

Microsoft Patch Tuesday August 2020: vulnerabilities with Detected Exploitation,...
source link: https://avleonov.com/2020/08/30/microsoft-patch-tuesday-august-2020-vulnerabilities-with-detected-exploitation-useful-for-phishing-and-others/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
Microsoft Patch Tuesday August 2020: vulnerabilities with Detected Exploitation, useful for phishing and others
This time I would like to review not only the vulnerabilities that were published in the last August Microsoft Patch Tuesday, but also the CVEs that were published on other, not Patch Tuesday, days. Of course, if there are any.
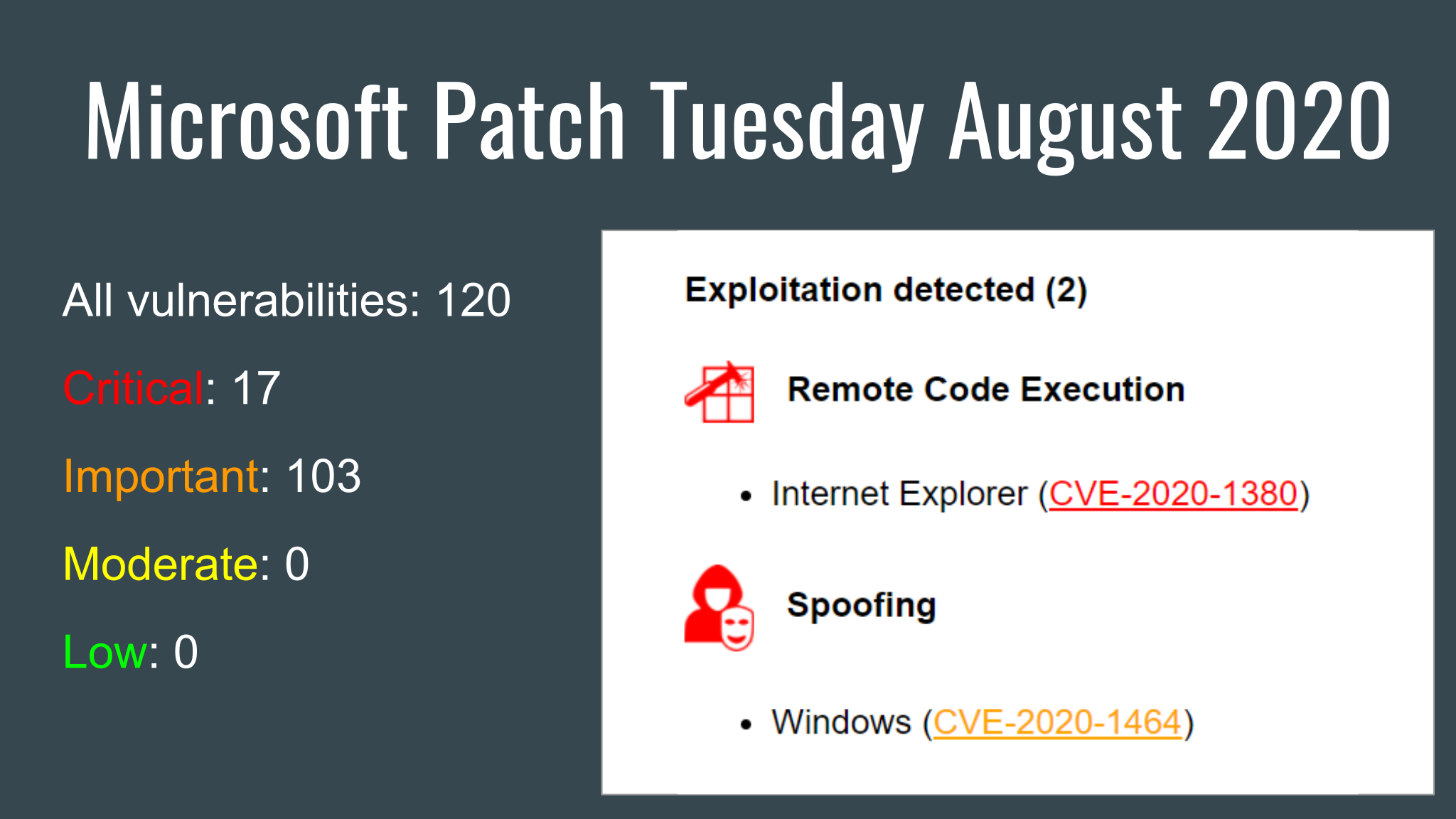
But let’s start with the vulnerabilities that were presented on MS Patch Tuesday on August 11th. There were 120 vulnerabilities: 17 of them are Critical and 103 Important. My vulristics script could not find public exploits for these vulnerabilities on Vulners.com.
For the first time in a long time, there were 2 Exploitation Detected vulnerabilities.
Exploitation detected (2)
 Remote Code Execution
Remote Code Execution
- Internet Explorer (CVE-2020-1380)
 Spoofing
Spoofing
- Windows (CVE-2020-1464)
Windows spoofing (CVE-2020-1464) is good for phishing. “In an attack scenario, an attacker could bypass security features intended to prevent improperly signed files from being loaded.”
RCE in Internet Explorer (CVE-2020-1380) might be interesting in the context of “An attacker could also embed an ActiveX control marked “safe for initialization” in an application or Microsoft Office document that hosts the IE rendering engine”.
Exploitation more likely (8)
 Remote Code Execution
Remote Code Execution
- Internet Explorer (CVE-2020-1570)
- MSHTML Engine (CVE-2020-1567)
 Elevation of Privilege
Elevation of Privilege
- Windows Ancillary Function Driver for WinSock (CVE-2020-1587)
- Windows GDI (CVE-2020-1480, CVE-2020-1529)
- Windows Kernel (CVE-2020-1566)
- Windows dnsrslvr.dll (CVE-2020-1584)
 Information Disclosure
Information Disclosure
- Windows Kernel (CVE-2020-1578)
For some reason, all VM vendors ignored Exploitation more likely vulnerabilities this time. Although RCE in Internet Explorer (CVE-2020-1570) and MSHTML Engine (CVE-2020-1567) may be interesting.
Other Product based (31)
Media Foundation
Microsoft Excel
Microsoft SharePoint
Windows Backup Engine
This time, the products with the most vulnerabilities are Media Foundation, Microsoft Excel, Microsoft SharePoint and Windows Backup Engine. VM vendors pay attention to Memory Corruption (in fact RCE) in Media Foundation, RCE in Microsoft Excel and Elevation of Privilege in Windows Backup Engine.
Other Vulnerability Type based (79)
 Remote Code Execution
Remote Code Execution
- .NET Framework (CVE-2020-1046)
- Jet Database Engine (CVE-2020-1473, CVE-2020-1557, CVE-2020-1558, CVE-2020-1564)
- Microsoft Access (CVE-2020-1582)
- Microsoft Edge (CVE-2020-1569)
- Microsoft Edge PDF (CVE-2020-1568)
- Microsoft Graphics Components (CVE-2020-1561, CVE-2020-1562)
- Microsoft Office (CVE-2020-1563)
- Microsoft Outlook (CVE-2020-1483)
- Microsoft Windows Codecs Library (CVE-2020-1560, CVE-2020-1574, CVE-2020-1585)
- Scripting Engine (CVE-2020-1555)
- Visual Studio Code (CVE-2020-0604)
- Windows Font Driver Host (CVE-2020-1520)
- Windows Media (CVE-2020-1339)
 Denial of Service
Denial of Service
- ASP.NET Core (CVE-2020-1597)
- Microsoft SQL Server Management Studio (CVE-2020-1455)
- Windows Remote Desktop Gateway (RD Gateway) (CVE-2020-1466)
 Elevation of Privilege
Elevation of Privilege
- ASP.NET and .NET (CVE-2020-1476)
- Connected User Experiences and Telemetry Service (CVE-2020-1511)
- DirectX (CVE-2020-1479)
- Local Security Authority Subsystem Service (CVE-2020-1509)
- Microsoft Office Click-to-Run (CVE-2020-1581)
- Netlogon (CVE-2020-1472)
- Windows (CVE-2020-1565)
- Windows Accounts Control (CVE-2020-1531)
- Windows AppX Deployment Extensions (CVE-2020-1488)
- Windows Backup Service (CVE-2020-1534)
- Windows CDP User Components (CVE-2020-1549, CVE-2020-1550)
- Windows CSC Service (CVE-2020-1489, CVE-2020-1513)
- Windows Custom Protocol Engine (CVE-2020-1527)
- Windows File Server Resource Management Service (CVE-2020-1517, CVE-2020-1518)
- Windows Function Discovery SSDP Provider (CVE-2020-1579)
- Windows Hard Link (CVE-2020-1467)
- Windows Kernel (CVE-2020-1417, CVE-2020-1486)
- Windows Network Connection Broker (CVE-2020-1526)
- Windows Print Spooler (CVE-2020-1337)
- Windows Radio Manager API (CVE-2020-1528)
- Windows Registry (CVE-2020-1377, CVE-2020-1378)
- Windows Remote Access (CVE-2020-1530, CVE-2020-1537)
- Windows Runtime (CVE-2020-1553)
- Windows Server Resource Management Service (CVE-2020-1475)
- Windows Setup (CVE-2020-1571)
- Windows Speech Runtime (CVE-2020-1521, CVE-2020-1522)
- Windows Speech Shell Components (CVE-2020-1524)
- Windows Storage Service (CVE-2020-1490)
- Windows Telephony Server (CVE-2020-1515)
- Windows UPnP Device Host (CVE-2020-1519, CVE-2020-1538)
- Windows WalletService (CVE-2020-1533, CVE-2020-1556)
- Windows Work Folder Service (CVE-2020-1552)
- Windows Work Folders Service (CVE-2020-1470, CVE-2020-1484, CVE-2020-1516)
 Information Disclosure
Information Disclosure
- DirectWrite (CVE-2020-1577)
- Microsoft Outlook (CVE-2020-1493)
- Microsoft Word (CVE-2020-1502, CVE-2020-1503, CVE-2020-1583)
- Windows ARM (CVE-2020-1459)
- Windows Image Acquisition Service (CVE-2020-1474, CVE-2020-1485)
- Windows Kernel (CVE-2020-1510)
- Windows RRAS Service (CVE-2020-1383)
- Windows State Repository Service (CVE-2020-1512)
- Windows WaasMedic Service (CVE-2020-1548)
 Cross Site Scripting
Cross Site Scripting
- Microsoft Dynamics 365 (On-Premise) (CVE-2020-1591)
If we look at the rest of the vulnerabilities, the most interesting are RCEs in Jet Database Engine (CVE-2020-1473, CVE-2020-1557, CVE-2020-1558, CVE-2020-1564), Microsoft Edge PDF (CVE-2020-1568), Microsoft Windows Codecs Library (CVE-2020-1560, CVE-2020-1574, CVE-2020-1585) and Windows Media (CVE-2020-1339).
The second block is Elevation of Privilege in Local Security Authority Subsystem Service (LSASS) (CVE-2020-1509), Windows Print Spooler (CVE-2020-1337) and Netlogon (CVE-2020-1472). For the last one “an unauthenticated attacker could use MS-NRPC to connect to a domain controller as a domain administrator”.
Other vulnerabilities
Now let’s take a look at the vulnerabilities that were released from 07/15/2020 to 08/27/2020 excluding the August Patch Tuesday. I added support for such exceptions in report_ms_patch_tuesday.py in Vulristics. In fact, there were very few CVE vulnerabilities outside the Patch Tuesday.
Other Vulnerability Type based (2)
 Remote Code Execution
Remote Code Execution
- Microsoft Dynamics 365 for Finance and Operations (on-premises) (CVE-2020-1182)
 Elevation of Privilege
Elevation of Privilege
- Microsoft Edge (Chromium-based) (CVE-2020-1341)
RCE in on-premises Microsoft Dynamics 365 for Finance and Operations. “An authenticated attacker with privileges to import and export data could exploit this vulnerability by sending a specially crafted file to a vulnerable Dynamics server”.
Elevation of Privilege in Microsoft Edge. “To exploit the vulnerability, the user must browse to a malicious website that is design to download a DLL file and click on the page to being the process”. But this vulnerability is surprisingly low-critical, only Moderate.
You may have heard about Microsoft unscheduled update to Windows Remote Access Elevation of Privilege released August 20. But it was about the same vulnerabilities (CVE-2020-1530, CVE-2020-1537) that were presented in August Patch Tuesday, but fixes this vulnerability for older OS versions: Windows 8.1, RT 8.1, and Server 2012 R2.
Hi! My name is Alexander and I am an Information Security Automation specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it much more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can also discuss my posts or ask a question at @avleonovchat.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK