

IoT botnets: Perspectives from a residential router
source link: https://itwire.com/guest-articles/guest-opinion/iot-botnets-perspectives-from-a-residential-router.html
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

Guest Opinion by Daniel Smith, head of research, Radware. Many of us are currently wrapped up in the SolarWinds and ProxyLogon events. But let's take a moment to highlight the risk that residential routers face from the propagation of IoT botnets and the problems devices present once they are infected.
To start, it's truly amazing to see how many malicious events a residential router experiences every single day – from scanners looking for vulnerable services to exploitation attempts from all over the world.
Users who wish to get into threat hunting and monitoring traffic personally would do well to install the T-pot Honeypot by Deutsche Telekom. It's a straightforward, easy-to-use, all-in-one solution that allows users to quickly deploy and review network events.
For a tutorial, I recommend Veronica Valeros's blog, Installing T-pot Honeypot Framework in the Cloud. Anyone interested in going a step further can report, track and analyse samples captured in their honeypot with URLhaus from Abuse.Ch and Intezer's malware analysis platform.
My focus, however, zeroes in on events strictly related to IoT botnets. For disclosure, the specific residential sensor used in this blog is located in Texas on a major ISP.
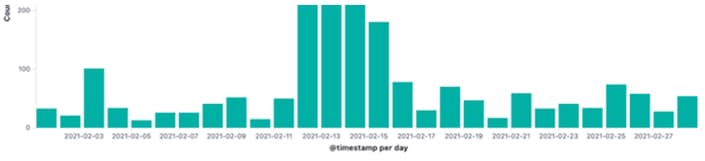
In February, this sensor saw millions of events. Of those, 2,227 were related to the propagation of malware for IoT botnets. A majority of these events came from China, Hong Kong and South Korea.
But this is no surprise as the Mozi campaign has been generating high volumes of malicious traffic from Asia for some time now. Surprisingly, a huge volume of the malicious traffic can reach a residential device.
While one would assume that these threat actors (known as bot herders) would want to live below the radar, in fact most of their campaigns are very loud and noticeable, deployed in a spray and pray fashion.
On an average day in February, the residential sensor saw about 50 malicious attempts to propagate IoT malware. Some days were busier than others. These spikes can be caused by the successful and rapid spread of malware, or a scanner that's merely spamming out multiple attempts to compromise a device.
Either way, these events are very noticeable and get reported for a takedown almost immediately.
Common alerts seen from the residential sensor include Mirai Variant User-Agent, WebShell Generic, and 401TRG Generic Webshell request from a signature base perspective. Below is a more detailed graph of the top 10 signatures seen for IoT malware distribution in February.
For example, a recent event was flagged and tagged with the signature SURICATA HTTP Unexpected Request Body, which originated from Guangdong, China.
The Uri POST /soap.cgi?service=WANIPConn1 tells us that this malware is propagating via a D-Link exploit that allows an attacker to leverage a command injection via the UPnP SOAP interface in multiple D-Link devices.
One of the things that stand out here is that CVE-2013-7471 is eight years old and still used to distribute one of the more notorious P2P botnets, Mozi.
Another point of interest while considering these network events is the ports that the malware is targeting. This kind of indicators can often help identify the device and/or service that is being targeted. For example, in February, the top five ports targeted by IoT malware were 80, 23, 60001, 7574, 49152.
So, what does this tell us? Other than the apparent ports, 23 and 80, port 60001 indicated that the malware is attempting to propagate and deliver a payload via a four-year-old vulnerability targeting JAWS DVR web servers.
One of my favourite indicators to check is the User-Agent. Bot herders have egos and a sense of humour, and sometimes this is displayed via User-Agents.
For example, in February the residential sensor saw several attempts to distribute IoT malware with the User-Agent, KrebsOnSecurity. Obviously, this is not the work of Brian Krebs. But this month, the same herder has replaced the User-Agents with ImSowwyForUsingMrCrabs and HelloBadPacketZ. Likely in an attempt for attention.
Another notable User-Agent leveraged by a bot herder was XTC and part of the Hoaxcall botnet campaign in 2020. Just to note, there are infected Hoaxcall routers still online. Even after the takedown to Hoaxcall's C2 servers, the payload is yet being distributed a year later.
Finally, once a residential router becomes infected, it can become weaponised to launch DDoS attacks, mine cryptocurrency, or leveraged as a proxy for fraudulent ad requests.
For example, the herder with a sense of humour from above has been running a fairly extensive campaign for the last few months. The payloads being retrieved from 45.14.149.204, 7069f495263a57733d787745246f5fbf34f6f9164f87cad5d11a810b6c718005, is designed to abuse IoT devices for the purpose of launching distributed denial of service attacks. The payload contains over 20 denial of service attack vectors and is hosted on several domains.
Clearly the threat landscape directed at residential routers is one of despair. The topic, in general, opens up too many ongoing debates about who should clean up and regulate the standards of security for IoT devices and if we, as a community, should be doing more to target bot herders.
One thing is certain: our industry could use more threat hunters, especially after recent events. I encourage anyone interested in threat hunting to jump right in. The community is very active and willing to help others. Regardless of skill set, the more eyes we have on the problem, the better off we will become.
Image: EpicTop10.com (CC BY 2.0)
Subscribe to ITWIRE UPDATE Newsletter here
GRAND OPENING OF THE ITWIRE SHOP
The much awaited iTWire Shop is now open to our readers.Visit the iTWire Shop, a leading destination for stylish accessories, gear & gadgets, lifestyle products and everyday portable office essentials, drones, zoom lenses for smartphones, software and online training.
PLUS Big Brands include: Apple, Lenovo, LG, Samsung, Sennheiser and many more.
Products available for any country.
We hope you enjoy and find value in the much anticipated iTWire Shop.
INTRODUCING ITWIRE TV
iTWire TV offers a unique value to the Tech Sector by providing a range of video interviews, news, views and reviews, and also provides the opportunity for vendors to promote your company and your marketing messages.We work with you to develop the message and conduct the interview or product review in a safe and collaborative way. Unlike other Tech YouTube channels, we create a story around your message and post that on the homepage of ITWire, linking to your message.
In addition, your interview post message can be displayed in up to 7 different post displays on our the iTWire.com site to drive traffic and readers to your video content and downloads. This can be a significant Lead Generation opportunity for your business.
We also provide 3 videos in one recording/sitting if you require so that you have a series of videos to promote to your customers. Your sales team can add your emails to sales collateral and to the footer of their sales and marketing emails.
See the latest in Tech News, Views, Interviews, Reviews, Product Promos and Events. Plus funny videos from our readers and customers.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK