

Phorpiex-Powered BitRansomware Targets APAC Universities
source link: https://blogs.vmware.com/networkvirtualization/2020/12/phorpiex-powered-bitransomware-targets-apac-universities.html/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
Phorpiex-Powered BitRansomware Targets APAC Universities
By: Jason Zhang, Stefano Ortolani – VMware Threat Analysis Unit
BitRansomware (also known as DCryptSoft or Readme) is a — you guessed it — ransomware program that first surfaced in July 2020. Initially targeting English-speaking users1 this threat actor recently expanded its attack to the APAC region, focusing in particular on universities in Japan and Hong Kong.
The BitRansomware malware encrypts victims’ files and then appends the suffix .ReadMe to each filename. Like the Nemty ransomware attack we reported on earlier this year2, the BitRansomware attack was delivered via a massive email campaign carried out again by the Phorpiex botnet3,4. The malspam campaign distributed a swarm of ZIP archive files containing ransomware downloaders in malicious executables.
In this blog post, we detail some of VMware NSX’s telemetry around the magnitude of the BitRansomware campaign, and we then provide a brief overview of the most distinctive aspects of the attack.
The Spam Campaign
The chart below shows the detection timeline of the campaign as it affected some of our customers in the APAC region. As we can see, the campaign started on November 3, and peaked at over 28,000 email instances on November 4 before fading away.

Figure 1: Number of emails with a ZIP attachment containing a BitRansomware downloader
Figure 2 shows some typical examples of email senders, subjects, and attachments from the campaign. As we can see, the subject line of the spam emails is always the same:
Photo of you???
The email sender display name is always Jenny Green in the campaign, and the sender email addresses are in the format of jennyd{2}@d{4}.com where d refers to a digit, e.g., jenny30@3058[.]com. The pattern of the email addresses in this campaign is similar to the Sextortion campaign also powered by the Phorpiex botnet5. All the ZIP archive attachments follow the naming pattern Photo-d{3}-d{3}.jpg.scr.zip.
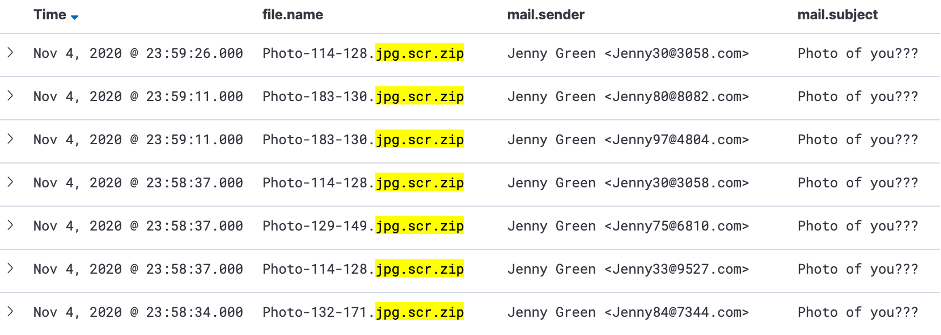
Figure 2: Some example names of mail senders, subjects, and attachments from the campaign
Using the keyword photo in email subject lines or attachment file names can certainly attract the attention and curiosity of the recipients, hence increasing the infection rate. This is a common social engineering technique leveraged by threat actors to entice potential victims into opening the attachment and activating the download process.
The Attack Infection Chain
To better understand the attack, we analyzed one of the samples from the campaign, as shown in Table 1, which lists the meta information for a ZIP archive file.
MD5 e93e26ad51389efe123b68fb34841daa SHA1 af658e98da25d6b64143966ad99f84d159f6cb0e SHA256 897ddd7880b0904097e09d1dffb5d7617951f8b6fe350b20f1ed722b95950166 File name Photo-170-190.jpg.scr.zip Size 33420 bytes Type application/zip Table 1: A ZIP archive attachment from the attack.Extracting the ZIP archive file in Table 1 reveals the actual malware downloader, as shown in Table 2. The downloader has a .scr extension, which makes it look like a screensaver file.
MD5 4a94758d9b8bed45249bffffbaaa0460 SHA1 fff1c09b6e710d1804716e6b6b6c055a899aa1fc SHA256 64cc82160edccda2bfd82d92b429ea0f98dcda9659a5c757b2748119847f5532 File name Photo-170-190.jpg.scr Size 33280 bytes Type application/x-pe-app-32bit-i386 Table 2: The malicious executable file extracted from the ZIP file in Table 1.It’s a common trait for attackers to use the same malware payload multiple times. This is exactly the case for the malicious downloader, which appeared in numerous ZIP archives, as illustrated in Figure 3.
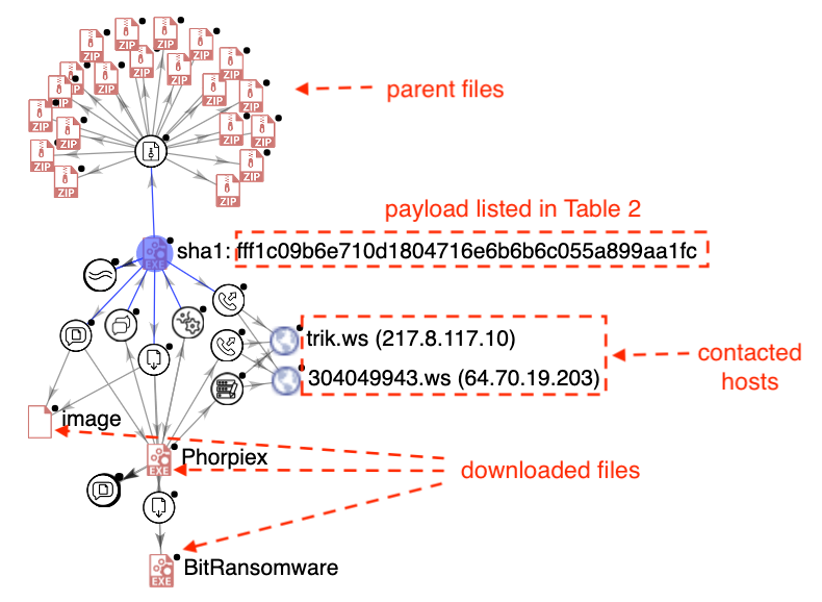
Figure 3: The attack infection chain, created with VirusTotal Graph, visualizing the relationship between the payload, its parent ZIP archives, contacted hosts, and files downloaded. The meaning of each node on the graph can be found here
If a recipient clicks on the ZIP archive (as shown in Table 1 and executes the payload (as listed in Table 2) embedded in the archive, the infection chain is activated, and the process Photo-170-190.jpg.scr is created. After establishing a connection to the command and control (C2) hosts (as shown in Figure 3, the initial payload attempts to download the second-stage payloads. First, it downloads an image from the following URL:
http://trik[.]ws:8080/p.jpg
The downloaded image (sha1: bbe3b9dc5ca78b399ae151afc0f03972e710b23b) is saved in the %TEMP% directory on the infected machine. The image is then displayed with the default photo viewer application on the victim’s machine by running the following command:
C:\Windows\System32\cmd.exe /c start C:\Users\Lisa\AppData\Local\Temp\14064.jpg
Figure 4 shows the downloaded image, whose disturbing nature is another attempt to attract the attention of users and prevent them from noticing other malicious activities.

Figure 4: The downloaded image (sha1: bbe3b9dc5ca78b399ae151afc0f03972e710b23b)
In the meantime, the same process Photo-170-190.jpg.scr downloads a Phorpiex spam bot (sha1: 96795527c65711c13aef7f2cda3b5a0ff5779137) in the background from the following URL:
http://trik[.]ws:8080/pcnew.exe
The Phorpiex payload is saved in two locations on the victim’s machine, as revealed by our analysis in a controlled environment:
C:\Users\Lisa\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\J3FMASWX\pcnew[1].exe
C:\Users\Lisa\AppData\Local\Temp\12412.exe
The process Photo-170-190.jpg.scr then spawns a child process to execute 12412.exe. The 12412.exe process first creates a folder with all digits as the folder name on the victim’s C: drive and makes a copy of itself with the name winsvcs.exe in the newly created folder:
C:\16791677923619\winsvcs.exe
The 12412.exe process then creates a child process to execute winsvcs.exe. It also adds itself to the victim’s Windows registry to make the infection persistent, as shown in Table 3:
Location HKU\S-1-5-21-3712457824-2419000099-45725732-1005\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Key Microsoft Windows Services Value C:\196481056811935\winsvcs.exe Table 3: Modify Windows registry settings to achieve persistence.Apart from sending spam emails, threat actors are also known to leverage the Phorpiex botnet to download and distribute malware of their choice3,4. In this attack, the Phorpiex spam bot process winsvcs.exe downloads a BitRansomware variant (sha1: 114954c44d72ee0bb630c317f06869e11b543f62) hosted on one of the C2 servers, as Figure 3 shows, into the %TEMP% directory:
C:\Users\Lisa\AppData\Local\Temp\2400122622.exe
A new process is created by the winsvcs.exe process to execute the ransomware payload.
Upon execution, the ransomware encrypts files of certain file types, and leaves a ransom note in the affected directories. Figure 5 shows the encryption file marker (CRYPTO LOKER) and part of the ransom note texts contained in the ransomware sample:
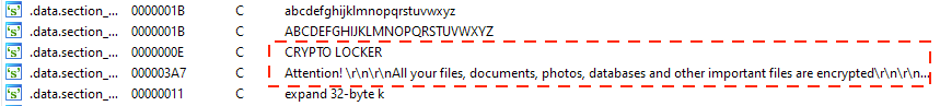
Figure 5: Encryption file marker and ransom note strings
The full ransom note is shown in Figure 6. The note contains a URL that requires a TOR browser. Like most ransomware attacks, it asks the victim to visit the link to pay a certain amount of cryptocurrency (Bitcoin in this case) to purchase the decryption key.

Figure 6: Ransom note dropped by the BitRansomware sample
VMware NSX Detection
VMware NSX customers are well-protected against this kind of Phorpiex-powered ransomware attack. Figure 7 shows the analysis overview from a controlled environment when executing the initial malware in the attached archive. As shown, VMware’s AI-driven NSX Advanced Threat Analyzer successfully detected a few high-risk artifacts, such as ransomware-specific behavior, malicious code reuse, and the creation of hidden executable files.
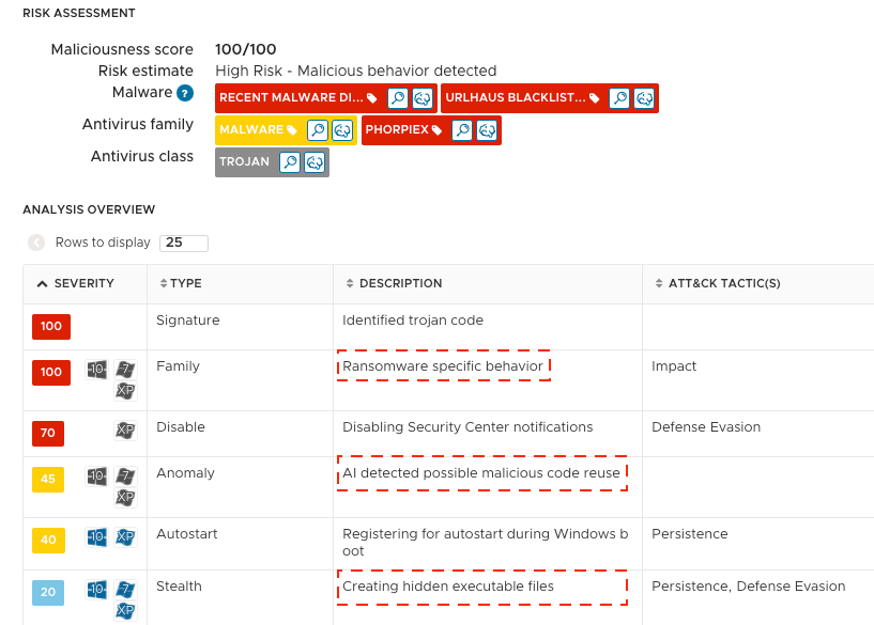
Figure 7: VMware NSX advanced threat analysis overview
The figure below shows the fishbone chart detailing the infection flow from NSX analysis, which echoes the infection flow discussed in the previous section.

Figure 8: BitRansomeware downloader infection flow from NSX advanced threat analysis
Conclusion
The Phorpiex botnet is known for delivering ransomware such as Nemty, and, when still active, GandCrab2,3. In this campaign, the attacker used the Phorpiex botnet to spread BitRansomware, targeting universities in the APAC region. As our analysis shows, the threat actor leveraged various techniques to maximize the infection rate of the attack. The attack started with a spam campaign. When the attachment was activated, it downloaded and displayed an image on the victim’s screen while also downloading the actual Phorpiex variant from one of the C2 hosts. Upon execution, the Phorpiex payload dropped the final BitRansomware copy from a C2 server. It’s worth noting that behavior-based approaches, such as VMware’s AI-driven NSX Advanced Threat Analyzer, are well-suited to identifying the complete kill-chain of the malware sample, thanks to a combination of static and dynamic analysis techniques.
Bibliography
[1] “BitRansomware,” 8 07 2020. [Online]. Available: https://id-ransomware.blogspot.com/2020/08/bit-ransomware.html. [Accessed 17 11 2020]. [2] J. Zhang and S. Ortolani, “Nemty Ransomware Scaling UP: APAC Mailboxes Swarmed by Dual Downloaders,” VMware, 18 2 2020. [Online]. Available: https://www.lastline.com/labsblog/nemty-ransomware-scaling-up-apac-mailboxes-swarmed-dual-downloaders/. [Accessed 17 11 2020]. [3] A. Bukhteyev, “Phorpiex Breakdown,” Check Point, 19 11 2019. [Online]. Available: https://research.checkpoint.com/2019/phorpiex-breakdown/. [Accessed 17 11 2020]. [4] ProofPoint, “Phorpiex – A decade of spamming from the shadows,” ProofPoint, 24 5 2018. [Online]. Available: https://www.proofpoint.com/us/threat-insight/post/phorpiex-decade-spamming-shadows. [Accessed 17 11 2020]. [5] G. Mansharov and A. Bukhteyev, “In the Footsteps of a Sextortion Campaign,” Check Point, 16 10 2019. [Online]. Available: https://research.checkpoint.com/2019/in-the-footsteps-of-a-sextortion-campaign/. [Accessed 30 11 2020].Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK