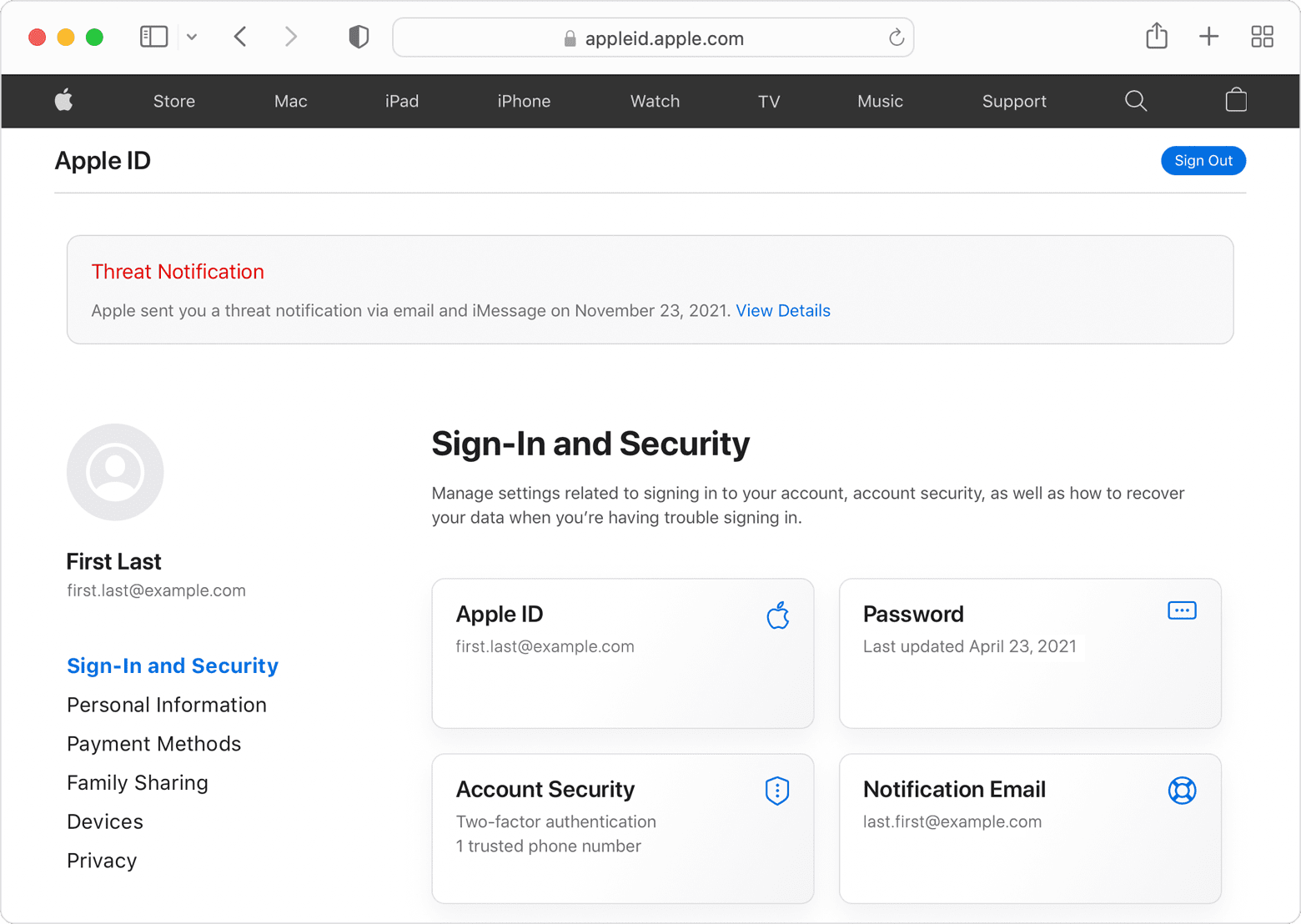
- A Threat Notification is displayed at the top of the page after the user signs into appleid.apple.com.
- Apple sends an email and iMessage notification to the email addresses and phone numbers associated with the user’s Apple ID.
These notifications provide additional steps that notified users can take to help protect their devices.
State-sponsored attackers are very well-funded and sophisticated, and their attacks evolve over time. Detecting such attacks relies on threat intelligence signals that are often imperfect and incomplete. It’s possible that some Apple threat notifications may be false alarms, or that some attacks are not detected. We are unable to provide information about what causes us to issue threat notifications, as that may help state-sponsored attackers adapt their behavior to evade detection in the future.
Apple threat notifications will never ask you to click any links, open files, install apps or profiles, or provide your Apple ID password or verification code by email or on the phone. To verify that an Apple threat notification is genuine, sign in to appleid.apple.com. If Apple sent you a threat notification, it will be clearly visible at the top of the page after you sign in.
All users should continue to protect themselves from cybercriminals and consumer malware by following best practices for security:
- Update devices to the latest software, as that includes the latest security fixes
- Protect devices with a passcode
- Use two-factor authentication and a strong password for Apple ID
- Install apps from the App Store
- Use strong and unique passwords online
- Don’t click on links or attachments from unknown senders
If you have not received an Apple threat notification, but have good reason to believe you may be targeted by state-sponsored attackers or you require emergency cybersecurity assistance for other reasons, we strongly suggest you enlist expert help. The Consumer Reports Security Planner website offers a list of emergency resources that may be able to assist you.
Information about products not manufactured by Apple, or independent websites not controlled or tested by Apple, is provided without recommendation or endorsement. Apple assumes no responsibility with regard to the selection, performance, or use of third-party websites or products. Apple makes no representations regarding third-party website accuracy or reliability. Contact the vendor for additional information.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK