

PowerShell: Encrypt and Decrypt Data by using Certificates (Public Key / Private...
source link: https://sid-500.com/2017/10/29/powershell-encrypt-and-decrypt-data/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

There are many encryption and decryption tools around. PowerShell is a Windows built-in tool and you can use it for cryptography as well. In this blog post I am going to play with encryption and decryption of data. My followers know what’s coming next: I don’t care much of 3rd party tools and yes, of course, I am going to use only Windows PowerShell.
Introduction
First of all we need a certificate. This certificate will include a private key and public key. With the private key we can decrypt data. With the public key we can encrypt data. This means if someone has my public key (I can give it to someone without any worries) he can encrypt data which is addressed to me. And I am the only one on this planet who can decrypt it. Because I am the only one who has the private key.

Creating a Certificate with New-SelfSignedCertificate
First I create a code-signing certificate with PowerShell. Name it whatever you want.
New-SelfSignedCertificate -DnsName pewa2303 -CertStoreLocation "Cert:\CurrentUser\My" -KeyUsage KeyEncipherment,DataEncipherment, KeyAgreement -Type DocumentEncryptionCert
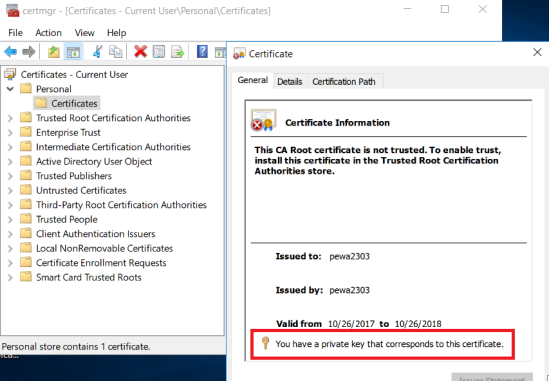
To view the certificate run certmgr.msc.
certmgr.msc
Oh, what a shame. I’ve promised I will use only PowerShell. Ok, ok here’s the command for showing your cert in PowerShell:
Get-Childitem -Path Cert:\CurrentUser\My -DocumentEncryptionCert
Memorize the Subject Name of your certificate. We’ll need it in the next step.
Encrypting Data
The Protect-CmsMessage cmdlet encrypts content. Make sure, you’re running PowerShell 5.0 or above.
(Get-Host).Version.Major
Pay attention to the To Parameter. You have to provide your certificate name there. The name of my certificate is cn=pewa2303. The encrypted data will be stored in a file.
"This is a secret message" | Protect-CmsMessage -To cn=pewa2303 -OutFile C:\Temp\secret.txtOnce completed, open the file with Notepad to see what happened. Nice code

Decryption of Data
To decrypt the encrypted data run Unprotect-CmsMessage. Make sure you are logged in with the user account that created the certificate and has the private key.
Unprotect-CmsMessage -Path C:\Temp\secret.txt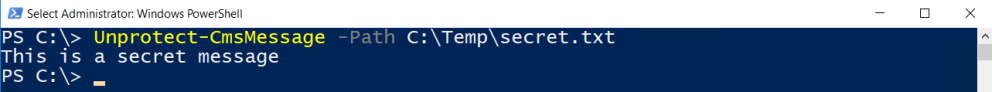
Nice one.
What happens when another user trys to open the file? Petra is not able to decrypt the data. She does not have the private key.

Unprotect-CmsMessage : The enveloped-data message does not contain the
specified recipient.
See also
See also my other security-related PowerShell articles …
How to digitally sign PowerShell Scripts
Monitoring Windows PowerShell: Enable Module Logging
Windows Server 2016: Configuring Time based Group Membership with PowerShell
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK