

Automate vulnerability scanning in AWS CodePipeline with Snyk
source link: https://snyk.io/blog/automate-vulnerability-scanning-in-aws-codepipeline-with-snyk/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

Automate vulnerability scanning in AWS CodePipeline with Snyk

Jay Yeras
June 8, 2021
Empowering developers to build securely has always been Snyk’s mission. We enable you to find and fix security vulnerabilities in your code and open source dependencies, as well as enable development teams to easily integrate security testing as part of their automated delivery pipelines. Snyk also provides native integrations with leading CI/CD platforms such as Jenkins, TeamCity, and CircleCI.
To this end, we are happy to announce Snyk’s latest integration with AWS CodePipeline. Part of the AWS developer tools suite, AWS CodePipeline allows organizations to rapidly deliver features to users by automating the software release process.
With this new integration, AWS CodePipeline developers no longer need to leave their console to conduct vulnerability scans. The automated security scans of Snyk Open Source are available directly within AWS. Additionally, this integration circumvents the need to integrate with other development tools, such as AWS CodeCommit.
As part of the continuous delivery service, Snyk allows AWS CodePipeline users to make security an automated part of their build, test, and deploy phases. As partners, AWS and Snyk help joint users and customers more easily and elegantly build security into their modern, automated CI/CD software pipeline.
Getting started with AWS CodePipeline
Snyk’s AWS CodePipeline integration can be initiated directly within the AWS CodePipeline console. If you don’t already have a Snyk account, you can sign up for a free.
From the AWS CodePipeline console, you can add Snyk to a new or existing pipeline in a few simple steps. At any point after the Source stage, you can add a Scan stage. Click Edit, and add a Scan stage. Then, click Add an Action Group to open the Edit Action window. Here you can name the action, click the Action Provider pulldown arrow, select Snyk, and click Connect with Snyk to begin the connection process.
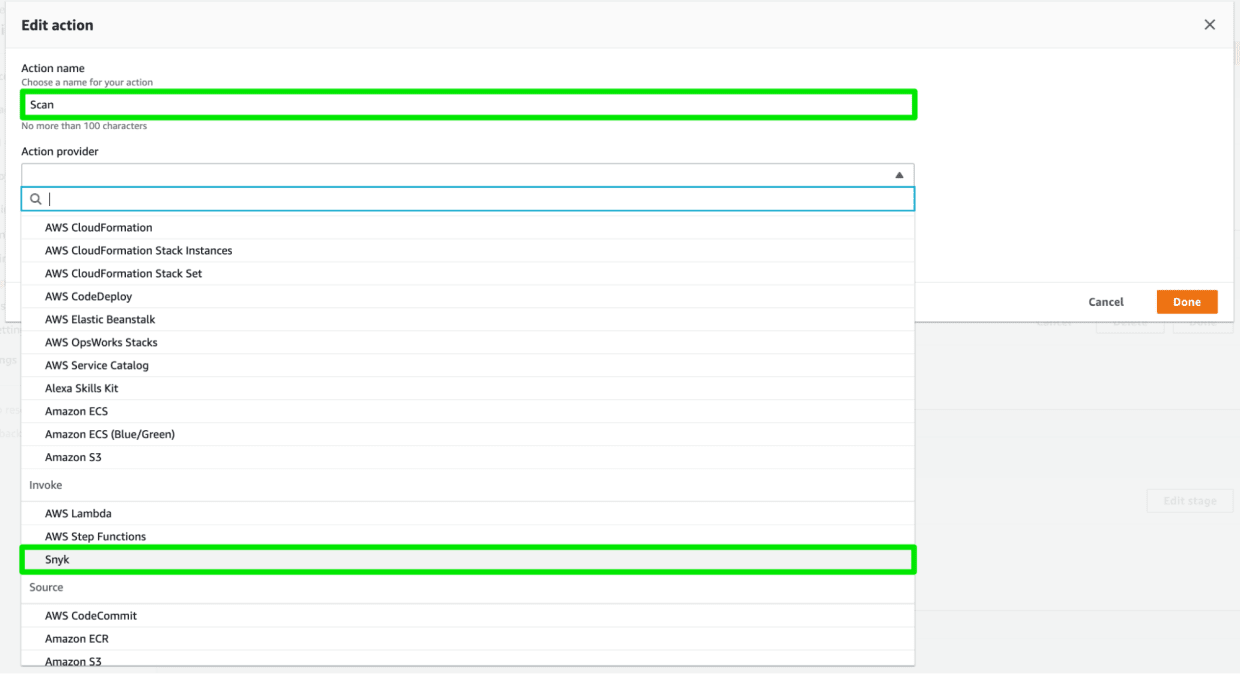 Snyk is now available in the Action Provider pulldown list of AWS CodePipeline.
Snyk is now available in the Action Provider pulldown list of AWS CodePipeline.You’ll then need to enter your Snyk credentials to give AWS CodePipeline permission to begin scanning your open source code.

Once you’ve connected Snyk, you can configure the integration with severity thresholds for issues reporting. For example, you may want to fail builds only for high severity vulnerabilities. You can also choose to scan your full application code or focus on code manifests.
Analyzing the results
Once a scan commences, Snyk analyzes the application’s manifest file and correlates the list of dependencies with Snyk’s vulnerability database. Upon completion, scan results show up immediately in AWS CodePipeline, providing visibility into issues found and how to remediate them within your console.
Snyk provides detailed reports for your open source code. You can navigate to Projects and choose View Report to set the frequency with which the project is checked for vulnerabilities.
From View Report, you can also choose the Dependencies tab to see which open source dependencies are being used to build the application. By analyzing the application’s manifest file, Snyk builds a full dependency tree, accurately identifying both direct and transitive dependencies (transitives account for 78% of the vulnerabilities detected by Snyk). This enables Snyk to show exactly how a vulnerability was introduced into the application.
Snyk provides fix recommendations that dramatically reduce the number of vulnerabilities in your open source code with minimal changes. There are often multiple alternative libraries available, but Snyk suggests the best dependency version to choose to eliminate the most vulnerabilities. Snyk also helps remediate issues within transitive dependencies with the fewest upgrades to direct dependencies necessary. This can dramatically accelerate the triage process for developers without introducing compatibility issues.
Within the AWS CodePipeline console, you can also review vulnerability data that’s organized by priority score, known exploits, and many other characteristics. You can filter the results to only show high severity issues, vulnerabilities that have a fix, or other options to help prioritize your remediation efforts.
Snyk’s ongoing partnership with AWS DevOps
AWS is an important partner in helping Snyk deliver on our mission of developer-first security. Many technology buyers have strong roots in and trust in the AWS ecosystem. The relationship between AWS and Snyk started with our company’s founding in 2015 and has grown stronger by the day. Snyk is very proud to be an APN Advanced Tier partner, an APN Global Startup Program launch partner, and an AWS customer.
Additionally, we recently announced integrations into the AWS suite of Kubernetes related tools, Amazon Elastic Container Registry (ECR) and Amazon Elastic Kubernetes Service (EKS). These integrations enable you to scan Kubernetes containers with Snyk without having to leave the AWS console.
Beyond Kubernetes, Snyk offers product integrations into AWS DevOps, serverless, and container solutions. And you can expect more integrated product solutions and useful technical content to come from AWS and Snyk in the coming weeks and months. Find out more on our dedicated AWS landing page.
Together, AWS and Snyk have made it as easy as possible to surface and remediate vulnerabilities in open source code housed in AWS CodePipeline. This easy to use integration enables early issue detection to help speed your entire SDLC. Now, your organization can continue to improve its security posture without facing developer friction.
Want to learn more about AWS CodePipeline workflow scanning? See our full documentation to get started.
Secure AWS CodePipeline for free
Sign up for Snyk to secure your CI/CD software pipeline for free.
Join us at SnykCon 2021
We’re bringing development and security together in our free, 3-day virtual event focused on helping teams build securely.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK