Was the Ashley Madison Database Leaked?
source link: https://krebsonsecurity.com/2015/08/was-the-ashley-madison-database-leaked/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

Many news sites and blogs are reporting that the data stolen last month from 37 million users of AshleyMadison.com — a site that facilitates cheating and extramarital affairs — has finally been posted online for the world to see. In the past 48 hours, several huge dumps of data claiming to be the actual AshleyMadison database have turned up online. But there are precious few details in them that would allow one to verify these claims, and the company itself says it so far sees no indication that the files are legitimate.
Update, 11:52 p.m. ET: I’ve now spoken with three vouched sources who all have reported finding their information and last four digits of their credit card numbers in the leaked database. Also, it occurs to me that it’s been almost exactly 30 days since the original hack. Finally, all of the accounts created at Bugmenot.com for Ashleymadison.com prior to the original breach appear to be in the leaked data set as well. I’m sure there are millions of AshleyMadison users who wish it weren’t so, but there is every indication this dump is the real deal.
Original story:
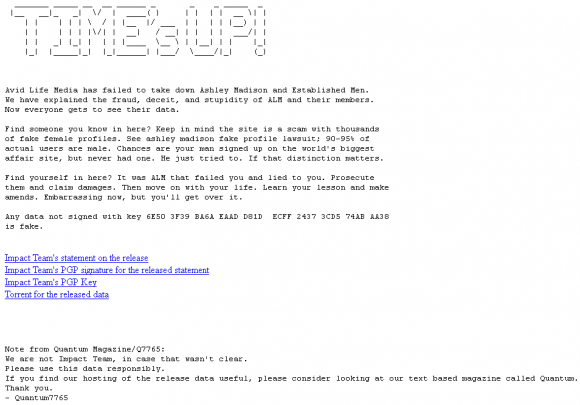
A huge trove of data nearly 10 gigabytes in size was dumped onto the Deep Web and onto various Torrent file-sharing services over the past 48 hours. According to a story at Wired.com, included in the files are names, addresses and phone numbers apparently attached to AshleyMadison member profiles, along with credit card data and transaction information. Links to the files were preceded by a text file message titled “Time’s Up” (see screenshot below).
From taking in much of the media coverage of this leak so far — for example, from the aforementioned Wired piece or from the story at security blogger Graham Cluley’s site — readers would most likely conclude that this latest collection of leaked data is legitimate. But after an interview this evening with Raja Bhatia — AshleyMadison’s original founding chief technology officer — I came away with a different perspective.
Bhatia said he is working with an international team of roughly a dozen investigators who are toiling seven days a week, 24-hours a day just to keep up with all of the fake data dumps claiming to be the stolen AshleyMadison database that was referenced by the original hackers on July 19. Bhatia said his team sees no signs that this latest dump is legitimate.
“On a daily basis, we’re seeing 30 to 80 different claimed dumps come online, and most of these dumps are entirely fake and being used by other organizations to capture the attention that’s been built up through this release,” Bhatia said.
“On a daily basis, we’re seeing 30 to 80 different claimed dumps come online, and most of these dumps are entirely fake and being used by other organizations to capture the attention that’s been built up through this release,” Bhatia said. “In total we’ve looked at over 100GB of data that’s been put out there. For example, I just now got a text message from our analysis team in Israel saying that the last dump they saw was 15 gigabytes. We’re still going through that, but for the most part it looks illegitimate and many of the files aren’t even readable.”
The former AshleyMadison CTO, who’s been consulting for the company ever since news of the hack broke last month, said many of the fake data dumps the company has examined to date include some or all of the files from the original July 19 release. But the rest of the information, he said, is always a mix of data taken from other hacked sources — not AshleyMadison.com.
“The overwhelming amount of data released in the last three weeks is fake data,” he said. “But we’re taking every release seriously and looking at each piece of data and trying to analyze the source and the veracity of the data.”
Bhatia said the format of the fake leaks has been changing constantly over the last few weeks.
“Originally, it was being posted through Imgur.com and Pastebin.com, and now we’re seeing files going out over torrents, the Dark Web, and TOR-based URLs,” he said.
To help locate new troves of data claiming to be the files stolen from AshleyMadison, the company’s forensics team has been using a tool that Netflix released last year called Scumblr, which scours high-profile sites for specific terms and data.
“For the most part, we can quickly verify that it’s not our data or it’s fake data, but we are taking each release seriously,” Bhatia said. “Scumbler helps accelerate the time it takes for us to detect new pieces of data that are being released. For the most part, we’re finding the majority of it is fake. There are some things that have data from the original release, but other than that, what we’re seeing is other generic files that have been introduced, fake SQL files.”
Bhatia said this most recent leak is especially amusing because it included actual credit card data, even though AshleyMadison.com has never stored credit card information.
“There’s definitely not credit card information, because we don’t store that,” Bhatia said. “We use transaction IDs, just like every other PCI compliant merchant processor. If there is full credit card data in a dump, it’s not from us, because we don’t even have that. When someone completes a payment, what happens is from our payment processor, we get a transaction ID back. That’s the only piece of information linking to a customer or consumer of ours. If someone is releasing credit card data, that’s not from us. We don’t have that in our databases or our own systems.”
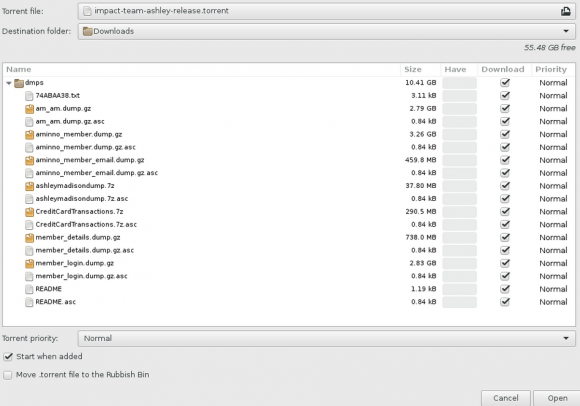
A screen shot of the archive released recently that many believe is the leaked AshleyMadison database.
I should be clear that I have no idea whether this dump is in fact real; I’m only reporting what I have been able to observe so far. I have certainly seen many people I know on Twitter saying they’ve downloaded the files and found data from friends who’d acknowledged being members of the site.
Nearly every day since I first reported the exclusive story of the Ashley Madison hack on July 19, I’ve received desperate and sad emails from readers who were or are AshleyMadison users and who wanted to know if the data would ever be leaked, or if I could somehow locate their information in any documents leaked so far. Unfortunately, aside from what I’ve reported here and in my original story last month, I don’t have any special knowledge or insight into this attack.
My first report on this breach quoted AshleyMadison CEO Noel Biderman saying the company suspected the culprit was likely someone who at one time had legitimate access to the company’s internal networks. I’d already come to the same conclusion by that time, and I still believe that’s the case. So I asked Bhatia if the company and/or law enforcement in Canada or the United States had apprehended anyone in relation to this hack.
Bhatia declined to answer, instead referring me to the written statement posted on its site today, which noted that investigation is still ongoing and that the company is simultaneously cooperating fully with law enforcement investigations, including by the Royal Canadian Mounted Police, the Ontario Provincial Police, the Toronto Police Services and the U.S. Federal Bureau of Investigation.
“This event is not an act of hacktivism, it is an act of criminality. It is an illegal action against the individual members of AshleyMadison.com, as well as any freethinking people who choose to engage in fully lawful online activities,” the statement reads. “We know that there are people out there who know one or more of these individuals, and we invite them to come forward. While we are confident that the authorities will identify and prosecute each of them to the fullest extent of the law, we also know there are individuals out there who can help to make this happen faster.”
Readers should understand that if this dump does turn out to be legit, that just finding someone’s name, email address and other data in the archives doesn’t mean that person was a real user. As the above-mentioned Graham Cluley points out, AshleyMadison never bothered to verify the email addresses given to it by its users.
“So, I could have created an account at Ashley Madison with the address of [email protected], but it wouldn’t have meant that Obama was a user of the site,” Cluley wrote. “Journalists and commentators would be wise to remember that the credentials stored by Ashley Madison must be considered suspect because of their shonky practices, even before you start considering whether any leaked databases are falsified or not.”
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK