

GitLab 14.0 released with a celebration of GitLab 14
source link: https://about.gitlab.com/releases/2021/06/22/gitlab-14-0-released/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

When we think of everything released in the year since GitLab 13.0, we could not be more proud of our community and our team. This month, we celebrate our release of GitLab 14.0 by first taking a step back.
Together, we’ve made so much progress over the last year that we want to talk about everything it took to get to GitLab 14.
We use semantic versioning so a point release, like 14.0, represents everything new in this month. GitLab 14 is the culmination of the past year. Even more than that, GitLab 14 represents the future of GitLab, and the future of DevOps.
With GitLab 14, teams of all sizes are moving from maintaining DIY DevOps toolchains to adopting modern DevOps. GitLab 14 is a complete DevOps platform with security embedded in its DNA, visibility and insights enabled by its single data store, and a seamless experience and extensible system, so end users and enterprises alike reap the benefits of speed and efficiency.
We’re so excited that we’ve written a post where you can read more about GitLab 14 and our vision for modern DevOps, and how it enables any team to build and deliver software with velocity, visibility, and trust.
As ever, we are also excited about what’s new this month in 14.0. Read on for our regular highlights from dozens of significant new features and improvements. Along with these exciting new features, there are a few breaking changes in 14.0. To preview what's coming in next month’s release, check out our Upcoming Releases page, which includes our 14.1 release kickoff video.
Join us for GitLab Commit Virtual to learn how DevOps teams increase collaboration.

This month's Most Valuable Person (MVP) is Mathieu Parent
Mathieu has contributed significantly to the Package stage with his work on both the Debian and Helm package registries. These direction features have been fully contributed by Mathieu thus far.
The effort to implement Debian packages has been ongoing since September of 2020. Approximately 38 MRs merged so far, and now we are nearing the end of the iterative plan that Mathieu put together and maintained. As a result of Mathieu’s efforts, we are just a few merge requests away from feature completion and release.
Mathieu also planned the Helm Charts Package Manager effort and has been working on that over the past three months. In this work, Mathieu has embraced the GitLab values of iteration and collaboration, working closely with the entire Package team and beyond on these and many other features.
Thank you for all of your amazing work, Mathieu!
Key features released in GitLab 14.0
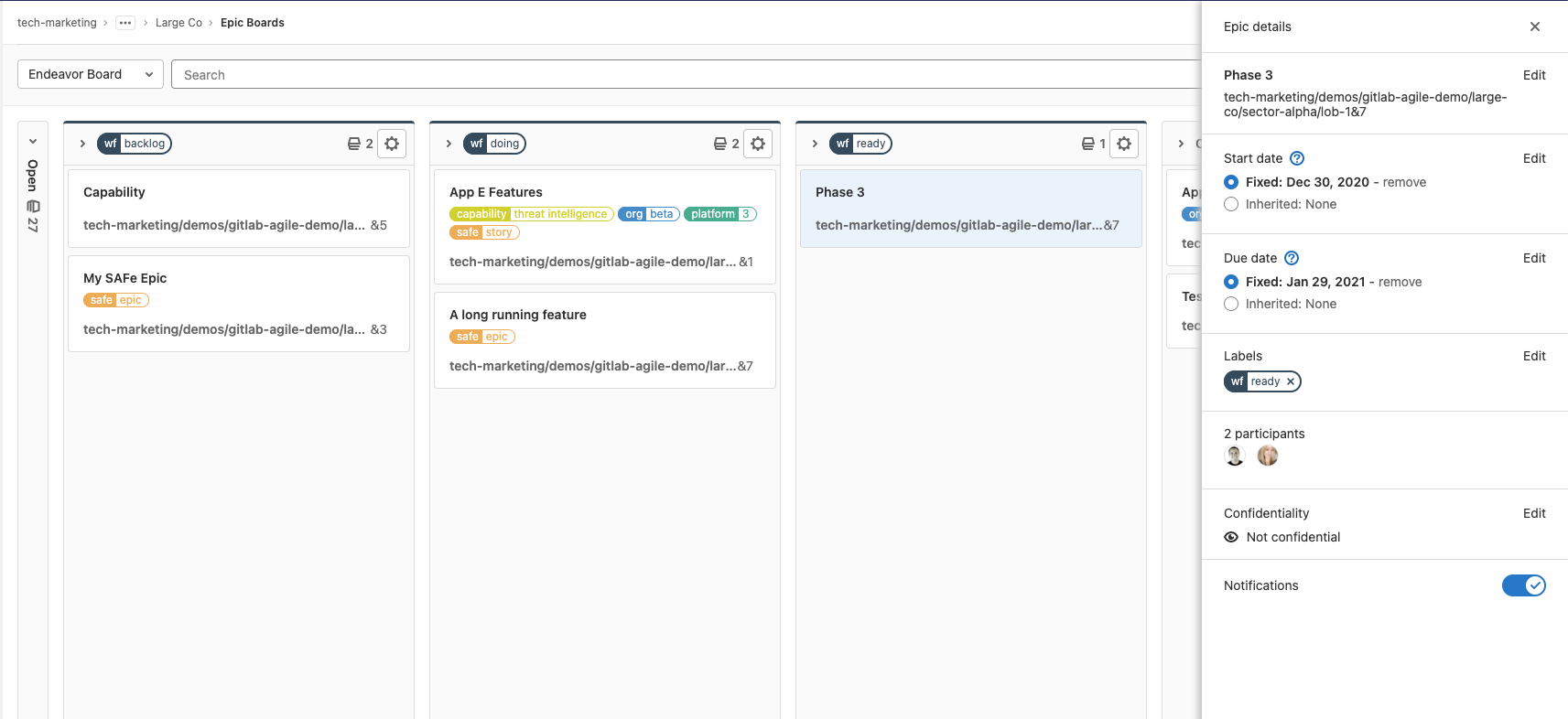
Epic Boards
Epic Boards align teams and organizations by communicating the status of epics continuously. Previous versions of GitLab required you to view and sort epics in a list to view the overall status. Keeping epics up to date meant making most changes through an epic’s detail page. Epic Boards enable you to visualize and refine all of your epics in one place, using a customizable, drag-and-drop interface that is easy for any teammate to understand and collaborate.
Epic Boards are also a game-changer for managing and visualizing ideal epic workflows, such as authoring workflow states (Draft, Writing, Done), DevOps workflow states (such as Planned, In Development, and In Production), or any other mutually exclusive states you might model with scoped labels. Visualizing workflows with an Epic Board empowers you to increase predictability and efficiency.
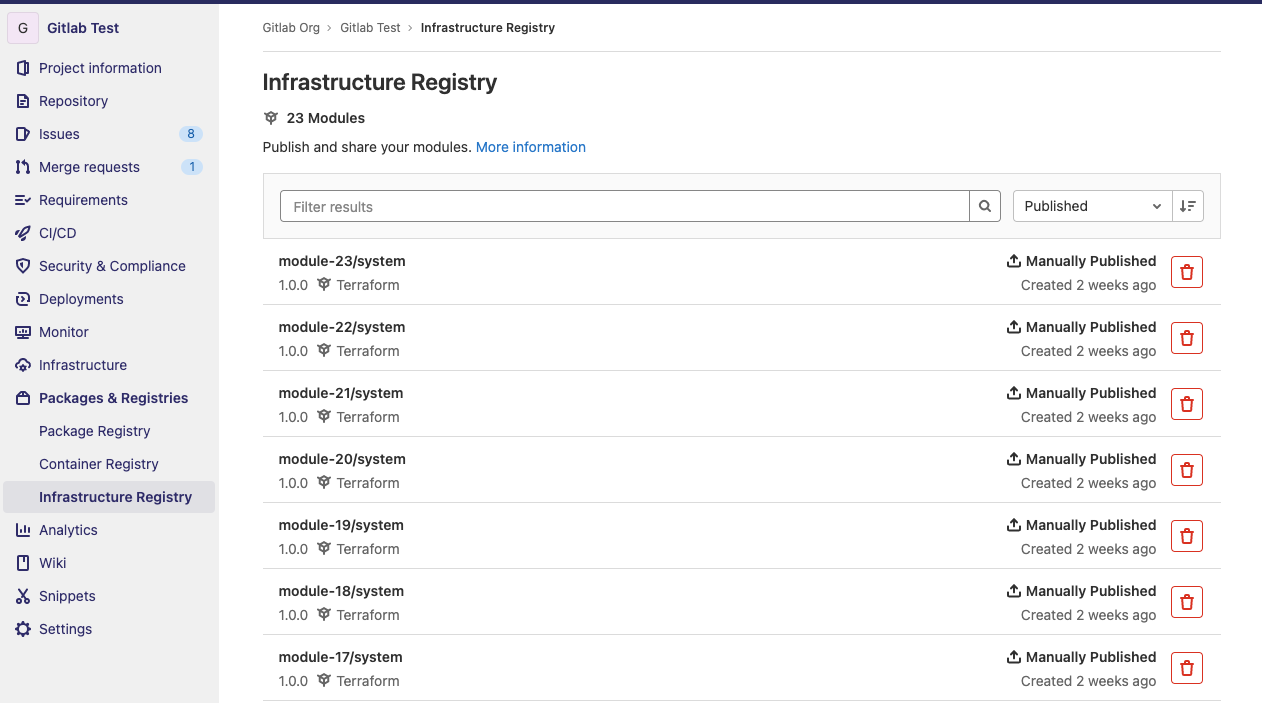
Terraform module registry built into GitLab
Terraform modules play a central role in building standard infrastructure components throughout an organization. Up to GitLab 13.12, GitLab users had to use either a third-party Terraform module registry, local modules, or Git-based modules. While these options work well, they do not help with the distribution of the modules and they lack proper versioning support, which introduces risks for module users. GitLab 14.0 extends our Infrastructure-as-Code offerings with a Terraform module registry. Now, you can use the Terraform module registry built into GitLab to discover Terraform modules with semantic versioning support for upgrades and maintenance. Moreover, you can publish modules easily using GitLab CI/CD.
While following Terraform’s best practices, we recommend developing each Terraform module in a dedicated GitLab project. To simplify the transition to the registry, users can host and publish multiple modules from a single GitLab repository. You can learn more about publishing and consuming a new module in our documentation.
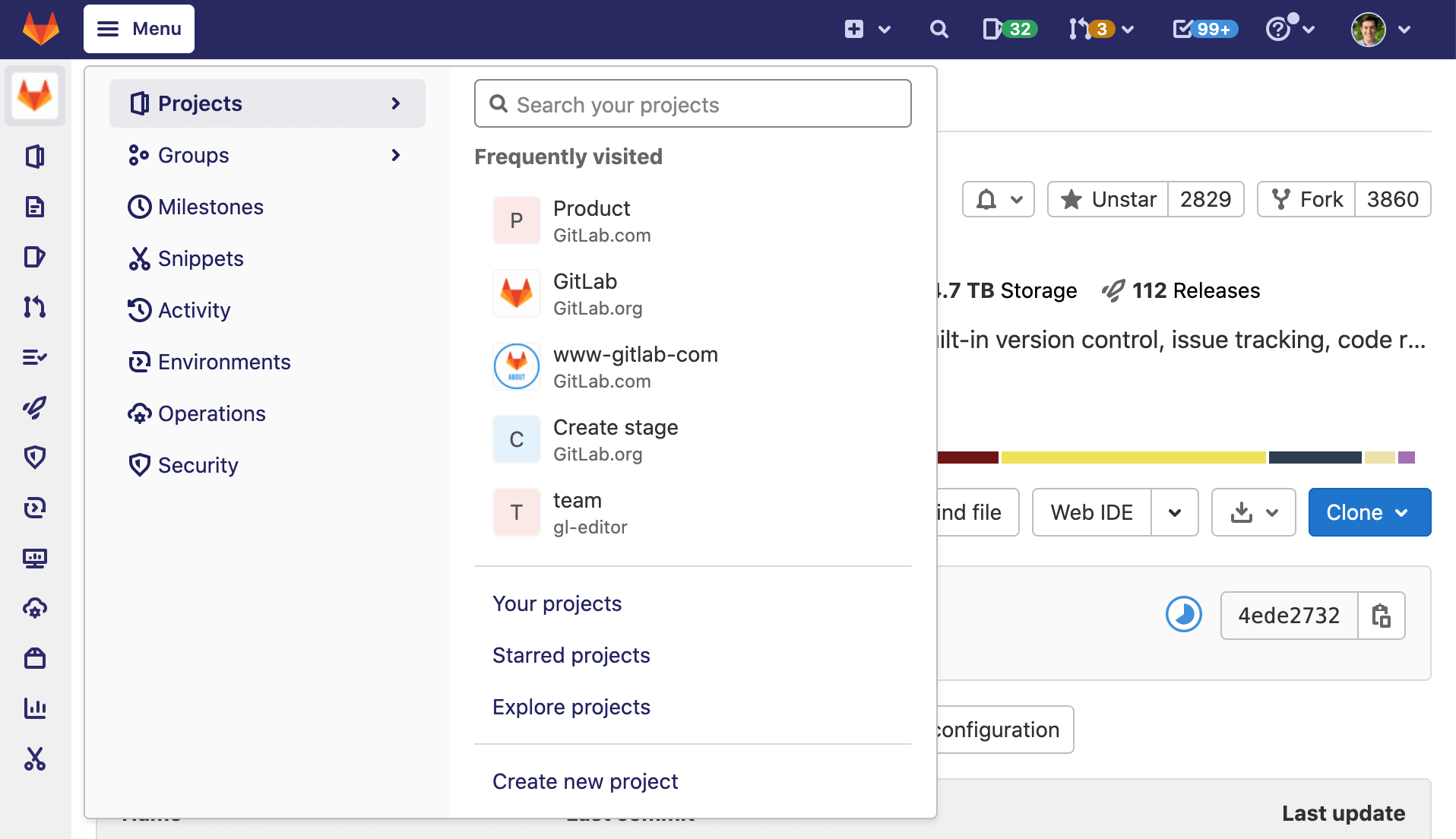
Streamlined top navigation menu
GitLab 14.0 introduces an all-new, streamlined top navigation menu to help you get where you’re going faster and with fewer clicks. This new, consolidated menu offers the combined functionality of the previous Projects, Groups, and More menus. It gives you access to your projects, groups, and instance-level features with a single click. Additionally, all-new responsive views improve the navigation experience on smaller screens.
Merge request reviews in VS Code
As a developer, you often spend a majority of your time working in your local development environment. When you’re assigned a merge request for review, this requires you to leave your editor and perform that review inside of GitLab. While performing your review inside GitLab, you might also need to use your local editor to gain more context on the proposed changes.
GitLab Workflow version 3.21.0 for Visual Studio Code (VS Code) now supports the complete merge request review process, including threads. Select the GitLab icon in VS Code to open the sidebar to display Merge requests I’m reviewing. Select a merge request overview to view the complete details and discussions of the merge request.
The sidebar also contains a list of all the changed files in the merge request. Selecting files opens a diff comparison for you to review the changes in VS Code. While viewing the diff, you can read feedback left on the files, and create new comments by selecting a line number and creating your comment. All comments and feedback you provide in VS Code are available in the GitLab web interface, making it easy for you to perform your reviews in VS Code, and other users to participate in GitLab.
We’re really excited about bringing the complete merge request review process to you inside of VS Code. Let us know what you think by opening an issue for GitLab Workflow.
Sidebar navigation redesign
GitLab is big. And it’s getting bigger. As we’ve introduced new features and categories, navigating the densely-packed left sidebar has become less intuitive.
In GitLab 14.0 we’ve redesigned and restructured the left sidebar for improved usability, consistency, and discoverability. We’ve moved some links to features around, split up features in the Operations menu into three distinct menus, improved visual contrast, and optimized spacing so all the menu items can fit comfortably on a smaller screen. These changes are intended to better match your mental model of the DevOps lifecycle, and provide a more predictable and consistent experience while navigating within your projects and groups.
Edit wiki pages with the WYSIWYG Markdown editor
Editing wiki content could be so much easier! Many GitLab wikis use Markdown formatting, and for some users, Markdown is a barrier to efficient collaboration. In this release, you now have access to a rich, modern Markdown editing experience in your wiki, so you can edit with confidence.
Instant feedback and visual editing tools help make wiki editing more intuitive, and remove barriers to collaboration. GitLab saves the changes as Markdown when you’re done, so users who want to edit the Markdown directly can do so. You can even type Markdown into the new editor and it will automatically format the text as you type.
GitLab 14.0 introduces the Content Editor into the Wiki with support for most of the basic Markdown content types like headers, bold and italic text, lists, code blocks, and links. Full support for the entire GitLab Flavored Markdown specification will arrive in upcoming releases. We also plan to make the Content Editor available in other areas of GitLab in the future. We welcome input on this early MVC in this feedback issue.

Aggregate identical DAST vulnerabilities into a single vulnerability
In GitLab 13.12 and earlier, all DAST vulnerabilities found in a scan were listed individually for each URL the vulnerability was found on. This could create many vulnerabilities when the fix was a single file or configuration change. For example: an issue with a server header sent with every HTTP response would be reported on every page on the site, rather than reported as a single issue with multiple occurrences.
To reduce the overhead of managing vulnerabilities, GitLab combines identical vulnerabilities found on multiple pages into a single reported vulnerability in the DAST report. The vulnerability details include a list of all the URLs where the vulnerability was found, rather than individual vulnerabilities being created in the vulnerability list and dashboard for each page.
This new reporting functionality will not retroactively combine vulnerabilities found in previous scans. It only applies to scans performed in GitLab 14.0 and later.

Cluster management project template
In this release, we are moving away from the CI/CD template-based approach for cluster management. Cluster management is the ability to manage Kubernetes clusters to improve application availability running on a cluster. The old method hides too much of the logic, restricts customizations and extensions of your apps. With the new approach, you can easily create a cluster management project from a project template and fully control your applications. A project created using the new template contains the code needed for cluster management jobs, including built-in support for several applications. You can easily extend the project to other applications and own them completely.
Additionally, new applications will be installed using Helm v3. If you have former GitLab Managed Applications installed using Helm v2, check the Helm migration guide and the GitLab Managed Apps migration guide. The CI/CD job output will also guide you through these migrations.
In GitLab 14.0, the cluster management project supports only certificate-based cluster integrations. We plan to add support for the GitLab Kubernetes Agent in the next release.

Prepopulate the CI/CD pipeline editor with an initial template
The pipeline editor in GitLab is your one-stop shop when interacting with CI/CD pipelines. Previously, when writing your first pipeline with the editor, you were presented with a blank configuration. While perfectly useful for experienced pipeline authors, it was a bit of a leap for those just starting out.
In this release, if a project does not have a pipeline configured, the editor preloads a template showing an example 3-stage pipeline. You can save and run this pipeline right away to see it in action in your project. On top of that, it also has comments that help you understand the syntax, and tips and hints to help you start customizing the template to match your needs. It is now much easier to get your first green pipeline!

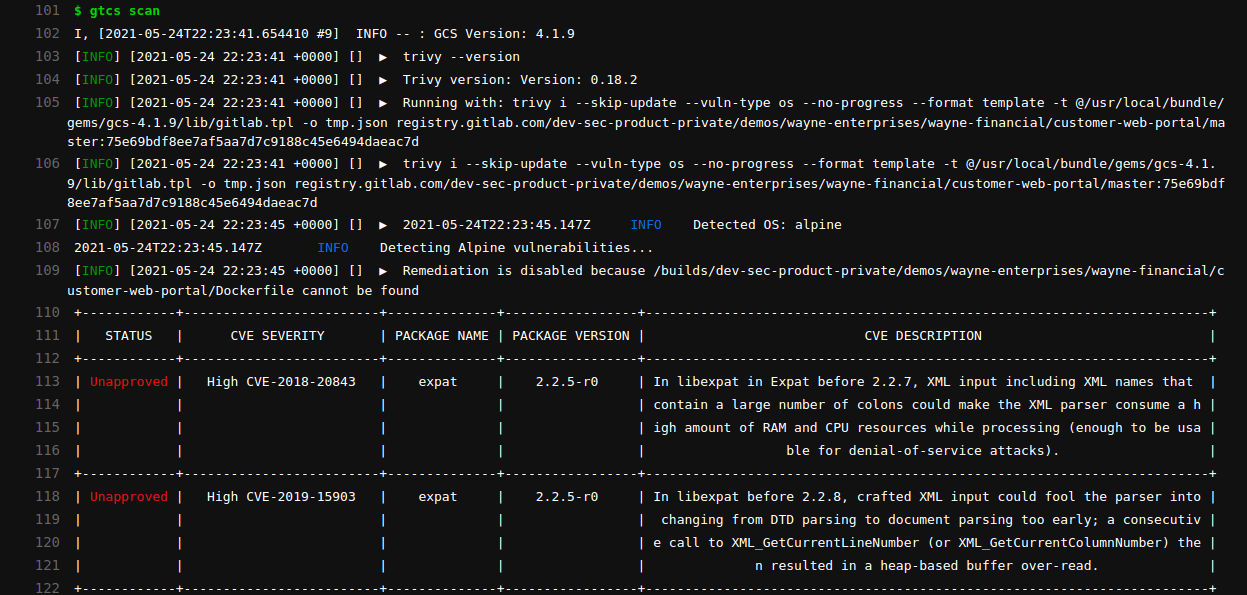
Container Scanning Integration with Trivy
Container scanning in GitLab now uses the Trivy engine by default. This change provides customers with more timely vulnerability intelligence updates, more accurate results, and support for a larger number of operating systems. Users who run container scanning with default settings are switched seamlessly and automatically to the new engine in GitLab 14.0. Users who customize the variables in their container scanning job should review our migration guide and make any necessary updates.
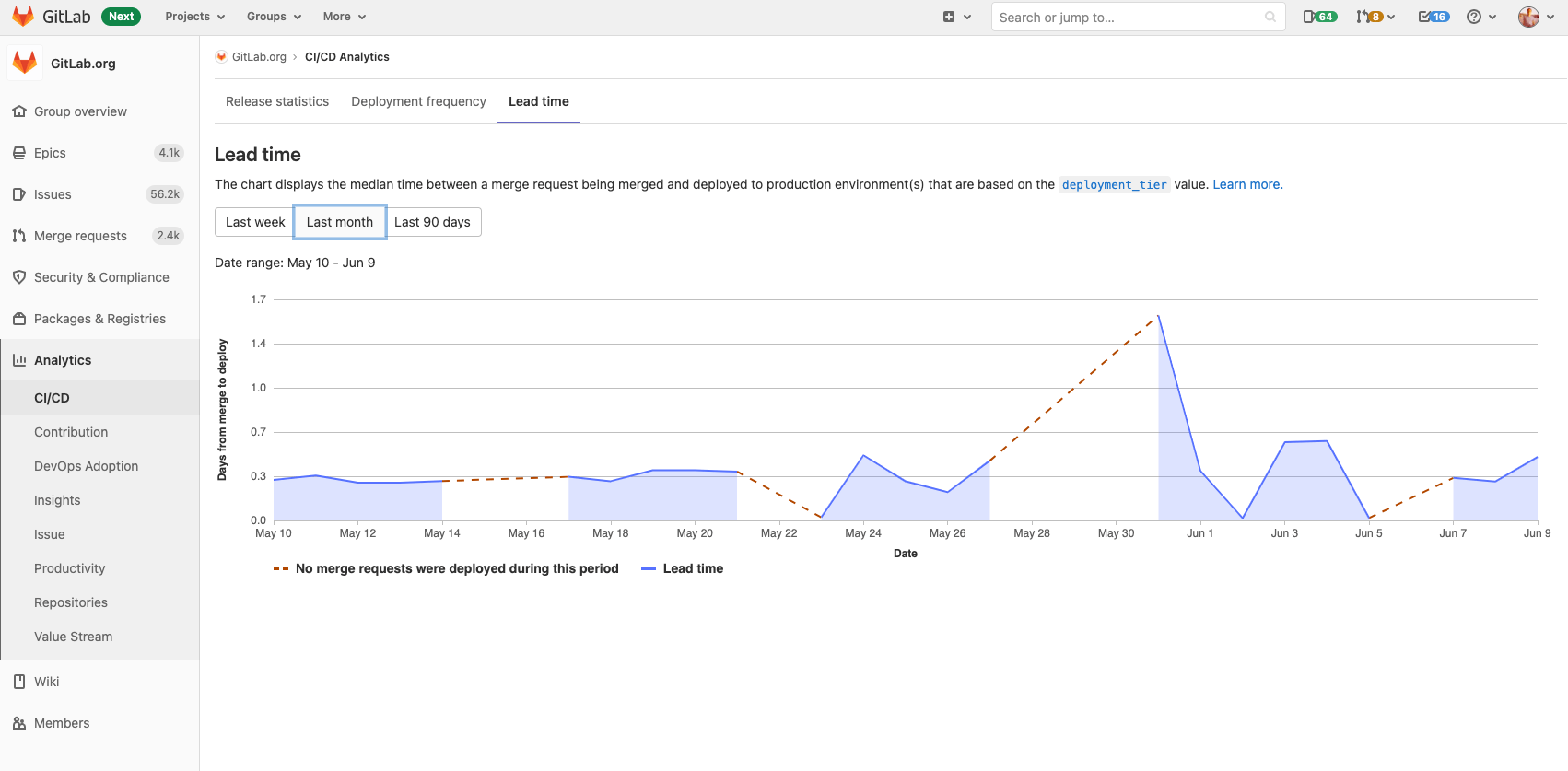
Lead time for merge requests at the group level
As part of our efforts to natively support DORA4 metrics in GitLab, the lead time for merge requests chart is now available at the Group level. This release extends on the work completed in GitLab 13.11; you can now use a chart that shows how long it takes merge requests to be deployed to a production environment (not just in individual projects, but aggregated across a group). This allows you to get a full picture of throughput across multiple projects.
Other improvements in GitLab 14.0
Horizontal navigation for project-level Value Stream Analytics
The stages in project-level value stream analytics are now shown in a horizontal layout. This helps visualize the flow of work through the stages of a value stream. It also matches the navigation experience in group-level value stream analytics.

Improved interface for adding groups to the DevOps Adoption table
The DevOps Adoption table provides insight into how GitLab has been adopted across your organization with a comparison by group and subgroup. Previously, you could add no more than 200 groups to the table. We understand that larger organizations can have thousands of GitLab groups. You can now use a searchable dropdown to add any subgroup to the table.
In addition, subgroups removed from the DevOps Adoption table in one group no longer automatically get removed from the tables of other groups. As a result of the data migration that was done for this fix, you might need to manually re-add some subgroups to your tables the first time that you revisit them.
SSH key expiration enforced by default
Expired SSH keys added to GitLab are now disabled by default. This helps to make your GitLab instance more secure. Previously, expired SSH keys added to GitLab were enabled by default, and could be used unless explicitly disabled by an administrator.
This change affects expired SSH keys used on GitLab.com. If your keys are expired or will expire soon, you need to update the key and any services using them. Our documentation on SSH keys has helpful steps on how to create a new SSH key.
Self-managed administrators can still allow the use of expired keys, similar to how they can allow use of expired personal access tokens.
Track usage of Code Owners
Code Owners are an important piece of the code review process in GitLab. When code owners are clearly identified, contributors can see who should review contributions to a file or repository. The Code Owners feature can also be used to establish a merge request approval process. Now, you can track which teams across your organization are using the Code Owners feature in their development workflow.
If you would like to drive adoption of Code Owners, sort the DevOps Adoption table by the Code Owners column to find teams that haven’t yet adopted the feature so you can easily identify which teams need help getting started. Alternatively, find teams that have successfully configured Code Owners and get tips and feedback. The DevOps Adoption table is available at the group level and the instance level.
Slack notifications for wiki edits include links to diffs
Our Slack notification service can notify you when a user edits a wiki page. The Slack message gives you helpful context about the edit, including the project, page name, and the commit message. Sometimes, however, the commit message doesn’t give enough context, and you need more information about how the content changed.
Now you can click Compare changes in the Slack message to immediately view the diff, saving you time and reducing confusion from ambiguous or incomplete commit messages.
Predefined CI/CD variable for environment action
If you want to reuse scripts and configuration between deployment jobs using the environment: keyword, it can be difficult to exclude certain behaviors based on the type of action the deployment job performs. For example, an environment: action of stop might be a job that is stopping a review_app, and you don’t want your deployment scripts to run.
Now, the value of environment: action: is available as the CI_ENVIRONMENT_ACTION predefined CI/CD variable, making it easier than ever to configure one script that can work for all deployment jobs.
Install PyPI packages from your group or subgroup
You can use your project’s Package Registry to publish and install PyPI packages. When you install a PyPI package, you must specify which project the package resides in. This works well if you have a small number of projects. If you have multiple projects nested within a group, you might quickly find yourself adding dozens or even hundreds of different sources.
For large organizations with many teams, it’s common for a team to publish packages to their project’s Package Registry alongside the source code and pipelines. However, they must also be able to easily install dependencies from other projects within their organization. You can now install packages from your group, so you don’t have to remember which package lives in which project. To do this, use the simple API to specify a package: GET groups/:id/packages/pypi/files/:sha256/:file_identifier.
You can also write the output to a file, or return the package descriptor as an HTML file. Read the docs for more info and let us know how it goes. We hope that this helps to make your team and organization more efficient.
Security report generalized details structure
Automated security scanning is an important part of any secure development process. There are a wide variety of tools and technologies covering the entire SDLC from source code scanning to post-deployment application and infrastructure scanning. While the ultimate goal of any of these tools is to discover both known and potential vulnerabilities, the information coming from any given scanner can vary widely. Efforts to standardize scanning output data do exist but they tend to focus only on one category of scanning technology or even a specific set of tools. This presents a big challenge to security teams who need to aggregate a wide array of scanner findings. Without a consistent way to normalize disparate findings, viewing the unique details for each scanner’s output can be a very apples-and-oranges experience. And if the tool outputs aren’t aggregated, then results are often reviewed in the source tool, leaving the true picture of vulnerability risk fragmented and sitting outside of the rest of the DevOps toolchain.
The new generalized details structure in our security report schemas can bridge this gap. You can already integrate a wide variety of security scanners into GitLab with minimal effort. Now you can go even further with rich formatting options for finding details. Our new structure makes it easy to map most tool’s existing outputs into our JSON report formats while adding consistent presentation logic automatically. Flexibility without sacrificing the ability to provide rich vulnerability finding data is a primary purpose behind the new structure. Details are provided in an open structure using pre-defined data types. The pre-defined types handle both data validation as well as standardized UI presentation inside GitLab. For instance, we provide types such as Integer, URL, Table, and even GFM (GitLab Flavored Markdown). This allows granular control over how finding details are presented while keeping the overall experience inside GitLab consistent.

Feature Flags User List is now on its own page
Previously, to access the user lists, you had to navigate to a separate tab under the Feature Flags page. This design obscured the relationship between feature flags and user lists since user lists are a sub-feature of feature flags. In this release, user lists are now under a subpage of Feature Flags, which improves the workflow and makes their relationship more clear.

Dynamically update the Incident Service Level Agreement Timer
The Incident Service Level Agreement (SLA) Timer, introduced in GitLab 13.5, shows the time remaining until an SLA violation for an incident. However, the user had to refresh the page to update the timer. Starting in GitLab 14.0, the timer updates dynamically every 15 minutes without the need for a page refresh.
Database load balancing moved to Free
GitLab’s database load balancer enables the distribution of read-only queries across multiple database servers. For GitLab instances with thousands of users, using the load balancer can reduce the load on the primary database and increase responsiveness, thus resulting in faster page load inside GitLab.
In this release, we moved the load balancer from Premium to Free to allow more users to benefit from this feature.
Geo support for PostgreSQL high availability in GA
Patroni is a solution for PostgreSQL high availability, which also allows the configuration of a highly-available PostgreSQL standby cluster on a Geo secondary. This configuration is important when a secondary is used as part of a disaster recovery strategy, because it allows systems administrators to mirror the number of database nodes on the primary and secondary site. This means that after a failover, no additional database nodes must be provisioned to regain high availability.
Geo now provides generally available support for highly-available PostgreSQL configurations using Patroni.
We have improved documentation, upgraded to use Patroni version 2.0.2, added database load balancing support on standby clusters, and ensured that the command to pause and resume replication works with a Patroni standby cluster.
GitLab upgraded to Ruby on Rails 6.1
In this release, we upgraded Ruby on Rails to version 6.1 to take advantage of the latest improvements of the application framework. Please refer to the Ruby on Rails 6.1 release notes for more details.
Performance bar shows how much memory is used
The performance bar allows systems administrators and software developers to understand the performance of a GitLab page.
Increasing the visibility of memory used is important for software developers, so they can improve the performance and user experience of GitLab. In this release, we’ve added a memory field that shows the amount of memory consumed and objects allocated for the current request. When selected, a view is displayed with additional information. With this information available, software developers can spot memory issues earlier and develop more memory-efficient and performant features.
Redesign for Geo sites dashboard
Geo replicates and verifies many different data types. System administrators need to monitor the health of their Geo sites to know whether there are any issues requiring attention, such as projects that failed to sync, or checksum mismatches. In our UX research, we found that administrators using the Geo admin page often had trouble finding the information they needed, and that the information displayed could be confusing. Our redesigned Geo sites dashboard addresses these pain points. We have added more useful indicators such as sync and verification summaries for data types, and verification status bars for individual data type components. We have also improved how the page is organized, reducing the number of clicks needed to surface important information.

Identify provisioned users at group level
In this release, we have added the ability to identify provisioned users and contributors. A new Enterprise label is displayed against provisioned users. This helps users identify accounts that a group created via SCIM automation instead of accounts created manually by a user.
Instance-level DevOps Adoption report enabled by default
Instance-level DevOps Adoption report is now enabled by default. The DevOps Adoption report shows which teams in your organization are using GitLab:
- Issues
- Merge requests
- Approvals
- Runners
- Pipelines
- Deploys
- Scanning
Compare GitLab adoption across your entire organization by adding groups to the adoption table. Here are just a few of the ways you can use the DevOps Adoption report:
- Verify whether you are getting the return on investment that you expected from GitLab.
- Identify specific groups that are lagging in their adoption of GitLab so you can help them along in their DevOps journey.
- Identify groups that have adopted specific features, such as pipelines, and provide tips to other groups interested in getting started with these features.
This is just the beginning of an exciting vision to measure DevOps adoption in your organization and evaluate the benefits. To learn about the additions that are coming next, read the epic.
The DevOps Adoption report is also available at the group level. For SaaS users, get adoption insights for your entire organization by viewing the DevOps Adoption report in your top-level group.
Set pronouns on GitLab user profiles
Pronouns have been added to GitLab user profiles. The pronouns appear next to user names in the Profile tab. You can:
- Decide whether or not to add pronouns to your profile.
- Self-identify and enter whatever pronouns you prefer, without selecting from a predefined list.
Besides being more inclusive, GitLab wants help people use the correct pronouns when replying to comments to respect people’s identity.
Edit default path and project name when forking
Forking a project enables you to have an exact copy of an original repository where you can experiment, apply changes, and submit contributions to the parent project. Your forks should have meaningful names that explain their goals, and if your project is diverging, you may need multiple forks of a single project.
In this release, GitLab now supports editing the project name and project slug directly when you create a fork. You can now create multiple forks of the same project, each with a different name, all in the same group!
Add ‘~’ to supported characters for CI/CD variable masking
Securely managing secrets stored in CI/CD variables is a must. You can hide variable values in job logs by masking the variables, but GitLab only support certain characters. Now we support masking variables with ‘~’ in the value, which expands the feature to support more secrets generated from other secrets provider platforms. Thank you to dallmair for the community contribution!
Identify which jobs triggered downstream pipelines
Previously, when looking at the pipeline view, it was difficult to determine which job triggered a downstream pipeline. Starting in 14.0, every downstream pipeline shows the name of the job that triggered it. This makes it easier to track the execution flow in complex pipelines that trigger downstream pipelines.
Delete associated package files via UI
You use the GitLab Package Registry to publish, install, and share your dependencies. When you publish a dependency, it generates several files including the package archive. Prior to GitLab 14.0, to delete such files you had to use the API. In GitLab 14.0, you can now use the UI to delete files related to a given package, and the package itself.
Since maintaining a tidy registry can be challenging, our goal is to make the process easier and more efficient for you by adding more options for how to delete unused files.
Pin to Specific SAST Analyzer Versions
With the maturity of GitLab Secure scanning tools, we’ve needed to add more granularity to our release process. Previously, GitLab shared a major version number for all our analyzers and tools. This requires all tools to share a major version and prevent the use of semantic version numbering. Beginning in 14.0 GitLab SAST removed the SAST_ANALYZER_IMAGE_TAG global variable in our managed SAST.gitlab-ci.yml CI template in favor of the analyzer job variable setting the ‘major.minor’ tag in the SAST vendored template. Each analyzer job now has a scoped SAST_ANALYZER_IMAGE_TAG variable which will be actively managed by GitLab and set to the ‘major’ tag for the respective analyzer. To pin to a specific version you simply change the variable value to the specific version tag.
If you override or maintain custom versions of SAST.gitlab-ci.yml you will want to update your CI templates to stop referencing the global SAST_ANALYZER_IMAGE_TAG and move it to a scoped analyzer job tag. We strongly encourage inheriting and overriding our managed CI templates to future-proof your CI templates. This change will allow you to more granularly control future analyzer updates with a pinned major.minor version.
Static Analysis Analyzer Updates
GitLab Static Analysis is comprised of a set of many security analyzers that the GitLab Static Analysis team actively manages, maintains, and updates. Below are the analyzer updates released during 14.0. These updates bring additional coverage, bug fixes, and improvements.
- Semgrep updated to version 2.8.0 - MR, Changelog
- Fixed wrong line numbers for multi line generic mode
SAST_EXCLUDED_PATHSis passed to semgrep to exclude as semgrep runs- Performance optimizations
- Add a url to primary identifier of a rule in the report to link to underlying rule
- GoSec updated to version 3.1.0 - MR, Changelog
- Remove
SAST_GOSEC_CONFIGsupport, deprecation notice - Add
COMPILEvariable to support skipping dependency fetching when desired - Add
GOSEC_GO_PKG_PATHvariable to give the option to set where go builds the app - Update dependency fetching to only download packages and not build/install by default
- Remove
- Flawfinder updated to version 2.0.17 - MR, Changelog
- SpotBugs updated to version 2.28.3 - MR, Changelog
- Updated dependencies
- PMD-Apex updated to version 2.12.3 - MR, Changelog
- Improved rule accuracy, bug fixes
- ESLint updated to version 7.27.0 - MR, Changelog
- Please note, this analyzer is planned to be replaced by Semgrep in an upcoming release.
If you are including the GitLab managed vendored SAST template (SAST.gitlab-ci.yml) you do not need to do anything to receive these updates. However, if you override or customize your own CI template, you will need to update your CI configurations. If you want to remain on a specific version of any analyzer, you can now pin to a minor version of an analyzer. Pinning to a previous version will prevent you from receiving automatic analyzer updates and require you to manually bump your analyzer version in your CI template.
Change an issue’s type
In some cases, you may wish to change an issue’s type. For example, you may want to escalate an issue to an incident to ensure that your team handles the problem properly. To change an issue’s type, edit the issue and select an issue type from the Issue type selector menu.

Container Scanning Integration with Grype
GitLab container scanning can now optionally use the Grype scanning engine instead of the default Trivy engine. This gives users flexibility and choice in selecting their container scanning engine. We did a comparison of the two open source scanners. However, as each scanner is unique, you may wish to do your own comparison to decide which is best for you. Users can try the Grype scanner by setting the CI variable CS_ANALYZER_IMAGE: registry.gitlab.com/security-products/container-scanning/grype:4.

Geo requires confirmation before resyncing all projects
The Geo Admin UI provides a button to Resync All projects. For customers with a large amount of projects trying to resync only failed repositories, unintentionally triggering this option can cause significant delays in troubleshooting. We now display a confirmation modal whenever Resync All is selected. This small, but impactful, UX improvement reduces the likelihood that administrators will accidentally trigger a resync of all their projects.

GitLab chart improvements
- With GitLab 14.0, it is expected the minimum version of Kubernetes to be 1.16.
- Previously, the Kubernetes Agent Server (KAS) deployment had no way of specifying an imagePullSecret. This would cause K8s to fail as not authorized. Now, with pullSecrets present the image fetch succeeds and the Pods start.
- GitLab 14.0 upgrades Cert Manager to 1.2.0.
- GitLab 14.0 upgrades Grafana to chart version to 6.9.1. Chart-deployed Grafana features are now on par with Omnibus (on 7.5.5) and resolves a deprecation issue.
Omnibus improvements
- GitLab 14.0 includes Mattermost 5.35.3, an open source Slack alternative. Due to the introduction of backend database architecture required for upcoming new features, the performance of the migration process for the v5.35 release is noticeably affected. Depending on the size, type, and version of the database, you should expect longer than usual upgrade times. This can vary from a couple of minutes (average case) to hours (worst case, MySQL 5.x only). You should also expect a moderate to significant spike in database CPU usage during this process. More details on the performance impact of the migration and possible mitigation strategies are provided in this post. v5.35.3 introduces a new feature to search for files and some changes to password generation logic used during bulk user import. Admins should immediately reset the passwords for all users generated during the bulk import process, and whose password has not been changed even once. v5.35.3 also contains a high level security fix, and upgrading is recommended.
- Previously, new GitLab instances would prompt users for the initial root password by default after installation, which meant an anonymous user could get there first to set a root password and take control. Now, an initial root password will be randomly created if one isn’t provided by the user. This improves the default security of newly deployed GitLab instances.
- The Omnibus GitLab docker image now includes BusyBox but removes vim and nano as pre-installed editors. BusyBox brings together minimal versions of lots of other tools, and by making BusyBox our default editor, we get many other tools that are useful when debugging inside of a container.
Project storage location available in REST and GraphQL APIs
When Hashed Storage was introduced, it became more difficult to discover the storage location of projects. Systems administrators were able to look up the path on the project’s admin UI, but it was impractical to do this for many projects. In this release, we’ve added API endpoints that expose a project’s storage information. In the REST API, this new endpoint is GET /projects/:id/storage. For GraphQL, the diskPath field is now available in the Repository object.
Bug Fixes
Some of the notable bug fixes in 14.0 are:
Performance improvements
In every release, we continue to make great strides improving GitLab’s performance. We’re committed to making every GitLab instance faster. This includes GitLab.com, an instance with over 1 million users!
In GitLab 14.0, we’re shipping performance improvements for issues, projects, milestones, and much more! Some improvements in GitLab 14.0 are:
Usability Improvements
In every release, we work on improving the overall effectiveness and usefulness of our product.
We also have a UI Polish gallery to track important updates to our interfaces. These updates, while often small, improve your user experience.
In GitLab 14.0, we’re shipping usability improvements for issues, projects, milestones, and much more! We highlight the following changes in GitLab 14.0:
Deprecations
NFS for Git repository storage deprecated
With the general availability of Gitaly Cluster (introduced in GitLab 13.0), we have deprecated development (bugfixes, performance improvements, etc) for NFS for Git repository storage in GitLab 14.0. We will continue to provide technical support for NFS for Git repositories throughout 14.x, but we will remove all support for NFS in GitLab 15.0. Please see our official Statement of Support for further information.
Gitaly Cluster offers tremendous benefits for our customers such as:
We encourage customers currently using NFS for Git repositories to plan their migration by reviewing our documentation on migrating to Gitaly Cluster.
Planned removal date: Jun 22, 2022
Removals
Breaking changes to Terraform CI template
GitLab 14.0 renews the Terraform CI template to the latest version. The new template is set up for the GitLab Managed Terraform state, with a dependency on the GitLab terraform-images image, to provide a good user experience around GitLab’s Infrastructure-as-Code features.
The current stable and latest templates are not compatible, and the current latest template becomes the stable template beginning with GitLab 14.0, your Terraform pipeline might encounter an unexpected failure if you run a custom init job.
Removal date: June 22, 2021
Code Quality RuboCop support changed
By default, the Code Quality feature has not provided support for Ruby 2.6+ if you’re using the Code Quality template. To better support the latest versions of Ruby, the default RuboCop version is updated to add support for Ruby 2.4 through 3.0. As a result, support for Ruby 2.1, 2.2, and 2.3 is removed. You can re-enable support for older versions by customizing your configuration.
Relevant Issue: Default codeclimate-rubocop engine does not support Ruby 2.6+
Removal date: June 22, 2021
Container Scanning Engine Clair
Clair, the default container scanning engine, was deprecated in GitLab 13.9 and is removed from GitLab 14.0 and replaced by Trivy. We advise customers who are customizing variables for their container scanning job to follow these instructions to ensure that their container scanning jobs continue to work.
Removal date: June 22, 2021
DAST environment variable renaming and removal
GitLab 13.8 renamed multiple environment variables to support their broader usage in different workflows. In GitLab 14.0, the old variables have been permanently removed and will no longer work. Any configurations using these variables must be updated to the new variable names. Any scans using these variables in GitLab 14.0 and later will fail to be configured correctly. These variables are:
DAST_AUTH_EXCLUDE_URLSbecomesDAST_EXCLUDE_URLS.AUTH_EXCLUDE_URLSbecomesDAST_EXCLUDE_URLS.AUTH_USERNAMEbecomesDAST_USERNAME.AUTH_PASSWORDbecomesDAST_PASSWORD.AUTH_USERNAME_FIELDbecomesDAST_USERNAME_FIELD.AUTH_PASSWORD_FIELDbecomesDAST_PASSWORD_FIELD.DAST_ZAP_USE_AJAX_SPIDERwill now beDAST_USE_AJAX_SPIDER.DAST_FULL_SCAN_DOMAIN_VALIDATION_REQUIREDwill be removed, since the feature is being removed.
Removal date: Jun 22, 2021
Default Browser Performance testing job renamed in GitLab 14.0
Browser Performance Testing has run in a job named performance by default. With the introduction of Load Performance Testing in GitLab 13.2, this naming could be confusing. To make it clear which job is running Browser Performance Testing, the default job name is changed from performance to browser_performance in the template in GitLab 14.0.
Relevant Issue: Rename default Browser Performance Testing job
Removal date: June 22, 2021
Default DAST spider begins crawling at target URL
In GitLab 14.0, DAST has removed the current method of resetting the scan to the hostname when starting to spider. Prior to GitLab 14.0, the spider would not begin at the specified target path for the URL but would instead reset the URL to begin crawling at the host root. GitLab 14.0 changes the default for the new variable DAST_SPIDER_START_AT_HOST to false to better support users’ intention of beginning spidering and scanning at the specified target URL, rather than the host root URL. This change has an added benefit: scans can take less time, if the specified path does not contain links to the entire site. This enables easier scanning of smaller sections of an application, rather than crawling the entire app during every scan.
Removal date: Jun 22, 2021
Default branch name for new repositories now main
Every Git repository has an initial branch, which is named master by default. It’s the first branch to be created automatically when you create a new repository. Future Git versions will change the default branch name in Git from master to main. In coordination with the Git project and the broader community, GitLab has changed the default branch name for new projects on both our SaaS (GitLab.com) and self-managed offerings starting with GitLab 14.0. This will not affect existing projects.
GitLab has already introduced changes that allow you to change the default branch name both at the instance level (for self-managed users) and at the group level (for both SaaS and self-managed users). We encourage you to make use of these features to set default branch names on new projects.
For more information, see the related epic and related blog post.
Removal date: Jun 22, 2021
Deprecated GraphQL fields have been removed
In accordance with our GraphQL deprecation and removal process, the following fields that were deprecated prior to 13.7 are fully removed in 14.0:
Mutations::Todos::MarkAllDone,Mutations::Todos::RestoreMany-:updated_idsMutations::DastScannerProfiles::Create,Types::DastScannerProfileType-:global_idTypes::SnippetType-:blobEE::Types::GroupType,EE::Types::QueryType-:vulnerabilities_count_by_day_and_severityDeprecatedMutations (concern**)-AddAwardEmoji,RemoveAwardEmoji,ToggleAwardEmojiEE::Types::DeprecatedMutations (concern***)-Mutations::Pipelines::RunDastScan,Mutations::Vulnerabilities::Dismiss,Mutations::Vulnerabilities::RevertToDetected
Removal date: Jun 22, 2021
Deprecations for Dependency Scanning
As mentioned in 13.9 and this blog post several removals for Dependency Scanning take effect.
Previously, to exclude a DS analyzer, you needed to remove it from the default list of analyzers, and use that to set the DS_DEFAULT_ANALYZERS variable in your project’s CI template. We determined it should be easier to avoid running a particular analyzer without losing the benefit of newly added analyzers. As a result, we ask you to migrate from DS_DEFAULT_ANALYZERS to DS_EXCLUDED_ANALYZERS when it is available. Read about it in issue #287691.
Previously, to prevent the Gemnasium analyzers to fetch the advisory database at runtime, you needed to set the GEMNASIUM_DB_UPDATE variable. However, this is not documented properly, and its naming is inconsistent with the equivalent BUNDLER_AUDIT_UPDATE_DISABLED variable. As a result, we ask you to migrate from GEMNASIUM_DB_UPDATE to GEMNASIUM_UPDATE_DISABLED when it is available. Read about it in issue #215483.
Removal date: June 22, 2021
Drop updated_at filter from Deployment API
If you are pulling data from the project deployments API endpoint to populate a custom-built dashboard in GitLab, you may have noticed that there is no way to restrict the API results to display only the latest changes. To overcome this, you had to retrieve all records, check the results one-by-one, and process only the records updated after the latest updated_at value in the last batch retrieved. In order to make this process more efficient and performant, this API is changing in GitLab 14.0. The updated_after and updated_before parameters will be replaced by finished_after and finished_before parameters. This will enable users to more efficiently choose the deployments they are interested in retrieving.
Removal date: June 22, 2021
External Pipeline Validation Service Code Changes
For self-managed instances using the experimental external pipeline validation service, the range of error codes GitLab accepts will be reduced. Currently, pipelines are invalidated when the validation service returns a response code from 400 to 499. In GitLab 14.0 and later, pipelines will be invalidated for the 406: Not Accepted response code only.
Removal date: Jun 22, 2021
Geo Foreign Data Wrapper settings removed
As announced in GitLab 13.3, the following configuration settings in /etc/gitlab/gitlab.rb have been removed in 14.0:
geo_secondary['db_fdw']geo_postgresql['fdw_external_user']geo_postgresql['fdw_external_password']gitlab-_rails['geo_migrated_local_files_clean_up_worker_cron']
Removal date: June 22, 2021
GitLab OAuth implicit grant deprecation
GitLab is deprecating the OAuth 2 implicit grant flow as it has been removed for OAuth 2.1.
Beginning in 14.0, new applications can’t be created with the OAuth 2 implicit grant flow. Existing OAuth implicit grant flows are no longer supported in 14.4. Migrate your existing applications to other supported OAuth2 flows before release 14.4.
Removal date: June 22, 2021
GitLab Runner helper image in GitLab.com Container Registry
In 14.0, we are now pulling the GitLab Runner helper image from the GitLab Container Registry instead of Docker Hub. Refer to issue #27218 for details.
Removal date: Jun 22, 2021
GitLab Runner installation to ignore the skel directory
In GitLab Runner 14.0, the installation process will ignore the skel directory by default when creating the user home directory. Refer to issue #4845 for details.
Removal date: Jun 22, 2021
Gitaly Cluster SQL primary elector has been removed
Now that Praefect supports a primary election strategy for each repository, we have removed the sql election strategy.
The per_repository election strategy is the new default, which is automatically used if no election strategy was specified.
If you had configured the sql election strategy, you must follow the migration instructions before upgrading to 14.0.
Removal date: Jun 22, 2021
Helm v2 support
Helm v2 was officially deprecated in November of 2020, with the stable repository being de-listed from the Helm Hub shortly thereafter. With the release of GitLab 14.0, which will include the 5.0 release of the GitLab Helm chart, Helm v2 will no longer be supported.
Users of the chart should upgrade to Helm v3 to deploy GitLab 14.0 and later.
Removal date: June 22, 2021
Legacy feature flags removed
Legacy feature flags became read-only in GitLab 13.4. GitLab 14.0 removes support for legacy feature flags, so you must migrate them to the new version. You can do this by first taking a note (screenshot) of the legacy flag, then deleting the flag through the API or UI (you don’t need to alter the code), and finally create a new Feature Flag with the same name as the legacy flag you deleted. Also, make sure the strategies and environments match the deleted flag. We created a video tutorial to help with this migration.
Removal date: June 22, 2021
Legacy storage removed
As announced in GitLab 13.0, legacy storage has been removed in GitLab 14.0.
Removal date: June 22, 2021
Limit projects returned in GET /groups/:id/
To improve performance, we are limiting the number of projects returned from the GET /groups/:id/ API call to 100. A complete list of projects can still be retrieved with the GET /groups/:id/projects API call.
Removal date: June 22, 2021
Make pwsh the default shell for newly-registered Windows Runners
In GitLab Runner 13.2, PowerShell Core support was added to the Shell executor. In 14.0, PowerShell Core, pwsh is now the default shell for newly-registered Windows runners. Windows CMD will still be available as a shell option for Windows runners. Refer to issue #26419 for details.
Removal date: Jun 22, 2021
Migrate from SAST_DEFAULT_ANALYZERS to SAST_EXCLUDED_ANALYZERS
Until GitLab 13.9, if you wanted to avoid running one particular GitLab SAST analyzer, you needed to remove it from the long string of analyzers in the SAST.gitlab-ci.yml file and use that to set the SAST_DEFAULT_ANALYZERS variable in your project’s CI file. If you did this, it would exclude you from future new analyzers because this string hard codes the list of analyzers to execute. We avoid this problem by inverting this variable’s logic to exclude, rather than choose default analyzers.
Beginning with 13.9, we migrated to SAST_EXCLUDED_ANALYZERS in our SAST.gitlab-ci.yml file. We encourage anyone who uses a customized SAST configuration in their project CI file to migrate to this new variable. If you have not overridden SAST_DEFAULT_ANALYZERS, no action is needed. The CI/CD variable SAST_DEFAULT_ANALYZERS has been removed in GitLab 14.0, which released on June 22, 2021.
Removal date: June 22, 2021
New Terraform template version
As we continuously develop GitLab’s Terraform integrations, to minimize customer disruption, we maintain two GitLab CI/CD templates for Terraform:
- The “latest version” template, which is updated frequently between minor releases of GitLab (such as 13.10, 13.11, etc).
- The “major version” template, which is updated only at major releases (such as 13.0, 14.0, etc).
At every major release of GitLab, the “latest version” template becomes the “major version” template, inheriting the “latest template” setup. As we have added many new features to the Terraform integration, the new setup for the “major version” template can be considered a breaking change.
The latest template supports the Terraform Merge Request widget and doesn’t need additional setup to work with the GitLab managed Terraform state.
To check the new changes, see the new “major version” template.
Removal date: June 22, 2021
OpenSUSE Leap 15.1
Support for OpenSUSE Leap 15.1 is being deprecated. Support for 15.1 will be dropped in 14.0. We are now providing support for openSUSE Leap 15.2 packages.
Removal date: June 22, 2021
PostgreSQL 11 support
PostgreSQL 12 will be the minimum required version in GitLab 14.0. It offers significant improvements to indexing, partitioning, and general performance benefits.
Starting in GitLab 13.7, all new installations default to version 12. From GitLab 13.8, single-node instances are automatically upgraded as well. If you aren’t ready to upgrade, you can opt out of automatic upgrades.
Removal date: June 22, 2021
Removal of deprecated trace parameter from jobs API endpoint
GitLab Runner was updated in GitLab 13.4 to internally stop passing the trace parameter to the /api/jobs/:id endpoint. GitLab 14.0 deprecates the trace parameter entirely for all other requests of this endpoint. Make sure your GitLab Runner version matches your GitLab version to ensure consistent behavior.
Removal date: Jun 22, 2021
Removal of legacy fields from DAST report
As a part of the migration to a common report format for all of the Secure scanners in GitLab, DAST is making changes to the DAST JSON report. Certain legacy fields were deprecated in 13.8 and have been completely removed in 14.0. These fields are @generated, @version, site, and spider. This should not affect any normal DAST operation, but does affect users who consume the JSON report in an automated way and use these fields. Anyone affected by these changes, and needs these fields for business reasons, is encouraged to open a new GitLab issue and explain the need.
For more information, see the removal issue.
Removal date: Jun 22, 2021
Removal of legacy storage for GitLab Pages
To make GitLab Pages cloud-native compatible, starting in GitLab 14.0, we’re changing the underlying storage architecture used by GitLab Pages to the recently introduced ZIP storage.
The migration to the new ZIP archives architecture is designed to be automatic, however, if after the migration you see 404 Not Found for some Pages, the automatic migration has probably failed. To ease this transition to ZIP storage, we’ve provided a temporary use_legacy_storage flag from GitLab 14.0 to 14.2, but we will remove it in GitLab 14.3. This flag will allow GitLab and GitLab Pages to use the non-ZIP deployments to serve content.
Removal date: September 22, 2021
Removal of release description in the Tags API
GitLab 14.0 removes support for the release description in the Tags API. You can no longer add a release description when creating a new tag. You also can no longer create or update a release through the Tags API. Please migrate to use the Releases API instead.
Removal date: June 22, 2021
Removals for License Compliance
In 13.0, we deprecated the License-Management CI template and renamed it License-Scanning. We have been providing backward compatibility by warning users of the old template to switch. Now in 14.0, we are completely removing the License-Management CI template. Read about it in issue #216261 or this blog post.
Removal date: June 22, 2021
Remove DAST default template stages
In GitLab 14.0, we’ve removed the stages defined in the current DAST.gitlab-ci.yml template to avoid the situation where the template overrides manual changes made by DAST users. We’re making this change in response to customer issues where the stages in the template cause problems when used with customized DAST configurations. Because of this removal, gitlab-ci.yml configurations that do not specify a dast stage must be updated to include this stage.
Removal date: Jun 22, 2021
Remove SAST analyzer SAST_GOSEC_CONFIG variable in favor of custom rulesets
With the release of SAST Custom Rulesets in GitLab 13.5 we allow greater flexibility in configuration options for our Go analyzer (GoSec). As a result we no longer plan to support our less flexible SAST_GOSEC_CONFIG analyzer setting. This variable was deprecated in GitLab 13.10.
GitLab 14.0 removes the old SAST_GOSEC_CONFIG variable. If you use or override SAST_GOSEC_CONFIG in your CI file, update your SAST CI configuration or pin to an older version of the GoSec analyzer. We strongly encourage inheriting and overriding our managed CI templates to future-proof your CI templates.
Removal date: June 22, 2021
Remove Ubuntu 19.10 (Eoan Ermine) package
Ubuntu 19.10 (Eoan Ermine) reached end of life on Friday, July 17, 2020. In GitLab Runner 14.0, Ubuntu 19.10 (Eoan Ermine) is no longer available from our package distribution. Refer to issue #26036 for details.
Removal date: Jun 22, 2021
Remove /usr/lib/gitlab-runner symlink from package
In GitLab Runner 13.3, a symlink was added from /user/lib/gitlab-runner/gitlab-runner to /usr/bin/gitlab-runner. In 14.0, the symlink has been removed and the runner is now installed in /usr/bin/gitlab-runner. Refer to issue #26651 for details.
Removal date: Jun 22, 2021
Remove ?w=1 URL parameter to ignore whitespace changes
To create a consistent experience for users based on their preferences, support for toggling whitespace changes via URL parameter has been removed in GitLab 14.0.
Removal date: Jun 22, 2021
Remove FF_RESET_HELPER_IMAGE_ENTRYPOINT feature flag
In 14.0, we have deactivated the FF_RESET_HELPER_IMAGE_ENTRYPOINT feature flag. Refer to issue #26679 for details.
Removal date: Jun 22, 2021
Remove FF_SHELL_EXECUTOR_USE_LEGACY_PROCESS_KILL feature flag
In GitLab Runner 13.1, issue #3376, we introduced sigterm and then sigkill to a process in the Shell executor. We also introduced a new feature flag, FF_SHELL_EXECUTOR_USE_LEGACY_PROCESS_KILL, so you can use the previous process termination sequence. In GitLab Runner 14.0, issue #6413, the feature flag has been removed.
Removal date: Jun 22, 2021
Remove FF_USE_GO_CLOUD_WITH_CACHE_ARCHIVER feature flag
GitLab Runner 14.0 removes the FF_USE_GO_CLOUD_WITH_CACHE_ARCHIVER feature flag. Refer to issue #27175 for details.
Removal date: Jun 22, 2021
Remove secret_detection_default_branch job
To ensure Secret Detection was scanning both default branches and feature branches, we introduced two separate secret detection CI jobs (secret_detection_default_branch and secret_detection) in our managed Secret-Detection.gitlab-ci.yml template. These two CI jobs created confusion and complexity in the CI rules logic. This deprecation moves the rule logic into the script section, which then determines how the secret_detection job is run (historic, on a branch, commits, etc).
If you override or maintain custom versions of SAST.gitlab-ci.yml or Secret-Detection.gitlab-ci.yml, you must update your CI templates. We strongly encourage inheriting and overriding our managed CI templates to future-proof your CI templates. GitLab 14.0 no longer supports the old secret_detection_default_branch job.
Removal date: June 22, 2021
Remove disk source configuration for GitLab Pages
GitLab Pages API-based configuration has been available since GitLab 13.0. It replaces the unsupported disk source configuration removed in GitLab 14.0, which can no longer be chosen. You should stop using disk source configuration, and move to gitlab for an API-based configuration. To migrate away from the ‘disk’ source configuration, set gitlab_pages['domain_config_source'] = "gitlab" in your /etc/gitlab/gitlab.rb file. We recommend you migrate before updating to GitLab 14.0, to identify and troubleshoot any potential problems before upgrading.
Removal date: June 22, 2021
Remove legacy DAST domain validation
The legacy method of DAST Domain Validation for CI/CD scans was deprecated in GitLab 13.8, and is removed in GitLab 14.0. This method of domain validation only disallows scans if the DAST_FULL_SCAN_DOMAIN_VALIDATION_REQUIRED environment variable is set to true in the gitlab-ci.yml file, and a Gitlab-DAST-Permission header on the site is not set to allow. This two-step method required users to opt in to using the variable before they could opt out from using the header.
For more information, see the removal issue.
Removal date: Jun 22, 2021
Remove off peak time mode configuration for Docker Machine autoscaling
In GitLab Runner 13.0, issue #5069, we introduced new timing options for the GitLab Docker Machine executor. In GitLab Runner 14.0, we have removed the old configuration option, off peak time mode.
Removal date: Jun 22, 2021
Remove redundant timestamp field from DORA metrics API payload
The deployment frequency project-level API endpoint has been deprecated in favor of the DORA 4 API, which consolidates all the metrics under one API with the specific metric as a required field. As a result, the timestamp field, which doesn’t allow adding future extensions and causes performance issues, will be removed. With the old API, an example response would be { "2021-03-01": 3, "date": "2021-03-01", "value": 3 }. The first key/value ("2021-03-01": 3) will be removed and replaced by the last two ("date": "2021-03-01", "value": 3).
Removal date: June 22, 2021
Remove success and failure for finished build metric conversion
In GitLab Runner 13.5, we introduced failed and success states for a job. To support Prometheus rules, we chose to convert success/failure to finished for the metric. In 14.0, the conversion has now been removed. Refer to issue #26900 for details.
Removal date: Jun 22, 2021
Remove support for Windows Server 1903 image
In 14.0, we have removed Windows Server 1903. Microsoft ended support for this version on 2020-08-12. Refer to issue #27551 for details.
Removal date: Jun 22, 2021
Remove support for Windows Server 1909 image
In 14.0, we have removed Windows Server 1909. Microsoft ended support for this version on 2021-05-11. Refer to issue #27899 for details.
Removal date: Jun 22, 2021
Removed Global SAST_ANALYZER_IMAGE_TAG in SAST CI template
With the maturity of GitLab Secure scanning tools, we’ve needed to add more granularity to our release process. Previously, GitLab shared a major version number for all analyzers and tools. This requires all tools to share a major version, and prevents the use of semantic version numbering. In GitLab 14.0, SAST removes the SAST_ANALYZER_IMAGE_TAG global variable in our managed SAST.gitlab-ci.yml CI template, in favor of the analyzer job variable setting the major.minor tag in the SAST vendored template.
Each analyzer job now has a scoped SAST_ANALYZER_IMAGE_TAG variable, which will be actively managed by GitLab and set to the major tag for the respective analyzer. To pin to a specific version, change the variable value to the specific version tag.
If you override or maintain custom versions of SAST.gitlab-ci.yml, update your CI templates to stop referencing the global SAST_ANALYZER_IMAGE_TAG, and move it to a scoped analyzer job tag. We strongly encourage inheriting and overriding our managed CI templates to future-proof your CI templates. This change allows you to more granularly control future analyzer updates with a pinned major.minor version.
This deprecation and removal changes our previously announced plan to pin the Static Analysis tools.
Removal date: June 22, 2021
Ruby version changed in Ruby.gitlab-ci.yml
By default, the Ruby.gitlab-ci.yml file has included Ruby 2.5.
To better support the latest versions of Ruby, the template is changed to use ruby:latest, which is currently 3.0. To better understand the changes in Ruby 3.0, please reference the ruby-lang.org release announcement.
Relevant Issue: Updates ruby version 2.5 to 3.0
Removal date: June 22, 2021
Segments removed from DevOps Adoption API
The first release of the DevOps Adoption report had a concept of Segments. Segments were quickly removed from the report because they introduced an additional layer of complexity on top of Groups and Projects. Subsequent iterations of the DevOps Adoption report focus on comparing adoption across groups rather than segments. GitLab 14.0 removes all references to Segments from the GraphQL API and replaces them with Enabled groups.
Removal date: June 22, 2021
Service Templates removed
Service Templates are removed in GitLab 14.0. They were used to apply identical settings to a large number of projects, but they only did so at the time of project creation.
While they solved part of the problem, updating those values later proved to be a major pain point. Project Integration Management solves this problem by enabling you to create settings at the Group or Instance level, and projects within that namespace inheriting those settings.
Removal date: June 22, 2021
Sidekiq queue selector options no longer accept the ‘experimental’ prefix
GitLab supports a queue selector to run only a subset of background jobs for a given process. When it was introduced, this option had an ‘experimental’ prefix (experimental_queue_selector in Omnibus, experimentalQueueSelector in Helm charts).
As announced in the 13.6 release post, the ‘experimental’ prefix is no longer supported. Instead, queue_selector for Omnibus and queueSelector in Helm charts should be used.
Removal date: Jun 22, 2021
Ubuntu 16.04 support
Ubuntu 16.04 reached end-of-life in April 2021, and no longer receives maintenance updates. We strongly recommend users to upgrade to a newer release, such as 20.04.
GitLab 13.12 will be the last release with Ubuntu 16.04 support.
Removal date: June 22, 2021
Unicorn removed in favor of Puma for GitLab self-managed
Support for Unicorn has been removed in GitLab 14.0 in favor of Puma. Puma has a multi-threaded architecture which uses less memory than a multi-process application server like Unicorn. On GitLab.com, we saw a 40% reduction in memory consumption by using Puma.
Removal date: June 22, 2021
Update Auto Deploy template version
In GitLab 14.0, we will update the Auto Deploy CI template to the latest version. This includes new features, bug fixes, and performance improvements with a dependency on the v2 auto-deploy-image. Auto Deploy CI tempalte v1 will is deprecated going forward.
Since the v1 and v2 versions are not backward-compatible, your project might encounter an unexpected failure if you already have a deployed application. Follow the upgrade guide to upgrade your environments. You can also start using the latest template today by following the early adoption guide.
Removal date: June 22, 2021
Update CI/CD templates to stop using hardcoded master
Our CI/CD templates have been updated to no longer use hard-coded references to a master branch. In 14.0, they all use a variable that points to your project’s configured default branch instead. If your CI/CD pipeline relies on our built-in templates, verify that this change works with your current configuration. For example, if you have a master branch and a different default branch, the updates to the templates may cause changes to your pipeline behavior. For more information, read the issue.
Removal date: June 22, 2021
WIP merge requests renamed ‘draft merge requests’
The WIP (work in progress) status for merge requests signaled to reviewers that the merge request in question wasn’t ready to merge. We’ve renamed the WIP feature to Draft, a more inclusive and self-explanatory term. Draft clearly communicates the merge request in question isn’t ready for review, and makes no assumptions about the progress being made toward it. Draft also reduces the cognitive load for new users, non-English speakers, and anyone unfamiliar with the WIP acronym.
Removal date: Jun 22, 2021
Web Application Firewall (WAF)
The Web Application Firewall (WAF) was deprecated in GitLab 13.6 and is removed from GitLab 14.0. The WAF had limitations inherent in the architectural design that made it difficult to meet the requirements traditionally expected of a WAF. By removing the WAF, GitLab is able to focus on improving other areas in the product where more value can be provided to users. Users who currently rely on the WAF can continue to use the free and open source ModSecurity project, which is independent from GitLab. Additional details are available in the deprecation issue.
Removal date: June 22nd, 2021
CI_PROJECT_CONFIG_PATH removed in Gitlab 14.0
GitLab 14.0 removes the CI_PROJECT_CONFIG_PATH pre-defined project variable in favor of CI_CONFIG_PATH, which is functionally the same. If you are using CI_PROJECT_CONFIG_PATH in your pipeline configurations, update them to use CI_CONFIG_PATH instead.
Removal date: Jun 22, 2021
CI_PROJECT_CONFIG_PATH variable has been removed
The CI_PROJECT_CONFIG_PATH predefined project variable
has been removed in favor of CI_CONFIG_PATH, which is functionally the same.
If you are using CI_PROJECT_CONFIG_PATH in your pipeline configurations,
please update them to use CI_CONFIG_PATH instead.
Removal date: Jun 22, 2021
GitLab.com reliability and performance
Webhook rate limiting on gitlab.com for GitLab Free
To improve GitLab.com infrastructure reliability, and protect against abuse and configuration errors, we’re now enforcing a rate limit of 120 calls per minute for each configured webhook in projects or groups. This limit currently only applies to Free users on GitLab.com. We’re also considering introducing higher thresholds for paid GitLab plans, which should still support normal webhook usage.
Free tier scheduled pipeline frequency limit on GitLab.com
Scheduled pipelines that run very frequently affect the performance of GitLab.com. In GitLab 14.0, we are limiting the frequency of scheduled pipelines to no more than once per hour per scheduled pipeline for Free tier users. Premium and Ultimate users are not affected by this change.
Important notes on upgrading to GitLab 14.0
- Remove old ElasticSearch migrations. By removing old ElasticSearch migrations, it will be easier to perform Advanced Search migrations when upgrading GitLab.
- GitLab 14.0 will only support migrations from GitLab 13.12. All previous versions must be upgraded to GitLab 13.12 before upgrading to GitLab 14.0, the GitLab’s latest major version, to complete all ElasticSearch migrations.
- Before upgrading to GitLab 14.0, you will need to upgrade to 13.12. For more details on upgrading, see Upgrading to a new major version.
- You must upgrade to PostgreSQL 12 before upgrading to GitLab 14.0. PostgreSQL 12 is the minimum required version starting in GitLab 14.0. PostgreSQL 11 has been removed and is no longer officially supported. You will need to plan on some downtime for the PostgreSQL upgrade because the database must be down while the upgrade is performed. If you are using the GitLab-provided PostgreSQL database, you should make sure that your database is PostgreSQL 12 on GitLab 13.12 regardless of your installation method.
- Multi-node database instances will need to switch from repmgr to Patroni, prior to upgrading PostgreSQL with Patroni. Geo secondaries can then be updated and re-synchronized.
- Before upgrading to GitLab 14.0 you must migrate fully to hashed storage.
- Before upgrading to GitLab 14.0 you must migrate to Puma.
Changelog
Please check out the changelog to see all the named changes:
Installing
If you are setting up a new GitLab installation please see the download GitLab page.
Updating
Check out our update page.
Questions?
We'd love to hear your thoughts! Visit the GitLab Forum GitLab Forum and let us know if you have questions about the release.
GitLab Subscription Plans
GitLab is available in self-managed and cloud SaaS options.
Self-managed: Deploy on-premises or on your favorite cloud platform.
- Free: For small teams, personal projects, or GitLab trials with unlimited time.
- Premium: For distributed teams who need advanced features, high availability, and 24/7 support.
- Ultimate: For enterprises that want to align strategy and execution with enhanced security and compliance.
Cloud SaaS - GitLab.com: hosted, managed, and administered by GitLab with free and paid subscriptions for individuals and teams.
- Free: Unlimited private repositories and unlimited collaborators on a project.
- Premium: For teams that need more robust DevOps capabilities, compliance and faster support.
- Ultimate: Great with many CI/CD jobs. Every public project gets the features of Ultimate for free irrespective of their plan.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK
