

15+ new code scanning integrations with open source security tools
source link: https://github.blog/2021-07-28-new-code-scanning-integrations-open-source-security-tools/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.


15+ new code scanning integrations with open source security tools
Last year, we released code scanning, a vulnerability detection feature in GitHub Advanced Security that’s also free on GitHub.com for public repositories. With code scanning, you can use GitHub CodeQL for static analysis, or you can choose from one of the many third-party integrations available in the GitHub Marketplace to execute security scans in your continuous integration pipeline and surface the results directly in GitHub. Today, we’re happy to announce more than 15 new integrations with open source security tools that broaden our language coverage to include PHP, Swift, Kotlin, Ruby, and more.
Below is a list of all the new integrations, with links to their GitHub Actions in the GitHub Marketplace. These integrations are brought to us by a number of key contributors from our open source community. Big thanks to @ajinabraham, @Moose0621, @GeekMasher, @Muglug, @GriffinMB, @jarlob, @presidentbeef, @A-Katopodis, @OwenRumney, @swinton and others for their contributions to the growing ecosystem of open source static analysis tools.
New open source scanner integrations
Mobile languages
Detekt is a static code analysis tool for the Kotlin programming language. A GitHub Action is available for Detekt, and a preconfigured workflow for Static Analysis Results Interchange Format (SARIF) upload is available in the GitHub user interface (UI) under the “Security” tab.
MobSF is an automated, all-in-one mobile application framework (Android/iOS Swift/Windows) for pen testing, malware analysis and security assessment that’s capable of performing static and dynamic analysis. With the help of @ajinabraham, MobSF now supports code scanning. Check out the GitHub Action or find it in the GitHub “Security” tab.
Big thanks to our own @Moose0621 and @GeekMasher for adding these popular tools for mobile applications! Kotlin and Swift support are forthcoming in CodeQL.
PHPElixir Phoenix FrameworkNode JSElectronRuby on RailsPowershellKubernetes YAMLTerraformC/C++Multiple languages: Java, Go, Ruby, Python and more
Contribute to the code scanning ecosystem
If you contribute to a static analysis tool, linter, or container scanning tool, you can easily integrate your project with code scanning by following our step by step guide to list your project directly in the GitHub UI and surface your scan results under the GitHub “Security” tab.
Fuzzers and dynamic application security testing (DAST) tools can also follow a pattern of uploading their results, similar to ForAllSecure’s Mayhem for API action or the StackHawk HawkScan action, which adds a link to DAST output in the SARIF help text metadata field.
Give code scanning a try
If you haven’t tried code scanning, now’s a great time to explore this capability and its many integrations. From the “Security” tab in the GitHub UI, you can configure code scanning on any public repository using CodeQL, or you can try one of our pre-configured Octodemos for Android Kotlin, iOS Swift, JavaScript, Terraform, or PHP. Below is a quick example using MobSF for iOS Swift.
- To try code scanning with MobSF, navigate to: https://github.com/octodemo/advance-security-mobile-ios
- Fork the repository to your GitHub Account. (Note that this demo uses OWASP iGoat Swift – A Damn Vulnerable Swift Application for iOS, a deliberately vulnerable application for code scanning demonstration purposes only!)
- Click the Actions tab and enable actions if required. 1000 free minutes are included in your GitHub account.
- Click on the MobSF workflow, then click Run workflow and run the workflow manually.
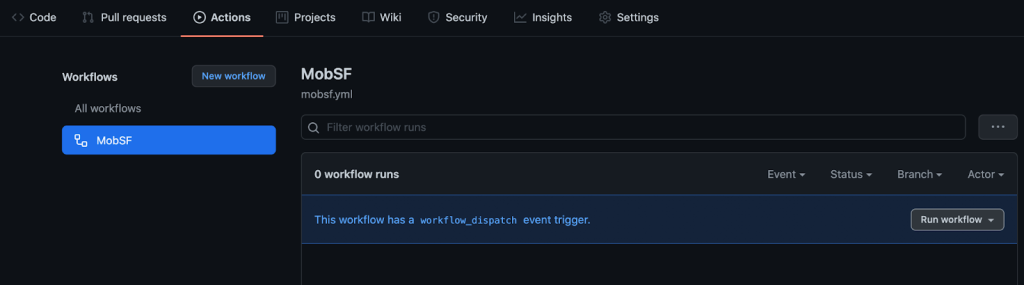
- In about a minute, you’ll see results populate in the “Security” tab under “Code scanning alerts.”
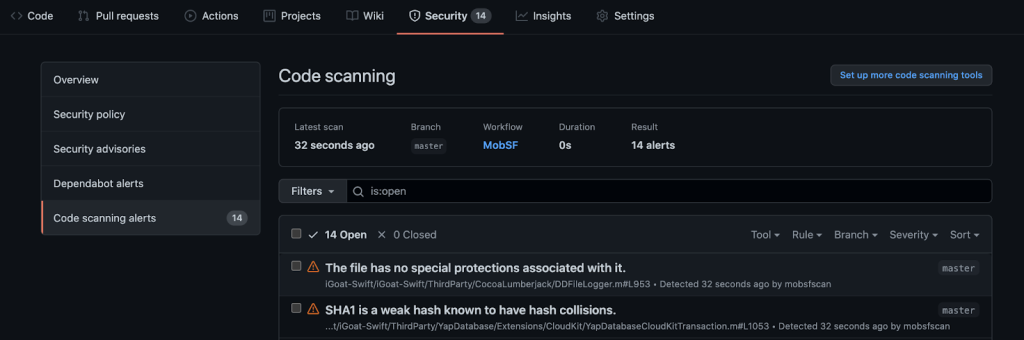
With GitHub Advanced Security, configuring a static analysis tool and delivering the results in context on every pull request is that simple! If you’d like a hands on demo for your organization don’t hesitate to contact us.
Tags: code scanning
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK